Neighborhood Watch: Identifying Early Indicators of the Central Bank of Bangladesh Heist

Analysis Summary
- Utilizing stolen SWIFT credentials, hackers recently targeted the Central Bank of Bangladesh, ultimately stealing over $87 million via transfers through multiple financial institutions.
- Early threat intelligence analysis provides a proactive path to discovery of potential vulnerabilities, and a guide to further internal research.
- Identification of the hackers’ TTPs, their methods of attack, and other IOCs will accelerate your security team’s response.
As a threat intelligence analyst, the largest impact you make may be the observation of early indicators of compromise (IOCs) on other companies within your industry vertical. When you see the neighbor’s house on fire, the first thing to do is determine whether your house is on fire as well. In early hacks, this equates to “Am I being attacked or am I about to be attacked?”
Using Recorded Future, we’re going to demonstrate how to take an observation of a compromise, identify the basic information, research the compromise, analyze the content, and draw conclusions with a plan of action for further research.
Use Case: Central Bank of Bangladesh
Let’s assume you’re part of a financial company (though this model can be adjusted to any industry). We’ll use the generic cyber dashboard, but a similar process is possible if you have a tailored cyber view.
Our cyber dashboard is a customizable quick look at the entire world of open source activity related to cyber attacks. There are broad columns populated with _ All Attackers_ , _ All Methods_ , _ All Targets_ , and _ All Operations_ . You can also add columns related to _ Authors_ (of content) and _ Indicators_ . Each column can be filtered to specific entity groups within the column headers — _ All Attackers_ related to China, for example.
Looking at the All Targets column, “Bangladesh” and, more specifically, “Central Bank of Bangladesh,” appear near the top. Recorded Future helps to prioritize where you need to spend your time on research and analysis. We’re seeing a high level of activity on “Central Bank of Bangladesh,” but what does that involve? Time for a deeper dive.
Clicking on “What recent cyber events involve the Central Bank of Bangladesh,” we see our fears confirmed — there’s a cyber incident involving the Central Bank of Bangladesh, which we’ll refer to as CBB for brevity’s sake. The _ timeline view_ can provide an easy insight into the event structure and how it develops. In this case, we see a smaller bump a month after the main spike in activity.
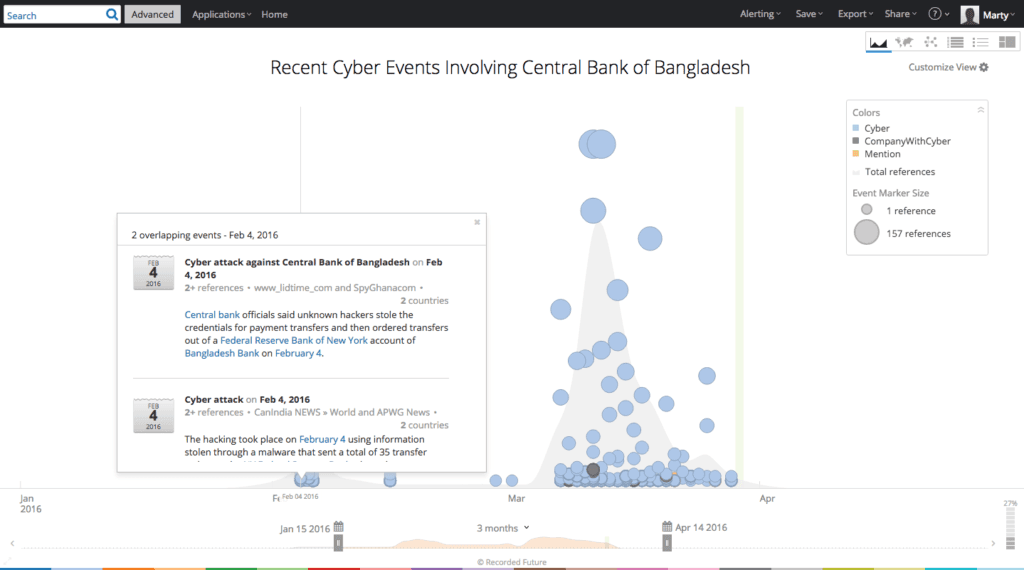
Focusing in on this bump of reports, we discover CBB was hacked back in early February, but the main reporting on this event didn’t occur until over a month later. The Philippines media initially broke the story of the hack, a point of controversy between the government of Bangladesh and the Central Bank. The Recorded Future timeline helps threat intelligence teams identify these trends earlier and prioritize their importance.
