A Look Inside Cloud Computing: Benefits Versus Threats
Cloud computing is the on-demand delivery of IT capabilities in which IT infrastructure and applications are provided to subscribers as a service over a network.
Initially, cloud computing technology was introduced by Amazon in 2006 following the release of Elastic Compute Cloud (EC2), a key element of Amazon Web Services (AWS). Since then, the cloud effectively “conquered the world” due to a wide variety of benefits this technology provides to clients, such as economic (lower maintenance costs and larger storage facilities), operational (flexibility, efficiency, and automatic updates), and staffing (less IT staff required, better usage of shared resources).
To further support these benefits, statistics reveal that this trend will last at least into the near future.
Cloud Computing by the Numbers
Financial results from Amazon illustrate that the company received the largest profit due to AWS, which generated 55 percent of the total operating profit of Amazon in the first quarter of 2018, despite only 12 percent going to the company’s net sales. Similarly, Gartner expects a 17.3 percent growth of the public cloud market services in 2019, totaling $206.2 billion, as shown in the table below.
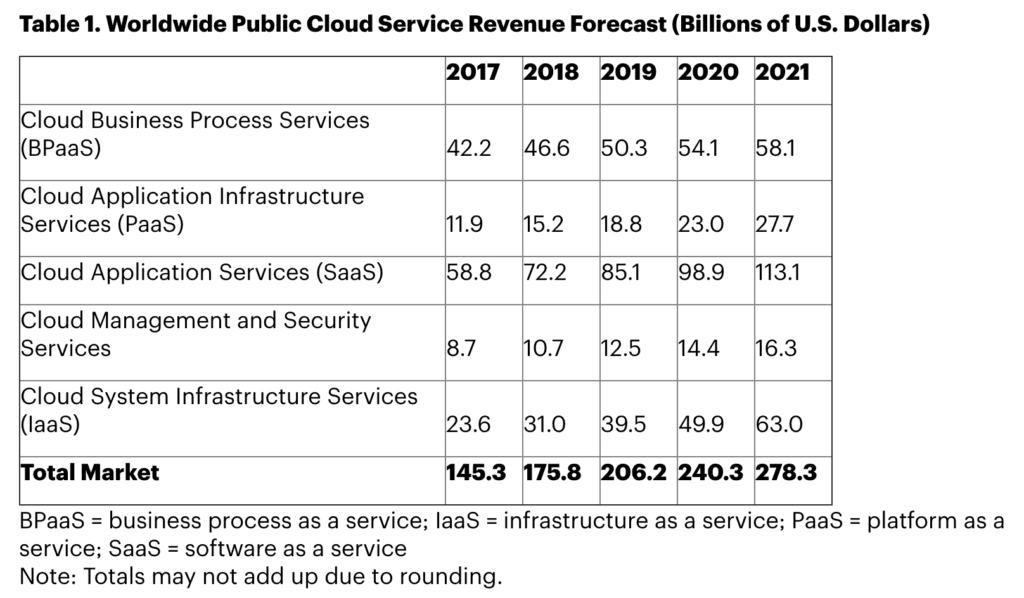
Gartner public cloud revenue forecast from 2017 to 2021. (Source: Gartner)
In addition to the forecast above, according to the IDC FutureScape 2018 prediction, allocations on cloud services and cloud-enabling hardware, software, and services will reach over $530 billion by 2021. Similarly, according to IDG’s 2018 Cloud Computing Survey, 73 percent of organizations have at least one application or some part of their infrastructure in the cloud, and a further 17 percent expect to be at this level within the next 12 months. #### Cloud Computing Service Reference Architecture Unlike traditional business-to-consumer (B2C) relations, the cloud computing service has more complex and diversified architecture and includes the following components, defined by the National Institute of Standards and Technology (NIST):- Cloud Provider
- Cloud Consumer
- Cloud Carrier
- Cloud Auditor
- Cloud Broker
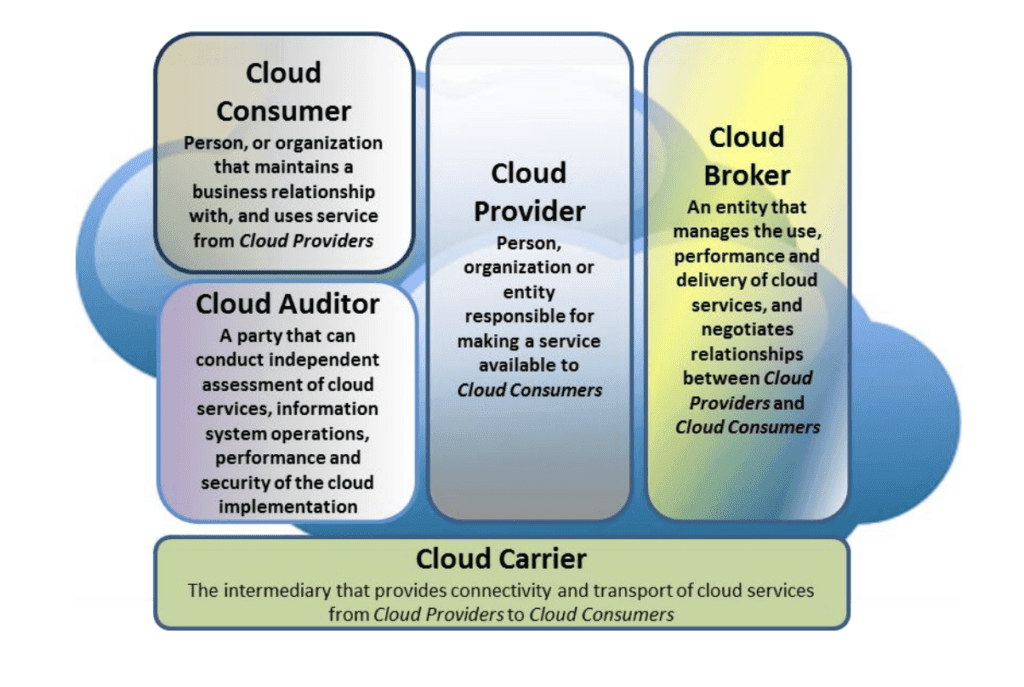
Cloud computing reference architecture. (Source: NIST)
From a legal perspective, it’s necessary to point out other key players — governments and international organizations. Due to a tremendous amount of stored data and its sensitive nature, many countries strictly regulate issues related to data storage and its distribution within a legal framework.The General Data Protection Regulation (GDPR) law within the European Union and European Economic Area implemented in 2018 outlines rules regulating all aspects of data usage, obligatory for all countries (members of the aforementioned integration formations). According to this law, organizations must report any data breaches within 72 hours. In case of violations, they may be a subject to a fine of up to €20 million, or up to four percent of their net worldwide turnover of the preceding financial year.
