Using the Recorded Future Platform for Our Annual Vulnerability Report Research
Editor’s Note: Recorded Future is working to bridge the gap between the theoretical and the practical by providing step-by-step guides to using its platform. This blog includes steps for recreating our recent report, “Microsoft Targeted by 8 of 10 Top Vulnerabilities in 2018,” published on March 19, 2018.
The vast amount of data available in Recorded Future opens up many avenues of research. Our 2018 annual top exploited vulnerabilities report was researched completely within the Recorded Future® Platform and restful API. This blog features the steps taken to complete the report, starting with a raw API query from our data science team encompassing all vulnerabilities referenced in 2018, along with the most occurrences of exploit kits, RATs, or phishing. Recorded Future’s collection of dozens of underground and dark web forums was also used for additional context.
For each step, care was taken to ensure that the references produced by the API were legitimate within the portal. I did this in a few ways: first, through the advanced query builder, I was able to check the references between the associations, ensuring that documents were not double counted and were validated by multiple sources.
Second, using Recorded Future’s capability to save and create lists of vulnerabilities, exploits, or notable references found along the way ensured that any work done was not lost and easily repeatable. Recorded Future’s data tagging ensured that I could easily filter results to each individual vulnerability, checking that associated exploit kits and RATs were correctly attributed. Recorded Future’s capability of querying by source type also provided the scope needed to determine how often and for how much some of these exploit kits were selling.
