Despite Infighting and Volatility, Iran Maintains Aggressive Cyber Operations Structure

Editor’s Note: The following post is an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
Recorded Future’s Insikt Group® is conducting ongoing research on the organizations involved in Iran’s cyber program. This report serves to provide greater insight into the major military and intelligence bodies involved in Iran’s offensive cyber program. Although offensive cyber capabilities include domestic attacks, we researched those organizations with declared international missions. Due to the secretive nature of some organizations and lack of verifiable information, we incorporated competing hypotheses to adhere to industry analytic standards.
For the purposes of this research, we investigated the Islamic Revolutionary Guard Corps (IRGC), including the Basij, as well as the Ministry of Intelligence and Security (MOIS), and the Ministry of Defense and Armed Force Logistics (MODAFL). Although the report suggests links between a select number of advanced persistent threat (APT) groups and certain intelligence organizations, we are unable to conclusively assign them to specific agencies due to gaps in information about each group.
The sources for our research primarily include intelligence surfaced in the Recorded Future® Platform, industry research released by Symantec, FireEye, ClearSky, and PaloAlto, among others, and open source news reports.
Executive Summary
While the Iranian cyber program remains at the forefront of Tehran’s asymmetric capabilities, its intelligence apparatus is colored by various dysfunctions and seemingly destabilizing traits. In particular, the politicization of its various intelligence agencies and ensuing domestic feuds have reportedly polarized officer-level rank and file throughout the various security crises of the Islamic Republic. These crises have surfaced publicly and have acted as catalysts to drive insider threats, have lowered intelligence morale, and have increased the occurrences of leaks. Competition between the intelligence groups has also allegedly led to direct acts of sabotage between agencies.
Amid the political infighting, certain organizations have experienced significant expansions in security powers which undoubtedly includes leveraging offensive hacking tactics, techniques, and procedures (TTPs) to further their intrusions and access to victims. First among those is the Islamic Revolutionary Guard Corps — Intelligence Organization (IRGC-IO). The entity’s mission has grown significantly in the last decade, so much so that it is capable of operating in direct contravention to the intelligence assessments and advice of the Islamic Republic’s constitutionally mandated intelligence agency, the Ministry of Intelligence and Security (MOIS).
This is Recorded Future’s third report on Iran’s cyber program. In January 2019, we reported on Iran’s best-known hacker forum, Ashiyane, and in March 2019, we released a report that covered Iran’s cyber defense structure and associated organizations.
Key Judgments
- We assess that although there is a differentiation between Iranian agencies that execute internal and external operations, the undefined (and at times overlapping) security missions of each intelligence agency likely complicates efforts to conduct cyber-related attribution.
- We assess that the potential for disinformation by Iranian and extra-regional actors is likely to remain elevated as a result of the volatility in the intelligence establishment and overlapping responsibilities.
- Owing to the complex nature of the Iranian intelligence establishment, history of leaks, and politicization, we assess that Iran’s security sphere likely remains volatile.
- Aggressive, ideologically motivated cyberattacks bear the traits of the IRGC, and in particular, its overseas operations command, the Quds Force. We assess the organization is likely to have coordinated destructive operations as part of Iran’s asymmetric response capability.
- We assess that tertiary academic institutions, such as the Imam Hossein University, are highly likely to continue to assist the Iranian cyber program and enhance the capabilities of regime-aligned operators.
- We assess that Iran-based, specialized contracting groups are likely to service various government and military entities. Contracting groups are also likely to cater to agency-specific tasking depending on the threat and target of opportunity.
Background
Iran’s intelligence and military-led cyber operations are influenced by a variety of factors: the complex nature of the intelligence establishment, overlapping mission sets, the rulings and interests of Supreme Leader Ali Khamenei, the influence of military organizations such as the Islamic Revolutionary Guard Corps (IRGC), and internecine politics.
The Iranian Intelligence Establishment
According to Iran’s Fars News Agency, the Iranian intelligence establishment has grown since the 1979 Islamic Revolution to include at least 16 separate bodies that conduct intelligence activities. The Fars report also highlighted the role of the Council for Intelligence Coordination (Shorai-e Hamohangi Etelaat) which purportedly acts as the principle mechanism to unite all intelligence entities to coordinate efforts against a variety of domestic and international security threats.
