Applying Threat Intelligence for Better Vulnerability Visibility
A lot of the time, organizations take a volumetric approach to security, particularly when it comes to addressing vulnerabilities. And of course, without threat intelligence to inform your strategy, it only makes sense to prioritize vulnerabilities based on the number of systems susceptible.
However, with a strong threat intelligence program that provides analysis of vulnerabilities from a wide breadth of available sources, you’ll be able to take a much more strategic and risk-based approach. Instead of painting by numbers, you can query a range of sources and be alerted to the specific indicators that increase the risk of a CVE being exploited.
But since vulnerability disclosure and reporting is sporadic (to say the least), what are the right sources to gather this intelligence from?
Real-World Example: Gathering Intel for CVE-2017-5689
Data from Recorded Future reveals that 75 percent of disclosed vulnerabilities since the beginning of 2016 appear on web and social media sites a median average of seven days **before** official reporting channels, such as the National Vulnerability Database (NVD). And as references to disclosed vulnerabilities increase, so does the likelihood of exploitation.
The nature of sources also becomes a factor here. An uptick in references on criminal forums or dark web communities will also contribute to an increased risk score, as threat actors begin to discuss and share methods for exploitation. The risk will increase yet again when indicators show the vulnerability becoming part of an exploit kit.
A recent real-world example of this process involves a vulnerability in a tool called “Active Management Technology,” which is used in some intelligence products. Our research team, Insikt Group, analyzed the available intelligence:
