Overview of Intelligence Cards
Intelligence Cards™ bundle essential information related to a specific investigation topic, like a technical indicator, malware family, or software vulnerability. Intelligence Cards are a starting point for triage, and are pivot points during an investigation.
Each entity type has an Intelligence Card™, and some examples are listed below. The rest of this page includes general descriptions of common components found in most, if not all, Intelligence Cards.
- IP Address - individual IPs and IP ranges (CIDRs)
- Domain - Domains and DNS names for FQDNs, Name Servers, Mail Exchanges, etc.
- Hash - includes MD5, SHA-1 and SHA256 hashes
- Vulnerability - primarily CVE vulnerabilities from NIST NVD
- Malware - malware family names
- Threat Actor - threat actor groups
- Location - threat and hazard information related to a specific City
Across all types, Intelligence Cards provide a similar baseline set of information sections. This overview introduces these common sections first, then adds details for specific Intelligence Card; types.
Heading
The heading section identifies the entity summarized in this Intelligence Card™, and provides the first and last dates when reporting about this entity was observed. The heading section also offers actions, including data exports and creating a share link for this Intelligence Card.
Risk Score
Risk Scores are provided for IP Addresses, Domains, Hashes, and Vulnerabilities. The score is based on a set of risk rules. Each rule triggers based on specific evidence, and can independently age out. The input sources for risk rules include Recorded Future's technical data collection, threat feeds, and context from 1M+ web sources including security researchers and blogs, social media, forums and more.
Each risk rule has a severity level. The risk score for an entity is in a banded determined by the highest severity risk rule that is currently triggered. Additional risk rules triggered at lower severity levels will slightly increase the overall risk score. Multiple risk rules triggered at same severity levels cause a larger increase in score, but will never cause the score to risk into the band of risk scores reserved for higher severity levels.
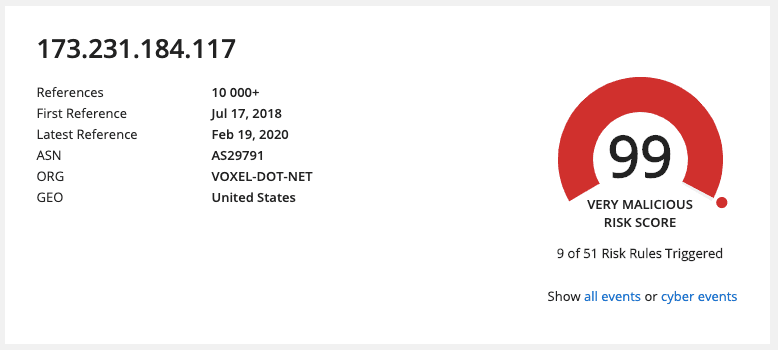
Evidence for Triggered Risk Rules
Intelligence Cards provide transparency into the evidence for each risk rule, usually including one or more reporting sources and links back to documents published by these sources.
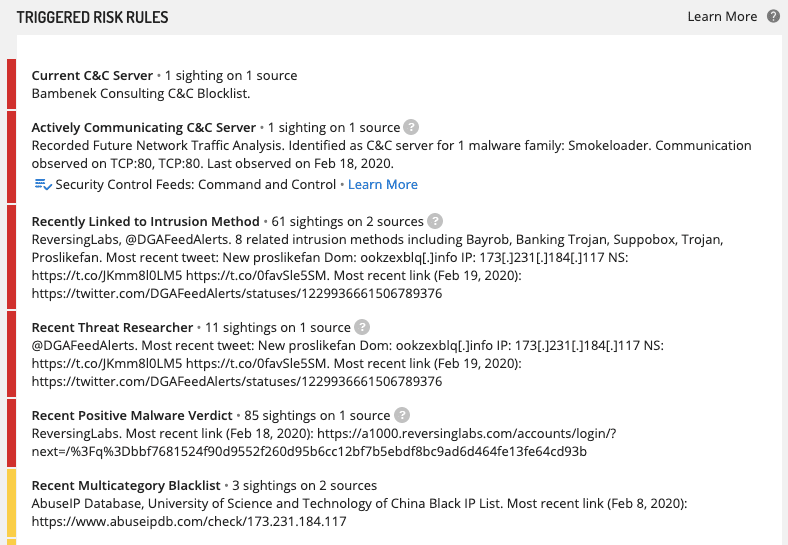
In addition to the triggered risk rules and evidence (nine in this example above, six of which are shown in the screenshot) we also state how many risk rules in total are being used to evaluate an entity's risk (51 in the example above.) We regularly add new risk rules, which are progressively evaluated for all entities of that type. During these updates you may see Intelligence Cards of the same entity type which state a different total number of risk rules.