Iranian intelligence agencies are either components of the IRGC organization, or like the Ministry of Intelligence and Security (MOIS), belong to the varying components of Iran’s elected government. These entities, however, are all subordinate to the edicts of Supreme Leader Khamenei; some, such as the Islamic Revolutionary Guard Corps — Intelligence Organization (IRGC-IO) are assessed to adhere to Khamenei’s interests more directly than others. MOIS, which is currently led by Mahmoud Alavi, officially leads MOIS’s intelligence mission in coordination with the priorities of the elected government.
Characteristics of Iranian intelligence include overlapping tasking, targeting requirements, and operational responsibilities, which in some cases lead to competition for, or a convergence of, intelligence and military resources. For example, as discussed below, combating domestic subversion is not only reportedly executed by MOIS, but also the IRGC-IO, as well as other agencies such as Iran’s Cyber Police (FATA).
Internationally, both MOIS and the IRGC have been reported to lead independent intelligence operations, as well as cooperate in operations against national security threats. Such overlaps, in certain cases, complicate kinetic and cyber attribution efforts. Other intelligence operations, such as those cited in a February 2019 U.S. Department of Justice (U.S. DOJ) indictment against various Iranian cyber operatives, suggests that resources are shared between agencies, and operatives are likely to provide services to more than one element associated with Iranian security services.
Overlapping Cyber Missions
The attribution of cyber campaigns and incidents in many cases reveal the plausible strategic and tactical interests of two, if not more, intelligence organizations of the Islamic Republic. The MOIS and the IRGC remain the most pertinent entities with overlapping intelligence and security missions. APT groups also respond to the tasking requirements of both organizations, and as we highlight below, to specific sub-groups. While technical attribution is conducted by Recorded Future and the broader industry, without access to information on the composition of APT groups, including personnel and their networks’ affiliations, APT attribution to specific organizations becomes more complex. Attribution necessitates the aggregation of multiple technical, organizational, and personal behavioral data sets, to enable more precise attribution.
Like other nations, strategic and tactical information is key for Iranian agencies. Political, military, and economic information is a major driver for international cyberespionage operations, including against officials from various Western and Middle Eastern governments. These operations have historically occurred during periods of elevated tensions between Tehran and the international community. Within this international area of operations, various threat actor groups have continued to support not only MOIS and the IRGC’s requirements, but those of a range of government stakeholders and academic institutions, including research and development organizations associated with the Ministry of Defense and Armed Force Logistics (MODAFL).
Public reporting reveals that known Iranian threat actors have also led operations against Middle Eastern states, at times coordinating and collaborating against specific targets as part of broad computer network attack operations. Most recently this included the use of the ZeroCleare destructive malware against Bahrain. However, destructive attacks have been part of Iran’s asymmetric response and attack capability since at least August 2012. In mid-December 2018, the Italian petrochemical giant, SAIPEM, was targeted, likely by pro-Iranian government actors, using an updated variant of the Shamoon(2) (Disttrack) malware. The December 2018 attack was accompanied shortly thereafter by hacktivist-style defacements and social media-based information operations executed by entities claiming to represent the Yemen Cyber Army, a collective supporting the interest of and aligned with the Houthi movement (Ansar Allah). The collaborative effort highlights the potential for mission coordination and shared resources in offensive efforts, by potentially diversified threat actor groups.
