Third-Party Risk: Keeping Your Friends Close and Your Enemies Not as Close
Key Takeaways
- Businesses now operate in an increasingly interconnected world, sharing sensitive data and access with third parties. This makes many processes easier, but it also increases the levels of risk originating from third parties.
- A new report from ESG looks at some of the ways that organizations currently measure third-party risk, including the top mechanisms used to conduct audits and how effective those mechanisms are.
- The story is grim — third-party risk management today is inconsistent and usually represents a point-in-time snapshot of a third party’s security rather than providing up-to-date assessments.
Who’s got your data? Until recently, the answer to this question was usually pretty simple — “Just me.” Businesses and other organizations mostly kept their sensitive data in-house, supporting a “walled garden” security model where the most important factor was to restrict access points.
Even as the world has grown, it’s also gotten smaller. Now, the answer to the question of “who’s got your data?” might most succinctly be answered with the “person shrugging” emoji. Sensitive data, IT infrastructure, and more are all shared with partners and vendors or outsourced to other third parties. Everything’s always connected to the internet or living in the cloud. This certainly makes a lot of business processes easier, but what also follows is the fact that third-party risk is greater than it’s ever been, and managing it effectively will require a rethinking of the traditional security model.
That’s the verdict in a new report from Enterprise Strategy Group (ESG), titled “Third-Party Risk: Why Threat Intelligence Matters.” In this blog, we’ll explore some of ESG’s findings, including the ways most organizations are currently measuring third-party risk, what those mechanisms are good for, and where they fall short. We’ll also look at the solutions ESG presents in a follow-up to this blog.
But in short, ESG’s research, as they say themselves, “paints a rather bleak picture” of third-party risk management (TPRM). The report explains, “many organizations rely on sporadic TPRM audits by under-resourced cybersecurity and GRC teams, leading to an ongoing TPRM gap that can’t address business requirements sufficiently.”
The Third-Party Risk Management Gap
ESG looked at four aspects of how organizations currently evaluate risk, asking the following question: “Generally speaking, how would you characterize each of the following aspects of your organization’s third-party security audit processes?”
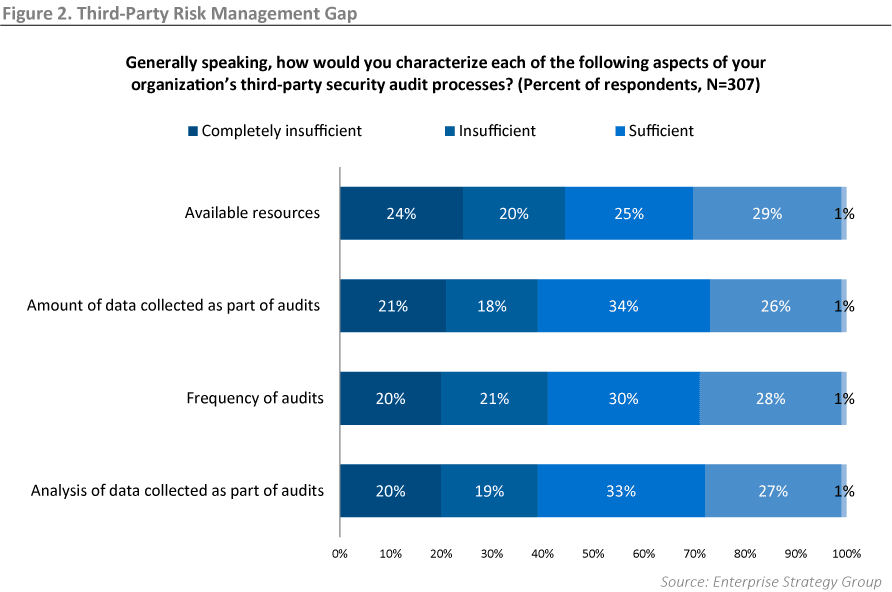
Notably, not more than about one-third of respondents said that their processes were “sufficient” in any of the four categories. In each category, between 39 and 44 percent of respondents replied that their processes were either “insufficient” or “completely insufficient.”
