Joker’s Stash Breaches Dickey’s Barbecue Pit
This blog post, initially published on the Gemini Advisory Blog, has been formally migrated to Recorded Future to ensure its continued exploration and insight.
Key Findings
- The Joker’s Stash dark web marketplace, known for advertising and uploading major breaches containing millions of compromised cards, has uploaded its latest breach, titled “BLAZINGSUN.”
- Gemini Advisory determined that the compromised point of purchase (CPP) was Dickey’s Barbecue Pit, a US-based restaurant franchise.
- Dickey’s operates on a franchise model, which often allows each location to dictate the type of point-of-sale (POS) device and processors that they utilize. However, given the widespread nature of the breach, the exposure may be linked to a breach of the single central processor, which was leveraged by over a quarter of all Dickey’s locations.
- Gemini sources have also determined that the payment transactions were processed via the outdated magstripe method, which is prone to malware attacks. This represents a broader challenge for the industry, and Dickey’s may become the latest cautionary tale of facing lawsuits in addition to financial damage from cybersecurity attacks.
Background
The Joker’s Stash dark web marketplace, known for advertising and uploading major breaches containing millions of compromised cards, has uploaded its latest breach, titled “BLAZINGSUN.” The marketplace’s administrator, who operates under the moniker “JokerStash,” originally claimed that this breach would be available in August, then again in September, before finally announcing that it would appear on October 12. The advertisement claimed that BLAZINGSUN would contain 3 million compromised cards with both track 1 and track 2 data. They purportedly came from 35 US states and “some” countries across Europe and Asia.
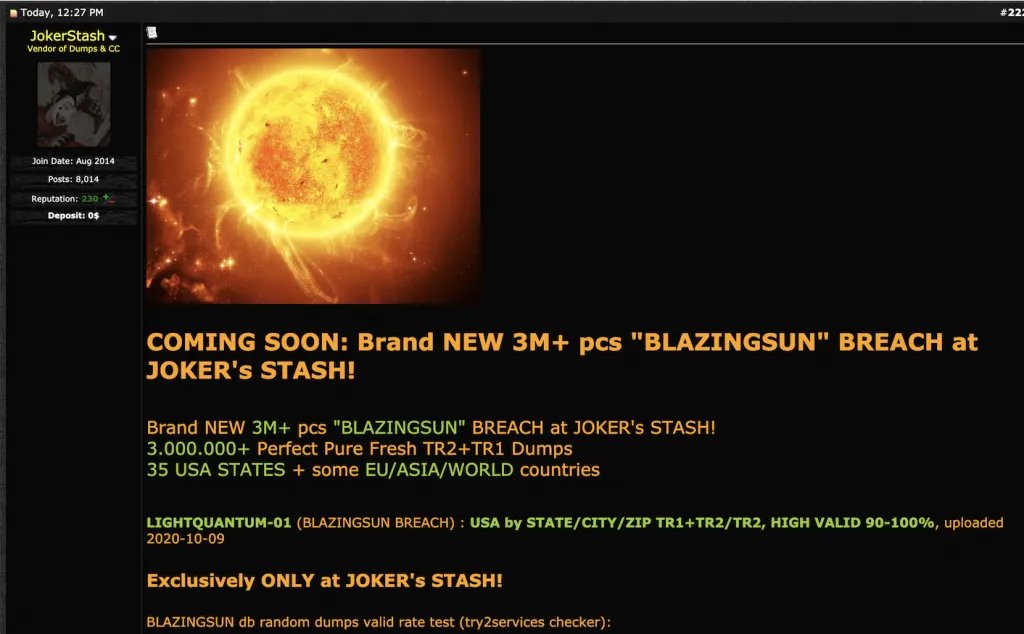
Image 1: JokerStash advertises the BLAZINGSUN breach.
In-Depth Analysis
The breach was uploaded on October 12. Gemini Advisory determined that the compromised point of purchase (CPP) was Dickey’s Barbecue Pit, a US-based restaurant franchise with 469 locations (411 of which are currently open) across 42 states. Further Gemini analysis indicated that 156 of these locations across 30 states have been compromised, with the highest exposure in California and Arizona. The exposure window appears to be between July 2019 and August 2020.
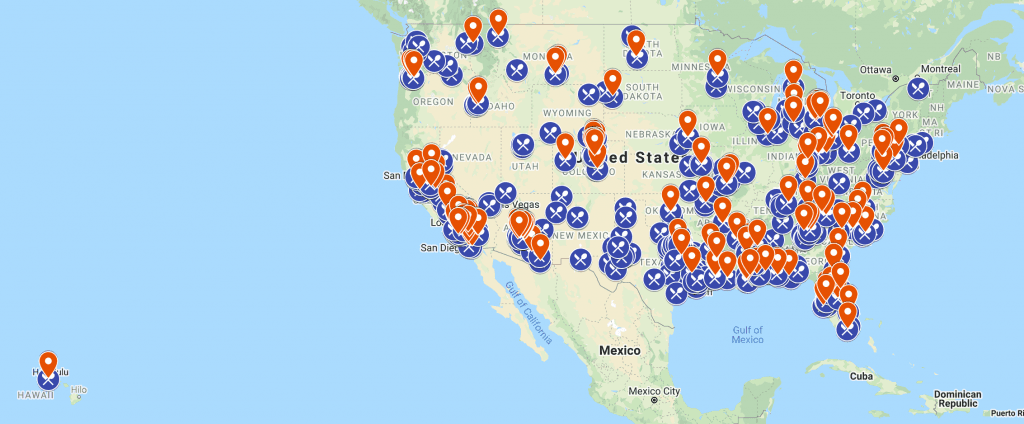
Image 2: Dickey’s locations are marked by the blue restaurant icon while the locations confirmed to be compromised are marked in red.
