Anticipating Black Friday Threat Trends
Executive Summary
- We studied attacks reported during the 2015 holiday period and identified new tools, techniques, and procedures (TTPs) that have emerged recently to help anticipate what to expect this year.
- Targeted threats against shoppers and retailers increase as the volume of shoppers surges during the holiday period.
- Key attack methods used over the Black Friday holiday period include phishing/smishing/spam, malvertising, pre-installed malware, point-of-sale (POS) malware, service disruption attacks, and account takeovers.
- Recent advances in threat actor TTPs have included updated POS malware such as FastPOS and increased service disruption potential following the Mirai botnet 1.2TB distributed denial of service (DDoS) attack.
- Both consumers and retailers can take actions to minmize successful attacks.
- In addition to strengthening security within the network, retailers can gain awareness into external risks using threat intelligence; for example, a recent Recorded Future analysis shows how analysts can be alerted to fake company websites used in phishing and other attacks.
- Consumers need to be vigilant with both online and offline transactions and check with your bank on setting up alerts on suspicious transactions, ensure your computer has the latest security updates and anti-malware, and don’t be afraid to ask retailers on the protection measures they have implemented.
Threat Environment
Black Friday sales and deals now extend to Cyber Monday; as a result, attacks can be seen for the whole weekend or even the whole holiday season. Akamai reports the Black Friday to Cyber Monday weekend is becoming as popular and important for retailers and e-commerce sites in Europe as it is in the U.S.
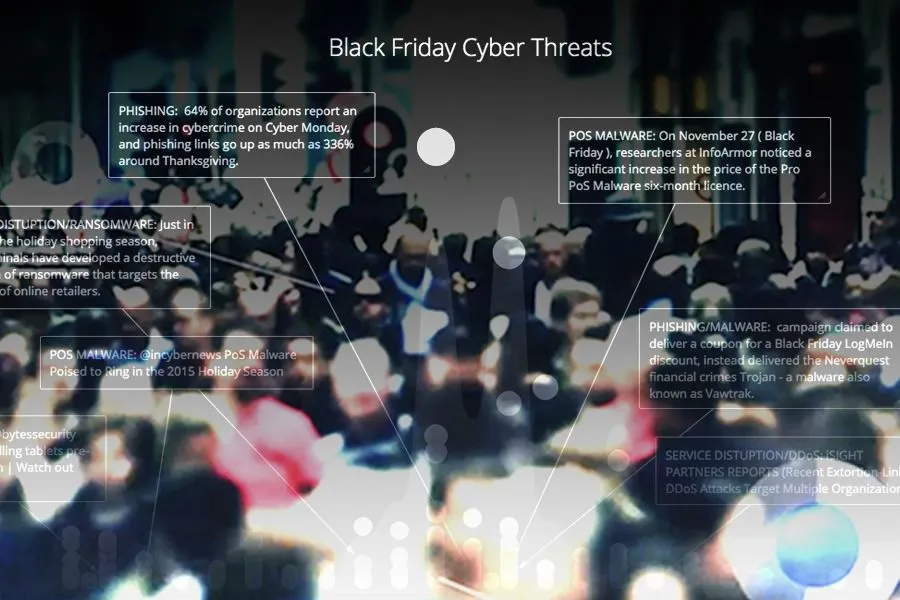
Looking at Recorded Future’s history of reported incidents around the holiday period during 2015, it’s clear there is heightened attention around Black Friday campaigns (see below). Details of the common attack methods seen are described below.
Cyber threats related to Black Friday weekend in 2015.
Phishing/Smishing/Spam
Studies have shown that the prevalence of phishing links go up as much as 336% around Thanksgiving. Email, text messages, and social media messages all may contain scams to dupe customers.
Themes include payment-related fraudulent emails purporting to be from PayPal, delivery confirmation emails claiming a package is being delivered, coupons promoting products or retailers, and fake refunds. Phishing kits even have holiday packages to help fraudsters lure customers.