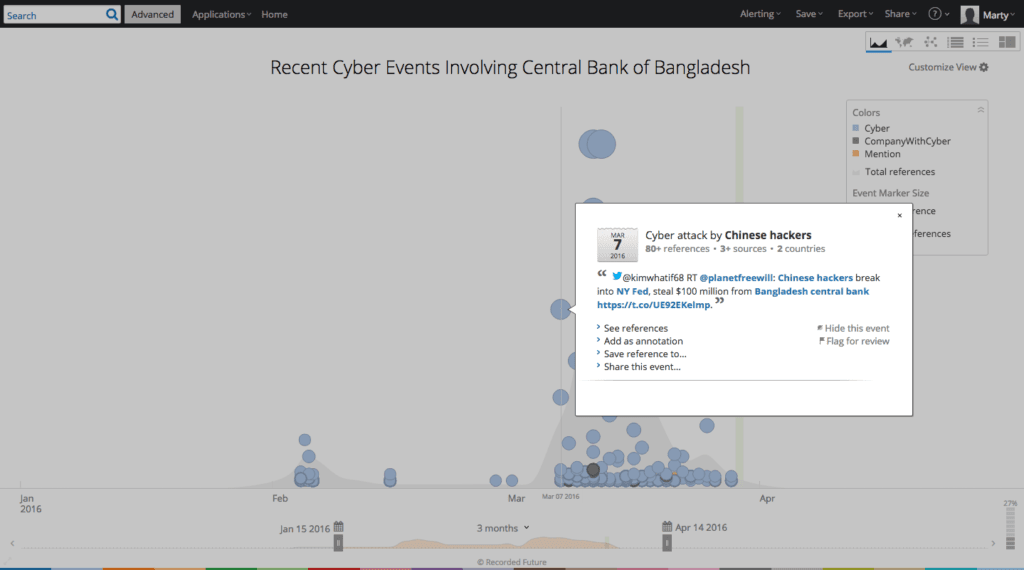
Looking at further incidents, we find a report alleging that Chinese hackers breached the Federal Reserve, and stole over $100 million from CBB. Interestingly, as we’ll see, almost everything in this report is false.
As is often the case with early reporting, there will be many alarming and extreme reports, emphasized by inaccurate, incomplete, and contradictory details. As reports develop, we’ll see less of these inaccurate reports in the timeline, and more of the accurate information.
Early Findings
Banks and financial institutions are particularly susceptible to broad infrastructure attacks from hackers. Most banks are linked by mutual agreements and trading structures, such as clearing houses, and transactional systems, such as SWIFT. This linkage provides a common surface to attack, posing a danger to anyone connected to it. Good threat intelligence practices and monitoring detects danger earlier and prioritizes threat mitigation tasks.
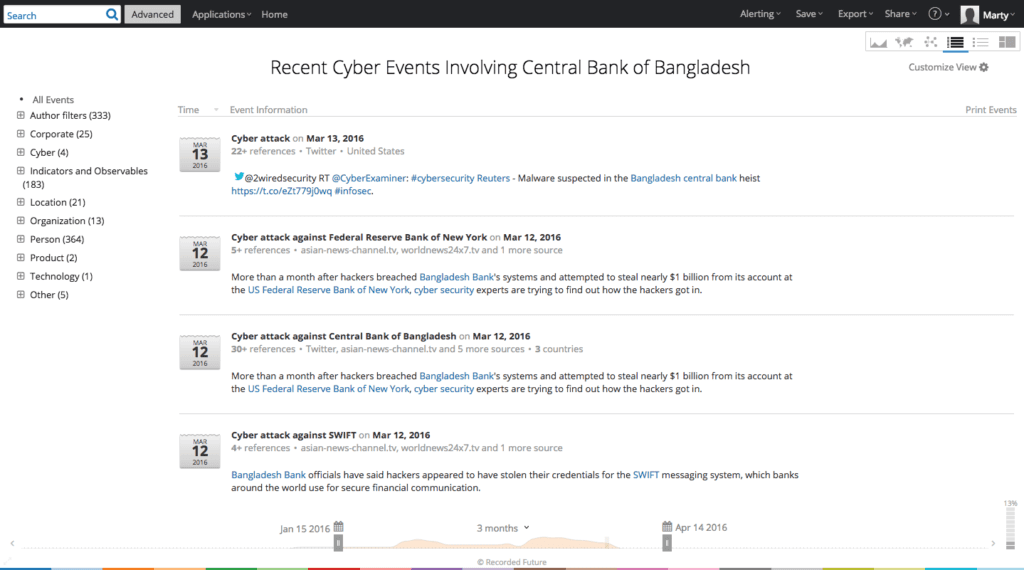
By switching to the _ table view_ , we can discover more detail concerning the events, such as summaries of the reported cyber events, in chronological order. These events are sortable by the different attributes, located in the column on the left. Now we can begin to draw a some initial ideas about this event:
Initial Review
| Who | Hackers (unknown), CBB, Federal Reserve Bank |
|---|---|
| What | Massive transfer of funds, over $100M? |
| Where | Bangladesh, New York, Phillippines |
| When | February 4-5, 2016 |
| How | Malware attack? Federal Reserve hacked? |
After initial review, it’s important to identify the specifics of the attack and create a task list for further research on our internal systems. Threat intelligence gives you multiple ways of conducting the open source research and identifying the tactical information needed for research, whether in the timeline, the dashboard, or using one of the other applications. One of the ways Recorded Future displays information is by references, as shown above. References are summarized in the table view, and can also be individually explored.
