Your AWS Presence Is Growing Fast. Keep Your Attack Surface From Growing Even Faster.

Think about the ways your Information Technology (IT) group has helped your company grow in the last few years.
- The number of legacy applications and workloads you’ve migrated from your data center to Amazon Web Services (AWS).
- The countless hours of remote computing and work at home you’ve enabled for your co-workers.
- The gigabytes of files you’ve authorized your outside business partners and suppliers to access.
- The ease and independence with which Engineering, Marketing, and Finance can spin up public-facing assets like virtual machines and collaboration sites.
You’re this far into your digital transformation and the upside is plainly visible to your company. But almost every step you take toward greater growth has the corresponding downside of expanding your attack surface.
And unfortunately, that reality is not so plainly visible to your company.
Catching up with your growing attack surface
When you embark on initiatives like digital transformation and cloud computing, you soon discover how easy it is to add cloud services. The average enterprise uses dozens - even hundreds - of distinct cloud services.
That’s why it’s important to put access policies in place and enforce them. Policies help you standardize and codify your approach to the cloud and they help you maintain compliance. Smart companies carefully vet and select a limited number of in-policy cloud providers so they can more easily maintain and monitor the assets they run in the cloud.
What happens when you overlook policies in your rush to the cloud? For one thing, you run the risk of inadequate identity and access management, leading to problems like data leaks, breaches and insider threats. More dangerous is your accumulation of out-of-policy providers: entities and services around the web that your IT organization doesn’t vet and doesn’t know about. As this shadow IT proliferates, the quantity, location and configuration of out-of-policy assets, such as applications, files, databases and shares, quickly gets out of hand.
In IT security, you can’t defend what you can’t find. And the more your attack surface grows, the less of it you can find and properly defend.
An AWS example
Suppose that AWS is your company’s in-policy provider for public cloud computing. Teams around the company are spinning up virtual servers with Elastic Compute Cloud (Amazon EC2), storing backups with Amazon Simple Storage Service (Amazon S3), and managing relational databases with Amazon Relational Database Service (Amazon RDS). Your IT group can ensure all of those assets are securely configured.
But outside of those AWS resources, your co-workers are also moving files around through less well-known sites. They’re spinning up boxes with second-tier cloud providers so they can quickly run a few tests. They’re posting code snippets for peer review in repositories they follow in developer forums. They’re using low-reputation sites to conduct demos for prospects.
They may be innocently going outside of AWS for convenience, or out of habit. They may be doing it to avoid detection. But either way, the effect is the same. They’re setting you up for policy violations and security lapses like subdomain takeovers, leaked product keys, and accidentally embedded company information spilling onto the public internet.
In short, they’re gradually expanding your company’s attack surface by engaging in shadow IT. The more they rely on out-of-policy providers and external assets to get their job done, the bigger the blind spot you have in your security landscape.
Find it — Attack surface intelligence for AWS
Attack surface intelligence is an approach to cloud security designed to help you find the providers and assets in your blind spot so you can better protect yourself. The Attack Surface Intelligence module from Recorded Future is an agentless solution that does not require any credentials for discovery. It takes inventory of your entire attack surface, then scans for 4,000 vulnerabilities and dangerous varieties of misconfiguration.
A rigorous inventory is the starting point for your security; without it, you can’t know what all you have to protect. Attack Surface Intelligence conducts inventory of on-premises and cloud assets. It provides persistent coverage of both your landscape and the internet to identify where assets are hosted, especially if they’re out of policy.
