The Role of US Technology in China's Public Security System

Editor’s Note: This is an excerpt of a full report. To read the entire analysis with appendices and endnotes, click here to download the report as a PDF.
This report examines how public security entities in China acquire and use technology from companies based in the United States. The analysis draws heavily from Chinese government procurement records and industry exhibition documents, as well as other open-source materials. The report will be of most interest to researchers and activists who focus on human rights, policing, and technology, government agencies in the US and other countries that engage in export control or human rights work, and corporate personnel who carry out due diligence, corporate security, and compliance work. Information about the author, Zoe Haver, can be found at the end of this report.
Executive Summary
The public security system of the People’s Republic of China regularly acquires and uses technology from companies in the United States. This system comprises the PRC Ministry of Public Security (MPS), the MPS’ directly subordinate organizations, province-level public security departments, city-level public security bureaus, and the bulk of China’s civilian police forces, among others. These entities engage in extensive state violence, including mass surveillance, the persecution of political and religious dissidents, and the mass detention of ethnic minorities, as documented by journalists, human rights researchers, and the US government. Public security entities in China also have a counterintelligence mission and carry out intelligence-related activities at home and abroad that target political threats to the Chinese Communist Party (CCP). As such, transfers of technology from US companies to Chinese public security entities risk facilitating state violence, intelligence, and counterintelligence in China, regardless of companies’ intentions.
This report examines the role of US technology in China’s public security system, with a focus on technology acquired via lawful commercial activity. First, we discuss the organization of China’s public security system, review the state violence that it carries out, highlight its intelligence and counterintelligence activities, and examine US export control responses. Second, we analyze why Chinese public security entities value technology from US companies, highlighting unique capabilities and compatibility requirements as motivating factors. Third, we identify several key technology transfer pathways, namely industry exhibitions, third-party companies, local subsidiaries, acquisitions, and talent flows. Finally, we examine how public security entities use the US technology that they acquire, highlighting the Hainan Province Public Security Department's use of network and communications hardware from US companies and Xinjiang public security entities’ use of hard drive disks from US companies.
Key Judgments
- Chinese public security entities almost certainly acquire and use technology from US companies that specialize in surveillance, network infrastructure, DNA analysis, aviation, countersurveillance, digital forensics, thermal imaging, criminal forensics, data storage, communications, optics, laboratory equipment, cybersecurity, explosives and narcotics detection, automobiles, and other areas.
- In some cases, public security entities in China almost certainly seek technology from US companies because foreign products outperform domestic equivalents. In other cases, these entities likely seek US technology to ensure compatibility with Chinese partner organizations that are already using products from a particular US company.
- For decades, numerous US companies and their representatives have used industry exhibitions, such as the China International Exhibition of Police Equipment, to directly market goods and services to Chinese public security entities.
- Third-party agents and distributors, like US-based Ryan Technologies, specialize in facilitating technology transfer and frequently act as intermediaries between US companies and public security end users in China.
- US companies, like Thermo Fisher Scientific, have established local subsidiaries in China that directly provide goods and services to Chinese public security clients.
- Chinese companies’ acquisitions of US companies, such as Chongqing General Aviation Industry Group’s acquisition of Enstrom Helicopter Corporation, have aided the growth of China’s domestic industries and facilitated sales of US products to public security end users.
- Cross-border flows of talent likely function as a pathway for transfers of knowledge and technology to public security entities in China like the MPS Third Research Institute.
- The Hainan Province Public Security Department almost certainly uses network and communications hardware from IBM, H3C, Cisco, Comtech, and Motorola in numerous information systems, which may facilitate police intelligence, support the Golden Shield Project, carry out mass surveillance, and enable the command and control of public security forces, among other uses.
- Public security entities in the Xinjiang Uyghur Autonomous Region appear to have purchased at least 481 hard disk drives from Seagate and Western Digital in early-to-mid 2022, including surveillance-specialized drives and drives acquired alongside equipment from China’s leading surveillance providers. Other entities in Xinjiang, such as prisons belonging to the paramilitary Xinjiang Production and Construction Corps, have also recently carried out surveillance-oriented purchases of Seagate or Western Digital hard disk drives.
China’s Public Security System
This section surveys the organization of China's public security system, highlights the forms of state violence that Chinese public security entities carry out, examines the intelligence and counterintelligence activities of public security entities, and discusses how the US has pursued export control measures in response to the state violence carried out by Chinese public security entities.
Organization of the Public Security System
The MPS is a central ministry under China's State Council. It is responsible for leading and commanding public security work in China, which explicitly includes protecting the political security of the CCP. Public security work includes predicting, stopping, and investigating criminal activity, defending against and striking at terrorist activity, maintaining social law and order, managing hukou, resident identity card, citizenship, immigration and emigration, foreigner residency, and tourist affairs, and supervising security control work for public information networks. As part of this work, the MPS is also responsible for significant portions of China’s ever-expanding mass surveillance system. Though the PRC Ministry of State Security (MSS) has absorbed much of the MPS’ original foreign intelligence and counterintelligence responsibilities, the MPS still engages in some counterintelligence-oriented activities and continues to perform operations on foreign soil, such as clandestine operations targeting overseas dissidents, ethnic minority groups, religious organizations, and fugitives.

Figure 1: The MPS’ headquarters at No. 14 Chang’an Road in Beijing (Source: Baidu Maps)
The MPS oversees various bureaus, research institutes, universities, and other such organizations, covering a wide range of responsibilities. For a list of such bureau-level units directly subordinate to the MPS, see Appendix A. Under the MPS, provincial and autonomous region governments have public security departments (公安厅), city and country governments have public security bureaus (公安局), and lower levels of administration have institutions like public security sub-bureaus (安分局) and police stations (公安派出所). Local public security entities are relatively autonomous but still answer to the MPS. The MPS and local public security entities are responsible for China’s detention center (看守所) system, which is distinct from the Ministry of Justice’s (MOJ) prison (监狱) system.
The MPS is responsible for the bulk of the People's Police (人民警察), China's civilian police force. The People’s Police absorbed the former Public Security Border Defense Force (公安边防部队) and Public Security Guards Force (公安边警卫部队) in the late 2010s. The MPS previously had partial authority over the People's Armed Police (人民警察); as part of the aforementioned set of reforms, the PAP was reorganized and placed under the sole authority of the Central Military Commission. Likewise, the former Public Security Firefighting Force (公安消防部队) was transferred to the Ministry of Emergency Management. Other components of the People’s Police fall under the MSS, MOJ, Supreme People’s Court, and Supreme People’s Procuratorate. The public security components of the People’s Police swear loyalty to the CCP.
Chinese Public Security Entities and State Violence
Public security entities in China have a well-documented track record of engaging in state violence. Researchers define state violence as “the use of legitimate governmental authority to cause unnecessary harm and suffering to groups, individuals, and states” with the goal of reaching “the organizational goals of a state or government agency”. Examples of state violence include “human rights violations, crimes against humanity, war crimes, genocide, torture, prisoner abuse, and the oppression of racial, ethnic, gender, religious, or political minorities”. Several specific forms of state violence, as defined by various academic sources, that public security entities in China carry out are discussed in greater detail below.
China’s public security system is associated with a wide range of human rights violations and repressive activities. The 2021 annual report of the US Congressional-Executive Commission on China (CECC) alleges that public security entities in China detained computer coders for sharing the personal information of CCP General Secretary Xi Jinping's relatives, detained critics of the CCP, denied activists access to lawyers, threatened the families of lawyers, extrajudicially detained activists, raided the homes of Christians, detained environmental advocates, and detained ethnic and religious minorities. Likewise, the CECC’s 2020 annual report alleges that public security entities in China surveilled human rights lawyers, detained individuals who were working to archive investigative reporting that was critical of the Chinese government’s response to COVID-19, punished medical personnel for sharing information about the December 2019 outbreak of COVID-19, surveilled religious leaders, and detained artists critical of the Chinese government’s policies toward ethnic minorities. The CECC also notes that, until December 2019, “public security officials were authorized to detain sex workers and their clients for six months to two years without judicial oversight” via the “custody and education” (收容教育) form of administrative detention, which “primarily targeted women” and was “prone to abuse”. Transgender sex workers in China face particularly high levels of negligence, harrassment, discrimination, and violence from the police.
Public security entities are also deeply involved in the implementation of mass surveillance across China, such as through the Golden Shield Project (金盾工程). The first phase of this project, which the MPS launched in the late 1990s or early 2000s, aimed to promote the “informatization” (信息化) of China’s public security system and included numerous components. For example, it involved the creation of shared national public security information network infrastructure for use at each level of China’s public security system. This phase also established 8 major national databases, such as the National Population Basic Information Resource Database (全国人口基本信息资源库), which, combined with the project’s population information management system (人口信息管理系统), now allows public security personnel to quickly search and analyze the personally identifiable information of China’s entire population. Another component of the first phase was setting up public security identity authentication and access control management systems (公安身份认证和访问控制管理系统), which official sources describe as public key infrastructure/privilege management infrastructure platforms (PKI/PMI平台) designed to promote system security and standardization. The second phase of the Golden Shield Project emphasized goals like promoting “big intelligence” (大情报), improving applicability, and promoting information sharing. Its components included the construction of intelligence information comprehensive application platforms (情报信息综合应用平台) for use at each level of China’s public security system, as well as the construction of a national police geographic information system basic platform (全国警用地理信息基础平台; PGIS平台). Other more recent programs that facilitate mass surveillance and that involve public security entities include the Skynet Project (天网工程), Sharp Eyes Project (雪亮工程), and the push to build smart cities (智慧城市).