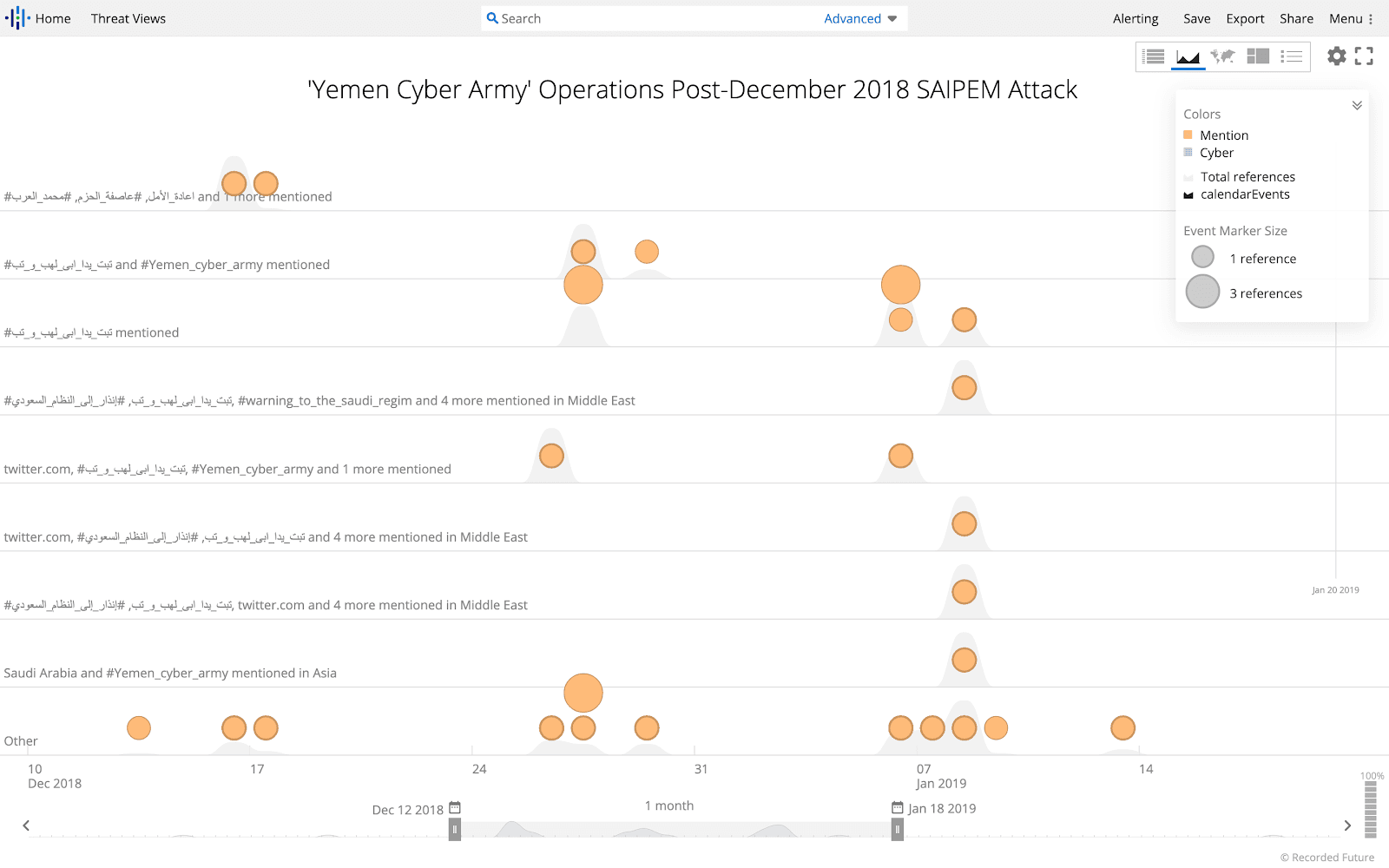
Recorded Future query on some of the Yemen Cyber Army’s social media operations.

Imagery that accompanied the Yemen Cyber Army’s social media operations listed SAIPEM, among other companies.
On the domestic front, the intelligence and security establishment, including FATA, combats a wide range of anti-regime political, militia, and extremist movements. The state’s security services have been recorded conducting kinetic and cyber operations against religious minorities as well as Kurdish, Ahwazi-Arab, and Balochi ethnic separatists. For example, the threat actor group referred to as Domestic Kitten by Check Point reportedly ran an extensive cyber surveillance campaign specifically targeting dissidents, extremist groups, and ethnic minorities inside and outside of Iran. This group reportedly ran most of its operations against Farsi-, Arabic-, Turkish-, and Kurdish-speaking targets, using social engineering to trick victims into downloading malicious mobile applications.