Now, diving in, here’s how we made it happen.
Research Steps
Step 1
I used Recorded Future’s API to find the highest number of references of vulnerabilities with either Exploit Kit or Remote Access Trojan (RAT) as the malware category, or Phishing as the attack vector. This is a useful query to run for any Recorded Future clients, specifically against vulnerabilities impacting a company’s technology stack. The results will highlight the types of exploits an organization should focus on combating the most, allowing for more targeted research and strengthening their position against future targeted operations.

List of exploit kits in the “Exploit Kits” malware category.

List of remote access trojans in the “RATs” malware category.
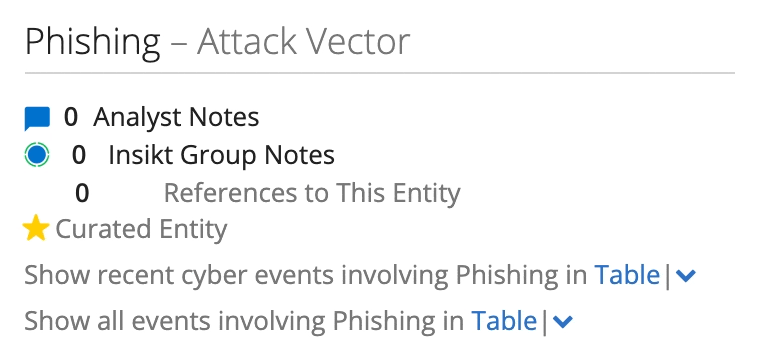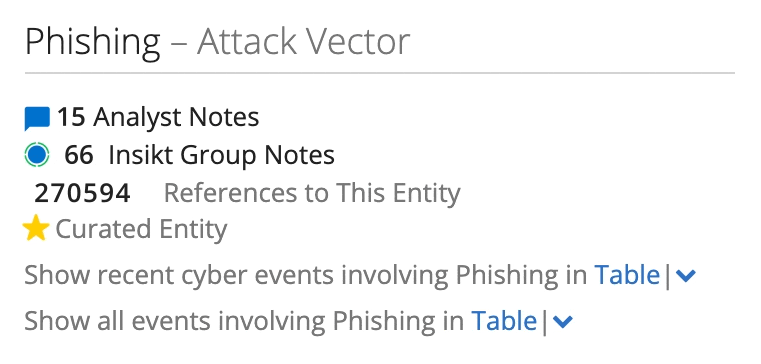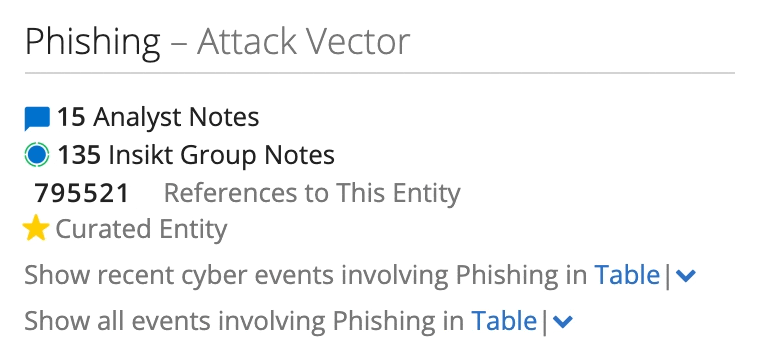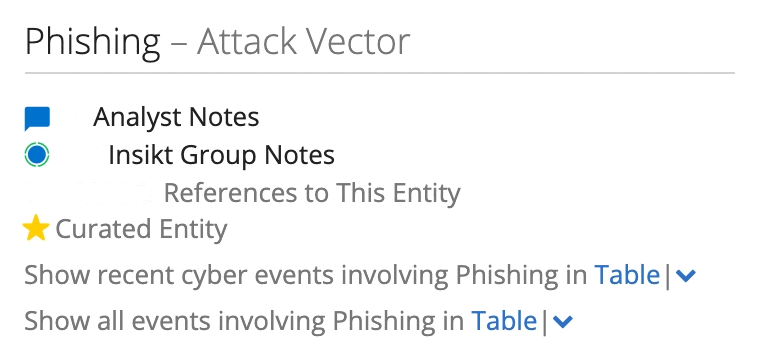
Part of the header for our Phishing attack vector Intelligence Card™.
Step 2
I checked the API results for the top 10 referenced vulnerabilities to ensure that vulnerabilities were correctly associated with exploit kits, RATs, and malware. I removed ones primarily used by nation-state actors after not finding evidence of their use on underground and dark web forums.
Step 3
I also used the API to discover the exploit kits and RATs that were created or first appeared in 2018. This was accomplished by using two raw API queries and comparing the results; a query for all exploit kits and RATs created before 2018 was compared with results from exploit kits and RATs referenced in 2018. An example of the prior query in the raw API is shown in the image below:
