Enriching User Behavior Analytics With Threat Intelligence
Key Takeaways
UBA is a relatively new, but fast growing, form of security detection that alerts on anomalous behavior, rather than traditional signature matches.
More security teams are adding UBA to their processes because of its effectiveness and ability to weed out the “noise” that troubles traditional detection methods.
While UBA provides a great tool for isolating potential security events, it doesn’t provide context around those events.
Recorded Future threat intelligence can provide context to UBA alerts, tying anomalous behavior to threat actors, or known patterns of attack activity.
User behavior analytics (UBA) — sometimes referred to as User and Entity Behavior Analytics (UEBA) — is a method of detecting malicious activity on a network by correlating information about an organization’s users and entities with anomalous activity.
Even though UBA has been around for several years, it has only recently started to gain traction within the security community. Part of the newfound attention has to do with the fact that processing power and storage have finally gotten to the point that UBA is a viable option in many organizations.
However, the biggest driver of interest from organizations is the fact that traditional security solutions are not working.
UBA as a mechanism for detecting malicious activity within an organization has grown so rapidly that Gartner predicts that over the next three years UBA will become the preferred detection method for organizations that are using it.1 While the UBA market has been dominated by niche players, larger security companies are also starting to get involved. For example HP announced last year that they would be OEM’ing Securonix and both Splunk and LogRhythm now have UBA capabilities added to their SIEM products.
Understanding UBA and Security
UBA grew out of the world of business analytics — in fact, UBA is really business analytics repurposed for security. UBA tools take a different approach to security analytics: rather than looking for specific events, UBA tools focus on anomalous activity. UBA tools monitor user and network traffic over a period of time, gathering and collecting data but not acting on it.
Over time, these tools learn patterns of behavior across the network.
These behaviors can be user behavior: Juan logs into his desktop between 8:55 and 9:10 every morning, accesses these 20 systems throughout the day, then logs off between 4:50 and 5:30 every evening.
The behaviors can also be system behaviors: The human resources file server is normally accessed from these parts of the network between 7:00 AM and 6:00 PM Monday through Friday.
It’s important to note that when discussing UBA and system behaviors that behavior analysis is still user-centric.
UBA solutions include pre-packaged analytics that run algorithms against collected user activity looking for anomalous behavior and can generate alerts based on standard deviation from normal behavior. This means that in the above example, Juan logging into his workstation at 8:00 AM will not generate an alert, but Juan logging into his workstation at 3:00 AM will.
Similarly, the human resources server being accessed from an office in Brazil with no HR presence will also generate an alert, even if the entity accessing has valid credentials from a user in HR.
UBA tools also operate by creating rules based on roles. Existing tools such as Active Directory groups, human resources information, access control lists, and other internal data are used to create rules for users or groups of users. While it can be resource intensive and time consuming, doing this work ahead of a UBA implementation helps better refine the analysis of the UBA tools and makes the learning process that much more effective.
The ultimate advantage of UBA tools is that they provide context around behavior within the organization; they help security teams determine whether behavior is normal or falls outside of normal patterns.<
UBA tools tell security teams that a behavior is anomalous, but they don’t necessarily know if it’s “bad” or, more accurately, what type of “bad” it is. It could be an insider threat, someone from the organization attempting to exfil data, or it could be a targeted attack, with an advanced attacker stealing data that can easily be sold on the black market.
This is where true threat intelligence can provide additional context to UBA alerts.
Recorded Future threat intelligence can help to better define what that bad behavior is, whether it’s correlating anomalous activity on the network that originates from a known Tor node or enabling security teams to match the hash of a file executed on a workstation against known malware.
Providing Context to UBA Alerts With Threat Intelligence<
To understand how threat intelligence can provide that additional context it’s important to take a step back to explain how modern attacks, especially advanced attacks, work.
While a <a href="https://www.recordedfuture.com/threat-actor-types/>threat actor may use an exploit to gain access to an organization, once inside that actor will use the same tools that the network administrators use to move around the network. To a modern threat actor tools like PowerShell, PSExec, and TaskManager are just as valuable as any zero-day exploit in their arsenal.
