Russian-Related Threats to the 2020 US Presidential Election

Editor's Note: The following post is an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
In this report, Recorded Future provides an overview of Russia-nexus cyberespionage and influence operations activity related to the 2020 U.S. elections, including from advanced persistent threat (APT) groups, information operations (IO) entities, as well as likely front entities and non-state groups aimed at presidential candidates, political parties, elections infrastructure, media platforms, voting efforts, and the U.S. population at large. Assessments provided in this report are based on content in the Recorded Future Platform® and data from social media sites, local and regional news sites, academic studies, information security reporting, and other open sources available between January 1, 2020 and August 25, 2020. We compared this to historical data to determine changes in tactics, techniques, and procedures (TTPs) to reveal cyber threats, information operations (IO), and hybrid threats that incorporate aspects of both cyber and IO actions.
Executive Summary
The threat landscape of the upcoming election differs from 2016 and 2018; threat actors and activity groups who previously targeted elections have largely remained on the sidelines. Consistent with 2016 and 2018, however, is that Russia continues to pose the greatest threat to the 2020 U.S. presidential elections, based on past success in conducting phishing and cyberattack operations, a relentless persistence in directly targeting U.S. democratic institutions and organizations, and the conducting of information operations targeting the U.S. electorate via conventional and social media.
Contemporary Russian-directed information operations against the United States have been ongoing since at least 2016, with activity becoming more distributed internationally. Additionally, Russian threat activity groups continue to expand infrastructure and develop malware and exploits, but have been less active in targeting elections-related entities. Despite the lack of observable Russian state-sponsored hack-and-leak operations since January 2020, we cannot rule out the possibility of a leak appearing before the November election, given how damaging such activities were in advance of the 2016 vote. Russian threat actors and activity groups likely will continue to conduct cyberattacks and pursue information operations against the U.S. electorate up to, and even after, election day.
Unattributed threats to the election also remain a significant concern, the most salient of these being burgeoning conspiracy theories and their adherents in the form of the QAnon and Boogaloo movements. Additionally, non-attributable activity from cybercriminal or other elements possess capabilities to disrupt or harm the U.S. election and warrant constant vigilance on dark web and underground sources.
Key Judgments
- Russian advanced persistent threat groups likely pose the greatest threat to the 2020 U.S. presidential election, despite a lack of identified activity against these targets to date; this assessment is based on past efforts against the 2016 and 2018 U.S. elections as well as identified retooling, development, and ongoing activity by U.S. and U.K. intelligence agencies.
- Information operations likely continue to play a major role in disrupting the U.S. domestic social and political environments ahead of the election; ongoing research initiatives from Stanford Cyber Policy Center, Graphika, and others have described how these efforts have evolved since 2016 and indicated how such operations continue to target elections internationally to disseminate deceptive information.
- Although no election-related hack-and-leak operations linked to Russian threat actors have been identified to date, it remains likely that such content could appear in advance of the election; there is historical precedent for entities like APT28 to distribute such data in a delayed manner.
- Ransomware likely poses an additional threat to elections-related infrastructure; carefully timed ransomware attacks within key battleground states have the potential to cause some limitations but are deemed unlikely to fully disrupt the 2020 election.
- Non-state groups also likely pose an information operations, influence, or protest threat to the elections; although not directly linked to Russian threat actors, Russian overt and covert influence operations have taken an interest in these groups and are amplifying their content and could potentially hijack or leverage these groups to conduct disruptive activities.
- The U.S.’s defensive posture and response to real or perceived cyber operations can present challenges for any would-be attackers, but is unlikely to completely deter any determined threat group.