Moreover, public security entities have been at the forefront of the mass detention and surveillance of the Uyghurs and other minority groups in China’s Xinjiang Uyghur Autonomous Region (XUAR). As part of this campaign, local public security bureaus have been building a predictive policing capability called the Integrated Joint Operations Platform (IJOP; 一体化联合作战平台). According to a 2019 Human Rights Watch (HRW) investigation into IJOP, the authorities in Xinjiang “are collecting massive amounts of personal information — from the color of a person’s car to their height down to the precise centimeter — and feeding it into the IJOP central system, linking that data to the person’s national identification card number”. After aggregating this data, the platform flags allegedly suspicious activity for the authorities, which includes benign behaviors such as “not socializing with neighbors”, having foreign ties, using WhatsApp, and “preaching the Quran without authorization”. HRW further notes that “some of those targeted [by IJOP] are detained and sent to political education camps and other facilities”, which have reportedly held around 1 million people. Recorded Future’s search of Xinjiang government procurement records uncovered documents mentioning IJOP as recently as December 2021, which suggests that the Xinjiang authorities are very much still using the platform.
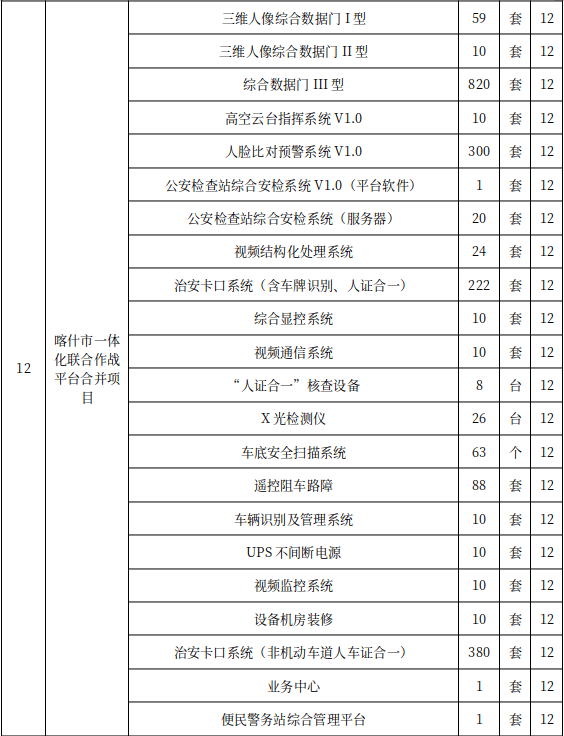
Figure 2: Description of IJOP components, such as a “facial comparison early warning system”, that was included in bidding documents for a Kashgar City Public Security Bureau (喀什市公安局) informatization maintenance and service project in late 2021 (Source: Kashgar City Public Security Bureau)
Intelligence and Counterintelligence Activities
Public security entities in China have a mandate to suppress perceived political enemies of the CCP and Chinese government, both at home and abroad. At the forefront of this effort are the secret police forces under the MPS Political Security Protection Bureau (公安部政治安全保卫局), known until recently as the MPS Domestic Security Protection Bureau (公安部国内安全保卫局), which collects intelligence on and targets dissidents, religious groups, ethnic minorities, and fugitives within China’s borders and in other countries. For instance, a local CCP committee website describes a city’s domestic (political) security protection dadui (大队) as having a range of intelligence responsibilities related to social stability, political stability, and state security. These include intelligence activities targeting “reactionary secret societies”, “illegal organizations”, “international terrorist groups”, “overseas hostile forces”, “criminal organizations masquerading as religious groups”, and “ethnic separatists”. Notably, the website also explicitly states that the dadui is “responsible for overseas investigation and research work, [and] carrying out secret forces construction and various kinds of concealed professionalization and socialization construction”. Research has confirmed that political security protection forces under the MPS operate abroad, such as entering Myanmar to capture and repatriate fugitives. Recorded Future also observed the Guangxi Zhuang Autonomous Region Public Security Department seeking to re-lease servers in both Hong Kong and the US as part of a “domestic [political] security protection information system operational maintenance” contract in 2018, which provides further evidence of China’s political security protection forces operating abroad.
China’s public security system very likely continues to engage in certain counterintelligence-oriented activities despite the fact that the MSS has absorbed much of the MPS’ original counterintelligence responsibilities. For instance, public security entities register and thereby track all foreigners traveling in China. Under the Exit and Entry Administration Law of the PRC, “Where foreigners stay in hotels in China, the hotels shall register their accommodation in accordance with the regulations on the public security administration of the hotel industry, and submit foreigners’ accommodation registration information to the public security organs in the places where the hotels are located”. Additionally, it states that “for foreigners who reside or stay in domiciles other than hotels, they or the persons who accommodate them shall, within 24 hours after the foreigners’ arrival, go through the registration formalities with the public security organs in the places of residence”. Likewise, in November 2021 journalists reported that the Henan Public Security Department had hired Neusoft Corporation (东软集团) to build a province-wide surveillance system to track foreign journalists, foreign students, and other “suspicious people” with the aim of protecting “national sovereignty, security, and interests”.
US Export Control Responses
In response to the state violence that Chinese public security entities carry out, particularly in Xinjiang, the US government has taken some steps in recent years to restrict the transfer of US technology to such entities. However, experts have questioned the efficacy of current US export control measures that target Chinese public security entities and the Chinese companies that support them. The Export Control Reform Act of 2018, which appears to have been in part motivated by concerns about China, defined dual-use items as including items with law enforcement-related applications and explicitly stated that US export control policy should serve to protect human rights. Moreover, during 2019 and 2020, the US Department of Commerce Bureau of Industry and Security (BIS) placed 21 Chinese public security entities (in addition to various Chinese companies) on the Entity List, which imposes export licensing restrictions on specific entities. These entities were placed on the Entity List due to their role in “human rights violations and abuses in the implementation of China's campaign of repression, mass arbitrary detention, and high-technology surveillance against [Uyghurs], Kazakhs, and other members of Muslim minority groups in the XUAR”. A full list of these 21 entities can be found in Appendix B. The Trump administration also signed the PROTECT Hong Kong Act in November 2019, prohibiting “the issuance of licenses to export covered munition items such as tear gas, rubber bullets, water cannons and other items” to the Hong Kong Police Force (HKPF). The HKPF falls under the Hong Kong Security Bureau rather than mainland China’s public security system. The exact extent of cooperation between the HKPF and Chinese public security entities is unclear, though both the MPS and MSS appear to have a relationship with the HKPF.
Moreover, many of the technologies described in this report very likely may not come within the ambit of existing US export controls. As such, Recorded Future assesses that a large volume of technology transfers detailed in this report very likely are not subject to extensive export controls and may be freely sold without much oversight from the US government. However, technology transfers that are legal can still facilitate state violence, intelligence work, or counterintelligence activities, as certain subsequent sections of this report will demonstrate. Such transfers are currently receiving greater public and government scrutiny.
The Value of US Technology
China’s party-state has long promoted technology transfer to make up for domestic shortcomings and stimulate innovation. The industries that serve China’s public security system have also participated in its drive to acquire, apply, learn from, and improve foreign technology. China’s surveillance industry, for example, appears to rely on foreign hardware because “this is where Chinese companies still largely cannot provide their own substitutes and are thus heavily reliant in the West”. Chinese surveillance companies rely on hard disk drives (HDDs) from US-based companies like Western Digital and Seagate, the latter of which has reportedly worked with Hangzhou Hikvision Digital Technology Co., Ltd. (杭州海康威视数字技术股份有限公司) to develop the world’s first surveillance hard drive, dispatched dedicated engineering teams to China to develop surveillance-oriented drives, and worked with Chinese surveillance companies as a strategic partner. Hikvision, which has been targeted by US export control measures, has been extensively involved in the mass surveillance and detention of the Uyghurs and other minority groups in Xinjiang, and reporting shows the Xinjiang authorities use drives from both Western Digital and Seagate for surveillance. Chinese surveillance companies also rely on graphics processing units (GPUs) from US-based companies like Intel and NVIDIA, with various US companies, including Intel, reportedly partnering with these Chinese surveillance companies to develop new surveillance capabilities.
As part of the procurement process, Chinese party-state entities sometimes provide expert assessments and other similar explanations to justify the purchase of specific foreign products, which collectively offer direct insight into why entities value US technology. In some cases, these internally oriented assessments clearly indicate that US products outperform equivalents from Chinese companies or otherwise offer unique capabilities. In other cases, these assessments reveal that Chinese public security entities likely seek out US products to ensure compatibility with partner organizations that are already using technology from a particular US company.