This means that an attacker, at least superficially, looks a lot like a normal user on the network. But, attacker patterns are, by their very nature, distinct from normal user activity — even if those activities appears normal at first glance. An attacker may be accessing the network at odd times, or using an administrator’s credentials to query a SQL database.
UBA tools detect a number of anomalous activity, but not all of them. For example, a user accessing the network over a VPN is normal activity, but what if the user is accessing the network over a VPN from an IP address originating in China? That’s unusual, and will be flagged by most UBA tools.
On the other hand, what if that IP address is based in the United States, but is a well-known Tor exit node, that’s one way that a threat intelligence overlay from Recorded Future can improve the effectiveness of UBA tools.
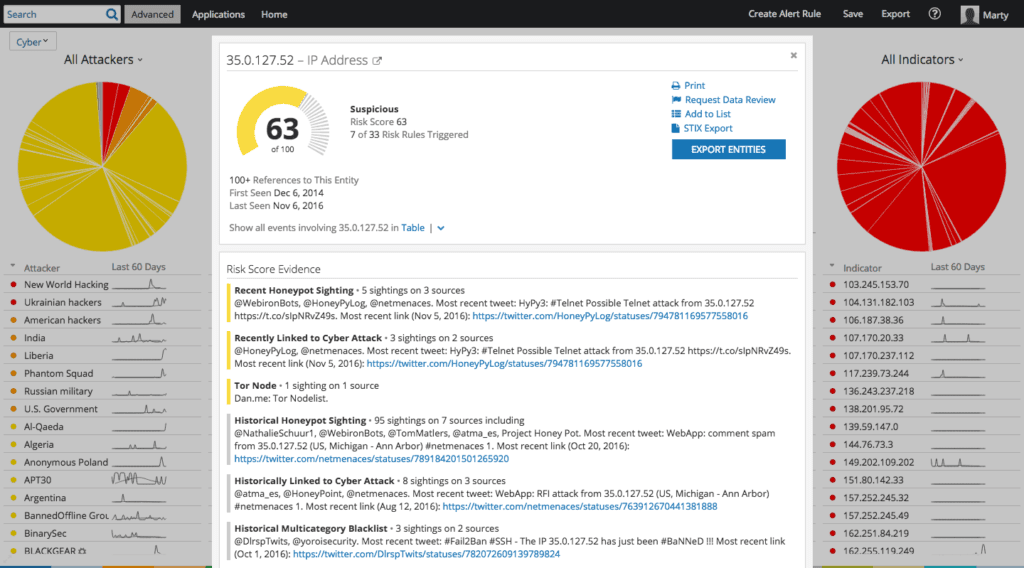
Intelligence Card™ for known Tor exit node IP address registered to a U.S. entity.
Threat intelligence from Recorded Future can be even more effective against advanced threat actors because it provides external context to anomalous behaviors. Especially against advanced threat actors just flagging behavior as anomalous doesn’t necessarily make a security team more effective.
Threat intelligence helps security teams track down the point of origin of the attack and completely remove the threat actor from the network. Thus, avoiding the trap of playing “whack-a-mole” security against an advanced threat actor.
UBA and Advanced Threat Actors
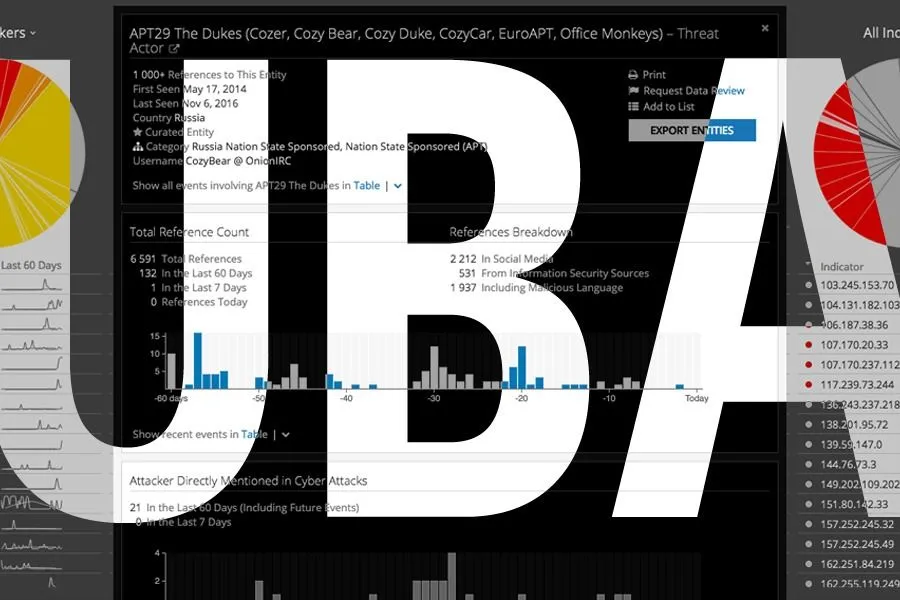
Recorded Future provides curated threat intelligence about hundreds of well-known threat actor groups, such as APT28, Deep Panda, and Poodle Corp, which can provide security teams using UBA tools with the necessary context to respond to an incident faster and more effectively.