A typical enterprise hierarchy includes:
- Two in-policy cloud providers, such as AWS and Google Cloud Platform, or AWS and Microsoft Azure
- Software-as-a-service (SaaS) providers, such as Salesforce and ServiceNow
- A variety of other, in-policy cloud providers that IT knows about and has authorized
- Everything else — mostly out-of-policy providers
Attack Surface Intelligence scans for a wide variety of immediate risks and out-of-policy assets, including:
- Historically insecure service providers, with a history of configurations or settings that are vulnerable to subdomain takeovers
- Misconfigured web application firewalls
- Open ports on databases
- Self-signed certificates left exposed on public hostnames
- Development or staging subdomains that should not be open to the public internet
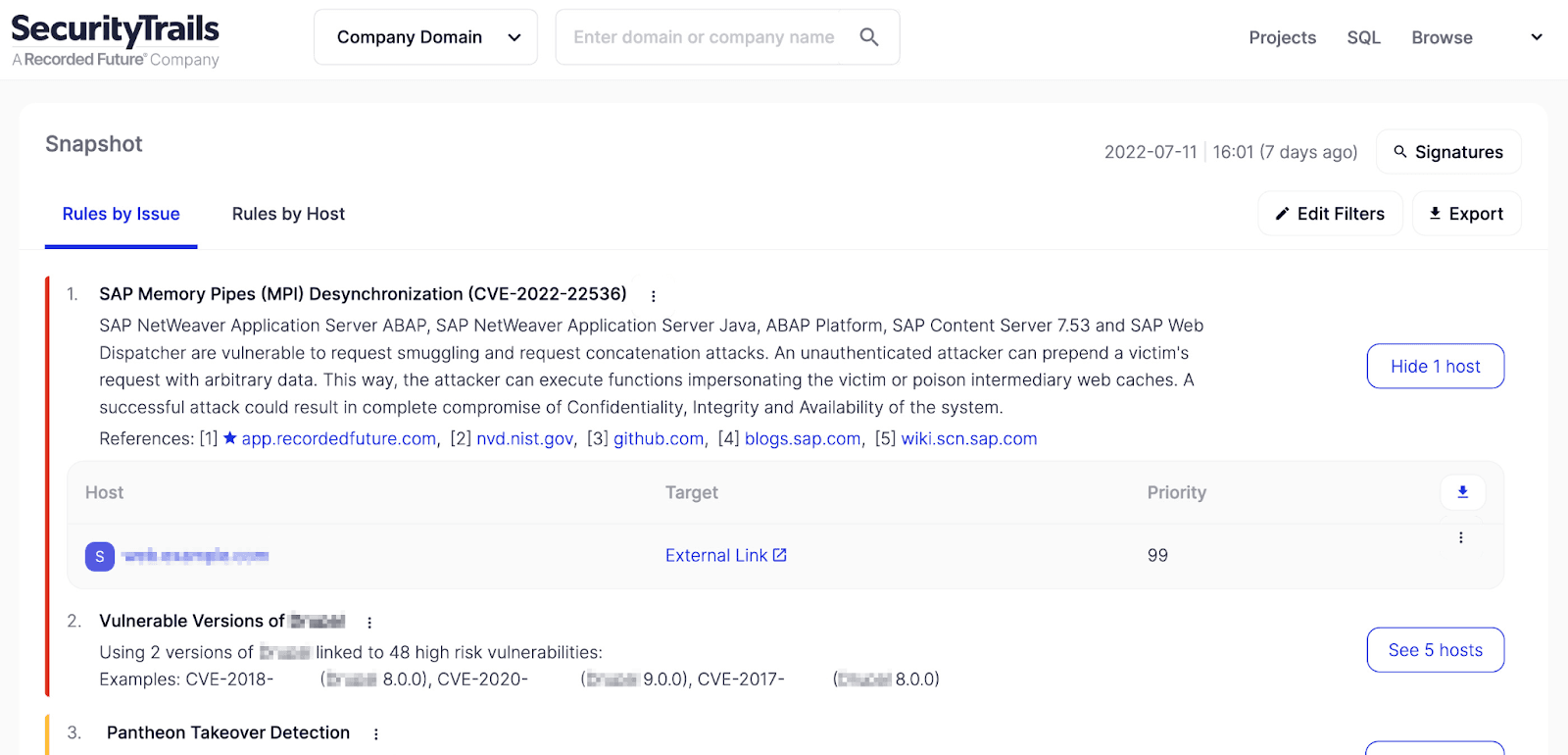
The inventory lists not only your in-policy AWS assets, but also your shadow IT assets hosted with second-tier cloud providers. With this unified view of its external infrastructure, an organization can better navigate across disparate technology systems and quickly map and resolve vulnerabilities, while keeping pace with its dynamic attack surface.