“Recorded Future had seen a sharp increase in content regarding the recent exploit CVE-2017-5689 (SA-00075) nicknamed ‘Silent Bob is Silent,’ which includes proof-of-concept (POC) code. The flaw was originally discovered by researchers at Embedi in mid-February of 2017, and they recently released the details in their published white paper.”
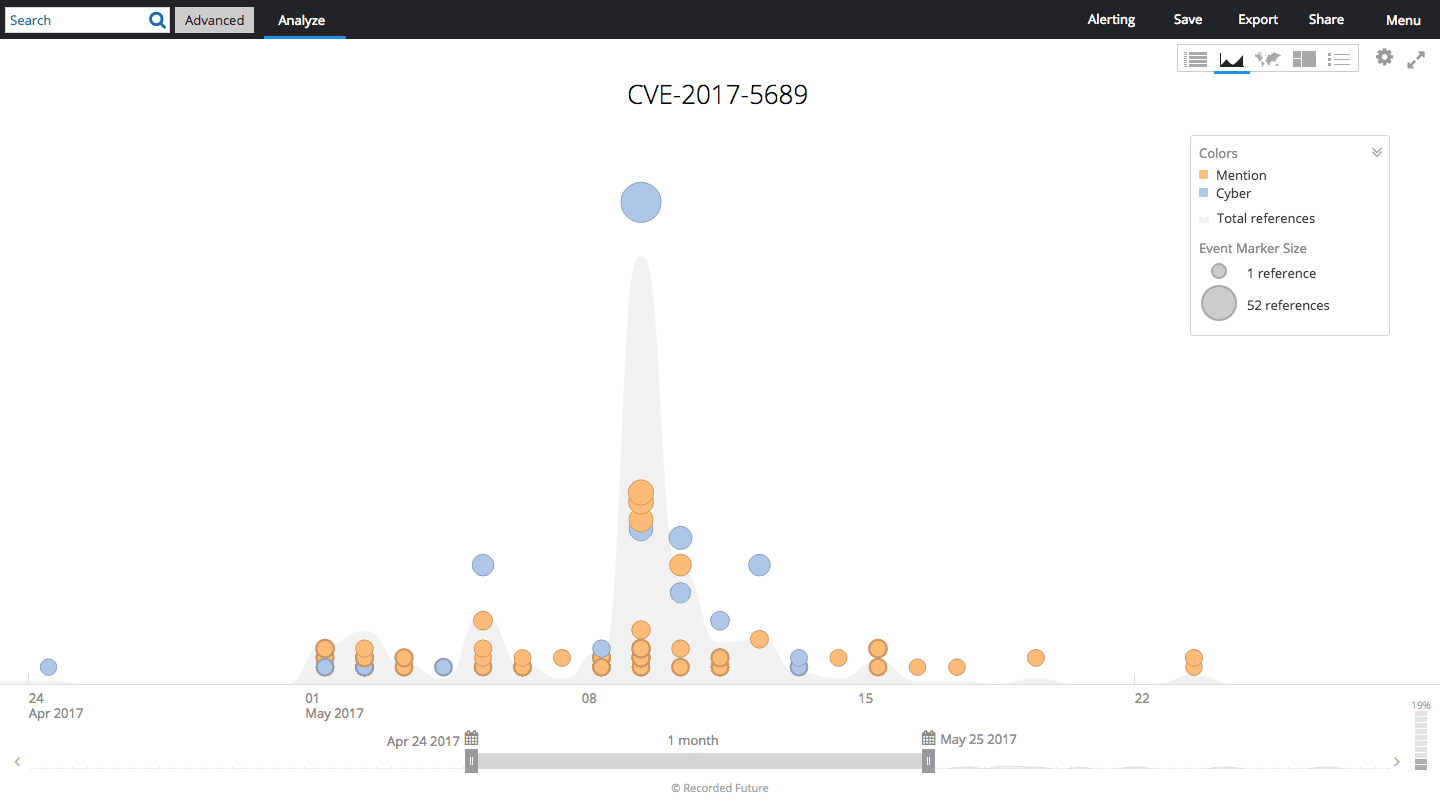
Timeline of CVE-2017-5689 in Recorded Future.
In the image above, you’ll note that as time goes on, references to the exploit quickly increase in volume. During the time period displayed, the CVE was added to a scanner, which enabled threat actors to easily identify vulnerable systems.
Following this, the POC code was added to GitHub, which quickly led to the exploit being actively discussed in criminal forums and dark web communities.
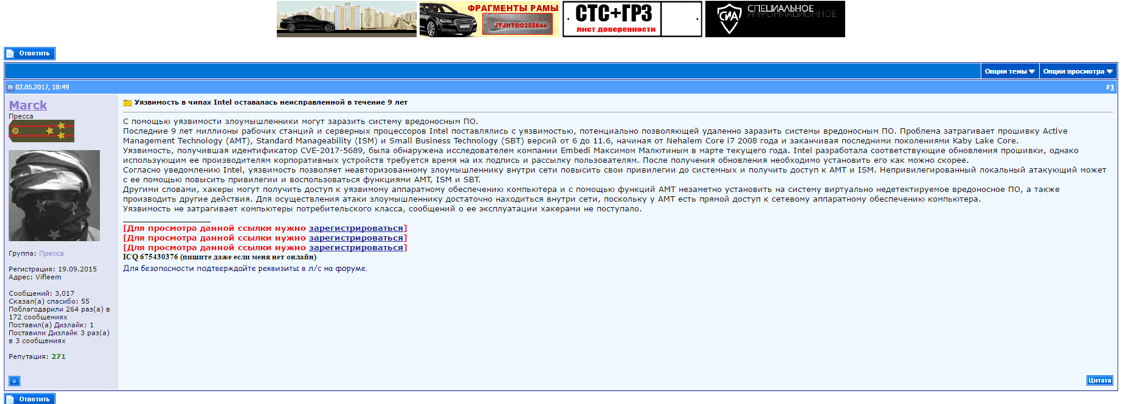
Reference to the POC exploit for CVE-2017-5689 on a criminal forum.
Identify the Most Significant Risks
Clearly, having this type of intelligence makes the task of prioritizing vulnerabilities far simpler and more powerful. After all, no matter how few of your assets it might impact, if an exploit is being actively discussed on dark web forums and is being weaponized at an alarming rate (as it was in this case), it should immediately jump to the top of your remediation priority list.
This process is in no way unique to vulnerability management. With a powerful threat intelligence capability, this level of data can constantly be gathered, analyzed, and used to inform a risk-based information security strategy. You’ll be in a position to identify the most significant threats to your organization at any point in time, and allocate your resources accordingly.
Want more real-world examples of applying threat intelligence to your security operations? Read our white paper titled, “Best Practices for Applying Threat Intelligence.”
Related