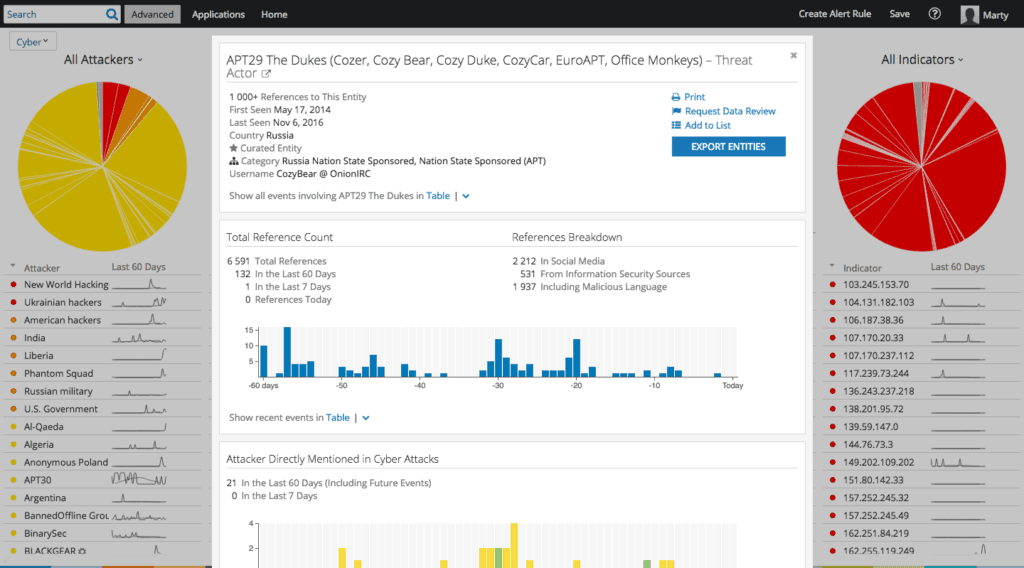
Intelligence Card™ for APT29 (Cozy Bear).
Let’s see how this works with a simple example.
A security engineer in a security operations center (SOC) is alerted to the fact that a legitimate network administrator was using PSExec at 2:00 AM to tell another machine on the network to execute a file with the MD5 hash 95b3ec0a4e539efaa1faa3d4e25d51de.
A quick search in Recorded Future shows that this hash is associated with threat group Cozy Bear (APT29). The Intelligence Card™ for Cozy Bear shows that one of the tactics, techniques, and procedures (TTPs) for this group is that they rely on PSExec to move around the target network once they gain access. Now the SOC analyst knows that the activity is malicious.
She can stop the immediate activity and use the rest of the threat intelligence that Recorded Future has in the Cozy Bear Intelligence Card™ — including predictive risk IP addresses, domain names, file hashes and their related data, any publicly available IDS/IPS signatures, and CVEs — to start hunting for other compromised systems.