Russia-Sponsored Elections Interference Efforts: 2016 and 2018
In 2016 and in 2018, Russian state-sponsored threat actors conducted an unprecedented campaign against the United States presidential and midterm elections, targeting political parties, candidates, and infrastructure associated with the vote. A U.S. government investigation into the intrusions, information operations (IO), and other corresponding activities, conducted by Robert Mueller III, revealed that the effort was primarily led by entities associated with the Main Intelligence Directorate (GRU, also called the Main Directorate [GU]) with support from organizations like the Information Research Agency (IRA). The Russian Main Directorate/Main Intelligence Directorate of the General Staff of the Armed Forces is the primary military intelligence entity within the Russian Federation. This organization conducts strategic and tactical foreign intelligence tasks for the Russian government. It is composed of subunits, several of which are engaged in cryptography, signals intelligence, disinformation, and intrusion activity. The IRA is a commercial media entity that has specifically been engaged in social media influence operations.
Threat Actors
Ahead of the 2016 U.S. presidential election, three Russian state-sponsored advanced persistent threat (APT) groups were involved in targeted intrusion activity; some of these threat actors also acted as “hybrid threats,” due to their involvement in information operations as well as targeted intrusions. The primary threat actors were identified as APT28, APT29, and the Main Intelligence Directorate/Main Directorate (GRU/GU) Unit 74455, which is tracked as Sandworm.
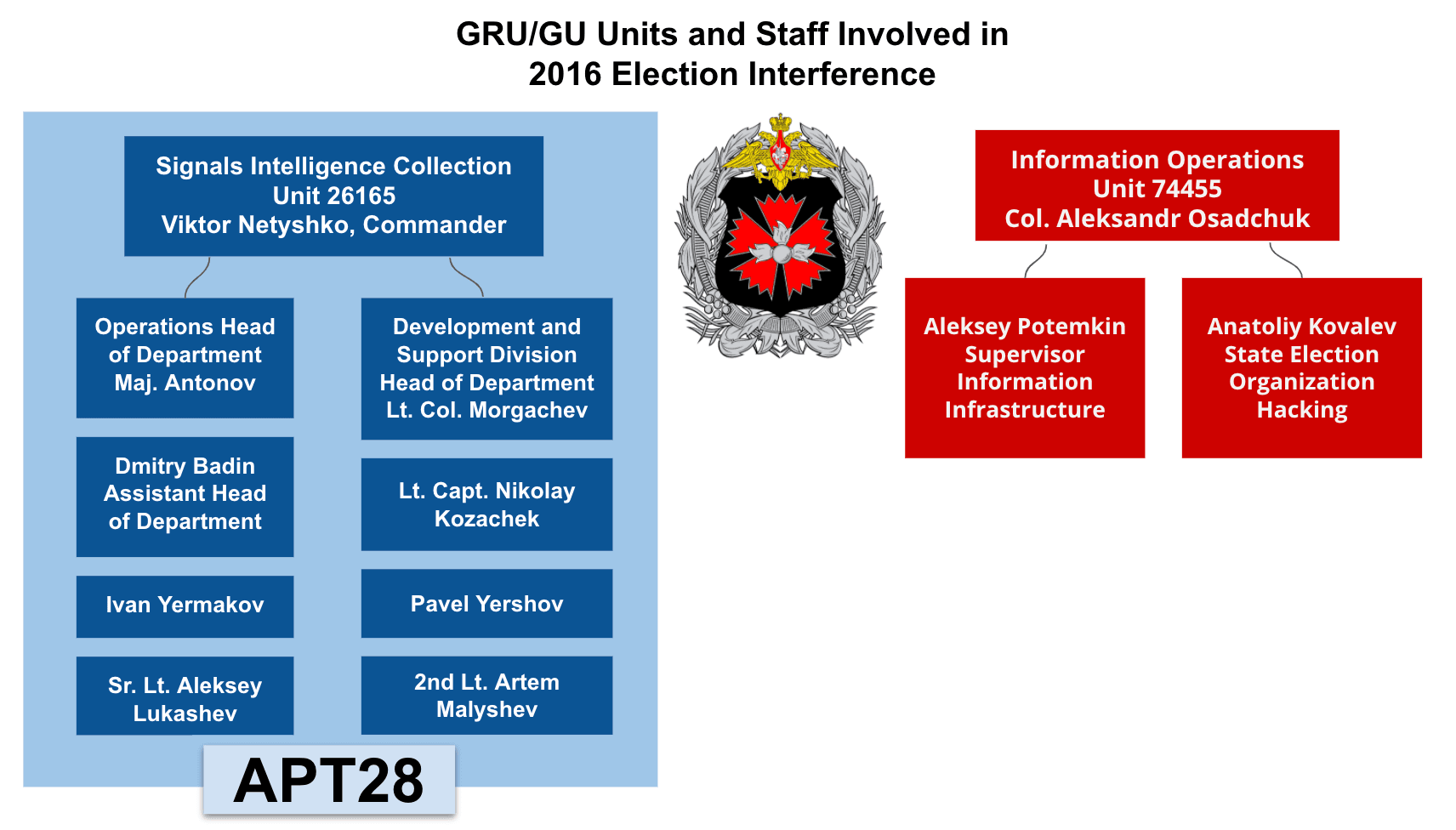
Organizational chart of GRU/GU units involved in 2016 election interference (Source: Ars Technica)
APT28 and APT29 were engaged in targeted intrusions against the DNC, DCCC and other elections-related individuals and organizations. Additionally, personnel from GRU/GU Unit 26165 were identified in a Department of Justice (DoJ) indictment in association with both the APT28 activity, as well as engaging in separate, information operations efforts. Personnel from GRU/GU Unit 74455 — the organization associated with Sandworm activity — was also indicted by the DoJ for their role in elections interference efforts (such as hack-and-leak operations); however, none of the custom malware attributed to Sandworm was identified on networks impacted by the intrusions. For that reason, efforts to interfere with the 2016 election conducted by this organization are identified by unit name (Unit 74455) as opposed to threat activity group designator (Sandworm).
