Joker’s Stash Upgrades With Large SSN Offering and Support Infrastructure

This report was written in collaboration with independent researchers Rodrigo Bijou and Jared Wilson.
Click here to download the complete analysis as a PDF.
This report identifies and connects the original Joker’s Stash marketplace to infrastructure used to support their user base. This report will be of greatest interest to those tracking the underground economy, enterprises who need to monitor for stolen credit card data, and analysts interested in infrastructure pivoting. Sources include the Recorded Future® Platform, DomainTools Iris, Shodan, BinaryEdge, Censys, SecurityTrails, and FarsightDNS, along with third-party metadata and common OSINT techniques.
Executive Summary
The Joker’s Stash marketplace has evolved both its offerings and its infrastructure to better support its clientele. The forum operators have moved beyond carding to include a variety of personally identifiable information (PII) on victims, including contact information and Social Security numbers (SSNs). This represents an escalation in the type of data that Joker’s Stash operators are selling. Additionally, the actors have continued to provide dedicated domains and servers for their buyers but have moved the infrastructure off of Tor, allowing the infrastructure to be enumerated and tracked.
Key Judgments
Joker’s Stash operators shifted their offerings to include more personally identifiable information that is easily accessible to users. The volume of this data has grown in recent years. This poses an evolving and enduring threat to consumers and retailers affected by fraudsters populating the market.
Recorded Future assesses with high confidence that the infrastructure of Joker’s Stash exceeds the main forum currently operated by threat actors; over 500 domains and 54 servers were linked to Joker’s Stash.