Outperforming Domestic Equivalents
Recorded Future observed numerous instances of Chinese public security entities describing US technologies as superior to their Chinese equivalents. For example, procurement records indicate that numerous Chinese public security entities have acquired and continue to use products from US-based video analysis provider Cognitech, Inc., with references appearing as early as February 2010 and as recently as November 2021. A product brochure from a Chinese police and military equipment sales company claims that more than 80 public security entities in China use Cognitech, Inc.’s video “fuzzy image analysis processing system”, which appears to be the Chinese name for the company’s “Video Investigator” tool. These entities include municipal public security bureaus, provincial public security departments and entities subordinate to these departments, academic institutions, and entities under the MPS. We also observed evidence of third-party Chinese companies that claim to represent Cognitech, Inc. participating in Chinese policing industry exhibitions (see Appendix D).
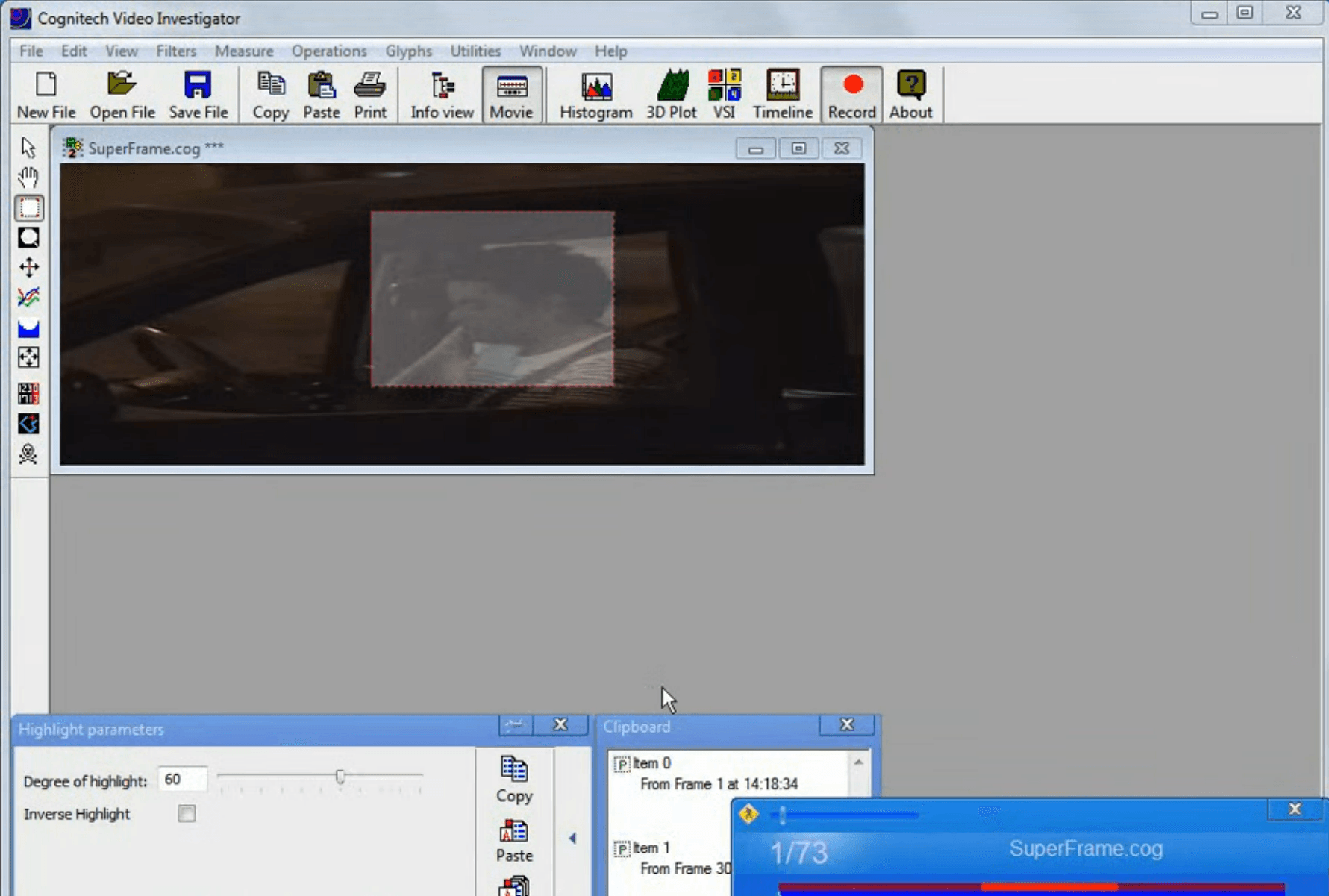
Figure 3: The user interface of Cognitech, Inc.’s Video Investigator tool (Source: Cognitech)
Cognitech, Inc. is headquartered in California, US. According to its website, the company “is a foremost developer of real-time image and video forensics processing and analysis software tools, 3D video photogrammetry software, lossless video acquisition cards, and integrated workstation systems for professional use by thousands of professional users in forensics, law enforcement, bio-identification, vehicle identification, intelligent CCTV systems … geo-intelligence (GEOINTEL) and in surveillance fields”. Cognitec, Inc. states that its government agency customers include “Provincial Forensic Labs & Police Departments” in China as well as the Executive Office for United States Attorneys, the US Department Of Justice, US Department of Defense, US Department of Homeland Security, US Federal Bureau of Investigation, Japanese National Police Agency, and German Air Force.
A 2017 single source procurement document from the Tianjin City People’s Procuratorate (天津市人民检察院) offers a detailed explanation of why law enforcement organizations in China value Cognitech, Inc.’s “video fuzzy image analysis processing system”. The document states that, thanks to the progress of “public security informatization construction”, the quantity and quality of video surveillance cameras in China have significantly increased. It further explains that the expansion of video surveillance across China has driven a corresponding surge in demand for video image processing capabilities. To meet this demand, the Tianjin City People’s Procuratorate was seeking to use a system from Cognitech, Inc. The 2017 document makes 3 main arguments to justify the acquisition of a Cognitech, Inc. system via single source procurement:
- The Cognitech, Inc. system has an original vector algorithm for complex moving images, 3-dimensional automatic measurement, and other capabilities that make it a true professional video fuzzy image analysis processing system.
- The Cognitech, Inc. system has unique, world-leading patented technologies, and multiple countries have approved the system for practical and scientific use.
- The Cognitech, Inc. system’s “overall functions and quality cannot be replaced by other brands” and its “use effectiveness is obviously superior to other similar products”. As such, the system is widely used by public security entities across China, including the MPS Material Evidence Evaluation Center (公安部物证鉴定中心), Criminal Investigation Police University of China (中国刑事警察学院), Beijing City Public Security Bureau Criminal Police Zongdui (北京市公安局刑警总队), and Guizhou Province Material Evidence Evaluation Center (贵州省物证鉴定中心). In practice, the system has played an important role in the responses to major incidents such as the July 2009 protests and subsequent riots in Urumqi, Xinjiang.
To support the aforementioned arguments, the Tianjin City People’s Procuratorate solicited expert opinions from senior engineers employed at the Criminal Investigation Police University of China, Shenzhen City Public Security Bureau Criminal Police Zhidui (深圳市公安局刑事警察支队), Guangdong Province Public Security Department Criminal Investigation Bureau Criminal Investigation Technology Management Center (广东省公安厅刑事侦查局刑事技术管理中心), and Jiangsu Yangzhou City Public Security Bureau Criminal Police Zhidui (江苏扬州市公安局刑警支队). Each expert affirmed that Cognitech, Inc.’s system uses unique, world-leading patented technology and that the system is clearly superior to other similar products. Recorded Future also observed the Changyi City Public Security Bureau (昌邑市公安局) in Shandong Province offering similar justifications for the purchase of the same Cognitech, Inc. system in 2016.
Beyond the case of Cognitech, Inc., Recorded Future identified other instances of Chinese public security entities providing detailed justifications for the purchase of foreign products that outperform domestic equivalents. Several examples include:
Countersurveillance devices. According to August 2021 procurement documents, the Nanning City Public Security Bureau SWAT Zhidui (南宁市公安局特警支队) in the Guangxi Zhuang Autonomous Region sought to obtain 2 nonlinear junction detectors from Research Electronics International, which is based in the US. According to Research Electronics International, its nonlinear junction detectors are “made to detect and locate hidden cameras, microphones, and other electronic devices” and have applications in technical surveillance countermeasures, countersurveillance, intelligence protection, and other similar areas. The documents from the Nanning City Public Security Bureau SWAT Zhidui highlight the application areas of searching for explosive devices, protecting state secrets, and detecting illicit devices in detention centers. The documents describe the underperformance of domestic products and provide an expert assessment to justify importing the Research Electronics International devices. Beyond Nanning City, we observed evidence of various city public security bureaus, provincial public security departments, and organizations directly subordinate to the MPS purchasing (or seeking purchase) Research Electronics International nonlinear junction detectors as well as other countersurveillance devices from the company, such as video pole cameras and telephone and line analyzers.