Top 5 Mechanisms Used to Conduct Third-Party Security Audits
ESG also looked at the question of what mechanisms organizations were currently relying on to conduct audits of the security of the third parties they worked with. In no case did even half of the respondents rely on any one technique, even among the five most popular.
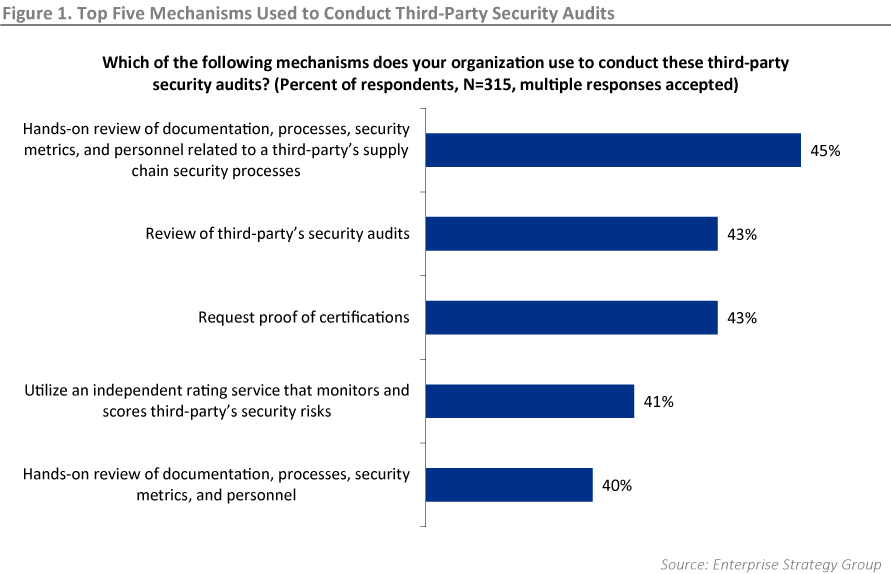
So what are these mechanisms good for, and how do they fall short? One quality shared across most of them is that they are snapshots in time — they may provide some idea of how well a third party is managing their security, but they may also quickly become outdated.
1. Hands-On Review of Documentation, Processes, Security Metrics, and Personnel Related to a Third Party’s Supply Chain Security Processes
As “hands-on” implies, this technique is the most comprehensive way of evaluating a third party’s supply chain. It’s also the most time-consuming. If it’s literally done manually, for example, by relying on in-house analysts to meet with and filter through the relevant contacts and data, respectively, this is not a process that will scale well or can be done frequently enough to keep risk assessments up to date.
2. Review of Third Party’s Security Audits
This is the next step down in terms of “hands-on” reviews — not doing it yourself, but reviewing what’s already been done. The problem, as before, is that these assessments can quickly become outdated.
3. Request Proof of Certifications
What security certifications an organization has can provide an important measure of their preparedness and whether they are following best security practices. The story these certifications tell is limited, however, and says nothing about the outside threats that the organization faces, such as whether it is actively being targeted by a threat actor.
4. Utilize an Independent Rating Service That Monitors and Scores Third Party’s Security Risks
Relying on independent rating services can help with the problem of scaling up. But many rating services will not monitor in real time, and they are not always transparent about the methodology behind their risk scoring, leaving you without valuable context.
5. Hands-On Review of Documentation, Processes, Security Metrics, and Personnel
This mechanism is very much the same as the first point, except it’s focused on the organization itself, not its supply chain.
Looking for Answers
Although many of these mechanisms described above are important ways of measuring and evaluating third-party risk, they fall short in providing up-to-date assessments. “Current TPRM audits can only be used to assess point-in-time security status,” the report states. “While this can serve as a useful guideline, business managers want to be aware of up-to-the-minute TPRM changes that may make their organizations vulnerable to devastating cyberattacks.”
The answer is to get data faster — “To mitigate these risks, CISOs and risk officers must bridge this gap by collecting, processing, and analyzing TPRM data in real time.”
We’ll explore what exactly the most effective solution — one that helps manage third-party risk by automating data collection — looks like in a follow-up to this blog. But if you can’t wait, download your complimentary copy of the report today and see for yourself.
Related