Several other Russian groups have been linked to election interference activities:
- On January 25, 2018, the Dutch Intelligence Agency (AIVD) publicly shared information identifying APT29 operators engaged in intrusions against the Democratic National Convention (DNC) and connecting it to the Russian Foreign Intelligence Services (SVR). The SVR is responsible for foreign espionage, active measures, conducting electronic surveillance in foreign nations, and more.
- Also in 2018, Estonian Intelligence Services released reporting that APT29 operations were associated with both the SVR and the Russian Federal Security Service (FSB).
- According to a Department of Justice indictment, two GRU/GU military units associated with APT28 and Sandworm — Unit 26165 and Unit 74455, respectively — used false front actors DCLeaks, Guccifer 2.0, and AnPoland, as well as employed Wikileaks, to launder exfiltrated data and to claim responsibility for intrusions against targeted resources.
- Finally, Russian-based troll farms — most notably the Internet Research Agency (IRA) — conducted mass dissemination of disinformation or inflammatory material in order to destabilize the U.S. domestic social environment ahead of the election, working as a force multiplier for other operations conducted by APT28, Sandworm, and APT29.
In 2018, some of these same threat activity groups and influence operations targeted the U.S. midterm elections. APT28 conducted spearphishing operations aimed at three candidates running for legislative office. Although it is unclear if these efforts were successful, Microsoft released information identifying the likely targets of this activity as the U.S. Senate, a political think tank, and a political non-profit. The DoJ also brought a criminal complaint against Russian influence operations entities for “...advertisements on social media platforms, registration of domain names, the purchase of proxy servers, and “promoting news postings on social networks,” among other things. The U.S. reportedly took action to deter the latter by targeting the St. Petersburg-based IRA, taking them temporarily offline. Although some of their operations were purportedly disrupted, Russian efforts to target American democratic processes remained largely undeterred and, even at that time, it was apparent that the Russian state-sponsored threat actors were adapting their strategy.