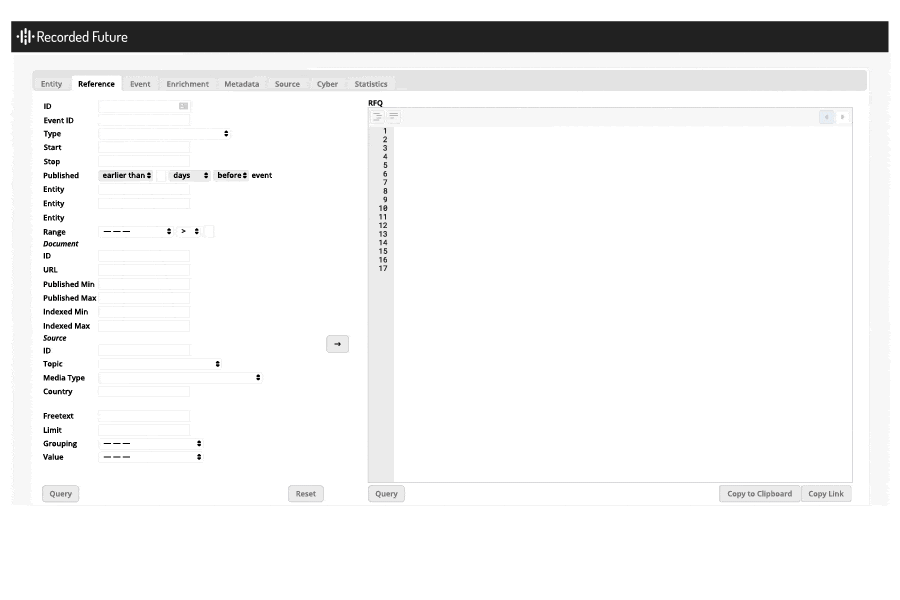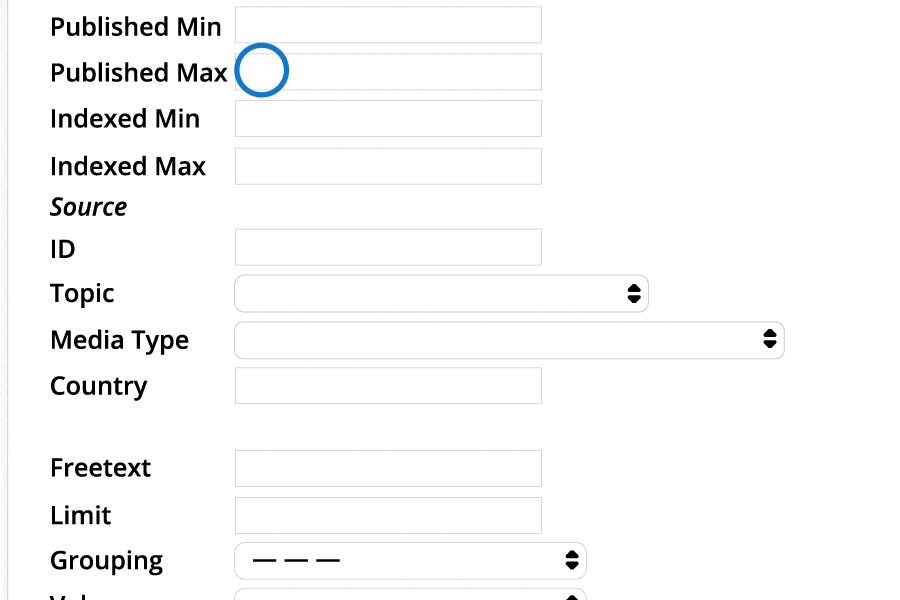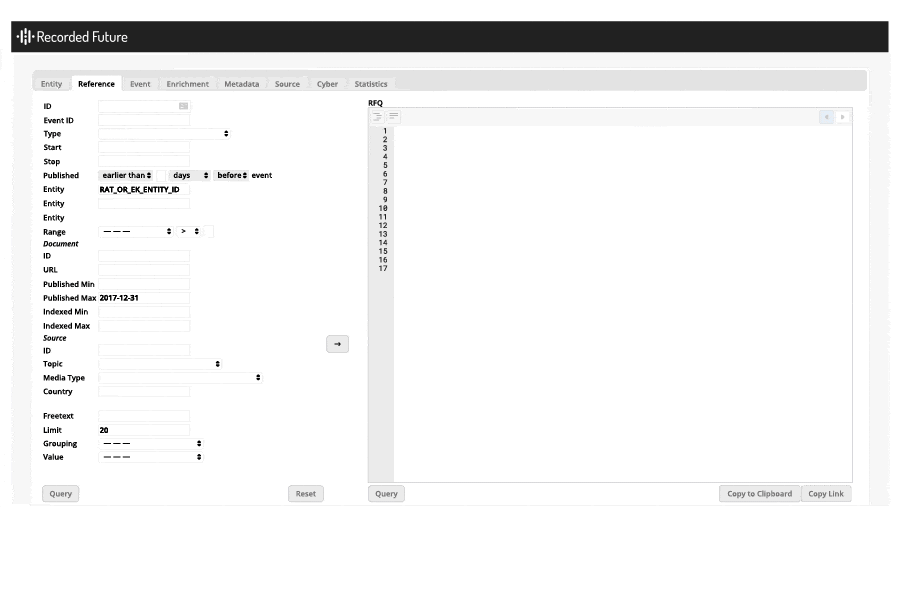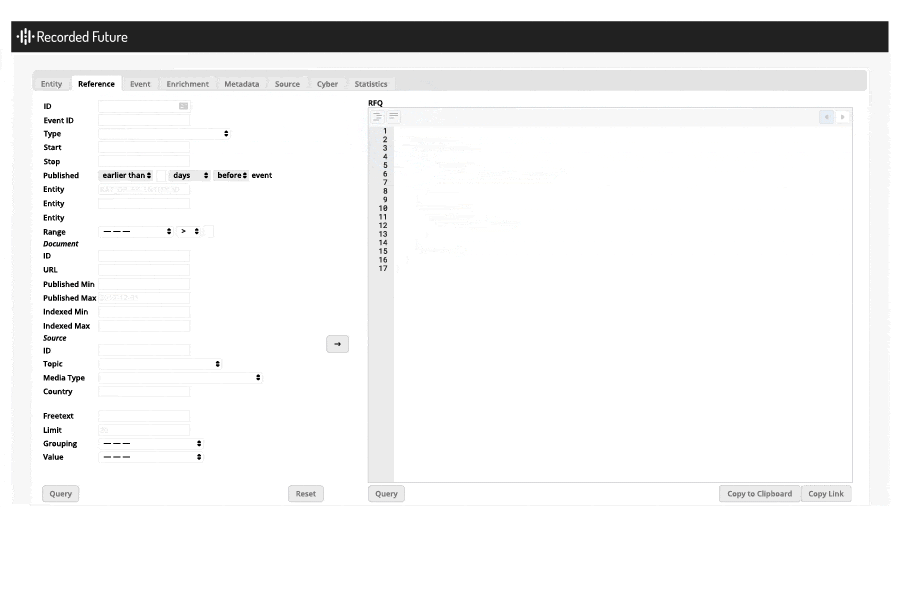
Query using Recorded Future’s raw API.
Step 4
After checking the results, I created a final list of the top 10 vulnerabilities using a Recorded Future list for easy follow-on queries, shown in the image below.
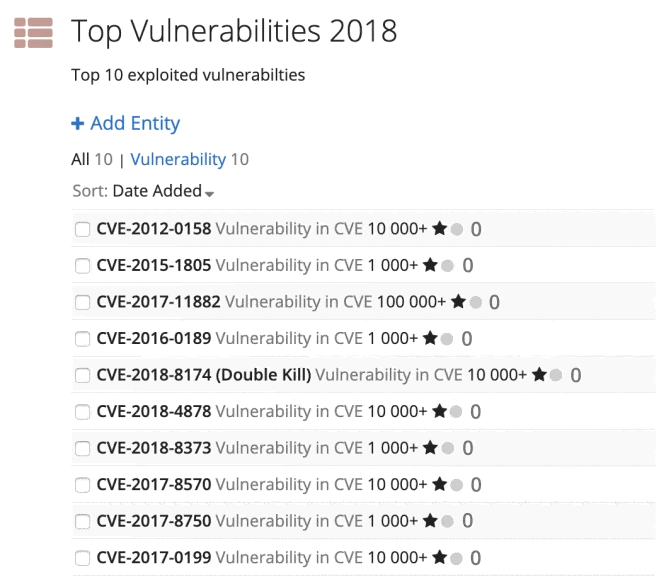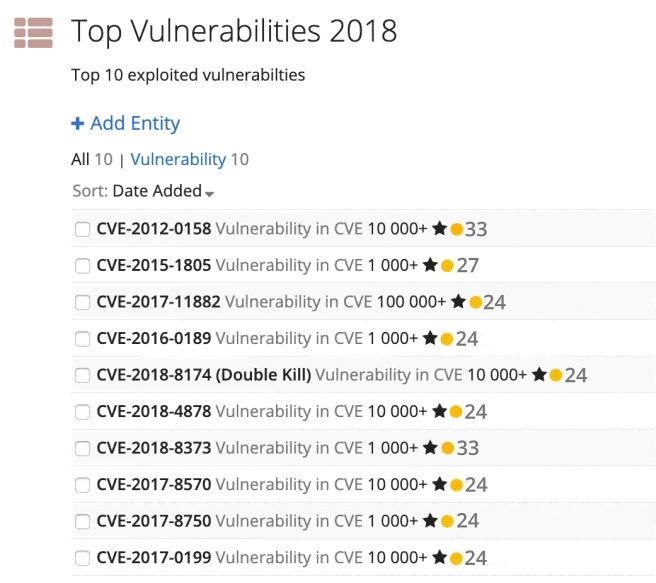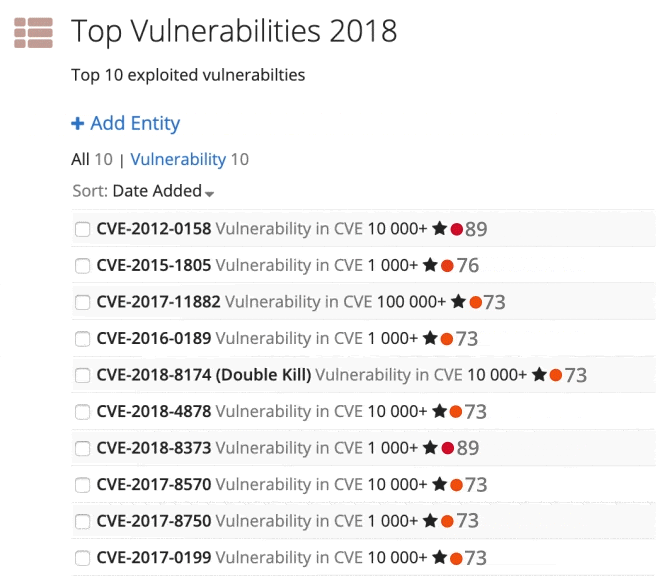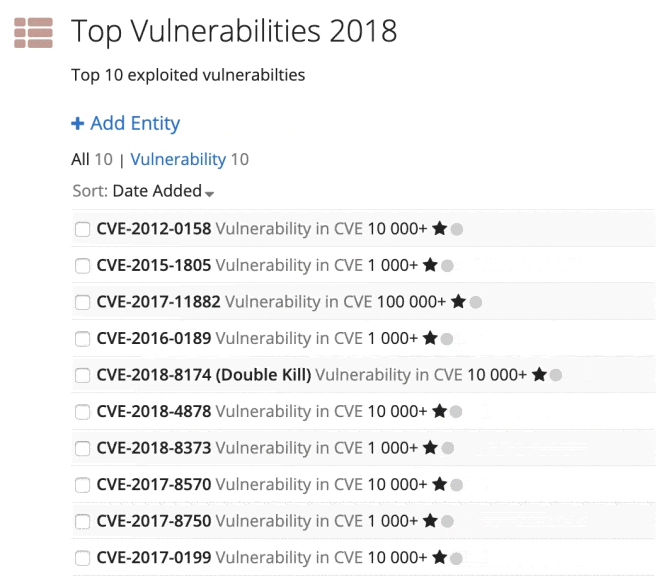
Custom list of the top 10 exploited vulnerabilities.
Step 5
I checked the associated exploit kits, RATs, and phishing references for each vulnerability by using the filter function, noting the number of other associated malware to create the malware number chart, shown below.