In FATA’s case, it too has reached beyond its purported legal mandate of countering cybercriminal activity and has targeted Iranian bloggers, such as Sattar Beheshti. We note that within the operational scope of Iranian cybercrime matters, and Iran’s Computer Crimes Law specifically, the definition of a cybercriminal has practically manifested to include political activists that are caught disseminating anti-regime material or participating in online protests. Industry research has detailed various cases where political activists have been arrested and imprisoned under the Computer Crimes Law, and the flexibility embedded in such legislation to enable law enforcement entities to apply it at their discretion. As such, FATA’s operations are highly likely linked to the government’s crackdown on bloggers and activists that transpired following the 2009 Green Movement uprisings, but are likely to be limited to domestic security.
Iran’s anti-dissident operations are also devoid of national boundaries, as Iranian cyber groups, such as APT35 (Charming Kitten), which has predominantly serviced the IRGC, and Flying Kitten have both demonstrated a penchant for targeting the Iranian diaspora throughout Europe and North America.
Military-related technologies, including software, also remain a top priority for a system that professes to be self-sufficient and strives to build and export its defense industry. As we expand on later in this report, entities such as MODAFL are assessed to be leading stakeholders and benefactors of computer network operations focusing on military armaments technology.
Iranian Intelligence Leaks
Leaks have regularly impacted Iranian intelligence, in particular the MOIS. Throughout its history, the organization has endured multiple bouts of high-impact disclosures that have threatened to expose the system’s high-ranking members and its international operations; significant cases include the “Chain Murders,” the “Iran Cables,” and to a lesser extent, various uncorroborated cyber leaks associated with anti-government operations. Political grievances have driven major leaks against intelligence agencies. These depict violations against fellow intelligence officers and Iranian society, corruption and cover-ups, or as the most recent Iran Cables suggests, MOIS’s disdain of the IRGC-Quds Force’s intelligence and military primacy and practices in Iraq.
Anti-government cyber operations predominantly materialized in the years following the 2009 Green Movement uprising and were conducted by self-declared anti-government anonymous collectives, such as Anonymous Iran. These groups aimed to expose Tehran’s cyber efforts against its civilians and international targets, and have resulted in the disclosures of allegedly confidential documents, cyber projects, corruption in the Iranian government, and international operations against Middle Eastern countries. The most recent uptick in anti-government cyber operations began near the end of 2017 until the time of writing, with various groups such as Tapandegan, Lab Dookhtegan, and Aahack Security Team reportedly leading intrusions against government and military assets.
Suspected Disinformation Efforts
Our investigations on Iranian disinformation continue to identify plausible cases of misdirection, and as such, at the time of this writing, we assess the potential for disinformation by Iranian actors is likely to remain elevated in the future. This is further amplified by leaks and the potential that extra-regional actors manipulate leaked data, or degrade data categorization and attribution, to service their interests against Western cybersecurity organizations. The latter, for example, includes the use of pre-existing C2s to obfuscate an extra-regional threat actor’s own operations.
Since late 2017 and throughout 2019, self-declared Iranian dissident entities have pursued comprehensive efforts to expose the Iranian intelligence and military establishments’ operations in Iran and throughout the Middle Eastern region. These efforts included groups such as Lab Dookhtegan, the “Green Leakers” (Afshagaran-e Sabz), “Black Box” (Resaneh Khabari Jabeh Siah), and “Hidden Reality” (Vaghiyate Penhaan). The latter reported on the activities of an alleged contractor, the Rana Institute, which we discuss in greater detail below. As of this writing, Insikt Group has not comprehensively corroborated all the information and missions these groups claim to uphold against the Islamic Republic. While these entities purport to act against Tehran, and have disseminated extensive information against an APT group as well as Iranian intelligence, we assess it is also possible that one or more of these groups was established with the objective of executing disinformation.
Kaspersky Labs published two reports in August and December 2019 possibly linking Russian threat actors with the Rana Institute leak. Based on an analysis of the leaked materials, the infrastructure, and the dedicated website, the reports assessed that threat actors associated with the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU) were behind the link. However, at the time of this writing, Recorded Future cannot confirm the validity of this assessment.