Recorded Future assesses with high confidence that the domains and servers related to Joker’s Stash are spun up and used for surges in available data to provide better support to clients that buy in bulk.
Recorded Future assesses with high confidence that Joker’s Stash will remain a popular marketplace for threat actors to advertise and sell compromised credit cards, as spikes in marketplace activities have coincided with major breaches.
Background
Over the past five years, Joker’s Stash has become one of the premier underground credit card shops through significant releases of stolen credit cards from data breaches at companies like Target, Walmart, Saks Fifth Avenue, Lord & Taylor, and British Airways. These compromised payment card sales are advertised on a number of dark web forums, including Omerta, Club2Crd, Verified, and others. On August 22, 2019, the store released the first batch of stolen credit card data (dumps) from an alleged point-of-sale (POS) breach at the gas and convenience chain Hy-Vee. It is estimated that Joker’s Stash lists 5.3 million credit card numbers related to this breach.
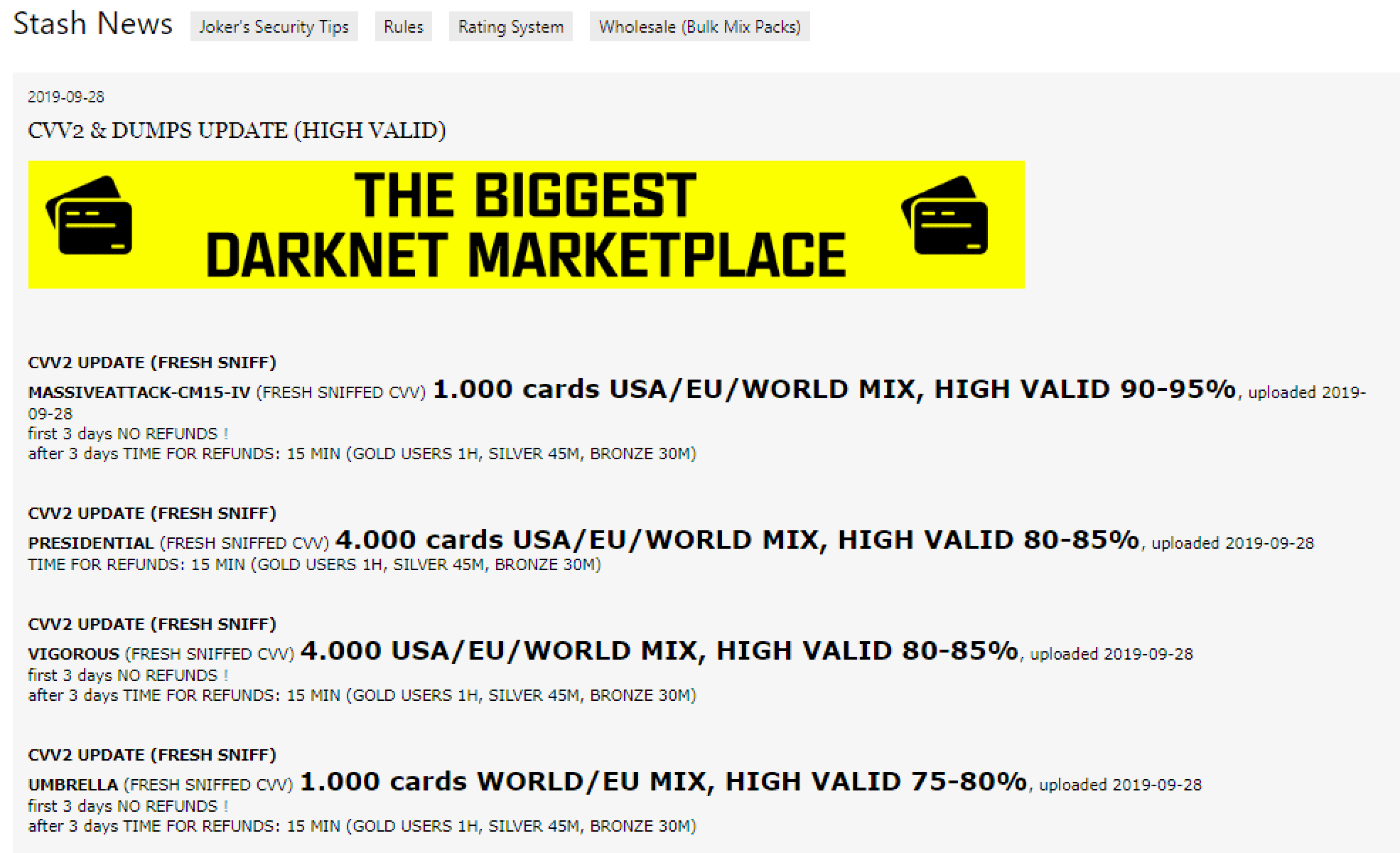
News section as listed on Joker’s Stash, as of September 30, 2019.
While it is mostly known for compromised payment cards, the shop has significantly expanded their database of SSNs with attached PII. The data includes records for Fortune 500 executives, members of the White House Cabinet, and cardholders from at least 35 U.S. states. Recorded Future could not verify the authenticity of these SSN records, but was able to verify a small number of checked instances where the PII was found to be correct. The group has been prominently advertising its SSN holdings on Twitter since August 2019.
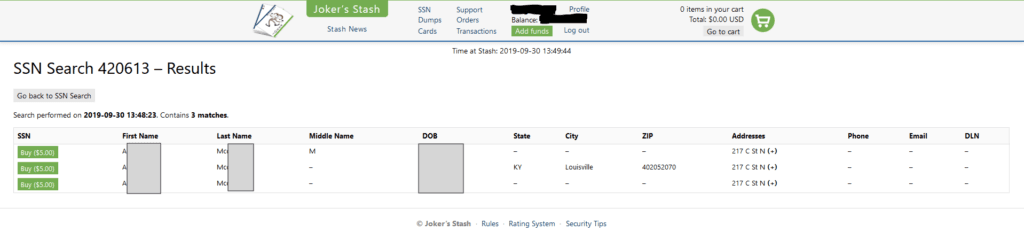
Results of an SSN search from the Joker’s Stash marketplace.