Tactical equipment. According to a July 2021 tender, the Jinhua City Public Security Bureau (金华市公安局) in Zhejiang Province was seeking to purchase an imported sniper rifle night vision device from L3Harris Technologies. The document specifies that domestic night vision devices have been tested against foreign products and have consistently underperformed for a variety of reasons. Likewise, according to a September 2020 tender, the Jinhua City Public Security Bureau was seeking to purchase nighttime combat devices from L3Harris Technologies, Steiner, 3M’s PELTOR brand, and Vortex Optics. Like the July 2021 tender, the September 2020 tender sought to justify buying imported equipment on the basis of China’s domestic equipment being inferior. L3Harris Technologies, 3M, and Vortex Optics are all US companies. Steiner is headquartered in Germany, but the tender document describes Steiner as a US company, which suggests that the bureau was likely seeking equipment from a US entity of Steiner.
Data center hardware. According to a December 2016 procurement document, the Qinghai Province Public Security Department (青海省公安厅) aimed to purchase an unspecified imported “data center computer room specialized chilled water unit and UPS [uninterruptible power supply] host” as part of a network security data center computer room infrastructure project. The document further specifies that the chilled water unit must comply with strict European Union or US certifications. The document claims that China currently lacks design and manufacturing standards or an industrial production licensing management system for such chilled water units, and that imported products outperform domestic equivalents. Likewise, the document argues that domestic UPS servers are inferior to imported equivalents. As such, the Qinghai Province Public Security department sought to import hardware. The document also includes an assessment from 6 experts, who agreed that domestic products cannot meet the requirements of the network security data center computer room infrastructure project.
Forensics devices. According to a single source procurement announcement, the Xianju County Public Security Bureau (仙居县公安局) in Zhejiang Province was trying to acquire a “US Elephant Company ultraviolet observation camera system” in October 2015. According to the bureau, European and US ultraviolet observation systems use a safe wattage while domestic equivalents use an unsafe wattage that can cause harm to users. As such, the bureau hoped to import a US product. The aforementioned US Elephant Company is very likely Elephant Engineering, which was a division of US-based Syntronics, LLC. US-based General Atomics acquired Syntronics, LLC in 2017.
Compatibility Requirements
Recorded Future also found that some Chinese public security entities likely seek US products for compatibility reasons. For example, procurement documents from late 2017 and early 2018 indicate that the Guangdong Province Public Security Department (广东省公安厅) purchased a US laboratory device so that its data would be compatible with national and local public security entities that use the same equipment. In a single source procurement announcement, the department states that the MPS Material Evidence Evaluation Center and some cities in Guangdong Province use the “Nuance EX” multispectral material evidence analysis system imported from the US, and that the MPS Material Evidence Evaluation Center had announced a project aimed at optimizing the system’s software and database. As such, the Guangdong Province Public Security Department appears to have worked through the supplier NBL Imaging System Ltd. (广州星博科仪有限公司; Guangzhou Xingbo Scientific Instruments Co., Ltd.) to acquire an imported “[Nuance] EX450-950” multispectral material evidence analysis system, which was almost certainly from US-based PerkinElmer, so that its data would be compatible with the MPS and local cities.
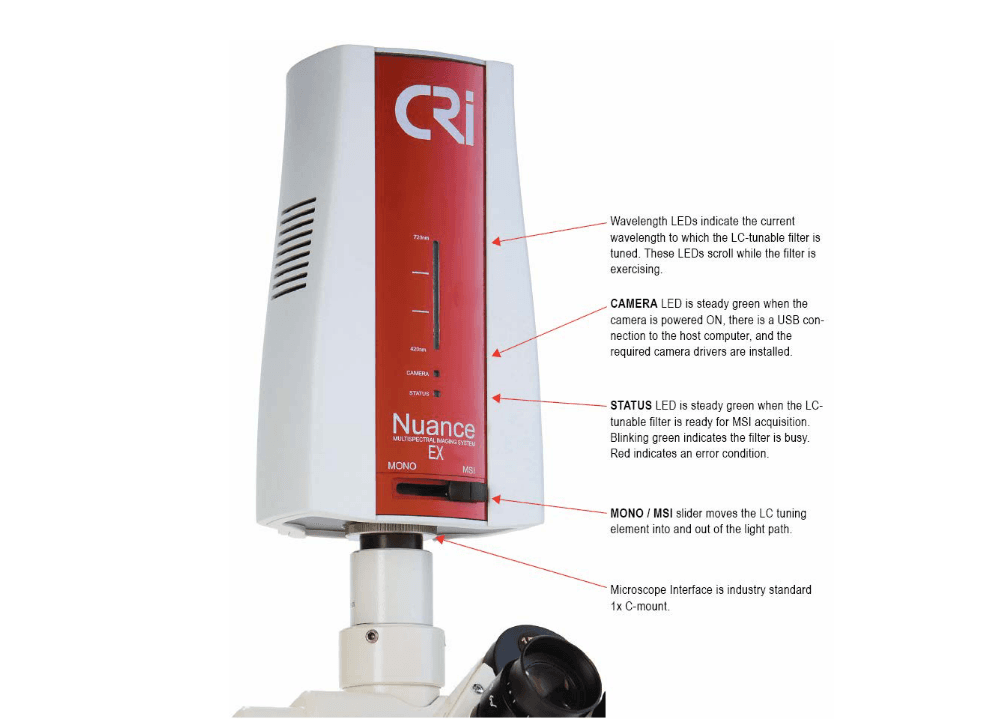
Figure 4: Nuance EX multispectral imaging system from PerkinElmer (Source: PerkinElmer)
Technology Transfer Pathways
This section analyzes several of the pathways through which China's public security system acquires or could acquire technology from US companies, namely industry exhibitions, third-party companies, local subsidiaries, acquisitions, and talent flows. These technology transfer pathways are open to both technologies that can facilitate state violence (such as video surveillance products) and technologies that have more benign applications (such as breath alcohol analysis products). Some of the technologies that move through these pathways can support both unremarkable police activity and more questionable endeavors, such as DNA analysis devices and other laboratory equipment that can help solve crimes but also can help build population DNA databases. As such, a given transfer or transfer pathway cannot be judged to be benign or harmful without end-use context.
Industry Exhibitions
US companies have almost certainly marketed their products to Chinese public security entities at industry exhibitions since at least the early 2000s, including numerous US military and law enforcement contractors. We focused our analysis on the biennial China International Exhibition of Police Equipment (CIEPE; 中国国际警用装备博览会), which has been running for roughly 20 years and is hosted by the MPS. Some state media reporting has described CIEPE as the only police equipment exhibition that the MPS hosts. Chinese state media has also described CIEPE as “an important platform for promoting international policing exchanges and cooperation” and touted the participation of companies from the US. According to a US exhibitor, “CIEPE serves the growing market for public security equipment in China” and “many of the 20 thousand in attendance are decision makers” who are “looking for equipment and technology for their departments to order and purchase”. Numerous companies from countries such as the United Kingdom (UK), Germany, France, Israel, Japan, and Italy have also participated in CIEPE over the years, though the activities of these companies are beyond the scope of this report.

Figure 5: Criminal investigation technology area at the 10th CIEPE in 2020 (Source: Xinhua)
Based on a review of publicly available exhibitor lists, we identified at least 52 likely instances of US-linked companies participating in CIEPE between the 2nd CIEPE in 2002 and the 10th CIEPE in 2020. A list of US-linked exhibitors at CIEPIE that we identified is included in Appendix C. In some cases, the US-linked companies appear to have directly participated in the exhibition. In others, US-linked companies were identified as participants but were actually represented by third-party agents. The companies that we observed include US-based companies, subsidiaries and joint ventures that US companies have established in China, and US companies that Chinese companies have acquired. A number of these companies have participated in multiple CIEPE events over the years. The companies specialize in areas such as video surveillance, thermal imaging, optics, aviation, biotechnology, explosives and narcotics detection, digital forensics, laboratory equipment, communications, edged weapons, cameras, lighting, automobiles, protective cases, and breath alcohol analysis. We also found US exhibitors that specialize in exporting technology to China from companies in the US and other foreign countries.
In addition to US companies selling their wares, we also observed third-party companies from China and Hong Kong marketing US policing technology at CIEPE as commercial agents. Appendix D includes 20 examples of self-described agent companies from the 5th CIEPE in 2010. At the 5th CIEPE, these 20 companies claimed to sell products from numerous US companies that specialize in areas like video surveillance, aviation, security inspection, counterterrorism, forensics, laboratory equipment, network infrastructure, optics, explosive ordnance disposal, tactical apparel and other gear, lighting, and cameras. Many of these agents’ websites still list products from US and other foreign companies, indicating these activities continue as of mid-2022.
Third-Party Companies
US companies that develop policing technologies often do not bid directly on Chinese government contracts. Rather, third-party companies based in China, as well as some from Hong Kong and the US, play a significant intermediary role in funneling technology from US companies to public security end users in China. To illustrate the role of such distributors and agents, below we analyze the corporate network and activities of US-based Ryan Technologies. This network distributes technologies oriented toward digital forensics, DNA analysis, security inspections, countersurveillance, and other activities.
