Steps to Applying Threat Intelligence

It’s human nature to assume that more of something is always better than less. But the enormous mass of data points from a typical threat feed can often lead to nothing more than “alert fatigue.”
It’s a shame, then, that so many organizations view pure threat feeds as their best opportunity to “get started” with threat intelligence. Of course, the reality is that if producing valuable, contextualized threat intelligence is your goal, there’s a need for massive quantities of incoming data from varied sources somewhere in the process.
But — and this is vital — there’s no need for human analysts to ever see it.
Rather than simply collating massive streams of threat data, a successful implementation of threat intelligence should provide analysts with only the intelligence they need to make proactive and reactive security decisions.
Key Questions
When defining a strategy to implement threat intelligence, it’s not ideal to start by investigating which technologies or vendors are available due to the massive amounts of threat data sources and providers available.
Instead, begin by considering three key questions:
Do you understand your greatest risk?
Which areas of your information security strategy have you already invested in and plan to invest in further?
How will your human resources impact your implementation strategy?
The answers to these questions will make it easier to define which operational areas threat intelligence will influence, and in turn, how your overall security profile can be enhanced. It’s also valuable to consider how your implementation of threat intelligence has the potential to result in greater efficiency, and more effective use of available resources.
The diagram below shows a suggested pathway for implementing threat intelligence, although naturally your own journey will be highly dependent on how you answered the questions above. The examples given here are by no means exhaustive, and there are a multitude of ways to make threat intelligence work in the context of your organization’s individual security strategy and architecture. With that said, the suggested applications for threat intelligence that follow should give you a strong indication of where you can reap benefits.
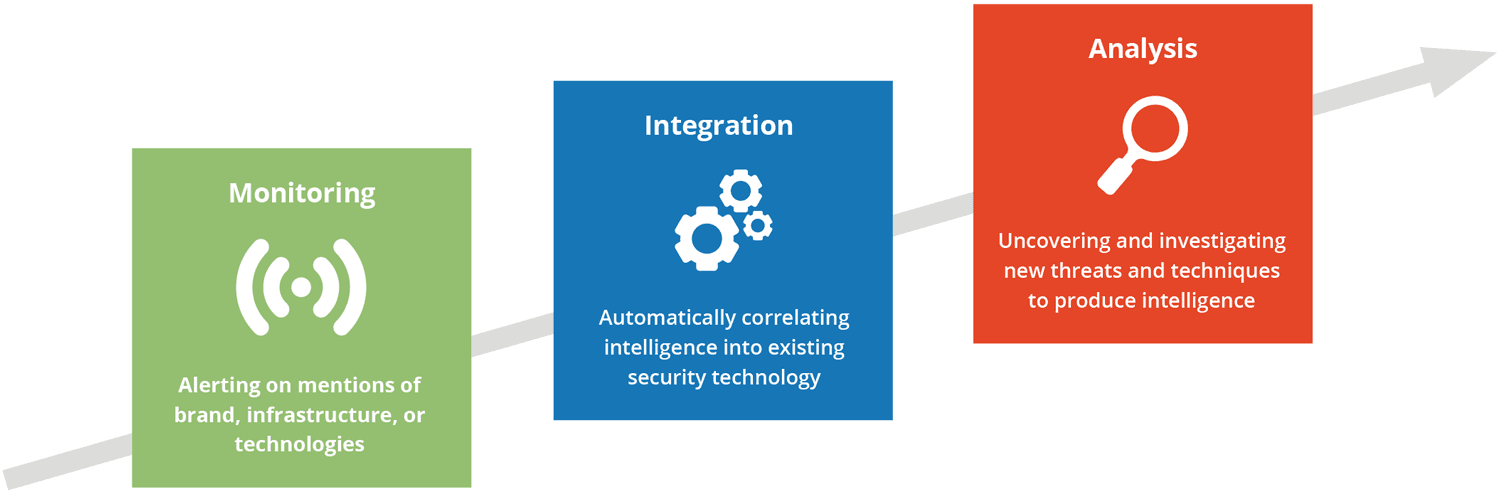
Monitoring
As you start to build your threat intelligence capability, it’s likely you won’t have the relevant expertise or time to support proactive analysis of threat intelligence. Nevertheless, you can still gain significant advantages and start to collect information from different sources by monitoring them for content that’s relevant to your business, and responding as part of your information security strategy. The types of intelligence you can uncover with this approach include:
- Leaked corporate credentials, data, and code.
- Visibility of new vulnerabilities.
- Threat trends that highlight potential new risks.