Analysis of Listings
The Joker’s Stash market is now broken into three main sections: dumps, cards, and SSNs. Dumps and cards are both related to stolen payment card data; dumps refer to the Track 2 — and in some cases, Track 1 — data on the magnetic strip of a payment card. Cards include the full data associated with a card-not-present transaction, such as the payment card number, expiration date, and CVV number, as well as other information typically provided by the payment card holder when making an online purchase. The SSN section represented a serious update to the marketplace, providing a more persistent fraud vector compared to the relatively short usefulness of credit card data. Joker’s Stash offers a comprehensive amount of personal details at $5 per record, searchable by first and last name, and at least one other identifier like “date of birth” or “state.” If the record is still available and unpurchased, the website will show a “buy” button. Records indicated as “too late to buy” have already been purchased by another threat actor, and are likely in use.
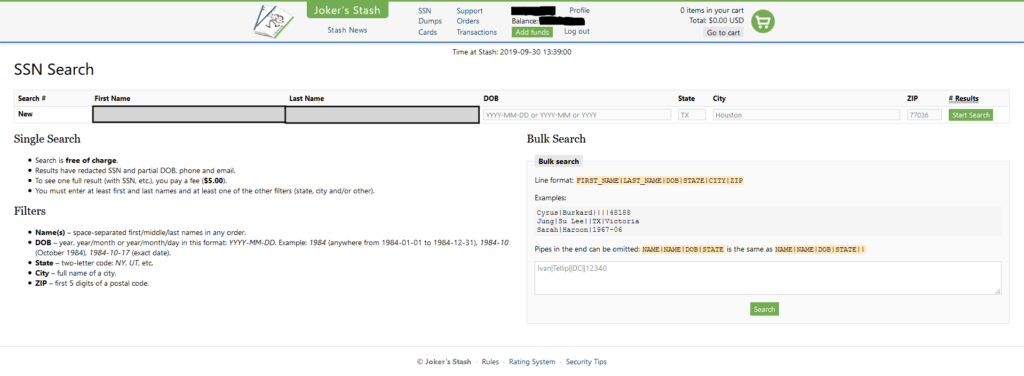
Social Security number search capability on Joker’s Stash, as of September 30, 2019.
The SSNs are searchable in bulk and can be filtered by location. The additional PII, including recent address and ZIP code, may allow for specific area targeting by fraudsters, potentially facilitating fraud against regional banks, credit unions, or smaller retail chains. The ease with which this data is accessed is particularly troubling. This is the most prominent market or forum Recorded Future is aware of that peddles SSNs in a bulk manner. It is also the first forum that allows such robust search capabilities across their data sets.
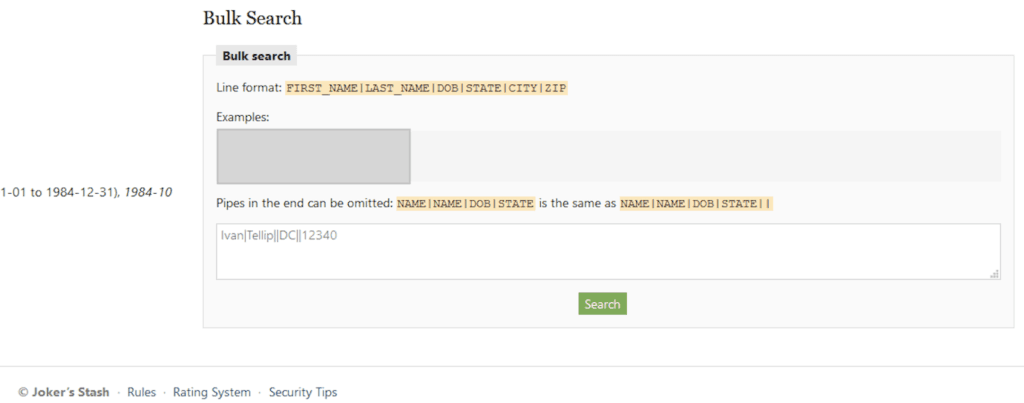
Bulk Social Security number search, as of September 30, 2019.
The introduction of SSNs that can be accessed without forum vetting significantly lowers the barrier to entry for identity theft. While the sale of SSNs on Joker’s Stash will likely result in identity theft and stolen financial data that will evade detection, it will also very likely encourage lower-end attempts. This will create volume issues for banks and financial institutions attempting to determine fraud when a request is made with fully correct PII.