Ryan Technologies, also known as Ryan Security and Ryan Security Technology, describes itself as “the global leader in forensic, security, and law enforcement product distribution in China”. According to its website, Ryan Technologies was “founded in 1992” and is “operated out of Santa Barbara California”. The company has “tightly coupled itself with foreign based rep offices headquarted [sic] in Beijing and has consistently expanded its coverage opening 5 other offices in key cities including Shanghai, Guangzhou, Chengdu, Wuhan and Shenyang”, with additional maintenance stations “in over 30 other locations throughout China”. Ryan Technologies has “sold and managed several technology transfer projects to China handling all training, sales, installations, after sales support and more”. The company further claims that “the high level of communication between our Mandarin fluent US office and highly motivated Chinese staff gives our clients an unparalleled and transparent view into the market”. The company’s “full fledged R&D team is capable of integrating products, developing add-on’s/accessories [sic], and creating systems out of products to solve the problems our customers face”. Ryan Technologies states that “we also service most the [sic] products we sell regularly which allows us to monitor the use of the product long after the sale”. According to its website, Ryan Technologies uses the phone number “805-962-3080” and the company is located at an address in Santa Barbara. The company’s addresses in China (as listed on its website) are provided in Appendix E. Ryan Technologies’ website identifies numerous partner companies from the US and other countries and claims that the company has received a number of export recognitions, including 1 from the US Commercial Service of the US Department of Commerce. The company has repeatedly participated in CIEPE (see Appendix C).

Figure 6: Partner information on Ryan Technologies’ website (Source: Ryan Technologies)
The corporate network of Ryan Technologies includes a number of companies, with each claiming to participate in the transfer of US technology to public security entities in China. Companies in this network include:
E.C. Ryan International. Ryan Technologies is almost certainly legally registered in the US as E.C. Ryan International, Inc.
Resonant. At some point in the past several years, Ryan Technologies almost certainly rebranded as Resonant Ltd. (香港美耐特有限公司; Hong Kong Mei Nai Te Co., Ltd.).
Beijing Ryan Wende Science and Technology. Ryan Technologies’ Chinese headquarters is almost certainly Beijing Ryan [Ruiyuan] Wende Science and Technology Co., Ltd. (北京瑞源文德科技有限公司).
Beijing Ryan Huade Science and Technology. Ryan Technologies’ network in China almost certainly includes Beijing Ryan [Ruiyuan] Huade Science and Technology Co., Ltd. (北京瑞源华德科技有限公司).
Of the companies in Ryan Technologies’ network, Beijing Ryan Wende Science and Technology Co., Ltd. is particularly notable. At the 5th CIEPE in 2010, Beijing Ryan Wende Science and Technology Co., Ltd. described itself as “Ryan Technologies (China), Ltd.”; claimed to be “well known for being one of the most experienced service providers in the industry, and for offering integrated solutions for China’s public security”; and claimed to specialize in “promoting and introducing western advanced IEDD/EOD [Improvised Explosive Device Disposal/Explosive Ordnance Disposal], anti-terrorism, public safety and forensic products to China”. The company claims to have over 40 products that have passed through MPS testing and certification. On its website, the company states that it sells and services technology from companies in the US, Canada, the UK, Italy, Israel, and other foreign countries and lists foreign partners such as “MICROGEM PLC”; “Oxygen Forensic”; “Attestor Forensics GmbH”; “BlackBag Technologies, Inc”; “Elcomsoft”; “Logicube”; “Rapiscan Systems”; “Vidisco”; “FOCLAR”, “Access Data”; “Med-Eng”; “DeltaPix”; “Foster + Freeman”; “L3 Technologies”; “REI” [Research Electronics International]; and “West Technology Systems Limited”. Some of these companies, but not all of them, offer digital forensics products, which could be used to forcibly access the phones of protestors, activists, and other perceived enemies of the Chinese party-state.
Procurement records suggest that Beijing Ryan Wende Science and Technology Co., Ltd. has widely bid on Chinese public security contracts. We observed at least 144 Chinese government procurement records dated between August 2008 and March 2022 that reference Beijing Ryan Wende Science and Technology Co., Ltd., including 103 instances in which the company is identified as a successful bidder. In most instances, the company’s clients are public security entities, though it has also won contracts from entities such as procuratorates, courts, and airports. These procurement records show that the company serves clients across China at all levels of the public security system, including municipal public security bureaus, provincial public security departments, and organizations directly under the MPS. Given that the Ryan Technologies network specializes in selling foreign technology in the Chinese market, the majority of Beijing Ryan Wende Science and Technology Co., Ltd.’s public security contracts very likely involve the sale of technology from foreign companies. In certain instances, the documents that we reviewed explicitly name imported products, including products from US companies. For instance, the Tianjin City Public Security Criminal Investigation Bureau (天津市公安刑事侦查局) selected Beijing Ryan Wende Science and Technology Co., Ltd. to provide an IntegenX-brand RapidHIT DNA analysis instrument from US-based Thermo Fisher Scientific in April 2015.
Local Subsidiaries
Some US companies have local subsidiaries in China that work directly with public security clients. A notable example of this is Invitrogen (Shanghai) Trading Co., Ltd. (英潍捷基(上海)贸易有限公司), a wholly-owned subsidiary of US-based Thermo Fisher Scientific. Invitrogen (Shanghai) Trading Co., Ltd. appears to offer ongoing genetic analysis equipment maintenance services to Chinese public security entities.

Figure 7: The copy of Invitrogen (Shanghai) Trading Co., Ltd.’s Chinese business license available on Thermo Fisher Scientific’s website (Source: Thermo Fisher Scientific)
As “the world leader in serving science”, Thermo Fisher Scientific claims that it “delivers an unrivaled combination of innovative technologies, purchasing convenience and pharmaceutical services through our industry-leading brands, including Thermo Scientific, Applied Biosystems, Invitrogen, Fisher Scientific, Unity Lab Services, Patheon and PPD”. In early 2019, journalists found that the Chinese authorities were using DNA equipment from Thermo Fisher Scientific as part of their mass surveillance campaign in Xinjiang. Though Thermo Fisher Scientific “said it would no longer sell its equipment in Xinjiang” in February 2019, reporting in mid-2021 revealed that “police in the Chinese region of Xinjiang are still buying hundreds of thousands of dollars’ worth of American DNA equipment despite warnings from the U.S. government that the sale of such technologies could be used to enable human rights abuses in the region”, including equipment from Thermo Fisher Scientific. Thermo Fisher Scientific has also repeatedly participated in CIEPE (see Appendix C).
Recorded Future observed at least 60 Chinese public security procurement documents dated between August 2013 and December 2021 that reference Invitrogen (Shanghai) Trading Co., Ltd., including 38 instances in which the company is identified as a successful bidder. Many of these contracts are for maintenance services of Thermo Fisher Scientific equipment. For example, the Fujian Province Public Security Department Criminal Investigation Technology Zongdui DNA Laboratory (福建省公安厅刑事技术总队DNA实验室) published a single-source tender announcement for a DNA information system maintenance project in September 2019. This project included a sub-contract for “DNA Laboratory ABI [Applied Biosystems, Inc.] Equipment Maintenance Services”. The document states that Applied Biosystems engineers provide DNA forensic equipment maintenance for the company’s products, and that no other organization has been entrusted to maintain these products. As such, the sole company granted maintenance authority is Invitrogen (Shanghai) Trading Co., Ltd. The document also mentions that the zongdui had purchased maintenance services for its “3130XL fluorescent sequencing instrument” from Invitrogen (Shanghai) Trading Co., Ltd. in 2015, very likely referring to Thermo Fisher Scientific’s 3130 Genetic Analyzer.
In other instances, Recorded Future observed Chinese public security entities acquiring Thermo Fisher Scientific products from Invitrogen (Shanghai) Trading Co., Ltd. via third-party companies, including in Xinjiang. For example, a pair of winning bid announcements from September 2020 show that the Urumqi City Public Security Bureau Criminal Investigation Zhidui (乌鲁木齐市公安局刑事侦查支队) had selected Xinjiang Kehua Hechang Biological Science and Technology Co., Ltd. (新疆科华和昶生物科技有限公司) to provide 2,732,480 RMB ($420,000) worth of Thermo Fisher Scientific reagent kits and other consumable materials from Invitrogen (Shanghai) Trading Co., Ltd.
Acquisitions
The acquisition of US companies by Chinese firms can help facilitate the transfer of US technology to public security Chinese entities. A clear example of this process can be observed in state-owned Chongqing General Aviation Industry Group Co., Ltd.’s (重庆通用航空产业集团有限公司; 重庆通航集团; CGAG) acquisition of US-based Enstrom Helicopter Corporation, which state media described in 2013 as the first time that a Chinese aviation enterprise had successfully purchased a well-known helicopter manufacturer from the US or Europe. These helicopters are used in China for counterterrorism, riot control, reconnaissance, and other missions.
According to its website, Enstrom Helicopter Corporation “designs and manufactures light, single-engine piston and turbine helicopters for commercial, government, and personal use”. It is headquartered in Michigan, US. Enstrom was reportedly one of the first Western helicopter brands to enter the Chinese market in the 1990s. CGAG, previously known as Chongqing Helicopter Industry Investment Co., Ltd. (重庆直升机产业投资有限公司), acquired Enstrom Helicopter Corporation in 2012 and is an authorized dealer for Enstrom Helicopter Corporation in China. Corporate records show that CGAG has multiple shareholders and that state-owned enterprises are its largest shareholders. Documents from the 10th CIEPE also indicate that CGAG is state-owned, and Chinese state media has described it as a state-owned enterprise.