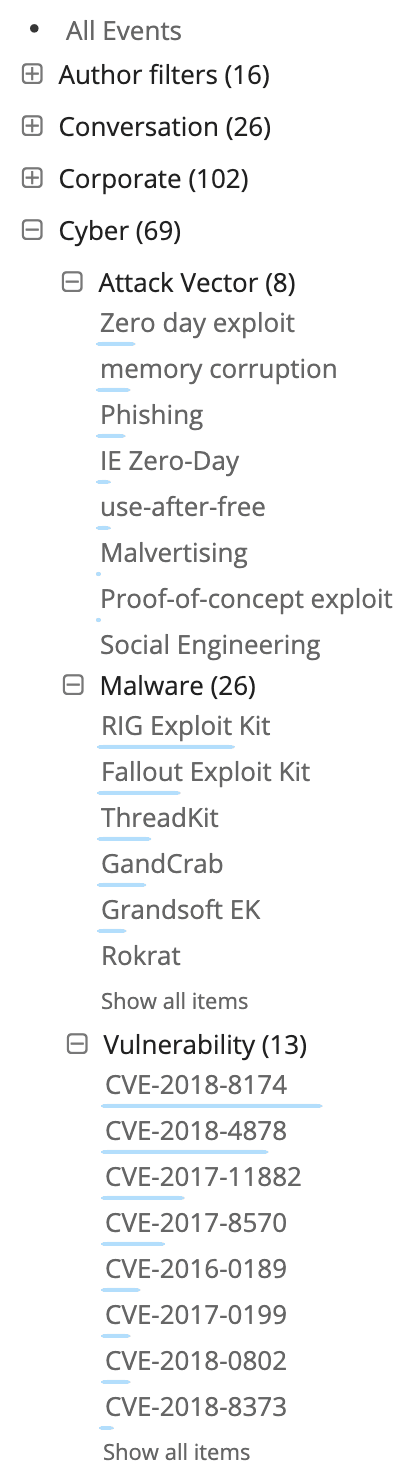
Filters available for pivoting to different results.
Step 6
I ran a query on the exploit kits associated with the top 10 vulnerabilities to see which ones included the most vulnerabilities.
Step 7
I ran a similar query to the one above to find out which vulnerabilities were associated with the most RATs, which resulted in the below list.
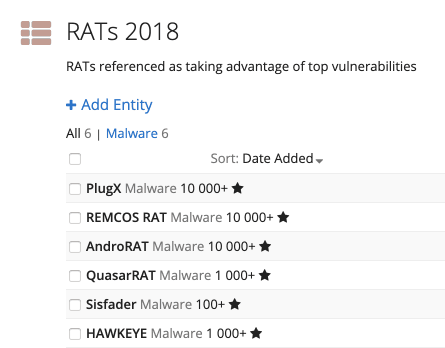
Custom list of RATs associated with top 10 exploited vulnerabilities.
