Guest Post: Voices in the Static – Proactive Cyber Threat Monitoring
Guest author: Ken Buckler is a professional cyber security consultant. He maintains a blog called “Caffeine Security” and provides a free Cyber Threat Watch page to keep his readers informed of the current state of the cyber security realm as well as major upcoming threats.
Your network is under attack. Right now. This very moment your public facing IP address space is being scanned and probed by someone. In fact, the entire Internet is being scanned by so many malicious attackers on a 24/7 basis that the most amount of time an unprotected computer can hope to last on the Internet without being compromised is seven minutes according to SANS. Scans and attacks have become so prevalent on the open Internet that many are now considered “background noise” and dropped by most organizations’ border firewalls without any logging whatsoever.
Cyber security has become so complex that it requires trying to account for the most likely causes of security incidents and planning/mitigating those causes first. But as a cyber security professional how can you possibly hope to know which threats are most likely to affect your organization? Are you waiting for major news organizations to report on the latest threats days…sometimes weeks after they occur? Or are you being proactive and watching for threats before they are on the radar. This is where proactive threat monitoring comes into play.
If you’ve done your homework and implemented security best practices – you may think your job is finished…but you work is far from over. The “bad guys” are increasingly clever in their ways, and if they decide that you have data in your network which they want…your job difficulty just increased ten fold.
First of all who are the “bad guys”? A few examples of bad guys could be in order of least to most threatening:
Curious hackers who want to poke around and explore the world of cyber security
Script kiddies looking for a thrill
Spammers looking for new servers to compromise and send spam with
Political activists looking to spread their message through defaced websites
Organized cyber criminals looking for sensitive personal or financial data
Foreign nation-states interested in industrial or military espionage
Disgruntled organization insiders looking for revenge
But back to the topic at hand. A well organized proactive cyber threat monitoring campaign will attempt to answer the following questions: Why? Who? How? Where? and When?
The very first question your organization should ask is: Why? Why would someone want to attack your organization? Are you a political or government entity? Do you have foreign competitors who would be interested in stealing your data? Do you process information which could be used in identity theft? Once you have identified the reasons someone would want to attack your organization you can begin to answer the remaining questions.
For example: Your organization is a major energy company with investments in oil and nuclear energy. Let’s look at a few possible sets of answers.
| Why? | Who? | How? | Where? | When? |
| Oil drilling is sometimes not considered environmentally friendly. | Political hacktivists such as Anonymous | Targeted Denial of Service Attacks or scanning of services looking for unpatched vulnerabilities for defacement or data compromise | Public facing websites and email addresses | Most likely when your company or industry receives a large amount of publicity in the media |
| Industrial Espionage | Foreign Nation States | Targeted spearphishing attacks or scanning of services looking for unpatched vulnerabilities for data compromise | Public facing websites and email addresses for initial reconnaissance and internal network once a foothold has been established | Any time |
| Compromise servers to send spam | Underground spam organizations | Blind scanning of services looking for unpatched vulnerabilities for system access | Public facing websites and mail servers | Any time |
| Revenge | Disgruntled employee | Targeted abuse access to obtain confidential documents or inflict harm against your network | Internal network | Most likely after an employee is terminated or fails to receive a raise or promotion |
So how can a cyber security professional hope to possibly defend against all of these attackers? First of all, only worry about proactive monitoring of threats which specifically target your organization. That immediately removes spammers from the list as their scans are normally blindly pointed at large subnets of the Internet. Spammers will only attempt to compromise the systems with the least amount of resistance – and as long as you’re strictly following other security best practices you should be safe.
Next – only proactively monitor for threats which you can predict and will be visible on the Internet ahead of time. This means that proactive monitoring of the Internet for industrial espionage by foreign nation-states would be futile – as most governments aren’t exactly going to announce their plans to attack over the Internet. However, don’t be surprised if a targeted attack by a foreign nation-state coincides with another type of attack which you can predict! More on this later._
This leaves us with two threat sources we can monitor – political hacktivists and disgruntled insiders. I’d like to take a moment to point out that one of the most important proactive steps a company can do to protect itself from the higher level threats – especially disgruntled organization insiders – is to keep a lookout for internal company documents being posted to the Internet. You can use alerts to detect when internal company documents are found on the Internet – and begin damage control immediately – including requesting removal of the documents and investigating how the documents were leaked onto the Internet in the first place. It is far less damaging to an organization’s reputation if they discover a data leak and begin remediating the problem before it hits the nightly news.