After CGAG acquired Enstrom Helicopter Corporation, industry media reported that “Enstrom is positioning itself for global expansion into emerging markets — with a bull’s eye squarely centered on China”. The reporting stated that “CGAG is currently pursuing a production certificate from the Civil Aviation Administration of China (CAAC) to build Enstrom variants in country” and “while the certification process runs its course, Enstrom is shipping kits from Menominee [Enstrom’s US headquarters] to CGAG in China”. Enstrom’s then-CEO asserted that CGAG “was tasked with finding a general aviation company ripe for purchase” and was “looking anywhere and everywhere to purchase a company, but of course, there were very few on the market then outside Enstrom”. According to the reporting, “CGAG’s goal when they purchased Enstrom in 2012 was to increase production to 50 helicopters in Menominee with another 50 assemblies sent to China”. A document from the Chongqing City Development and Reform Commission (重庆市发展和改革委员会) shows that CGAG likely had the capacity to produce at least 30 Enstrom helicopters a year in Chongqing by the end of 2014.
Chinese state media touted CGAG’s participation in the 10th CIEPE in 2020. The coverage notes that CGAG demonstrated the capabilities of the police-model Enstrom 380B helicopter and other police equipment in areas like counterterrorism, anti-crime, emergency rescue, and guarding security. It further claims that CGAG equipment supports the actual combat needs of public security forces, and that police aviation customers have unanimously recognized the company. According to materials from the 10th CIEPE, CGAG is an “important platform” of the State Air Traffic Control Commission, National Development and Reform Commission, and CAAC for the development of general aviation. The CIEPE materials claim that CGAG received a helicopter production license from CAAC, established the Chongqing Enstrom General Aviation Technology Research Institute (重庆恩斯特龙通用航空技术研究院), and established the Enstrom Helicopter Domestic Maintenance Center (恩斯特龙直升机国内维修中心). Moreover, the materials say that the company sells products like the Enstrom 480B and 280FX, and is developing products like the Enstrom TH180. The materials further state that the police-model Enstrom 480B helicopter is widely used in patrol, emergency rescue, counterterrorism, anti-drug, anti-smuggling, air command, and other police missions (very likely in China). CGAG displayed the police-model Enstrom 480B helicopter at the 10th CIEPE. Enstrom Helicopter Corporation or CGAG also participated in the 9th CIEPE in 2018 (see Appendix C).

Figure 8: CGAG booth at the 10th CIEPE in 2020 (Source: Xinhua)
Recorded Future did not observe any tenders from public security entities for the purchase of Enstrom helicopters from CGAG, though we did uncover a number of maintenance contracts that provide evidence of CGAG and its subsidiaries providing Enstrom helicopters to Chinese public security entities. These documents are dated between October 2015 and April 2022, were issued by entities like the Guizhou Province Public Security Department (贵州省公安厅), Lanzhou City Public Security Bureau (兰州市公安局), and Chongqing City Public Security Bureau (重庆市公安局), and largely consist of single-source procurement announcements. For instance, according to a March 2022 document from the Chongqing Public Security Bureau, the bureau purchased Enstrom 480B helicopters from CGAG in 2013 and in 2016. The document further states that, due to the professional and technical requirements of helicopter maintenance, no company in China other than CGAG subsidiary Chongqing General Aviation Co., Ltd. (重庆通用航空有限公司) is qualified to provide maintenance services for the Enstrom helicopters, used for missions like counterterrorism, riot control, and reconnaissance. Likewise, a November 2018 document from the Guizhou Province Public Security Department indicates that the MPS donated Enstrom 480B helicopters to the department, that the MPS has a police aviation construction and development cooperation agreement with CGAG, that the MPS Police Aviation Management Office (公安部警用航空管理办公室) has a strategic cooperation framework agreement with CGAG, and that CGAG is uniquely qualified to provide long-term maintenance services from Enstrom 480B helicopters. State media reporting shows that CGAG and the MPS Police Aviation Management Office signed their strategic cooperation agreement at a helicopter exhibition in September 2017. As part of this agreement, CGAG reportedly agreed to provide 10 Enstrom 480B helicopters at a discounted price to support the development of China’s police aviation industry and offer services in areas like personnel training and airport construction.
Talent Flows
Cross-border talent flows are a pathway for knowledge and technology transfers from the US to China. Though such transfers can help facilitate state violence in China, Recorded Future emphasizes that Chinese nationals living, studying, and working abroad should not be assumed to be engaged in activities for the purpose of supporting state violence, espionage, or illegal activities, and deserve to live without the threats of xenophobia, ethnic profiling, and violence. We also note that foreign academics and universities are known to facilitate transfers of technology to China’s public security system. In this section, we examine the career trajectories of several individuals who received educations from US universities or gained professional experience from US companies and then went to work for the MPS Third Research Institute (公安部第三研究所), a major research organization within China’s public security system. To protect the privacy and safety of these individuals, we anonymize their personal identifiable information, their US alma maters, and their former US employers.
The Third Research Institute carries out scientific research and technical support activities related to smart policing and network security. It is based in Shanghai. The institute was founded in 1978 as the "Shanghai Public Security Science Research Institute" (上海公安科学研究所), was renamed to "MPS Public Security 876 Research Institute" (公安部上海八七六研究所) in 1979, and was then renamed once again to "MPS Third Research Institute" in 1984. The Third Research Institute claims to have made significant advances in the fields of “police information intelligent perception”, “police data security sharing”, and “illegal crime monitoring [and] early warning”. It provides “core key technology support and systems solutions” in areas like “network offense and defense, network reconnaissance, technical reconnaissance, domestic encryption, electronic evidence collection, classified protection, big data analysis, intelligent security, and drug testing”. It owns at least 6 companies, including Beijing Run Technologies Co., Ltd. (北京锐安科技有限公司), and oversees numerous departments, centers, and research laboratories. Procurement records from early 2022 reveal that Beijing Run Technologies Co., Ltd. sells open-source intelligence (OSINT) software that facilitates the collection and analysis of data from foreign sources across the clear web, deep web, and dark web, including Instagram, Facebook, LinkedIn, and other major social media platforms.

Figure 9: The MPS Third Research Institute's headquarters at No. 76 Yueyang Road in Shanghai (Source: Baidu Maps)
Recorded Future observed a number of instances of self-described current or former Third Research Institute employees claiming to have previously worked for foreign companies or claiming to have received degrees from foreign universities, including US companies and universities. We highlight several examples below of such individuals who appear to have supported the Third Research Institute’s work on cybersecurity and mass surveillance. In each of these cases, the individuals almost certainly leveraged their US educations or work experiences when employed at the Third Research Institute.
Individual 1. Individual 1 works on cybersecurity at the Third Research Institute, received a PhD from a US university, and has published numerous technical papers on cybersecurity and other topics. Individual 1 was employed as an associate research fellow at the Third Research Institute since September 2018. Previously, Individual 1 had been a postdoctoral researcher at the institute from May 2015 to September 2018. At the institute, Individual 1 reportedly works on “connected vehicle information security and privacy”, and they previously worked on “privacy and network security”. Before joining the institute, Individual 1 was a research assistant at a US university from September 2011 to February 2015. The individual received a PhD in electrical, electronics, and communications engineering from the same US university in 2015. Individual 1 has published nearly 30 conference papers, technical standards, and other publications related to subjects like network security, neural networks, unmanned aerial vehicles, and cyber threat intelligence.
Individual 2. Individual 2 was employed at the Third Research Institute to work on subjects like computer vision and machine learning, has researched the use of neural networks in mass surveillance, and joined the Third Research Institute after receiving a master’s degree from a US university. Individual 2 was employed as a deep learning researcher at the Third Research Institute from August 2013 to November 2015. At the institute, their responsibilities reportedly included working on precise image retrieval based on deep learning. Individual 2 received a master's degree in signal and image processing from a US university at an unspecified date. At this university, Individual 2 studied subjects such as digital image processing, digital video processing, pattern recognition, affine transformation, image segmentation, motion estimation, face recognition, and optical character recognition. Between September 2010 and June 2013, the individual worked for a laboratory that is very likely part of the aforementioned US university. At the US laboratory, this individual’s responsibilities reportedly included working on facial recognition and researching context-based color image retrieval, among others.
Individual 3. Individual 3 has been employed as a project manager at the Third Research Institute since September 2018. At the institute, the individual’s responsibilities reportedly include designing and managing roadmaps based on trends in the cybersecurity industry, designing overall solutions for the cybersecurity of public security sensor networks, leading a cross-functional team to accomplish public security standard specifications, participating in national and ministerial cybersecurity research projects, managing product documents and answering bids, and providing regular trainings to customers and users on product portfolios and solutions. Before joining the institute, Individual 3 worked in the Shanghai offices of a US telecommunications company and a French-US telecommunications company.
Applications of US Technology
The technologies that public security entities in China acquire from US companies have a large number of possible applications. Previous sections of this report have already provided some details regarding how public security entities leverage products from US companies to facilitate activities such as surveillance video analysis, forensic analysis, police aviation, DNA analysis, countersurveillance, and SWAT operations. Our data on CIEPE participants (see Appendix C and Appendix D) further highlights potential applications of US technology in China’s public security system, including thermal imaging, network infrastructure, digital forensics, communications, and many others. Moreover, numerous other studies and reports have detailed the support that foreign companies provide to China’s public security system in the area of mass surveillance, where companies from the US and other countries have for decades aided the Chinese authorities’ efforts to build a highly advanced surveillance state.
