Biometric Authentication: Still Waiting for Identity 2.0

It took just four days for German researchers to give the latex finger to the new Samsung Galaxy S5 and crack its fingerprint authentication. We should not be surprised, after recalling the similarly swift exploit of the iPhone by Chaos Computer Club last fall. We learn that phones with higher resolution scanners create demand for higher resolution fake fingers.
Looking for post-password authentication, it’s easier to see an arms race than a promising future. Captchas, the web’s way of sorting bot from human, are defeated by seedy yet cheap APIs backed by mTurks or compute, and so we are challenged to decipher harder captchas. Happily, more services offer two-factor authentication and adoption has accelerated outside justifiably paranoid security circles. Continuing to look for silver linings, we can see continued password phishes like the Syrian Electronic Army attacks on Twitter and Forbes as high profile public service announcements for hard passwords and multi-factor. Mobile two-factor is clearly an improvement, but no silver bullet, especially considering recent history of passcode cracks and designed-in hacks exploiting emergency call features.
Passwords may in fact be obsolete. We might dispute passwords are iniquitous, but they are surely ubiquitous. And very important, as unfortunately proven by yet another naysayer this week. Market forecasters predict strong growth in mobile devices, while technology forecasters predict advances in biometrics technology.
<a href="https://www.recordedfuture.com/assets/biometric-authentication-timeline.png
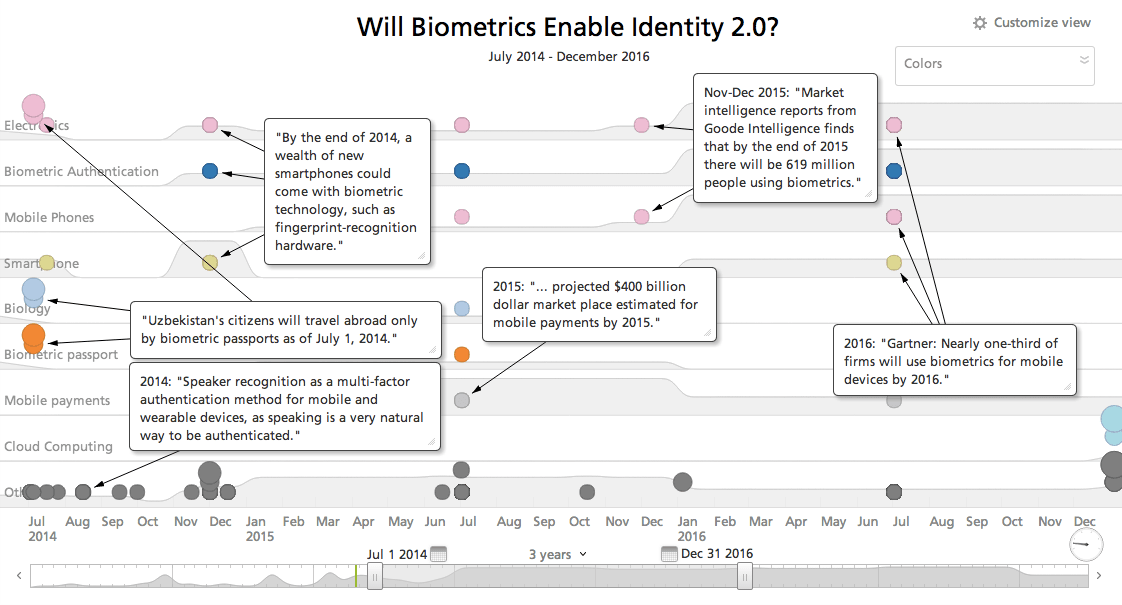
Click image for larger view
Will innovation in biometric authentication and identity management lead us to a post-password world in 2014? 2015? 2016? The timeline view above shows future predictions collected from open sources by Recorded Future. We invite readers to weigh in on the subject and tweet us at @RecordedFuture.
Related