Fuel Incident Response With Threat Intelligence to Lower Breach Impact

Ondrej Krehel, chief executive officer at LIFARS, and Scott Donnelly, senior analyst at Recorded Future, recently presented a webinar on how LIFARS, a digital forensics, incident response, and cyber security intelligence provider, relies on Recorded Future to provide context and technical details that help LIFARS better understand the intricacies of dealing with the aftermath of an incident and identify potential infections.
Cyber Crime in Numbers
A new cyber ecosystem has evolved. Every day security professionals are seeing various data breaches and hacking incidents play out in the media, as well as in our networks. The scope of the problem is staggering; the average cost of a breach is $3.79 million.
Companies are powerless to detect and defend against breaches (and are therefore prone to paying the high costs associated with cleanup) if they don’t have access to reliable and actionable threat intelligence. Krehel explained that his firm wanted to find threat intelligence that allowed them to be more proactive and speed up the incident response (IR) lifecycle. Making matters more complicated:
Incident response is a critical, time-consuming process.
Necessary information is often scattered across multiple sources.
Speed is important since a delay in detection or response means greater loss.
Threat intelligence can help, but only if it is structured in a way that allows the recipient to respond swiftly, accurately, and proportionally to the attack
Next-Generation Incident Response
In today’s world, it’s a sad fact that 68% of companies have experienced a security breach in the past 24 months, and 46% say another incident is imminent and could happen in the next six months. To improve the process, Krehel introduced “Next-Gen Incident Response,” which:
Makes use of next-generation automation tools to speed up the IR process.
Has specialized external teams to help reduce costs and increase response efficiency.
Takes down today’s advanced threats with military style “cyber snipers.”
Using Recorded Future as part of their comprehensive cyber security program, LIFARS now applies real-time threat intelligence from the entire web to inform and speed up the IR process.
Based on concerns and requirements from LIFARS, Recorded Future identified six indicators of compromise (IOCs). Recorded Future uploaded and searched these IOCs tied to a recent malware campaign and compared it against over 750,000 sources.
The information was compiled and centralized in a Recorded Future Intelligence Card™, which displays structured data and calls out non-obvious associations. In this case, Recorded Future found 86 total references in multiple media types, pulled from paste sites, social media, malware repositories, vendor blogs, and more.
For the purpose of this blog post, we’ll focus on the Vulnerability Intelligence Cards™.
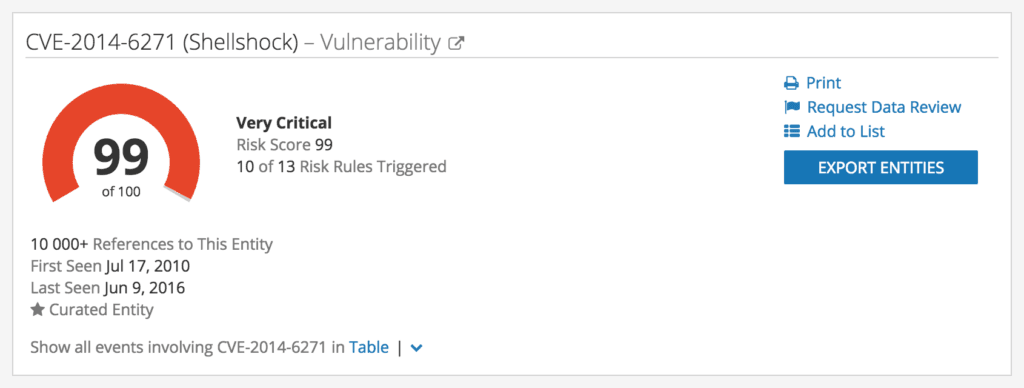
The top part of a Recorded Future Intelligence Card™.
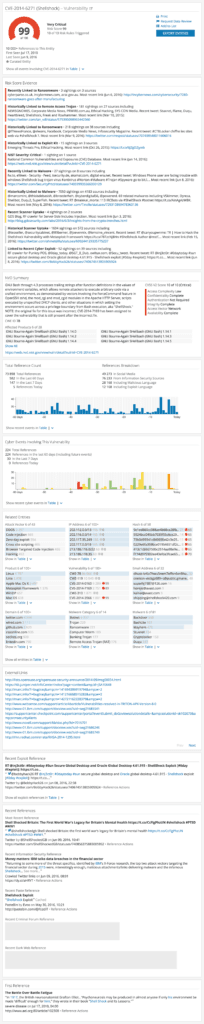
Donnelly illustrated how LIFARS could very quickly drill down into the information and find context around the malware’s authors, attack vectors, and even email addresses tied to the threat.
Doing so allows LIFARS to understand the scope and size of the threat which still exists, all in the proverbial “single pane of glass.”
Recorded Future even assigns a risk score, which offers additional context and transparency, and is useful when presenting information to executives, business partners, and customers during or after an incident.
With Recorded Future, LIFARS was able to see that what started as a simple malware problem had morphed into a bigger issue; they were able to track how the malware evolved, form a profile of the attacker, and draw conclusions that helped them complete their forensic analysis.
A Holistic Picture of the Threat Landscape
The big takeaway from the relationship is just how easy it is for LIFARS to see associations with malware, in this case, AlienSpy, and how easy Recorded Future makes it for LIFARS to pivot across information to understand what happened, how it happened, and how they can better prepare for the future.
To see many more details on AlienSpy and how Recorded Future was able to assist LIFARS, register to view the webinar replay. You’ll also learn how Recorded Future analyzes intelligence from across the open, deep, and dark web to provide more accuracy and create a holistic picture of the threat landscape.
Related