After conducting this research, this is the summary we’re able to draw:
Beginning as early as January 2016, unidentified hackers penetrated the servers of the Central Bank of Bangladesh. The hackers installed an unidentified malware, possibly a remote access trojan (RAT), likely used to monitor the CBB banking transactions.
Specifically, the hackers stole the CBB credentials used for SWIFT transactions, the system banks use for secure messaging between banks. The actors then made a string of upwards of 35 transaction attempts, of which four were successful, ultimately routing funds of over $81 million through accounts in the Philippines, Sri Lanka, and Hong Kong.
The fifth transaction of $20 million was detected by Pan Asia Banking Corp., and withheld by Deutsche Bank, a routing bank, due to the unusually large amount for the destination, and the misspelling of the name of the destination account, the Shalika Foundation (misspelled “fandation”). The 31 unsuccessful transaction attempts requested amounts totalling between $850-$870 million.
Of note, the hackers appear to have initially attempted smaller transactions, then increasing to significantly larger transactions after the stoppage of the Shalika transfer.
The hack was first reported by news media in the Philippines, then by written statements by CBB and the Fed. CBB accused the Federal Reserve of being hacked by the Chinese, a claim refuted by both the Fed and SWIFT, a Belgian organization.
At this time, the identity of the hackers, the specific methodologies/vulnerabilities used to infect the CBB intranet, the source of insider knowledge needed to utilize the SWIFT transactions, and the specific sources where the money exited the banking system are all still unknown.
| Initial Review | Final Review | |
|---|---|---|
| Who | Hackers (unknown), CBB, Federal Reserve Bank | Hackers (unknown), CBB, Federal Reserve Bank, SWIFT, intermediary banks and NGOs |
| What | Massive transfer of funds, over $100M? | $81 million stolen, additional $850-$870 million in attempted transfers |
| Where | Bangladesh, New York, Philippines | Bangladesh, New York, Philippines, Sri Lanka, Hong Kong |
| When | February 4-5, 2016 | Intrusion as early as January, discovered February 4-5, 2016, reported last week |
| How | Malware attack? Federal Reserve hacked? | Compromised credentials by malware on CBB intranet connected to SWIFT |
Now What?
Using this information, we can begin to answer our initial questions. Are we being attacked, or are we about to be attacked? This attack appears particularly targeted, utilizing very specialized knowledge about the CBB and SWIFT transactions. The likely answer is no, however the situation will become much more complex if analysis reveals the hackers utilized an unpatched or undisclosed vulnerability. This situation should continue to be monitored, however none of the immediate reports point to the compromise.
Moving on to the second question, we can use the above information to prioritize our internal search. The Federal Reserve and SWIFT were adamant in their statement that the network had not been compromised, and that valid codes were used to certify the SWIFT transactions. It appears the primary point of intrusion was the CBB intranet nodes connected to the SWIFT transaction network. A good starting point might be a review of the SWIFT transactions conducted at your institution, followed by a vulnerability assessment on the SWIFT or other banking credentials stored and utilized on your networks. Lastly, implementation of higher security for credentials, including two-factor authentication, should be implemented.
Always on Alert
In conclusion, like a fire at your neighbor’s house, attacks on companies in or near your business space need to be very carefully watched. “Neighborhood” attacks should be reviewed for vulnerabilities to your networks, lessons learned, and internal research prioritization. Recorded Future assists threat intelligence analysts with these functions and more.
Related