Tactics, Techniques, and Procedures (TTPs)
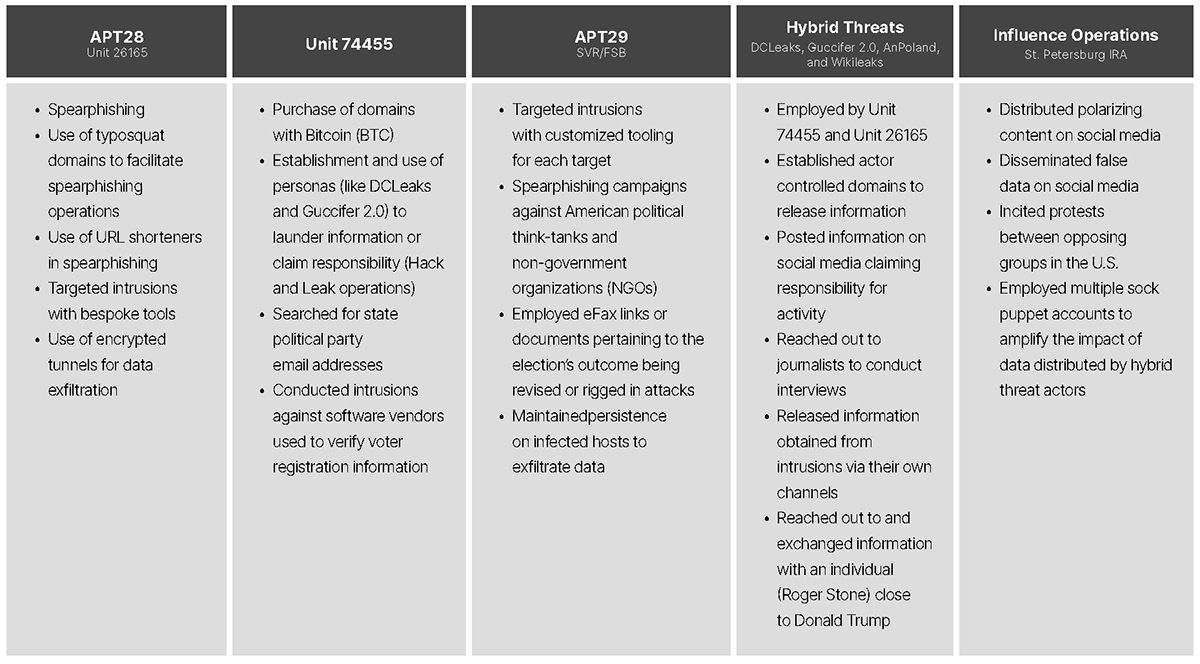
Some of the main TTPs conducted by these threat groups in both the 2016 and 2018 elections can be broken down as follows:
Victimology
These groups targeted a wide range of U.S. democratic institutions. In the 2016 presidential election, threat actors targeted political parties, candidates and campaign staff, elections contractors (such as VR Systems), states’ boards of elections, voter registration data, charitable foundations, and think tanks, and the American populace as a whole. In the 2018 midterm election, the scope of the targeting was largely narrowed to candidates and campaign staff and Americans on social media. A narrowing of the target scope may have been the result of limitations to threat actor operations due to increasing security around vulnerable elections infrastructure, a byproduct of the midterm elections being viewed as less consequential to the threat actor, or the result of a lack of necessity (i.e. it may not be necessary to conduct intrusions into infrastructure hosting voter registration data frequently as that information does not change drastically in short spans of time).
Threat Actor Activity Since January 2020
Since January 2020, several Russian APT groups have been active against U.S.-based entities not related to the elections, as well as international entities with a potential nexus to the election. Although Recorded Future has not identified any direct intrusion activity by threat activity groups against U.S. elections infrastructure, candidates, political parties, or voting efforts as of this writing in advance of the 2020 presidential election, that does not preclude such efforts from materializing. Recorded Future has found that, in this same time frame, Russian APT groups have been developing malware which could potentially be used to target elections-related entities. Furthermore, Recorded Future identified infrastructure development, evolving TTPs, and changes to malware during this same time frame.
