Proactive Threat Identification Neutralizes Remote Access Trojan Efficacy
Immediately Available: Download your free copy of this report now.
Intelligence is formulating an analysis based on the identification, collection, and enrichment of relevant information.
Continuously applying new and unique methodologies for identifying useful information sources is paramount to a successful threat intelligence practice, both for law enforcement and businesses. One example is proactively identifying remote access trojan (RAT) client (controller) locations before the RAT campaign begins spreading, and before the RAT executable is available for analysis.
RATs are simple to acquire, easy to operate, and often invisible to victims. Criminal forum posts and YouTube tutorials provide an “easy start” RAT guide for the uninitiated and the non-technical. New instances of RATs like Dark Comet and njRAT proliferate because the perceived risk of attribution is low. That mindset is a mistake.
Installing a RAT controller means that the threat actor’s computer is listening for incoming connections on a new port (often configured by the threat actor). Before a single RAT executable is submitted to an anti-virus aggregation service like Jotti, the threat actor is almost immediately vulnerable. Scanners like Nmap are used to identify specific ports and services on reachable hosts across the Internet, and common RAT families are simple to profile, making RAT client locations across the Internet easily identifiable.
The following graphic illustrates hundreds of RAT controller locations during the August 17-21, 2015 time frame as identified by Shodan. The family is denoted by color, the RAT controllers are clustered by autonomous system (AS), and the size of the node is dictated by the host’s listening port (between port 21 and port 12345) – the higher the port, the larger the node.
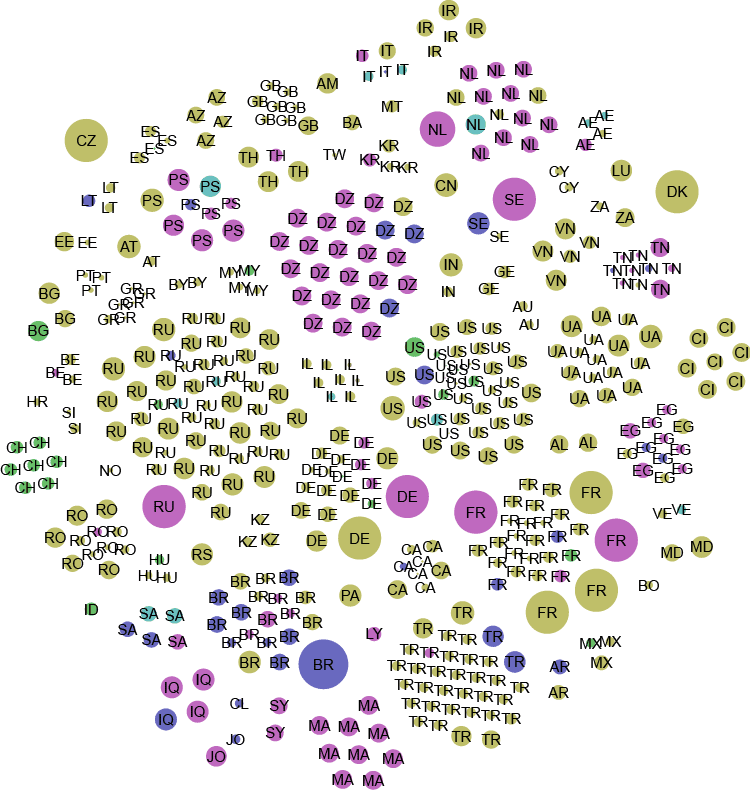
Legend: BlackShades, DarkComet, NetBus, Poison Ivy, XtremeRAT, njRAT
The applicability of this proactive methodology is apparent for law enforcement, but it’s also useful for the enterprise. Beyond operational indicators of compromise (IOC) correlation, iteratively profiling and identifying specific live RAT controller instances – regardless of the malware campaigns observed – used in commodity and targeted attacks is a strategically valuable exercise.
For additional information on this methodology and analysis results please download the report.
Related