Integration
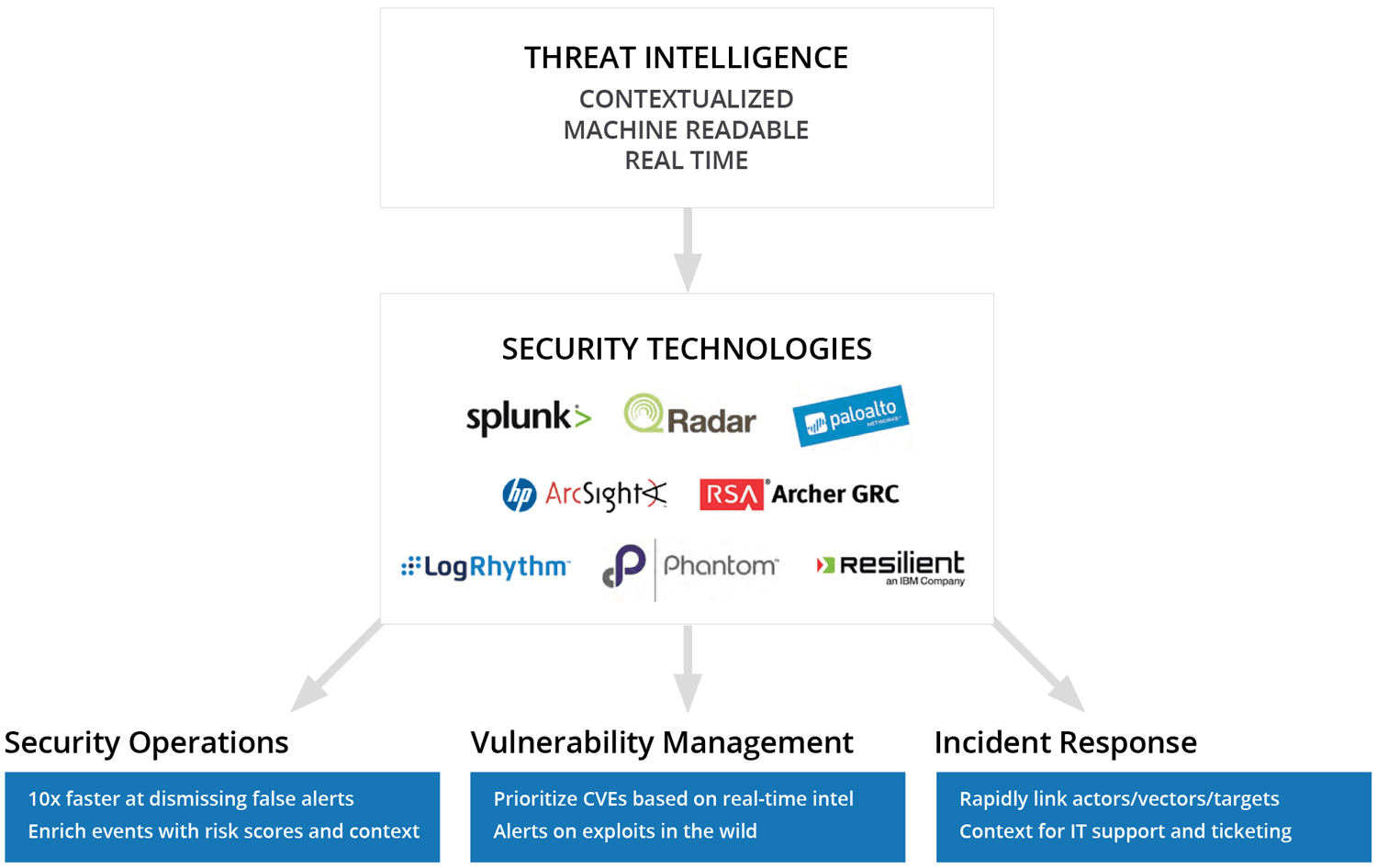
If you’ve invested significantly in security operations and supporting technologies, there are a number of ways you can utilize external threat intelligence to help combat “alert fatigue” within your organization. This intelligence can provide a great deal of context to the indicators you’re seeing from internal sources, which in turn can bring significant advantages including:
- Much faster identification of which alerts matter.
- Enriched intelligence on uncovered indicators.
- More context from more sources than technical threat feeds.
Analysis
As your threat intelligence function begins to mature, there’s no doubt you’ll seek ways to proactively identify emerging threats, and more closely examine the trends that pose risks to your industry, competitors, vendors, and supply chain. And with this level of threat intelligence capability, you’ll be gathering the kinds of insight that will not only uncover new threats and risks, but also show strategic value. For instance:
- Intelligence that informs your entire security strategy.
- Uncovering new threats, methods, and exploits.
- Analyzing threat trends related to your industry.
Throughout the development of your threat intelligence capability, this should be your aim. After all, while it’s incredibly valuable to identify malicious traffic (for example) and instantly respond, the true value of threat intelligence can only be realized if you take a more strategic view.
Do you need help getting started? Read our white paper to get best practices for applying threat intelligence.
Related