How Abbott Laboratories Supercharges SecOps With Security Intelligence
Key Takeaways
With security intelligence from Recorded Future, the SecOps team at St. Jude Medical (which has been acquired by Abbott Laboratories) dramatically accelerated investigation and response, resulting in:
- 63% reduction on exploit kit traffic delivered via malvertising into the network
- 28 times better detection of botnet traffic
- 50% savings in analyst time for malicious indicator of compromise (IOC) investigation
Due to the sensitive nature of its work, its large number of employees, the valuable IP it possesses, and their extensive ecosystem of third-party vendors, the organization relies on contextualized, real-time security intelligence from Recorded Future to enhance its overall security.
Before Abbott acquired St. Jude, Russ Staiger, the lead analyst with the Cyber Threat Action Center (CTAC) there co-presented a webinar on how his team uses Recorded Future in its security operations center as a way to detect, analyze, and prioritize emerging threats and IOCs. Security intelligence enables his team to make faster, more confident decisions based on external threat indicators automatically correlated with internal threat data — in real time and at scale across vast amounts of data, and without any manual research.
Previously, their firewall bot detections required an average of 168 unique sources per daily report. Recorded Future’s real-time intelligence integrated with their Splunk SIEM, enabling the organization to leverage only an average of six sources per day to accomplish a similar result. Armed with the context they need, the team can now quickly discount false positives, discover previously unidentified threats, accelerate triage efforts, and confidently take immediate action.
With Recorded Future, detections of exploit kit traffic dropped from an average of 27 per day to an average of less than 10 per day. Staiger says that his team now deals with fewer machine rebuilds, and analyst time is freed up to focus on bigger-picture threats and preventative measures. With the support of Recorded Future, the organization experienced:
- 63% reduction on exploit kit traffic delivered via malvertising into the network
- 28 times better detection of botnet traffic
- 50% savings in analyst time for malicious IOC investigation
Organizations seeking to further automate threat prevention can integrate Recorded Future Security Control Feeds with tools they already use — such as firewalls and email security and endpoint solutions — to automatically block high-risk indicators without additional enrichment.
To reduce their threat profile, Staiger urges other organizations to consider the ways attackers are operating and evolving their methods. Attacker networks are true business operations — they employ skilled people who have sophisticated processes and use technologies to achieve their objectives. As such, companies need to consider the who, what, and how, as well as the potential attack surfaces in intelligence gathering. Recorded Future provides this actionable, real-time context for his team, as well as automated solutions to combat automated attacks.
With Recorded Future, the SecOps team is able to:
- Investigate suspicious firewall traffic reports
- Determine the nature of undescribed or unknown traffic
- Ascertain greater effect of hosting policies for blocking
- Establish interlinked content delivery network exposures
Recorded Future’s dashboard, which Staiger considers his “landing page,” provides a quick temperature check to see what’s boiling to the surface of the cyber world. This includes pertinent information such as:
- Predominant types of exploits in the wild
- What other companies are experiencing
- Who has been targeted in recent attacks
When needed, the team can gain instant context around suspicious observables and indicators — with just one click into Recorded Future Intelligence Cards™. The team can rapidly prioritize threats or dismiss false-positives using Recorded Future’s dynamic risk scores. Staiger calls this functionality “powerful” as it “can give you a view of the risk of an IP address, URL, or CIDR block range.”
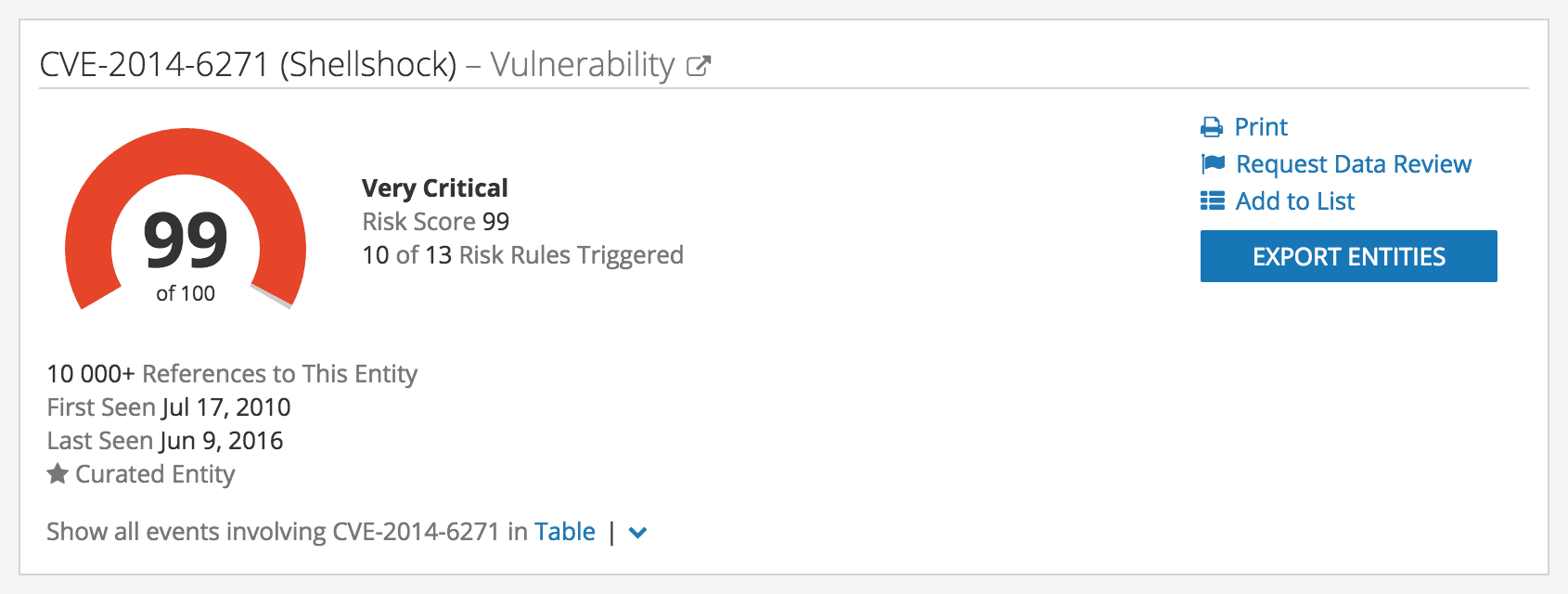
The top part of a Recorded Future Intelligence Card™.
Staiger presented use cases for Recorded Future, focusing on enrichment services for hashes, domains, and IP addresses and ranges. Since the Recorded Future Security Intelligence Platform “marries into Splunk’s enterprise security app,” his SecOps team gains valuable context. They can pivot through information, are able to quickly see correlations and references, and — perhaps most importantly — can align all of the external data with internal intelligence to form a complete picture of emerging threats and IOCs.
Recorded Future combines sophisticated machine and human analysis to fuse open source, dark web, and technical sources with original research. In describing this unique approach, Staiger says, “Recorded Future is an extremely well curated collection of some of the hardest to reach, as well as publicly available, sources all brought together to tell one story. It’s a magical moment in technology. They’re leaders in terms of having this much to draw from and having this much power.”
Learn more about Recorded Future for security operations and response, and view the on-demand webinar to hear how Abbott’s (Formerly St. Jude Medical’s) CTAC was able to improve its security intelligence program with Recorded Future.
Related