Step 8
I read Insikt Group notes to see the biggest storylines and which exploit kits were primarily used by which groups using a list of the most referenced exploit kits, shown in the images below.
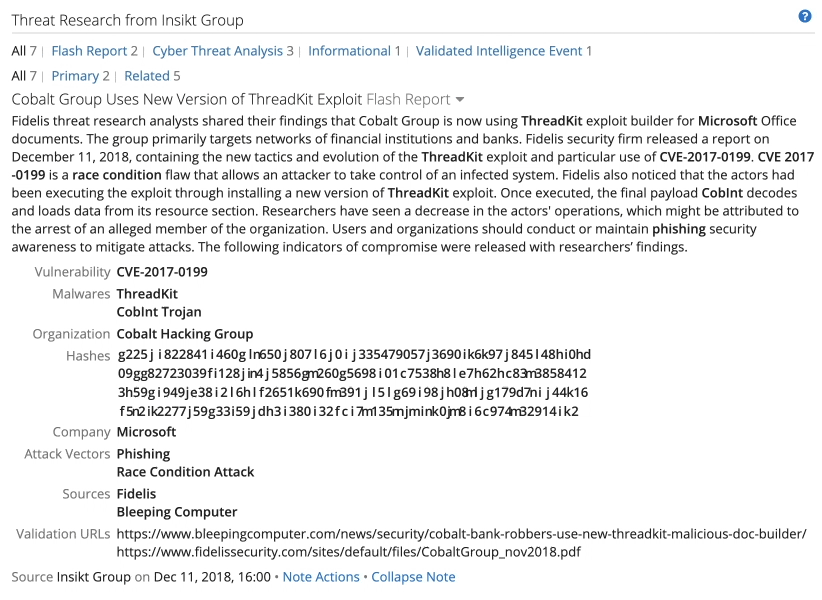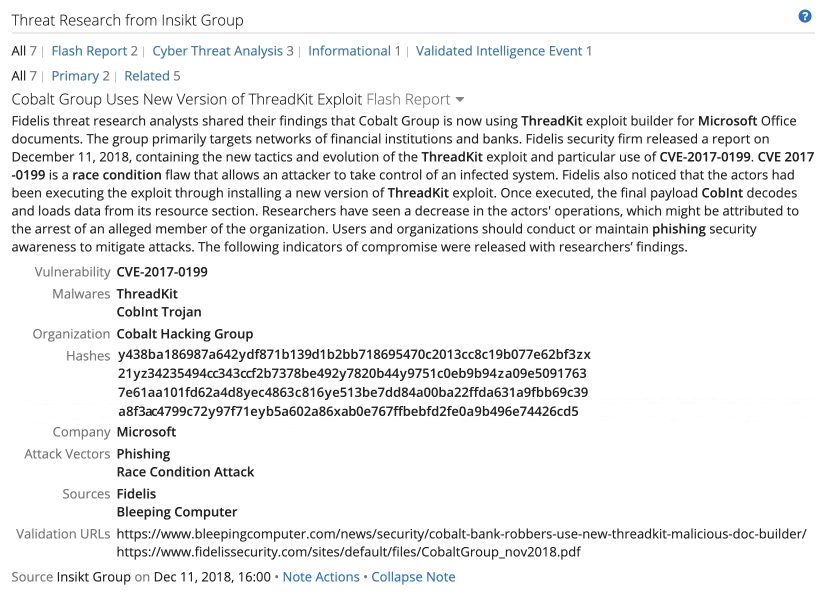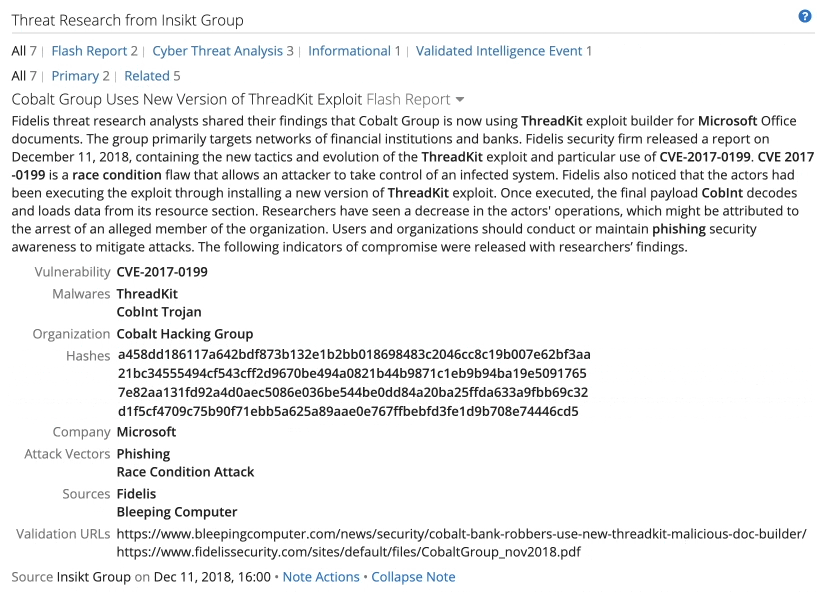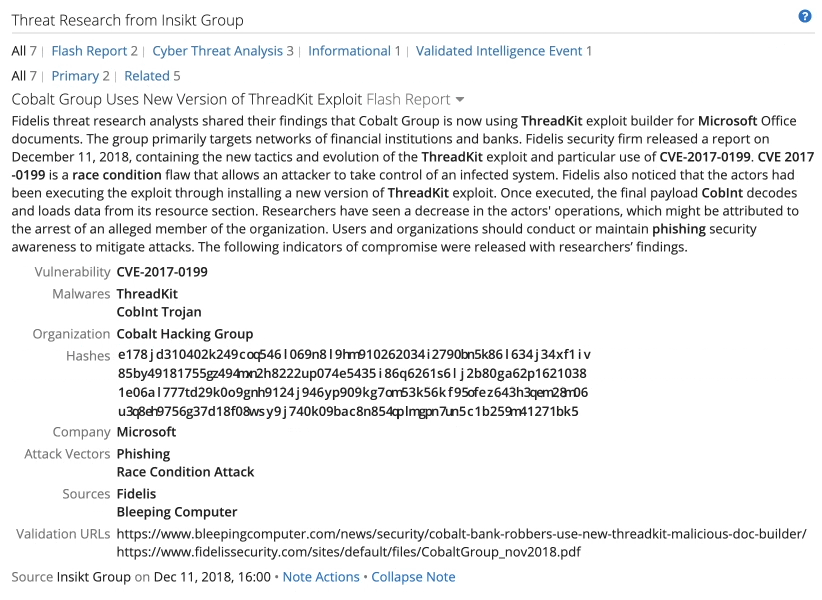
Part of an Intelligence Card™ with Insikt Group research on the ThreadKit exploit kit.
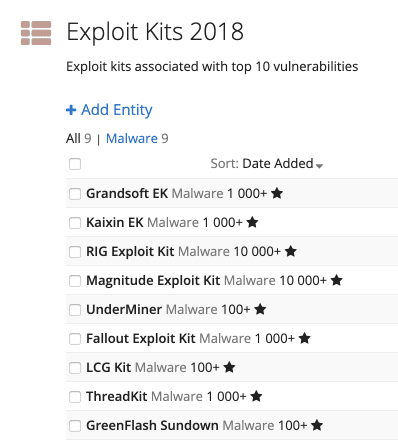