In another case, Recorded Future reported on the alleged death of a senior member of Iran’s cyber program, Mohammad Hussein Tajik, which was covered in reporting on Iran’s hacker hierarchy and disinformation efforts surrounding the IRGC-IO’s capture of dissident Ruhollah Zam. As of this writing, the information disseminated about Iran’s cyber program to dissidents like Zam has not been corroborated. Zam has repeatedly been the subject of character defamation attacks, as well as being outed by Iranian intelligence as being a victim of their intelligence operations. We assess such activities were presumably undertaken to degrade Zam, and the confidence placed on his sources and methods. Zam’s reporting on Tajik implicated Iran in international cyber operations against the U.S., Saudi Arabia, and Turkey, and also linked it to an operational facility, the Khaybar Center, from where those attacks were allegedly launched. This facility, according to Zam’s accounts, operates like a fusion center with members from Iran’s major intelligence group’s present onsite.
While disinformation efforts emanating from Iran remain a credible threat, we assess that extra-regional actors could also be attempting to misdirect detection and attribution efforts by impersonating Iranian APT groups. We assess this may include using server infrastructure (C2) previously affiliated with Iranian threat actors, such as APT33, APT35, and MuddyWater. We highlighted this as a possible scenario in our December 2019 Operation Gamework report that revealed C2 and malware overlaps with Russian APT BlueAlpha.
Politicizing the Intelligence Establishment
Due to the Iranian intelligence establishment’s history of leaks, and periods of increased politicization and factionalism, we assess that Iran’s security sphere likely remains volatile.
Farsi-language open source reporting highlights how Iran’s MOIS has experienced increased levels of factionalism, which has likely harmed the agency’s ability to secure its scope. Public reporting further indicates that internecine politics has affected multiple layers of the intelligence establishment, pitting the head of the IRGC-IO Hossein Taeb against former MOIS leader Heydar Moslehi and various politicians, including former president Mahmoud Ahmadinejad (2005-2013) and Sadeq Larijani. The IRGC-IO leader is reported to have backed intelligence operations against Iranian political groups that had compromising evidence against the IRGC that specifically depicted cases of corruption.
Under former president Mohammad Khatami (1997-2005), MOIS is purported to have undergone a cull of hardline officers and supporters, which ultimately led to the agency’s retreat from pursuing aggressive international operations and its moderation.1 Between 1997 and 1998, Supreme Leader Khamenei is reported to have promoted the IRGC’s intelligence mission to that of a directorate. From that point on, the IRGC’s Intelligence directorate commenced executing similar duties to those of MOIS, which we believe contributed to the overlapping efforts to address national security threats.
Under former president Ahmadinejad, MOIS reportedly experienced further instability after the 2009 uprising, with IRGC-led purges against MOIS officers. Public reports also cite how Ahmadinejad attempted to leverage MOIS to accrue kompromat (“compromising material”) against political rivals. Hardliner intentions to undo the Iranian reformism led by Khatami and his predecessor Rafsanjani were accurately captured in an early declaration, “The New Era and Our Responsibilities” (dowlat-e jadid va masooliat-haye ma), authored by leading members of Iran’s hardline and pro-IRGC Ansar Hezbollah. The declaration issued a warning and demanded that the first government of Ahmadinejad prevent MOIS’s continued drift toward Khatami-era changes, and presumably, an Iranian intelligence service less likely to execute ideologically motivated international operations.
MOIS has experienced similar instances of politicization under current President Hassan Rohani (2013-present). Iran’s Intelligence Minister, Mahmoud Alavi, has been blamed for lacking intelligence and security credentials, and has subsequently been the target of politically-motivated attacks instigated by hardline elements. Similar to the Khatami presidency, Rohani commenced his term with a reform-minded agenda, which included moderating MOIS and making it more accountable. Reporting from the BBC suggests Rohani has used the agency in anti-corruption cases, which has further entrenched it in a political dogfight to evict the IRGC and its supporters from commandeering sectors of the Iranian economy.