Risk Rule Guidance
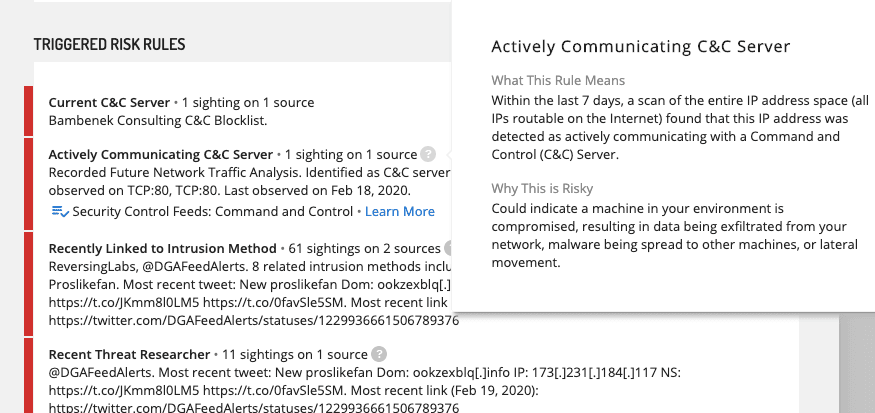
Intelligence Cards also provide guidance that explains the logic and intend use of triggered risk rules. Click on the question mark icon next to a triggered risk rule to see the guidance, which explains when the rule triggers, why that kind of information or sighting has risk significance, and what next: suggested actions that are appropriate to the nature and confidence of the risk information.
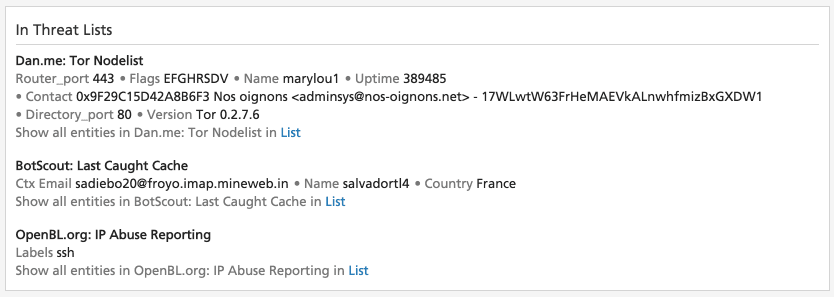
Threat Lists
When the entity is currently including in one more threat lists, this is reflected on the Intelligence Card. Recorded Future tracks updates to threat lists, daily or more frequently depending on the cadence of the threat list provider. A removal of the entity from an external threat list is rapidly reflected in Recorded Future, and risk rules are updated accordingly. Note that entities included in whitelists and mitigation lists will also reflect that list here. A description of each list is available here.
Recent Event Timelines
Recorded Future organizes reporting involving the entity by time, and Intelligence Cards include a timeline of reporting in the last 60 days.
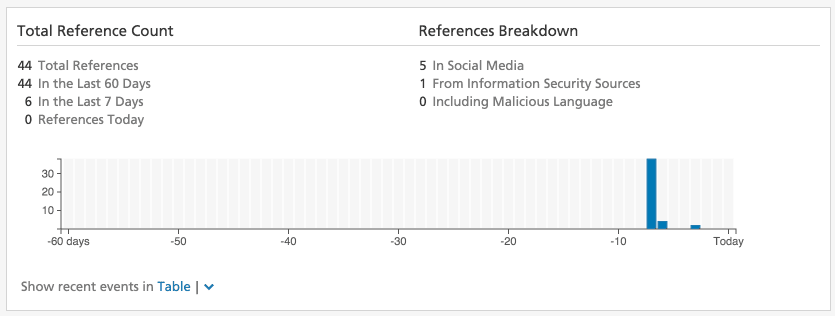
Malware, Vulnerability, and Threat Actor Intelligence Cards may show two timelines. The first timeline, colored in blue, summarizes all reported events involving this entity in the last 60 days. The second timeline summarizes reported Cyber Attack and Cyber Exploit events specifically. Each day in the cyber event timeline is color-coded by the criticality of the Cyber Threat signal for this entity on that date.