Tracking Joker’s Stash Infrastructure
The operators of Joker’s Stash have relied on infrastructure on the clearnet in addition to their markets that use obfuscated methods of access. Joker’s Stash implemented the use of Blockchain DNS via browser extension in 2017, alongside a Tor marketplace, to lower barriers of access for new customers. The use of Blockchain DNS involves the download of a browser extension that stores all of the DNS data for various top-level domains (TLDs) locally. The hosting data is not managed by, or shared with, mainstream DNS providers, but over a peer-to-peer network. The peer-to-peer nature of the service renders the Joker’s Stash marketplace more impervious to takedowns or sinkholing by DNS authorities.
Insikt Group was able to identify 49 servers and 543 domains that are linked to Joker’s Stash with high confidence. The Blockchain DNS browser extension is needed to access jstash[.]bazar, but Blockchain DNS published the IP address of jstash[.]bazar on another web page, circumventing any potential obfuscation provided by the decentralized DNS.
The group has advertised a number of different domains across their alleged social media accounts on Reddit, Twitter, PasteSites, and other carding forums. There are three domains notably associated with Joker’s Stash:
jstash[.]bazar, the flagship Joker’s Stash shop, is only accessible via Blockchain DNS browser extension. However, the domain was found to be hosted on the IP address 185.61.137.166.
jstash[.]ch has been advertised on carding forums by the Joker’s Stash handle, but operates on the open internet on the server 188.209.52.24.
jstash[.]de has been advertised on Reddit, is hosted on 185.61.138.182, and previously was hosted on the same server as jstash[.]ch, on 188.209.52.24.
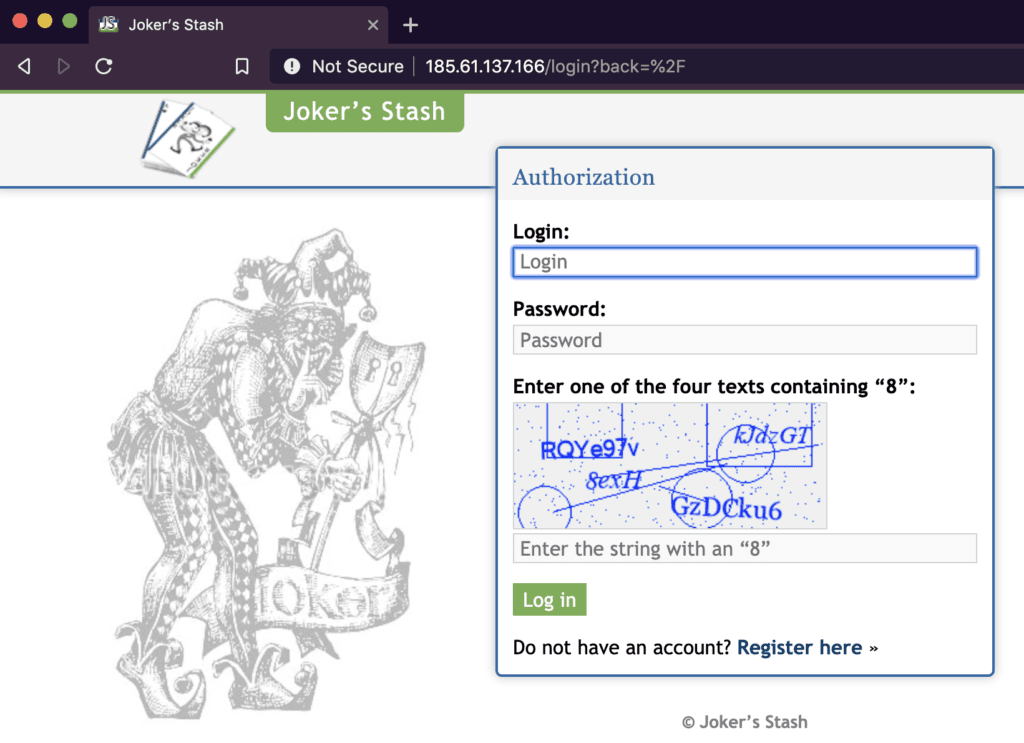
Attempting to access the Joker’s Stash server via normal DNS on September 25, 2019.