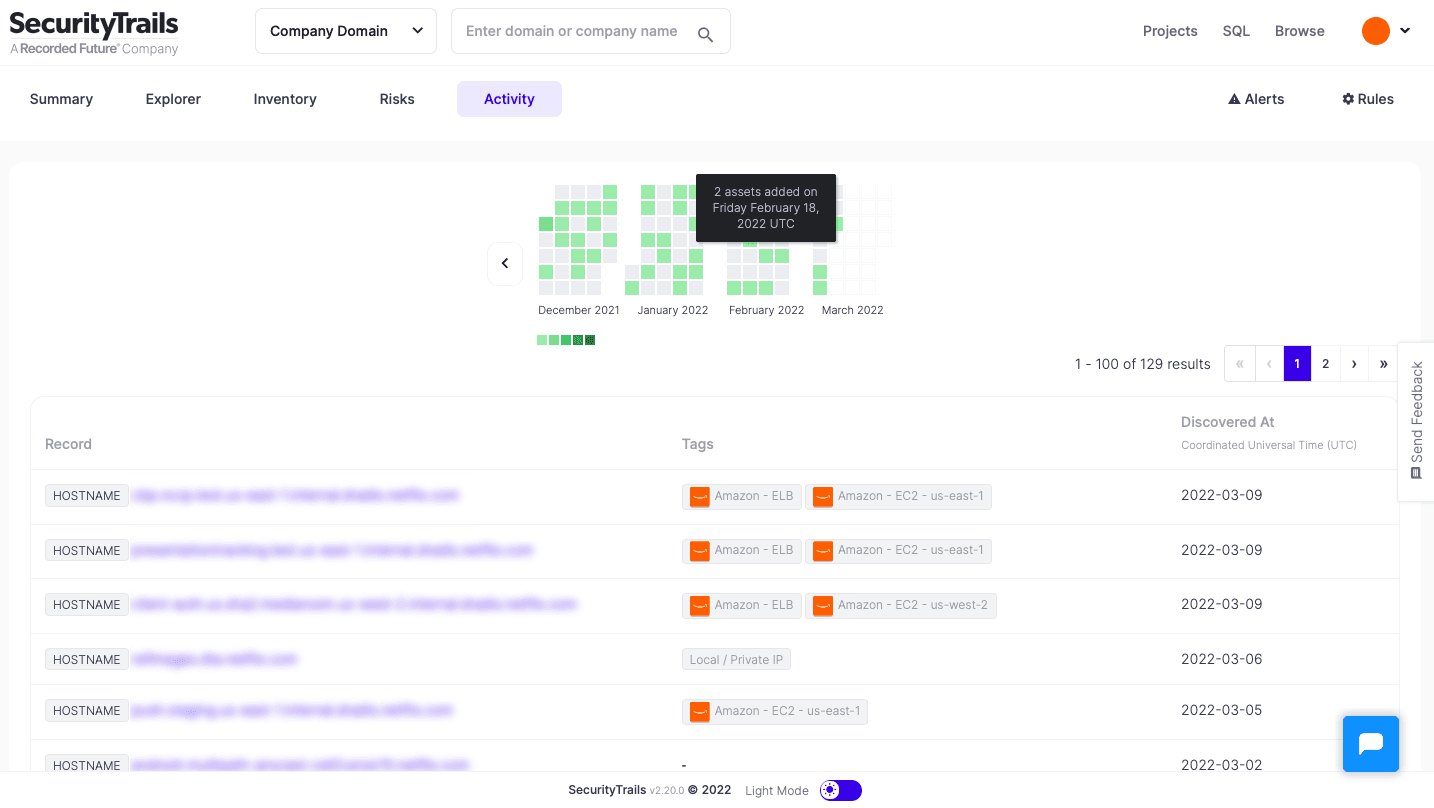
Secure it/Defend it — Threat Intelligence for AWS
Once you’ve taken inventory of your assets in AWS and elsewhere, questions arise:
- What are you going to do about assets and providers you didn’t know you had?
- Can you identify and trace all of them to the group that owns them?
- Are those assets and providers vulnerable?
- Are any assets misconfigured? Have they already been exploited?
- How do you assess the risk you run? How urgent is the security gap you’ve just discovered?
In short, the next step is to assess your exposure so you can decide how to secure and defend your environment. That involves other modules from Recorded Future such as Threat Intelligence and SecOps Intelligence. The modules are integrated into threat detection tools like Amazon GuardDuty, and security information and event management (SIEM) tools like Splunk to better identify, protect, and respond to threats.
Threat Intelligence from Recorded Future is gathered from underground communities and correlated with a large quantity and variety of sources from the surface web. It is then enriched by world-class analysts and integrated directly into your workflows. Threat intelligence arms your security analysts with a powerful tool for seeing, understanding, and disrupting the malicious actors who take aim at your IT assets.
Security operations rely on having alerts in more than one context: the context of the external threat landscape and the context of prior responses to similar alerts. SecOps teams can write alert statuses and notes directly from Splunk into the Recorded Future Intelligence Cloud. That facilitates sharing, eliminates siloes and promotes better-informed decision making.
Take the next step
Growing companies of all sizes turn to AWS to grow even bigger. The safest way for any company to grow its AWS presence is by setting policies and using real-time intelligence to comply with them. That applies to AWS and all cloud-based assets and providers.
Find out more about the integration between Recorded Future and Amazon GuardDuty – and how you can proactively reduce your attack surface today.
Related