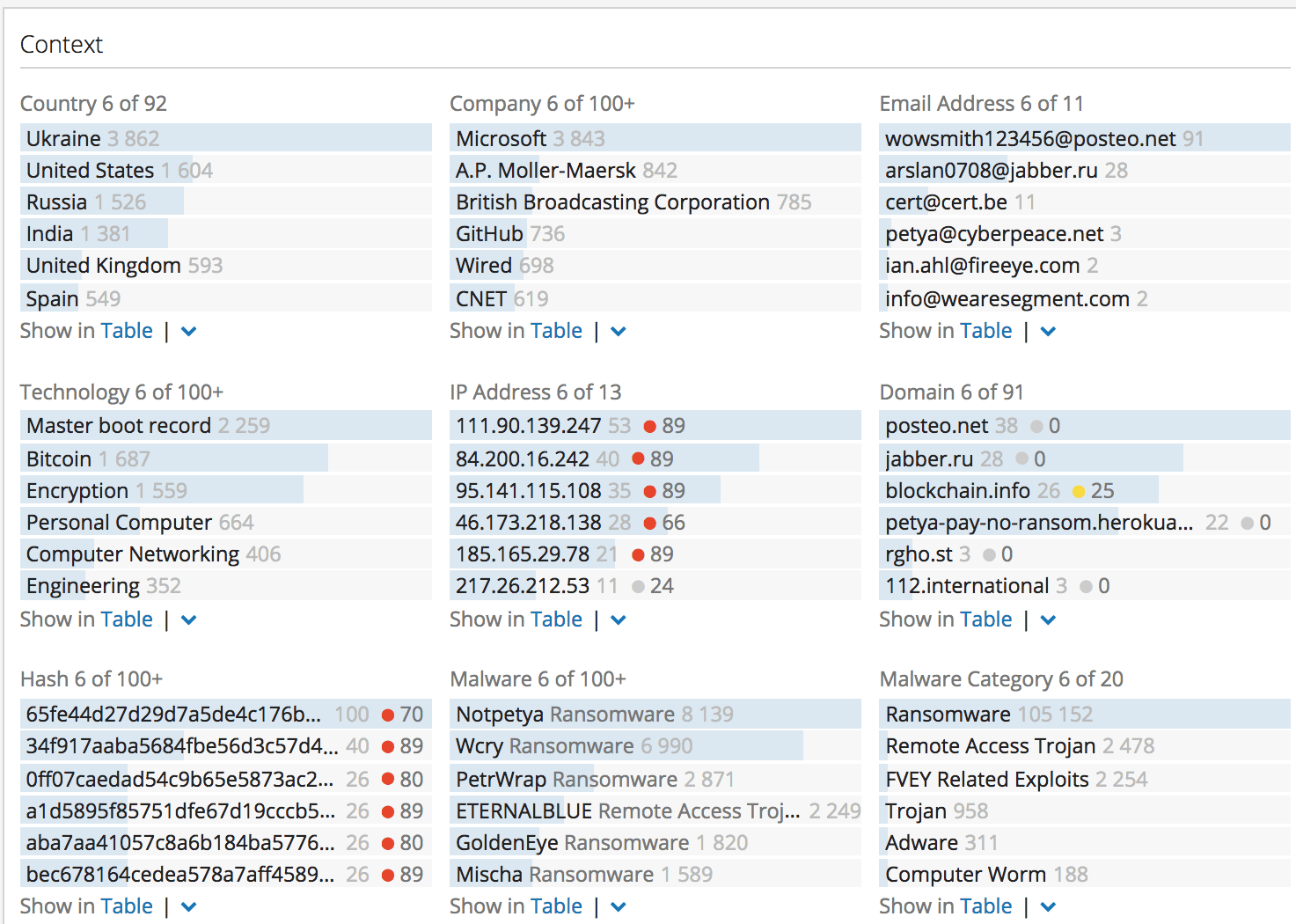
Context
These lists summarize other infrastructure and entities reported together with the primary entity for the Intelligence Card. The Context section records co-occurrences, which are mentions of the Intelligence Card entity and the related entity from this section in the same sentence or document. The co-occurrences do not make any assertion about the nature or strength of the connection between entities, just that they were mentioned together.
The length of the blue bar for each related entity shows the relative frequency with which it is mentioned in conjunction with the primary entity. You can view the specific events for each link by clicking on the related entity in the list. You can view more related entities, beyond the top list shown in the Intelligence Card, by clicking the Show in Table action.
Extensions
Extensions are integrations that enhance Intelligence Cards with content from our Intelligence Partners.
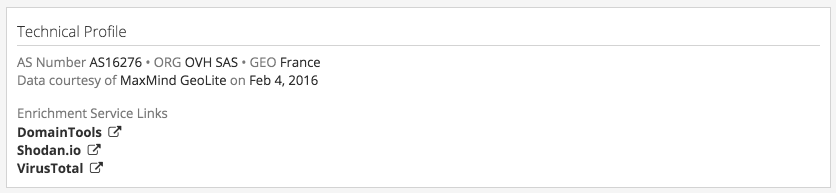
Technical Profile and Enrichment Service Links
Convenience navigation links are included for several enrichment services that publish information to the security community. These include DomainTools (domain registration and WHOIS), Shodan (open ports and services) and VirusTotal (malware linked to the infrastructure through static or sandbox behavioral analysis.)
Recent References and First Reference
Each Intelligence Card concludes with a set of individual references, highlighted based on time of reporting (most recent report and first report) or highlighted as the most recent report from an event type or group of sources. These highlighted recent events include Cyber Events, Paste Sites, Social Media, Information Security sources, Underground Forums, and Dark Web sources.
Recorded Future processes unstructured data from open web, technical web, dark web, expert research, and customer provided sources with machine learning and natural language processing techniques. While we have both rigorous automated and manual processes in place to ensure the highest quality threat intelligence, there may be small errors or misattributions in our Intelligence Cards. If you come across a data inaccuracy, help us improve the information by Requesting a Data Review and one of our expert researchers will conduct a review.
In order to request curation of an entity and make sure it is up to date with missing information, navigate to the Intelligence Card; for that entity. Then click the 3 dots in the top-right, and click "Report Data Issue" > "Request Curation". Fill out any necessary fields and include additional information that could help us perform the curation.
If data is believed to be incorrect, you'd want to use the "Request Data Review" option, which will trigger further investigation and follow up.


In each request, please include as much information as possible about the request so that our expert researchers are able to focus their attention on the specific data element.