The servers 185.61.138.182 and 185.61.137.166 provided two unusual qualities for pivoting. Certificate pivoting identified four additional IP addresses on the same CIDR range, 185.61.137.0/24, which made use of the same TLS certificate serial numbers as the servers mentioned above. Additionally, all of the IP addresses shared an HTTPS title: “Joker’s Favorite CAPTCHA.” Pivoting through Shodan, Binary Edge, and Censys data revealed 54 servers that shared the same HTTPS title, headers, and landing page. These IP addresses can be found in Appendix A, while sample headers can be found in Appendix B.
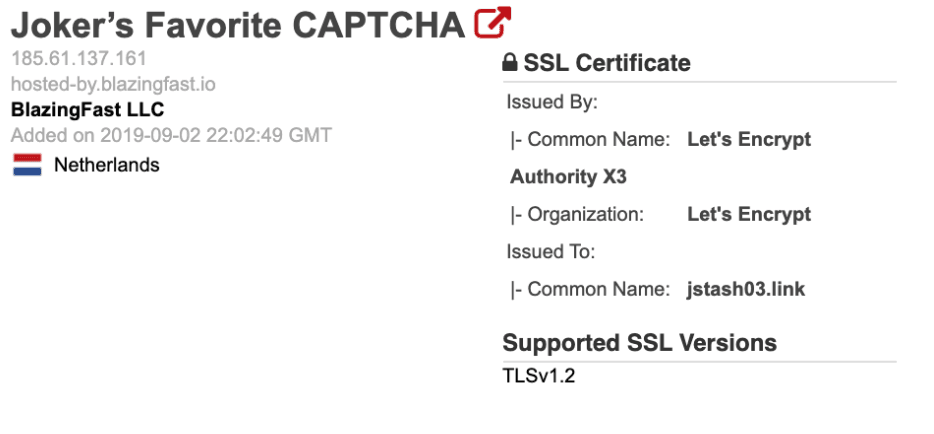
Joker’s Stash server header example, via Shodan.
Using Reverse-IP Lookups and WHOIS pivots identified a total of 543 domains. The domains used a similar naming convention: [English-word1]-[English-word2]-[English-word3].[tld]. It should be noted that these domains are not malicious, in the manner of delivering malware or phishing visitors. Domains of this nature have been previously reported on by Brian Krebs; the domains act as portals for Joker’s Stash’s biggest clients to have dedicated servers to purchase, store, and retrieve cards of interest. Insikt Group verified the connection by making test transactions on the domains, which were reflected in test account balance on the flagship shop. The majority of the domains were hosted on the following IP addresses:
179.43.169.17
185.82.200.250
185.178.211.162
85.25.193.28
85.25.192.57
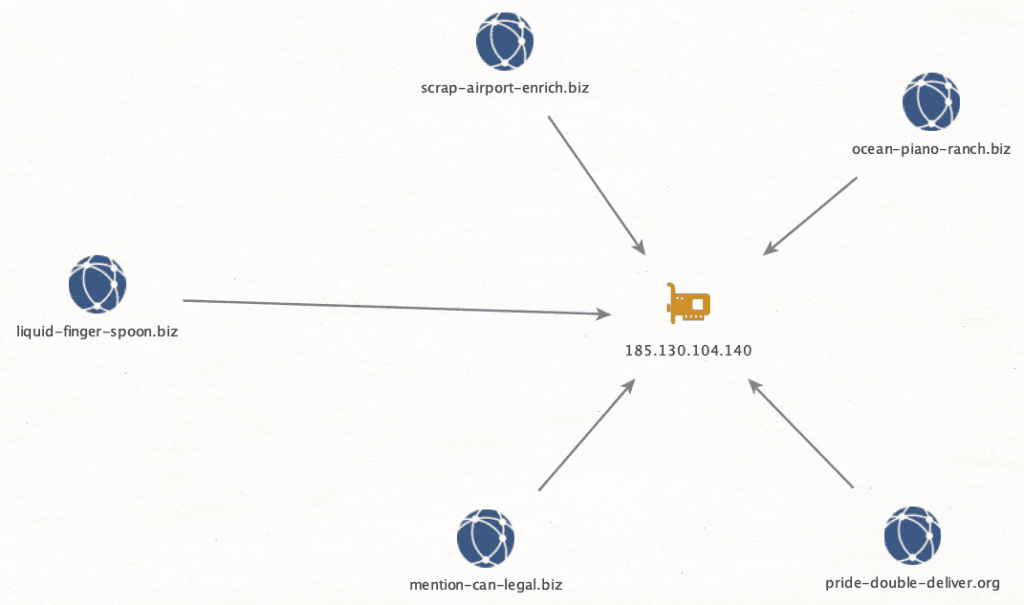
Example cluster of domains to an IP from Joker’s Stash infrastructure.