Although it is very likely that Russian threat actors have improved their operations, these threat groups have also continued to use some of the same approaches to intrusions that they have historically applied. Therefore, changes to operations and shifts in behavior are likely not indicative of a wholesale abandonment of previous tools, but rather an example of both flexibility in adapting operations when necessary and pragmatism in ensuring the mission is completed successfully.
Activity Targeting the Candidates and Political Parties
It is likely that threat actors maintain an ongoing interest in the candidates, their affiliates, and the U.S. political parties more broadly because of their role in the campaign or their relationships with those involved in the election. This assessment is based, in part, on a report which indicates that the Russian government is attempting to interfere in the 2020 U.S. presidential election. The reporting did not elaborate on what interference efforts would entail; however, Recorded Future searched for any Russian state-sponsored threat actor activity aimed at incumbent President Donald Trump, his family, or high-profile individuals associated with the campaign since January 2020, but found no references to any such efforts as of this writing. Open-source searches likewise did not yield any relevant content. We also searched for any activity attributed to Russian state-sponsored threat actors aimed at former Vice President Joe Biden, Senator Kamala Harris, the Biden family, the Harris family, or other high-profile individuals associated with the campaign since January 2020. There were no indicators of intrusion activity against these individuals.
Since January 2020, there have been no indications of Russian APTs targeting the Republican National Committee (RNC), National Republican Congressional Committee (NRCC), or the National Republican Senatorial Committee (NRSC). Similar research into Russian APT groups’ targeting of the DNC or the Democratic National Convention Committee (DNCC) identified a total of 20 instances — all to historical items; none were indicative of any present or imminent threat aimed at the DNC or DCCC. Although these searches do not appear to reveal any ongoing or imminent threat against the political parties, as of this writing, it also does not preclude such efforts from the list of potential threats either. These references may be summarized generally as follows:
- Two results were references in social media to historical reporting associated with the 2016 intrusion into the DNC.
- At least six of these references were found in forum posts focused on disputing the assessments and findings of the intelligence community and information security industry in attributing the 2016 U.S. presidential election interference operations to Russian APT groups.