List of exploit kits associated with top vulnerabilities.
Step 9
I researched top-referenced exploit kits mentioned on the dark web for evidence of sale, adding good references to a Reference List to be able to easily come back to the results, shown below.
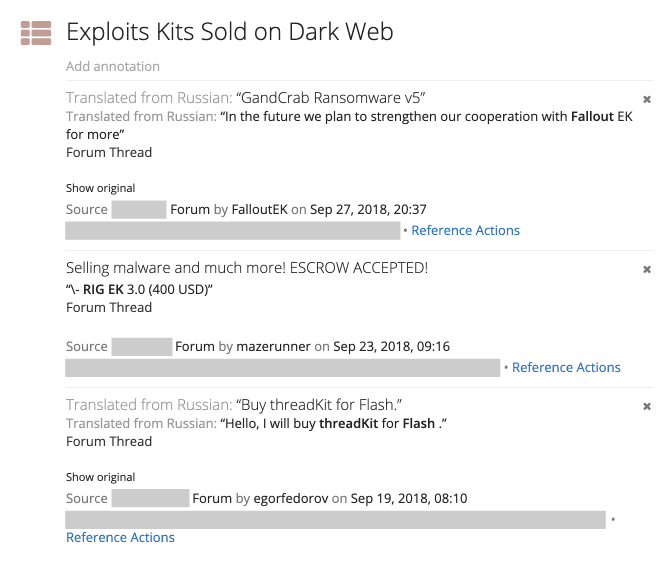
Recorded Future reference list.
Learn More
For more information about how Recorded Future can help organizations better understand and prevent threats, request a personalized demo today.
Related