Dickey’s operates on a franchise model, which often allows each location to dictate the type of point-of-sale (POS) device and processors that they utilize. However, given the widespread nature of the breach, the exposure may be linked to a breach of the single central processor, which was leveraged by over a quarter of all Dickey’s locations. The current exposure by location does not exactly align with the restaurant’s distribution across states, although with the exception of Texas, which hosts 123 restaurant locations but only three compromised locations, the exposure is approximately reflective of the overall distribution.
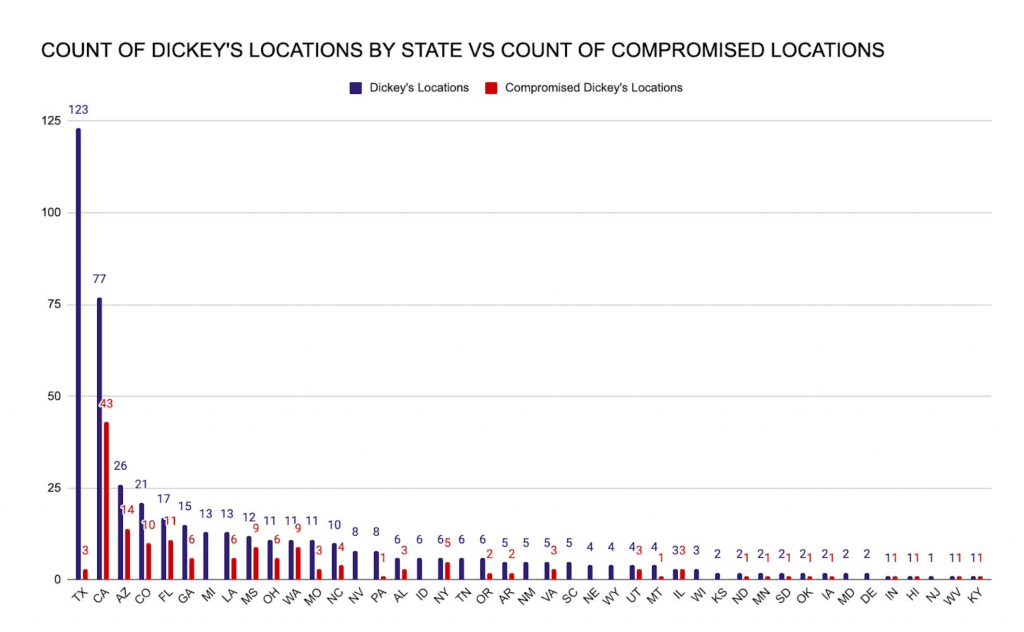
Image 3: The number of Dickey’s locations (including those currently closed) per state compared to the number compromised per state.
Dickey’s experienced a ransomware attack in 2015 with a $6,000 extortion demand. In January 2018, the restaurant franchise published an article detailing this incident and committing Dickey’s to a robust cybersecurity posture. The article, complete with security best practices and an endorsement of investing in proactive measures, featured quotes from then-CEO Laura Rea Dickey. However, this BLAZINGSUN breach purports to contain 3 million compromised payment records with a median price of $17 per card. Despite the restaurant’s emphasis on security, this new breach dwarfs the scale of the 2015 ransomware incident.
Conclusion
Based on previous Joker’s Stash major breaches, the records from Dickey’s will likely continue to be added to this marketplace over several months. Joker’s Stash’s largest breach this year compromised records from the convenience store and gas station chain Wawa. The marketplace advertised this breach as containing 30 million records, and as of this writing, it continues to add compromised cards. Since the breach first appeared in January 2020 and continues to add records 10 months later, the BLAZINGSUN breach may follow a similar timeline of several months.
Gemini sources have also determined that the payment transactions were processed via the outdated magstripe method, which is prone to malware attacks. It remains unclear if the affected restaurants were using outdated terminals or if the EMV terminals were misconfigured; either of these possibilities may hold serious liability for Dickey’s. Wendy’s and Hy-Vee, for example, have faced lawsuits over similar accusations of outdated or lax security postures. This represents a broader challenge for the industry, and Dickey’s may become the latest cautionary tale of legal woes adding to financial damage from cybersecurity attacks.
Related