There are very likely additional domains related to this activity that are not identified in this research. Domains that Recorded Future connected to Joker’s Stash with high confidence are listed in Appendix C.
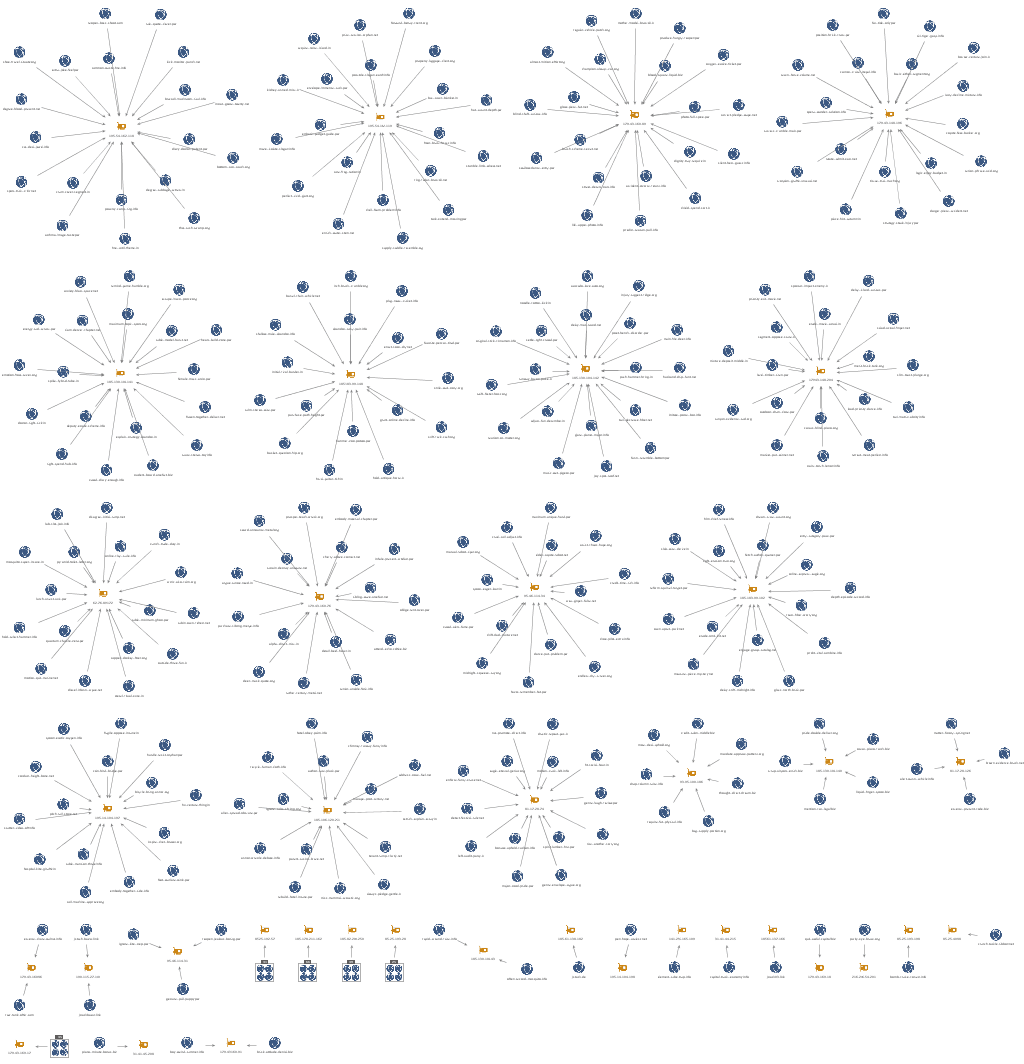
Maltego mapping of Joker’s Stash infrastructure.