Cloud computing services are large-scale and elastic systems with multiple clients. Despite serious organizational, technical, and legal efforts, as well as the allocation of financial resources to prevent cloud data breaches, both providers and clients of cloud technologies are subjects to multiple malicious actions. These actions may include both traditional cyber threats and cloud-specific attacks, which may cause global, financial, reputational, and technological losses.
Notable Breaches
Many major companies have had their cloud data breached:
- Microsoft
- Dropbox
- National Electoral Institute of Mexico
- The Home Depot
- Yahoo
- World Wrestling Entertainment (WWE)
As a result of these attacks, hundreds of millions of users’ credentials and other personally identifiable information (PII) were sold on the dark web and used by cybercriminals in various fraudulent ways. Insikt Group recently revealed the identity of notorious hacker tessa88, a dark web seller of compromised Dropbox, LinkedIn, and Yahoo accounts, who could be potentially affiliated with the hacker groups that were behind the attacks on the aforementioned corporations.
Some of the most traditional cloud computer cyber threats include:
- Data breach or loss
- Abuse of cloud services
- Insecure interface and APIs
- Malicious insiders
- Illegal access to cloud systems
- Privilege escalation
- Natural disasters
- Hardware failure
- Supply chain failure
- Modifying network traffic
- Authentication attacks
- Malware attacks
- Loss of encryption keys
- Compliance risks
Cloud-Specific Cyber Threats
The primary threat to cloud computing services is the economic denial of sustainability (EDoS), a variation of the regular denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks. Cloud computing services operate according to the service-level agreement (SLA) between the cloud provider and the client. This document stipulates the level of service defined by the client, which the cloud provider delivers.
The number of resources provided to the client is charged by the provider proportionally. In this case, when fraudsters launch a DDoS attack on a cloud client, the cloud provider is responsible for responding to it in a timely manner and allocate as many financial resources as needed to neutralize the attack. Thus, the DDoS attack turns into a EDoS attack with direct negative economical input. In this situation, the client may choose another less expensive technical solution rather than cloud computing to continue operations, which means a serious reputational loss for the cloud provider.
The Value of Threat Intelligence
Cloud computing is a widespread, convenient, and perspective technology — one that still requires new technological and organizational solutions to secure its clients.
When implemented into cloud computing systems, threat intelligence allows organizations to foresee fraudulent actions and alert top management, security teams, and clients in a timely manner. Recorded Future applies artificial intelligence to prevent and defend against the potential threats discussed above, providing quality service to its clients at the highest level.
To learn more about how Recorded Future can help organizations understand and prevent these kinds of threats, request a personalized demo today.
Related