Over the course of our research, Recorded Future observed countless references to products from US companies in Chinese public security procurement documents. This technology is being used at every level of China’s public security system across the country, including in particularly heavily surveilled jurisdictions like Xinjiang and Tibet. This report would be hundreds of pages long if we named every US company, product, and Chinese public security end user that we identified via publicly accessible procurement documents. As such, we provide 2 case studies below that highlight several particularly notable application areas and end users. The first focuses on the Hainan Province Public Security Department’s (海南省公安厅) use of network and communications hardware from US companies in its information systems, including in information systems that support mass surveillance and police intelligence. The second examines Xinjiang public security entities’ continuing use of HDDs from US companies, including drives used for surveillance.
Case Study: Network and Communications Hardware in Hainan Province
The Hainan Province Public Security Department almost certainly uses a variety of products from US companies in its information systems. We observed evidence of this in bidding documents attached to annual information system maintenance tenders that the department published in late 2019, late 2020, and late 2021. These documents provide detailed descriptions of numerous information systems and lists of the hardware and software that the information systems currently use. The documents show that multiple information systems use hardware and software from a variety of US companies. In this report, we limited our review to network and communications hardware. According to the documents, public security entities in Hainan are using hardware from these companies to facilitate their mission, including carrying out police intelligence, supporting the Golden Shield Project, carrying out mass surveillance, and enabling the command and control of public security forces. The documents also reveal other, more benign applications of this technology, such as the use of this hardware in the department’s local area network (LAN) infrastructure. This case study therefore demonstrates how Chinese public security entities can leverage a given technology in multiple different ways.

Figure 10: The Hainan Province Public Security Department’s headquarters at No. 9 Binya Road in Haikou (Source: Baidu Maps)
The 2019, 2020, and 2021 documents from the Hainan Province Public Security Department identify network and communications hardware from various US-based or US-invested companies, including IBM, H3C, Cisco, Comtech, and Motorola.
IBM. IBM is headquartered in New York, US, and provides products and solutions in areas like artificial intelligence, blockchain, business operations, cloud computing, data and analytics, hybrid cloud, information technology infrastructure, security, and supply chain. Previous research has found that China’s public security system uses IBM products in various contexts, including mass surveillance.
H3C. H3C, also known as New H3C, is a joint venture between US-based Hewlett-Packard Enterprise (HPE) and China-based Unisplendour Corporation, with HPE holding a 49 percent stake and Unisplendor holding a 51 percent stake. Unisplendor is a subsidiary of Tsinghua Holdings, a state-owned enterprise. When Hewlett-Packard (HP), HPE’s predecessor, established H3C in 2015, it claimed that H3C would include “HP’s China-based server, storage and technology services businesses” and that H3C would be “HP’s exclusive provider of servers, storage and networking, as well as hardware support services in China”. According to HPE, “this structure enables HPE to participate in the fastest-growing IT market in the world, through HPE’s sale of products to New H3C for resale in the China market”. Previous reporting has found that Chinese law enforcement forces use H3C products, including in Xinjiang.
Cisco. Cisco is headquartered in California, US, and offers solutions in areas such as analytics and automation, artificial intelligence, cloud, collaboration, critical network infrastructure, intent-based networking, internet of things, networking, security, software, software-defined networking, smart buildings, and wireless mobility. Previous research and reporting has found that Chinese public security entities have long used Cisco products, including for mass surveillance.
Comtech. Comtech Telecommunications Corp. is based in New York, US, and offers products and solutions in areas like public safety and security as well as satellite and space communications. The Comtech products described in this section very likely come from a Comtech subsidiary, Comtech EF Data, which provides “high-performance satellite communications ground equipment” and is based in Arizona, US. Previous reporting has found that China’s maritime militia forces in the South China Sea are very likely using technology from Comtech EF Data.
Motorola. Motorola, Inc. split into Motorola Mobility and Motorola Solutions in 2011. Motorola Solutions is headquartered in Illinois, US, and is “a global leader in public safety and enterprise security” and offers solutions in “and mobile radio communications, video security & access control and command center software”. Reporting has shown that Motorola has long supplied equipment to police in mainland China and Hong Kong, and Recorded Future found that a Chinese subsidiary of Motorola has repeatedly participated in CIEPE (see Appendix C).
Alongside network and communications hardware from these companies, 1 of the projects discussed below also uses vehicles from Ford and Mercedes-Benz. Ford is a US company, and Mercedes-Benz is a German company. A joint venture that Ford established in China has reportedly participated in CIEPE (see Appendix C).
Intelligence Comprehensive Application Platform
According to the 2019 bidding documents, the Hainan Province Public Security Department QB Platform Optimization and Improvement Project (海南省公安厅 QB 平台优化完善项目), also known as the Intelligence Comprehensive Application Platform (情报综合应用平台), uses an unspecified server from IBM. Both the 2020 and the 2021 bidding documents reference the Intelligence Comprehensive Application Platform, but neither discusses any specific hardware. We assess that the IBM server is likely still in use.
According to the 2019 documents, the Hainan Province Public Security Department initiated the Intelligence Comprehensive Application Platform project in 2013. The project was likely implemented as part of the second phase of the Golden Shield Project. The platform’s capabilities include police intelligence dynamic monitoring and analysis, abnormal behavior monitoring, intelligent statistical analysis, key persons comparison early warning, key persons accumulated early warning, and data resources monitoring and management, among others. The platform has been fully applied in every city and county bureau across the province, serving as the basic system and work carrier for intelligence at the grassroots level. The 2020 bidding documents further specify that this platform was built in line with MPS big intelligence platform requirements, describing a ministry-province-city big intelligence work system that facilitates vertical and horizontal information sharing. This system was almost certainly developed as part of the Chinese authorities’ longstanding efforts to reform and improve intelligence work in policing.

Figure 11: Description of the Intelligence Comprehensive Application Platform from 2020 that highlights the platforms “key persons dynamic control” and “major incidents early warning and prevention” capabilities (Source: Hainan Province Public Security Department)
Public Security PKI/PMI Platform
According to the 2019 bidding documents, the Hainan Province Public Security Identify Authentication and Access Control Management System (海南省公安身份认证与访问控制管理系统), also known as the Hainan Province Public Security PKI/PMI Platform (海南省公安厅 PKI/PMI 平台), is a certificate authority (CA) authentication center that was built using public key cryptography. The 2019 platform software and hardware product maintenance list identifies servers and network security switches from IBM, Cisco, and H3C. 2020 and 2021 bidding documents reference PKI/PMI the PKI/PMI platform specifically, but we assess that the system is likely still in use. The IBM, Cisco, and H3C components are listed in Appendix F.
According to the 2019 documents, this platform unifies the identity expression methods of public security information network users, authentication methods, and the authorization management modes, which promotes cross-department and cross-region secure information sharing. The construction of this local second-level PKI/PMI platform was completed during the first and second phases of the Golden Shield Project and the platform’s PKI/PMI software, directory service software, application middleware, and certificate comprehensive suit query subsystem have been progressively upgraded. Hainan public security organs have issued over 20,000 digital certificates, which are connected to every major application area. The platform completes the basic security transformation of multiple application systems such as the police comprehensive [system], population information query system, and big intelligence system, which allows for basic authorized access control based on digital certificates via connection to the public security PKI/PMI system. As such, the PKI/PMI system platform constitutes the basic system and work carrier of grassroots civilian police informatized applications. The MPS has long identified such PKI/PMI platforms as an essential component of the Golden Shield Project.
Public Security Video Monitoring and Checkpoint System
According to the 2019 and 2020 bidding documents, the Hainan Province Public Security Video Monitoring and Checkpoint System Project (Checkpoint Phase 1) (海南省公安视频监控和卡口系统项目(卡口一期)) uses several H3C S1224 switches and came into use in 2014. The 2021 documents do not reference the system, but we judge that it is likely still in use. The system integrates numerous facial recognition and thermal imaging cameras, as well as human face analysis software, from Hikvision, thereby enabling port and train station surveillance.
Public Security “Communications on the Move” Satellite Communications System
According to the 2019 bidding documents, the Hainan Province Public Security “Communications on the Move” (COTM) Satellite Communications System (海南省公安“动中通”卫星通信系统) includes components from Comtech, Motorola, Cisco, and H3C. The 2020 documents do not reference the COTM system. The 2021 bidding documents reference the same components. The components from Comtech, Motorola, Cisco, and H3C are listed in Appendix F. According to the 2019 documents, the system was built in 2009 and 2014. The system has 1 Ford COTM satellite vehicle and 1 Ford image acquisition vehicle with an accompanying satellite ground station. The system also has 1 Mercedes-Benz COTM satellite vehicle with 5 accompanying satellite ground stations. The Hainan Province Public Security “COTM” Satellite Communications system was built in accordance with MPS requirements, helps respond to emergency situations, and facilitates mobile command via real-time video and audio communications.
