Putting Data in Perspective With Web Intelligence
Summary
Government and private sector threat intelligence analysts are awash in data: both proprietary and open source. The evaluation of both – all-source analysis – provides analysts the perspective they need to communicate risk and better task (often expensive) resources at their disposal. Leveraging web intelligence (WEBINT) can effectively apply open sources to this process.
… open sources—the systematic collection of foreign media—have always been a bedrock source of information for intelligence.9/11 Commission – Staff Statement No. 11
The Web Intelligence Perspective
Evaluating open sources requires the least infrastructure of all the “INTs.” SIGINT (Signals Intelligence) and IMINT (Imagery Intelligence) require massive investment and infrastructure maintenance. HUMINT (Human Intelligence) requires extensive amounts of time, vetting, and physical risk. Similarly – storing, visualizing, and analyzing private network logs is a costly and cumbersome process.
Extracting all freely available information is critical for the targeted deployment of not only these systems, but also the personnel assigned to them.
Although access to raw data is free, utilizing open source information demands analyst time. In the private sector, analysis and collection are generally combined, forcing analysts to spend a majority of their day collecting intelligence – and only then – analyzing. Hiring and retaining good analysts involves a significant financial commitment, making effective use of open source data sets critical.
Understanding WEBINT: Web intelligence is the structuring of unstructured information from the Internet for analysis. Traditional open source analysis requires document by document collection and evaluation. WEBINT allows for the identification of trends over time and alerts on upcoming future events.
Web intelligence (WEBINT) is a means to efficiently identify the intelligence available in open source (OSINT). Structuring and visualizing web-based information allows an analyst to surface tactical information like technical indicators, and strategic understandings like the swaying sentiment of a troubled region.
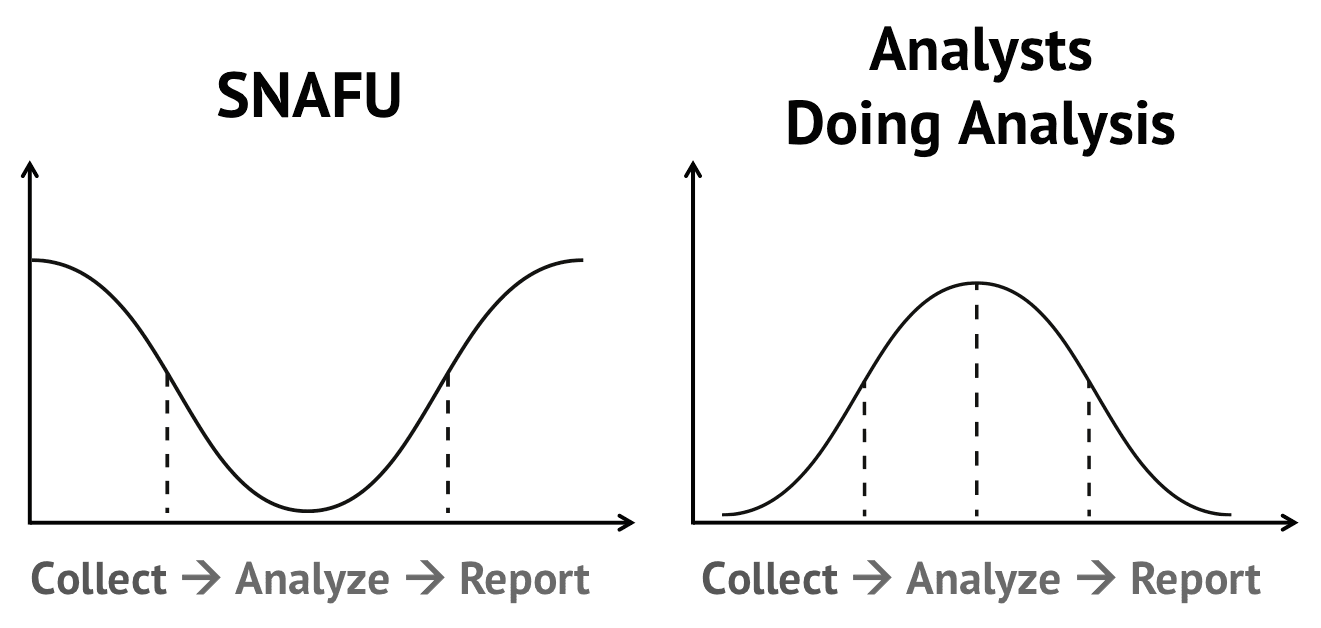
This structured approach allows for efficiencies in OSINT collection and analysis. This gives a threat intelligence analyst the information he/she needs to make a more targeted search of their network logs and/or private data sets. Alert Logic recently detailed this process in a webinar with us, explaining how OSINT bookends their analysis of cyber threats.
Research Collaborations Using Web Intelligence
Recorded Future research collaborations with ThreatConnect, ReversingLabs, DigitalGlobe, and OrphanSecure illustrate this trend of WEBINT; driving both investigations of collected data and deployment of future collection.

APT (advanced persistent threat) research is incredibly costly in both time and effort. Recent collaboration with ThreatConnect demonstrates WEBINT’s identification of key geopolitical events, trends and future events that may signal APT activity/response. This aids in the collection of APT exploits, provides clues to the ultimate actors, and can support alerts to a workforce about what to look for in a phishing attack or social engineering campaign.

Understanding a threat actor’s use of encrypted communication is extremely difficult. However, applying WEBINT to the problem set can identify changes in tools, techniques, and patterns of operation. Recorded Future’s analysis of shifting Al-Qaeda encryption technologies pointed ReversingLabs at key pieces of information in their enormous malware repository.

WEBINT can support the deployment of costly infrastructure as seen in Recorded Future’s collaboration with DigitalGlobe during the 2014 Winter Olympic Games in Sochi. Identifying swaying sentiment in areas around the “ring of steel” provided critical context to geospatial analysts seeking a better understanding of the situation on the ground.

Orphan Secure’s utilization of WEBINT supports the identification of new incidents, developments, and trends to better inform their identification of human trafficking.
Take Action
In sum, open source is a bedrock dataset for each and every threat intelligence analyst – either in the government or private sector. Effectively applying web intelligence to open source can drive all-source analysis and efficiencies all around the intelligence cycle.
Related