Unlike the main Joker’s Stash shop, the domains and servers can be accessed via normal browsers. This allows operators to provide better service for their best customers without other operational security measures. This infrastructure was originally generated to provide confirmed clients with access, while avoiding the assortment of fake Joker’s Stash domains that were created between 2015 and 2016. Notably, connecting to the domains or servers via Tor will load a splash page, telling users to use a normal browser to access the page via clearnet. This likely is to block known Tor exit nodes, as lists are commonly propagated.
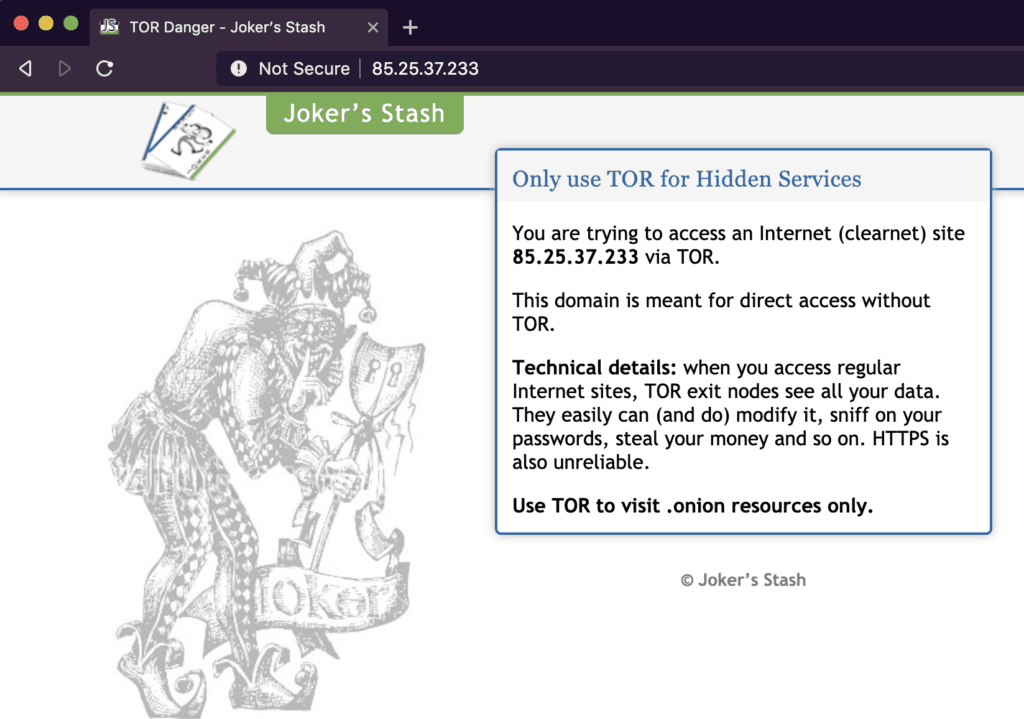
Tor warning from the Joker’s Stash server on September 25, 2019.
464 of the domains returned the same “511 Network Authentication Required” error code as the servers mentioned above. Web pages that did resolve rendered the same “Joker’s Favorite CAPTCHA” page; however, they did not grant access to normal Joker’s Stash credentials. This implies that they are used for the specific clientele.
Historical hosting data of these domains identified 176 unique servers; Recorded Future assesses a large portion of these to be low confidence, from registrars parking the domains to interim hosting. This data may provide value for future correlation, but currently are not part of the Joker’s Stash infrastructure.