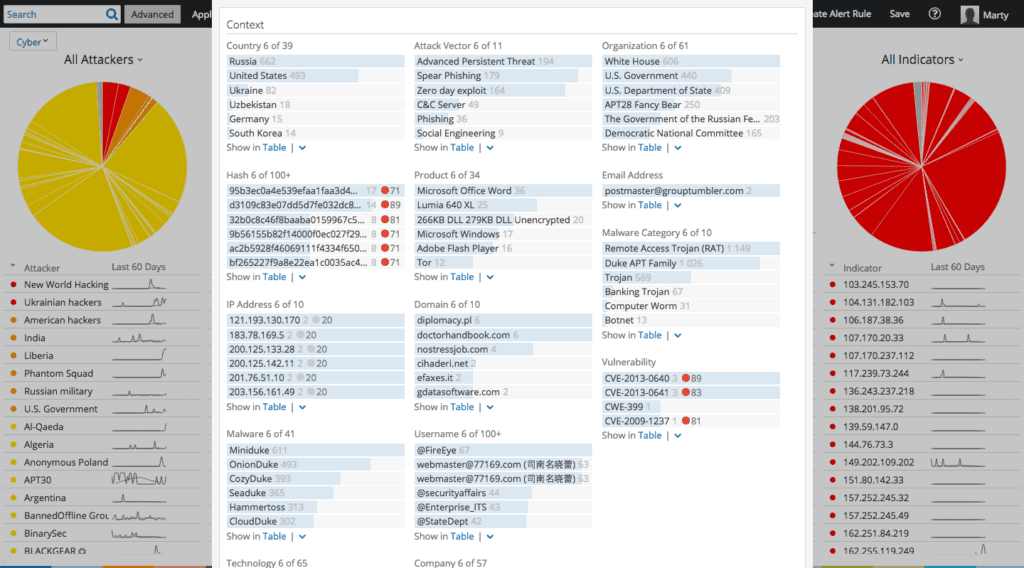
Context for threat actor APT29.
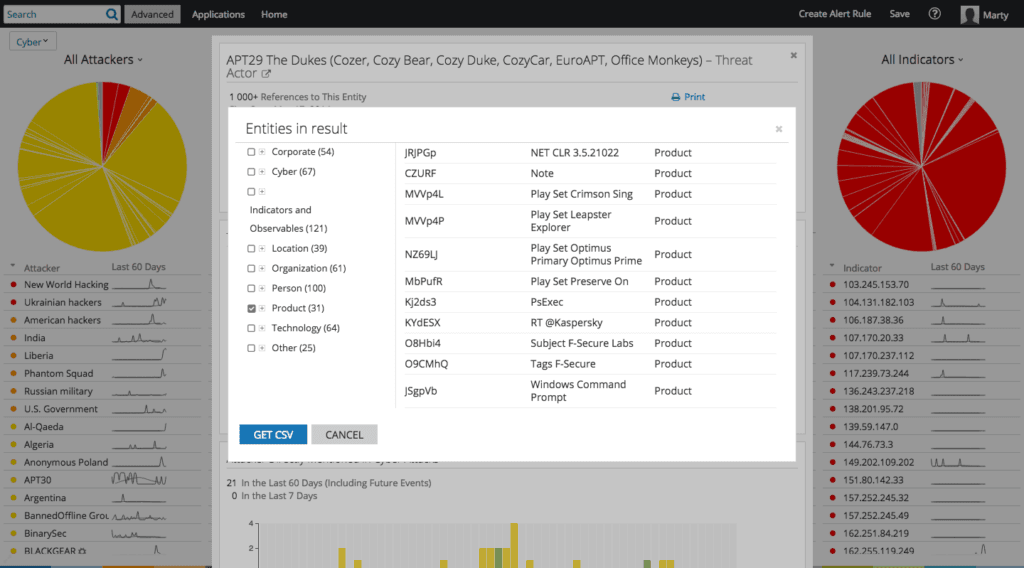
List of APT29’s associated products.
In short, UBA is a powerful tool for detecting malicious activity in an organization, but UBA works better when it’s informed by comprehensive threat intelligence.
Using Recorded Future threat intelligence as an overlay to UBA alerts helps security teams distinguish between malicious insider behaviors and threat actor activity. It also provides security teams context around the nature of threat actor activity, not only isolating threat actors but also providing related TTPs and IOCs (indicators of compromise) that help the security team with the hunt mission.
1 “Market Guide for User and Entity Behavior Analytics,” (Gartner; Sept 22, 2015; Avivah Litan [G00276088]).
Related