According to a BBC report, MOIS, on at least three separate occasions, has been outmaneuvered and its rulings rejected by the parallel activities and clout of the IRGC-IO. These reportedly included arresting managers of pro-reformist Telegram Channels, the arrest of members of Rohani’s Joint Comprehensive Plan of Action (JCPOA) negotiations team on espionage charges, and the arrest of environmental activists. Under Rohani, MOIS is reported to have continued to lose its powers to the IRGC-IO within the national security sphere, in particular within the counterintelligence and counter domestic subversion domains.
Impact on the Iranian Cyber Cadre
The increased level of factionalism in the Iranian intelligence establishment is likely to have impacted Iran’s cyber forces. Insikt Group assesses the direct results of the political infighting is likely to have trickled down to Iranian cyber operators, which to date publicly support one side or another (MOIS or the IRGC).
Social media chatter, for example, has shed light on the disagreements and taunts between Iran-based cyber operators supporting the IRGC, such as Armin Rad (also known as “Ayoub Tightiz”) and Mohammad Jorjandi, who has often criticized Rad and his support base.2 Additionally, according to Jorjandi, who is reportedly based in the U.S., as of this writing, the hack and leak operations tied to Lab Dookhtegan are allegedly borne out of the competition between the MOIS and the IRGC, where the latter has purposefully leaked information about MOIS to damage its reputation and standing.
Although we can not corroborate Jorjandi’s statements, the alleged targeting of MOIS as depicted by Lab Dookhtegan has included members of APT34, such as Yashar Shahinzadeh. Our observations of Shahinzadeh’s social media chatter suggest he has sided against pro-IRGC regime hackers like Rad, and has attempted to assist members of the elected government, in particular the Minister of Information and Communications Technology, Mohammad Javad Jahromi. This assistance has predominantly centered on detecting vulnerable government databases.
Outlook
Iran’s cyber actors are uniquely placed to continue to deflect attribution attempts, primarily due to the increasing number of actors catering to Iran’s different intelligence centers. Whether the IRGC-IO, the Quds Force, MODAFL, or MOIS, the entities remain at the forefront of Iranian cyber capabilities, and are able to lead international attacks. Public information also points to these entities using a community of contractors to pursue their intelligence targets, and we assess this to remain a significant characteristic of Iran’s cyber ecosystem in the future.
With a more skilled cyber cadre, more effective tooling, and more robust operational security measures, including the ability to produce and distribute disinformation, Iranian cyber operations are likely to continue to swiftly target Middle Eastern nations and the international community as a whole. Iran’s security services will also highly likely continue to target Iran’s diaspora and ethnic minority communities, both of which pose a threat to Tehran’s perceived domestic stability.
Mitigations
- Interested stakeholders should leverage structured analytic techniques, such as red hat analysis and deception detection, to aid in more refined attribution attempts, while also mitigating disinformation efforts by cyber adversaries.
- Remain abreast of political developments in Iran to observe activities that impact the intelligence landscape (such as corruption scandals, power struggles, arrests of journalists and activists, reshuffling leaders of intelligence groups, use of foreign technologies, prohibition of the use of social media, and so on).
- Farsi-language dissident reporting regularly covers activities pertinent to crackdowns against minority groups, protestors, and arrests of foreign and dual nationals. These sources also usually provide insight into the intelligence and military organizations involved in the arrests and their claimed motives.
- Iranian cyber operators maintain a relatively public presence on Instagram and Telegram. These public sources may provide insight into the organizational developments, training, political insight, and their operational network.
- To prevent and mitigate disinformation efforts, we recommend verifying and corroborating Iranian cyber developments sourced from social media and publicly-available messaging platforms.
- Campaign tracking of Iranian APT groups will not only provide insight on the TTPs, but also the victimology, which serves to deepen understanding about organizational interests.
Editor’s Note: This post was an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
Footnotes
1S. Chubin, Wither Iran?: Reform, Domestic Politics and National Security, New York, Oxford University Press, 2002, P. 91.
2https[:]//www.tabnak[.]ir/fa/news/816849
Related