- One local news website also disputed the intelligence community findings.
- 10 references were to news websites or court documents associated with the reporting of Russian APT activity against the 2016 U.S. presidential election.
- One item that referenced this activity has since been removed from social media.
Threat Actors
APT28
Since January 2020, APT28 has engaged in a number of activities, such as infrastructure development, attempted spearphishing, and malware development. Of these, only spearphishing has a potential nexus to the election, specifically an alleged phishing attack against Burisma Holdings.
Attempted Spearphishing Activity
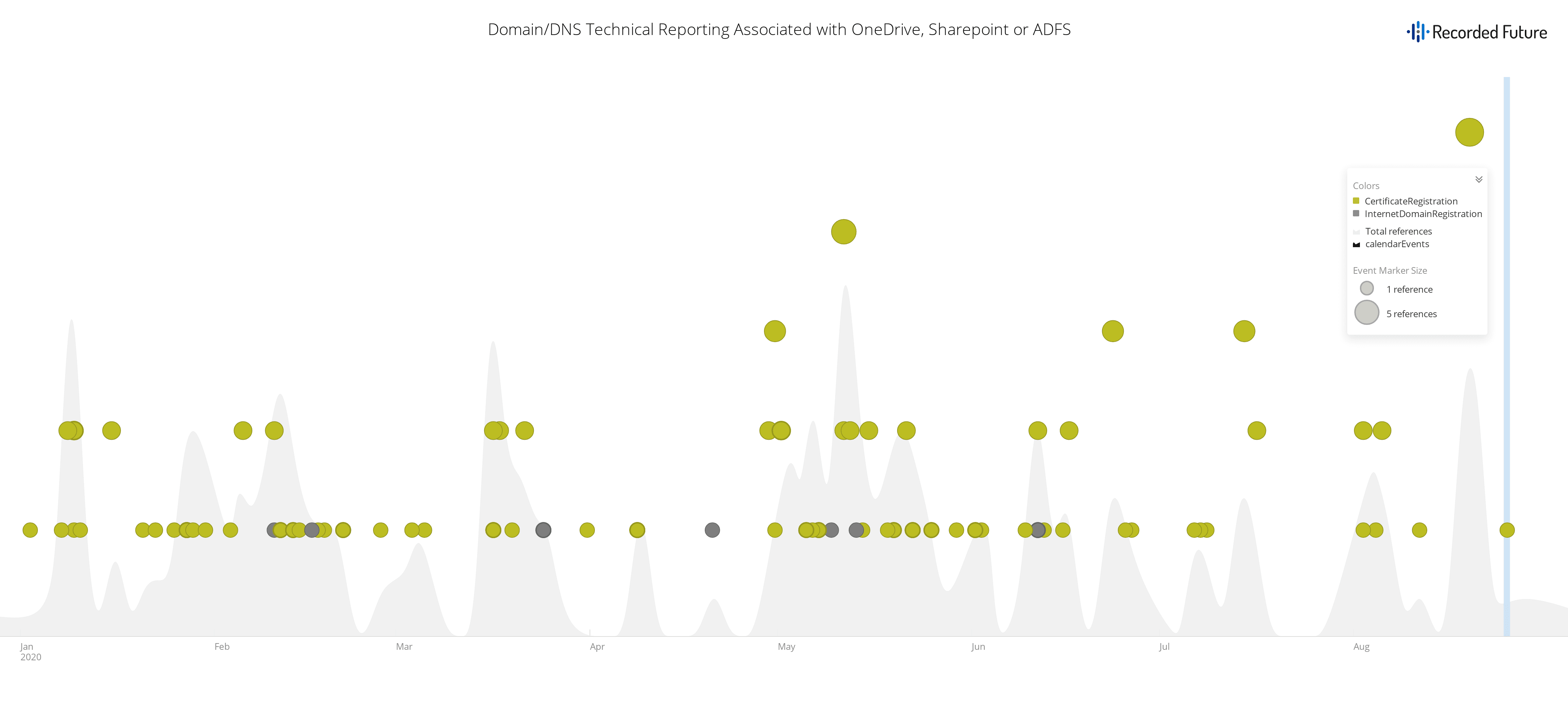
On January 13, 2020, cybersecurity firm Area 1 released a report titled “Phishing Burisma Holdings,” which outlined spearphishing attempts they attribute to the GRU/GU against Burisma Holdings, an energy company in Kiev, Ukraine. According to the report, the campaign, active since at least November 2019, employed domains which mimicked those used by legitimate partners or subsidiaries linked to Burisma Holdings. Burisma Holdings is of particular interest, as Joe Biden’s son Hunter Biden previously served on the board of Burisma Holdings. A simultaneous effort unrelated to the phishing attempt, as reported in the Washington Post, detailed multiple attempts by current U.S. administration affiliates to solicit information regarding audio recordings of Biden in relation to former Ukrainian president Petro Poroshenko. This activity included the solicitation of information from Andriy Derkach, a Ukrainian parliament member with ties to Russian-sympathetic groups.
One of the TTPs described in the Area 1 report includes the use of websites which mirror genuine login pages across multiple attack surfaces (for example, mimicking a Roundcube installation and Outlook 365 logins via Sharepoint) in an effort to obtain credentials for the targeted entities. This TTP aligns with previous methodologies employed by APT28 during the 2018 U.S. midterm election as well as the 2016 U.S. presidential election. In the course of the campaign, the threat actor leveraged various email-related authentication technologies to establish legitimacy. In particular, the threat actor used Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) (cryptographic hash), both of which are used by a recipient to verify the identity of a sender. In doing so, the threat actor registered their SPF with a yandex[.]net Mail Exchange (MX) record, suggesting this action was conducted by a Russian-based threat actor.