Another element of the infrastructure analysis is looking at a time analysis on domain registration dates. Taking a look at all domains identified via this method, analysts plotted the domain registration date over time, as highlighted below in the “Domain Registrations Over Time” (DROT) graph. Based on our findings, spikes in activity occurred in 2015 and 2017, which correlate with approximate dates of major breaches. Many of these domains have been reactivated in 2019 for ongoing use.
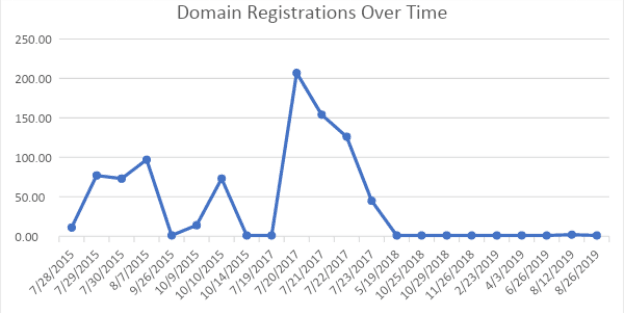
DROT graph for domains connected to Joker’s Stash.
The reuse of these domains shows that the carding customer base fluctuates around large breaches. For example, a large number of these domains were registered in 2017, preceding the disclosure of the Sonic and Jason’s Deli breaches, as well as other major payment card breaches. Joker’s Stash typically promotes the release of new payment cards from a fresh breach well ahead of time, and may similarly be expected to improve infrastructure in anticipation of these releases. Insikt Group believes with high confidence that a number of domains were reactivated in 2019 surrounding Joker’s Stash acquisition of the Hy-Vee breach data. Insikt Group theorizes that this infrastructure is spun up in anticipation of customer engagements around bigger breaches. Examples of these domains can be seen below.
| canoe-hill-face[.]com | sustain-swim-robot[.]in | evidence-way-certain[.]org |
| eternal-seek-banner[.]com | wonder-abuse-sure[.]org | crater-wait-hazard[.]org |
| hope-two-upper[.]com | tower-project-unusual[.]org | rug-property-slogan[.]net |
| spawn-mind-arrest[.]com | taxi-van-rich[.]org | profit-minor-dash[.]net |
| swarm-upset-voyage[.]com | stick-inject-organ[.]org | near-pulse-blur[.]in |
| warfare-firm-aware[.]info | moon-joy-drum[.]org | better-electric-rabbit[.]in |
| time-demise-picnic[.]pw | month-three-manual[.]org | lobster-rival-mix[.]info |
Outlook
Joker’s Stash’s expansion of SSN records has cemented it as an enduring threat to retailers, hospitality entities, and consumers, making the detection of fraudulent transactions all the more difficult. Recorded Future believes Joker’s Stash will remain a substantial risk due to the ease of use and monetization of stolen payment card data. Additionally, the volume of infrastructure created for clients that purchase large amounts of data from Joker’s Stash indicates a large client base. Moreover, the inclusion of PII records likely promotes the expansion of carding to lower-tier criminals, as it will make it easier for less sophisticated individuals to circumvent anti-fraud measures.
The ready and inexpensive availability of seemingly accurate personal data on Joker’s Stash can be even more damaging to individuals than the loss of payment card data. Once a person’s PII is out, it is much harder to mitigate than simply issuing a new card, and the fraud may follow the victim for years to come since information such as Social Security number, mother’s maiden name, date of birth, place of birth, and so on is much harder to change or replace as verification methods.
Recommendations
Social Security information, banking credentials, and payment cards should be closely monitored for fraudulent activity. While protections offered by major banks and credit card vendors are very good at identifying fraud, Recorded Future recommends continued review and auditing of payment card and banking transactions, like setting up notifications for all card-not-present transactions. Insikt Group recommends continuing to monitor the Joker’s Stash infrastructure listed in the associated appendices for new IP addresses and domains, to understand the ebbs and flows of the store’s operators and clients.
Recorded Future believes that network administrators should monitor for the domains and IP addresses listed in Appendices A and C, as they may indicate that a user in the network is involved in some sort of fraud.
To view a full list of the associated indicators of compromise, download the appendix.
Related