Malvertising
Malvertising attacks use online ads to distribute malware via reputable websites. Invincia reports Yahoo!, eBay UK, and Huffington Post visitors were all hit with malvertising prior to the 2015 holiday season.
Pre-Installed Malware
Reports of pre-installed malware on tablets purchased from various retailers including Amazon were seen ahead of the Black Friday sales. It’s not the first case of this type of threat with Android, Lenovo, and other smartphones having been infected in the past.
POS Malware
Reports on point-of-sale malware, for stealing credit card details directly from retailers, were released ahead of the 2015 holidays. ModPOS and Pro PoS were two variants of the malware reported by security firms to be actively used and targeting retailers.
Symantec states the most common attack route against POS systems is through the corporate network. Once an attacker gains access to the corporate network — through a vulnerable public-facing server or spear-phishing email, for example — the attacker could traverse the network until they gain access to an entry point to the POS network. This entry point is often the same as a corporate administrator would utilize to maintain the POS systems.
POS malware is constantly evolving with each year bringing new names, types, and variants. An analysis of POS malware in 2014 by Recorded Future shows that the names have changed but the objective remains the same.
Service Disruption Attacks
According to Akamai, DDoS attacks are a consistent threat for retailers during the holidays, with average attack size growing by 2x. DDoS attacks can take down a retailer’s online site during the busiest shopping days of the year and often come with an extortion threat.
Additionally, according to independent security journalist Brian Krebs, fraudsters have developed new ransomware — dubbed “Linux.Encoder.1” — that targets websites to essentially hold its files, pages, and images for ransom.
Account Takeovers
Account takeover is big business for criminal actors, and they’re targeting more than bank information. Accounts such as mobile phone contracts, PayPal, and Uber can sell for much more than stolen credit card details on the underground market.
The ThreatMatrix Q4 2015 report states there was a large increase in account creation and account takeover fraud driven by the increased availability of stolen identities in the wild, harvested from massive breaches. The overall attacks increased by over 100% compared to the previous year. Additionally, it mentioned there was an 80% increase in attacks over Q4 2014; and 250% increase in attacks on retailers during the peak shopping days.
Anticipating 2016 Holiday Cyber Threats
We envision more of the same types of attacks as threat actors advance their TTPs:
- Holiday-themed phishing/smishing/spam: Dynamoo’s security blog is currently reporting many cases of Locky malware being spread. This is likely to continue over the holidays.
- POS malware: FastPOS was just reported to have been updated last month (October) ahead of the holiday season.
- DDoS attacks: The Mirai “Internet-of-Things” (IoT) botnet attack that took many websites offline via attacking DNS service provider Dyn on October 21 is likely to be a large threat over the holidays especially as the source code has been released. Criminal botnet operators will likely use Mirai’s success as a way to extract blackmail payments from online retailers and banks with threats of interfering with online shopping.
- Pre-installed malware: This year pre-installed malware have already been seen on CCTV devices and cheap noname Android devices.
- Malvertising: Big mainstream sites like BBC and New York Times have already been found to be serving malware via malvertising this year. More recently, Spotify and Google AdWords have been spreading malware via ads.
- Account takeover: There have been many data breaches in the press already this year. Some may have occurred years ago (e.g., Yahoo) but data is being openly shared now. This type of personal data can be used by threat actors to facilitate account takeovers. Some breaches may contain full credentials that are being sold on the underground market.
Threat intelligence plays a very helpful role in gaining insight into these threats at multiple levels. It provides insight into broader threat trends (as visualized in the timeline above), and it can provide operators with tactical content (see below), directly applicable for detecting and blocking threats before they impact the retailer or consumer.

Malware Intelligence Card™ for FastPOS.
Recorded Future Intelligence Cards™ analyze and summarize intelligence related to an indicator or malware. This intelligence, automatically generated and updated in real time, is immediately actionable for security operations.
Related