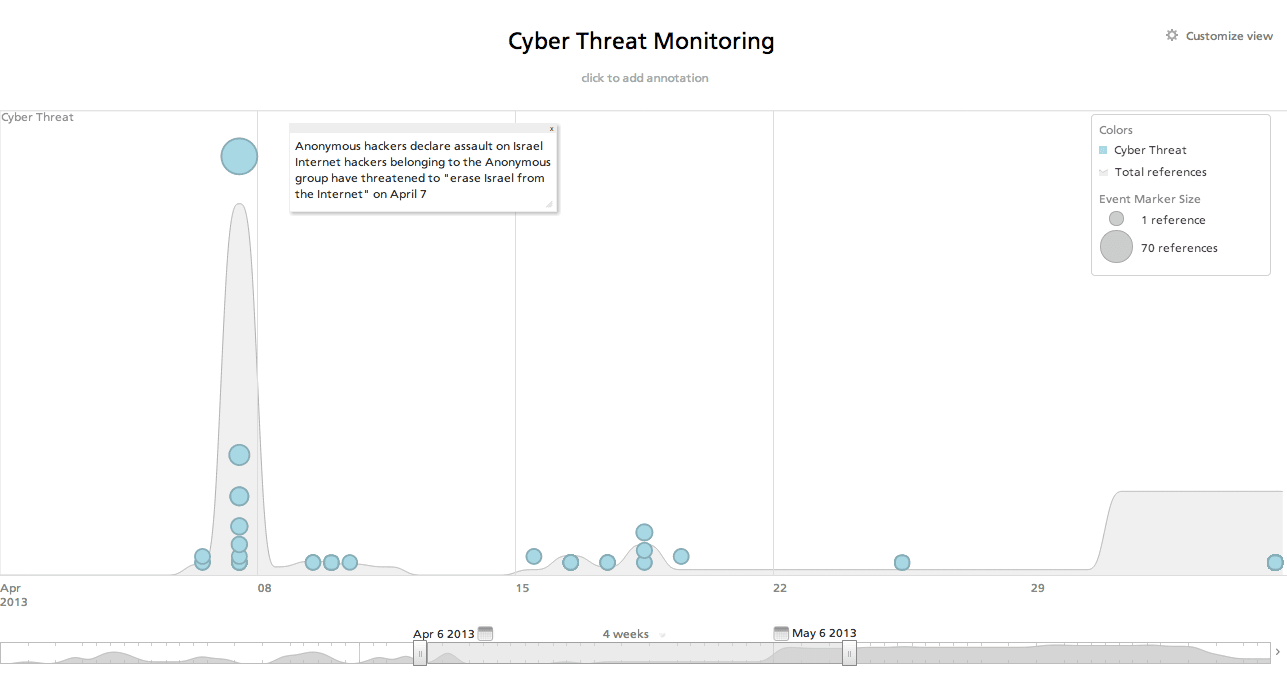
A second means of monitoring political hacktivists is to look for campaigns against your organization. Setting up Google Alerts as well as creating analysis on Recorded Future can typically be used to identify upcoming cyber attacks well before they actually take place. For example, take a look at the Anonymous #OpIsrael campaign analysis. Remember how it was said earlier that attacks by a foreign nation-state may coincide with other attacks? It is becoming common practice to use Denial of Service attacks to mask an infiltration attempt – after all any successful attack will be buried within the denial of service attack logs – most likely never to be found. Given the interesting governmental ties to some of the hacking groups involved in #OpIsrael the Israel government will need to be especially cautious to verify nothing malicious is hidden on their systems during this massive Denial of Service attack. Also…let’s not forget that cyber attacks can sometimes coincide with real-world attacks as the country of Georgia found out in 2008.
Proactive threat monitoring is by no means an end-all solution – and security best practices should continue to be followed by your organization. However…adding proactive threat monitoring to your cyber security toolbox…much like checking the weather report…will help your organization prepare for any upcoming “cyber storms”.
Editor’s note: To see examples of cyber security analysis with Recorded Future, visit Analysis Intelligence. We’ve researched topics ranging from the Shamoon malware attack on Saudi Aramco to Miniduke to forewarned hacktivist campaigns.
Related