APT28 has previously conducted “hack and leak” type operations, targeting entities to obtain sensitive information which is later dumped in an effort to harm either the targeted entity or affiliated organizations and individuals. These have included efforts against the campaign of former Secretary of State Hillary Clinton during the 2016 U.S. presidential election, in addition to organizations associated with international sports during the 2016 Olympics. Given its involvement in these campaigns and the nexus between Burisma Holdings and the U.S. and Ukrainian political climates, chances are about even that this threat activity group is conducting this campaign in an effort to obtain information for later distribution as part of an information operation.
Screenshot of Sharepoint, ADFS, OneDrive domain and certificate registrations (Source: Recorded Future)
Outlook
U.S. officials or organizations have a greater awareness of and are more prepared for the potential of foreign interference to the November 2020 elections. Russian threat actors or activity groups are likely sensitive to measures the U.S. has taken to defend the 2020 elections and factoring that into their calculus. Based on these changes, it is likely any threat activity that may emerge from Russia against the 2020 U.S. presidential election will manifest differently from past efforts.
Russian threat activity groups who had conducted intrusions and operations against political parties and candidates in 2016 and 2018 have largely refrained from acting as of this writing. Although there has been no identified activity from Russian threat activity groups against elections-related entities yet, there has been activity by these groups in relation to malware development and intrusions against other entities in the U.S. Additionally, there have been attempts to spearphish entities abroad that have a nexus to the election, due to their association with Democratic presidential candidate Joe Biden. It is unclear at the time of writing if those efforts were successful. Recorded Future notes that, in a separate effort, some audio content has begun to be released that appears to relate to Biden, although this content has not been validated by third-parties as authentic or unaltered. Given that threat activity groups like APT28 have previously waited to release information they have obtained via targeted intrusions in order to maximize their impact, it is possible that a similar approach to delayed information release could occur in advance of the election.
Information operations are much more amenable to threat actor anonymity and very difficult to combat. Recorded Future observes that such operations remain an ongoing and real threat to the 2020 U.S. presidential election. Recorded Future has identified how the presence of Russian domestic and foreign operations conducted by the One Africa, One Success WhatsApp group, EBLA, and troll farms in Nigeria and Ghana reveal a shift away from more centralized and controlled operations to distributed and resilient information operations networks. Although many such efforts have been identified and taken down, there are still likely more remaining, operating unseen. While the fragmentation of such operations could point to the success of a U.S. operation to disrupt IRA influence efforts during the 2018 U.S. midterm elections, it is likely that they also reveal a degree of persistence and resilience of these operations, in the near term.
Russian threat actors or activity groups actively sought to use domestic American assets to bypass social media’s increasingly difficult advertising restrictions against foreign nationals, as well as to increase the difficulty in accurately detecting false personas or personas influenced by nefarious objectives. As social media platforms continue to limit the availability of advertisements and ability for foreign nationals to engage in U.S. political discourse, we continue to expect that engagement with Americans will remain a priority by Russian influence operations assets to bypass ad restrictions, establishing intelligence assets, and astroturf divisive content.
The expansion of conspiracy groups like QAnon or anti-government groups like the Boogaloo movement pose an additional threat to the election. These leaderless groups have the potential to be infiltrated and co-opted by a foreign threat actor seeking to disrupt the election. Adherents to the QAnon conspiracy have already displayed a willingness to engage in “information warfare” and several of their followers have committed criminal acts. In a similar fashion, several adherents to the Boogaloo Movement have committed murder or attempted murder and attempted domestic terrorism in the hopes of acting on their anti-government creed, to bring about a second U.S. civil war. The group has had a visible presence in recent “reopen” and BLM protests, appearing in body armor and heavily armed. This group presents itself both as a physical threat to election security, should the group choose to target election-related assets or polling places, as well as an online threat to spreading disinformation, which could eventually skew towards election related topics in an anti-government narrative.
Editor's Note This post was an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
Related