Public Security Information Network Border Security Access Platform
According to the 2019 bidding documents, the Public Security Information Network Border Security Access Platform (公安信息网边界安全接入平台) uses servers, switches, and routers from H3C and IBM. The 2020 and 2021 documents include an identical list of components. The H3C components are listed in Appendix F. According to the 2019 documents, the platform was put into use in December 2010 and provides a secure channel for data exchanges, both within network and externally, and provides secure data support for all kinds of professional police work. It has over 30 access services and has access links including a party-government-military link, an externally deployed public security link, and a social enterprise and institution link.
Public Security Department Organs LAN H3C Network Equipment
According to the 2019 bidding documents, the LAN of the Hainan Province Public Security Department main office building comprises network equipment purchased from H3C in 2011. This equipment carries the internet of the department’s internal organizations and serves as a public security information backbone network. The 2019 maintenance service list associated with the Public Security Department Organs LAN H3C Network Equipment breaks the computer network systems into an “internet” section and a “public security network” section. The internet section comprises a pair of H3C S10500 switches and various other accompanying components. The public security network section identifies an identical pair of switches and accompanying components. The 2020 bidding documents identify the same equipment. The 2021 bidding documents do not mention these components, but we assess that they are likely still in use. The H3C components are listed in Appendix F.
Public Security Network Upgrade and Transformation (Video Transmission) Project
According to the 2019 bidding documents, the Public Security Network Upgrade and Transformation (Video Transmission) Project (公安网升级改造(视频传输)项目) uses switches, servers, routers, and other equipment from H3C. The 2019 hardware maintenance list confirms that the project uses a wide range of H3C components. Most of the same components are also identified in the 2020 and 2021 bidding documents. The H3C components are listed in Appendix F. According to the 2019 documents, the project entered into use in July 2015. It involved procuring provincial public security department core switches, city and county convergence switches, provincial department LAN convergence switches, provincial department LAN access switches, network management platforms, routers, and servers. The new equipment is used to carry key services and effectively guarantees the reliable operation of video private network equipment.
Case Study: Hard Disk Drives in the Xinjiang Uyghur Autonomous Region
HDDs from Seagate and Western Digital are almost certainly being used by public security entities in Xinjiang, where the authorities have been carrying out a campaign of mass surveillance, mass detention, forced labor, forced sterilization, and other human rights violations targeting the Uyghur muslims and other minority groups. Both companies are industry leaders in data storage and are based in California, US. In November 2019, journalists reported that Seagate and Western Digital sell drives to Chinese surveillance companies like Hikvision; that Seagate had long partnered with Chinese surveillance companies to develop new capabilities; that surveillance providers appear to rely on Seagate and Western Digital drives; that surveillance customers sometimes specifically request products from Seagate and Western Digital; and that these companies’ drives are used in Xinjiang for surveillance. At the time, Seagate and Western Digital “said they comply with all laws and are closely watching Xinjiang”, with Western Digital claiming that “we recognize the gravity of the allegations related to surveillance in the Xinjiang Province”. Based on a review of recent XUAR government procurement records, Recorded Future judges that public security entities in Xinjiang are still widely using HDDs from Seagate and Western Digital as of mid-2022, including some for what appears to be surveillance activities. We also observed evidence of the paramilitary Xinjiang Production and Construction Corps (新疆生产建设兵团; XPCC) recently procuring Seagate and Western Digital drives for use in at least 2 of its prisons, both of which reportedly have held individuals detained as part of the mass detention campaign in Xinjiang.
Between January 1 and May 12, 2022, we observed at least 60 unique contract or winning bidding announcements from Xinjiang public security entities that reference Seagate drives. The documents were issued by 37 different public security entities, including city public security bureaus, city district sub-bureaus, county public security bureaus, and entities subordinate to the XUAR Public Security Department (新疆维吾尔自治区公安厅), among others. According to the documents, these entities purchased at least 248 Seagate drives, including surveillance, network-attached storage (NAS), enterprise, computer, and portable drives. Of the 32 surveillance drives that were purchased, 28 are from Seagate’s SkyHawk series of surveillance-specialized storage HDDs. The SkyHawk series of products “leverages Seagate's extensive experience in designing drives purpose-built for surveillance applications” and their best fit applications include network video recorders (NVRs), embedded surveillance digital video recorders (DVRs), hybrid surveillance DVRs, and surveillance DVRs. These HDDs include “ImagePerfect firmware”, which is “designed to ensure seamless video footage capture in 24×7 surveillance workloads that record video from 64 HD cameras”. They also have “SkyHawk Health Management”, which “actively helps protect your surveillance storage by focusing on prevention, intervention and recovery options”. In several instances, XUAR public security entities, including entities that BIS has placed on the Entity List (see Appendix B), procured surveillance drives and other HDDs alongside surveillance equipment from leading Chinese surveillance providers like Hikvision, Zhejiang Dahua Technology Co., Ltd. (浙江大华技术股份有限公司), and Zhejiang Uniview Technologies Co., Ltd. (浙江宇视科技有限公司). See Appendix G for more details regarding these surveillance-related purchases of Seagate drives.
Between January 1 and May 12, 2022, we observed at least 16 unique contract or winning bid announcements from Xinjiang public security entities that reference Western Digital drives. The documents were issued by 12 different public security entities, largely comprising city, county, and city district public security bureaus and sub-bureaus, with other end users being the Xinjiang Police College (新疆警察学院) and the public security bureau of an XPCC division. According to the documents, these entities purchased at least 233 Western Digital HDDs and solid state drives, including data center, enterprise, computer, and portable drives. In 2 instances, XUAR public security entities procured Western Digital HDDs alongside surveillance equipment from Hikvision. See Appendix G for more details regarding these surveillance and intelligence-related purchases of Western Digital Drives.
In addition to public security entities’ procurement of Seagate and Western Digital products, we also observed XPCC prisons acquiring drives from these companies for use in surveillance. The XPCC was created in the 1950s using demobilized PLA units and placed under the authority of various party, state, and military entities. The paramilitary organization “operates an administrative system with unified Party, government, military, and enterprise roles”; has “made strenuous efforts to fulfill faithfully the responsibilities the state has entrusted to it to cultivate and guard the border areas”; and now oversees a sprawling commercial empire. According to the PRC authorities, the XPCC focuses on countering “seperatist”, “religious extremist”, and “terrorist forces” in the XUAR, which “have become a major threat to national unity and to Xinjiang's social stability”. In recent years, the XPCC has actively participated in the surveillance and detention of the Uyghurs in Xinjiang and has profited from this repression campaign via forced labor.
Recorded Future observed at least 2 possible recent instances of XPCC prisons purchasing Seagate or Western Digital HDDs. In October 2021, the XPCC First Division Aral Prison (新疆生产建设兵团第一师阿拉尔监狱) announced the winning bidder for a “monitoring and control [surveillance] equipment” contract, which included 40 Seagate drives and various products from Dahua, such as 31 color infrared network hemisphere cameras. Bidding documents associated with this contract show that the Seagate HDDs are surveillance-specialized drives. The XPCC First Division Aral Prison reportedly holds victims of the Xinjiang mass detention campaign. In August 2021, the XPCC Third Division Gemilik Prison (新疆生产建设兵团第三师盖米里克监狱) announced the winning bidder for a contract that, according to an attached product list, included 30 surveillance-specialized HDDs from either Seagate, Western Digital, or Japan-based Toshiba. The announcement specifically mentions Seagate’s ST8000DM004 computer drive, which suggests that the prison may have selected this drive over products from Western Digital or Toshiba. The XPCC Third Division Gemilik Prison reportedly holds victims of the Xinjiang mass detention campaign.
Outlook
Public security entities in China widely procure and use technology from companies in the US. In many cases, these entities likely leverage US technology to carry out relatively benign activities. However, Chinese public security entities also engage in significant levels of state violence and are tasked with intelligence and counterintelligence missions. As such, transfers of technology from US companies to Chinese public security end users risk inadvertently supporting state violence, intelligence work, and counterintelligence work in China. Without significant reforms to the US export control system or other government action, such transfers of technology to China’s public security system will almost certainly continue unabated for the foreseeable future.
The transfer of policing technologies is not a problem unique to US companies. During the course of our research, we frequently observed Chinese public security entities procuring products from companies in the UK, Israel, Japan, Italy, Germany, Canada, Taiwan, and other countries. Moreover, cross-border flows of technology often go both ways. For instance, while US companies have reportedly sold surveillance technology (which has reportedly been used against US protesters) to public security entities in China, Chinese companies have reportedly provided surveillance capabilities to law enforcement entities in the US. Many US law enforcement entities reportedly use surveillance drones from the China-based DJI, which appears to be a leading law enforcement drone provider in the US, very likely for activities such as search and rescue operations, collision and crime scene documentation, and hazardous material incidents, as well as against US protesters in some instances. Likewise, US federal and local law enforcement entities have reportedly used surveillance cameras from Chinese providers like Hikvision and Dahua. As such, the behavior of US companies selling policing technology to China must be considered alongside the growth of the global surveillance industry, the international expansion of mass surveillance, and other similar trends.
Editor’s Note: This is an excerpt of a full report. To read the entire analysis with appendices and endnotes, click here to download the report as a PDF.
Related