How to Use STIX for Automated Sharing and Graphing of Cyber Threat Data

MITRE, a not-for-profit organization with offices near Boston and Washington, D.C., has developed several interrelated toolkits to enable sharing of cyber threat intelligence between trusted parties. STIX is one of several components in what might be considered the MITRE cyber security platform.
The Department of Homeland Security, NIST, US-CERT, and other government organizations have aided in the development of STIX through MITRE, but now industry has begun to consider adopting STIX. Recent data breaches at major retailers and the Heartbleed vulnerability have shown private industry that their customers’ information is valuable and must be protected. The financial industry and intellectual property belonging to US firms are also vulnerable to cyber threats, so STIX may become one technology used to help guard them from attack.
STIX Overview
STIX itself is a set of XML schemas which together comprise a language for describing cyber threat information in a standardized manner. This is important because cyber threat sharing currently occurs manually between trusted parties; with a standardized way of describing the data, automated threat sharing becomes possible. For this purpose MITRE has also developed TAXII to share STIX data over HTTP and HTTPS.
STIX Benefits
STIX can be used to characterize indicators, TTPs, exploit targets, and other aspects of a cyber threat. STIX takes advantage of another MITRE schema, CybOX, to represent Observables, and can be extended to utilize existing schemas, such as CAPEC or OpenIOC.
For the purpose of developing the technology STIX has been implemented in XML, but STIX will likely later also have the same functionality built in JSON to support the needs of industry. There are Python code repositories available on GitHub with which the current XML schemas can be used to validate STIX XML documents.
STIX can be used to describe cyber threat intelligence manually or the process can be automated. For those looking to automate the production of STIX XML documents, MITRE has created Python and Java tools to do that. STIX can also be converted to HTML with the use of an XSLT transform. All of the materials referenced here can be found on the main STIX website or the GitHub page for the project.
There are no plans to create a public repository for storing STIX data, nor does such a thing yet exist. Data related to cyber threats can contain sensitive information that should only be shared over a secure connection using a protocol such as that described by TAXII. Some communities may create their own STIX data repositories meant to be shared among trusted members of the same industry. Public reporting of certain individual cyber threats may also be released in STIX format in the future.
STIX Example
In order to help users of STIX better understand the relationships between different aspects of a threat the technology is meant to make clear, STIX-Viz can be used to generate and display the graph of the different constructs. STIX-Viz is a standalone JavaScript application which takes advantage of the capabilities of Node.JS and Chromium rendering engine. There is a pre-packaged Windows .exe file available for use on the STIX Github page. The source code for STIX-Viz is also on Github, and can also be run from Mac or Linux. This was slightly more complicated, but can be accomplished in a few simple steps.
First start by installing Node.JS, Node Package Manager (NPM), and Node-webkit. Then bundle the STIX Viz program as a .nw app as described. Finally, navigate to /stix-viz/src/nodejs in terminal and run nodewebkit as administrator. The STIX-Viz app should pop up as a standalone window.
Once STIX-Viz is running, it should allow you to import an XML file, and then display a graph, tree, or timeline view. MITRE has provided sample STIX files for use with STIX-Viz.
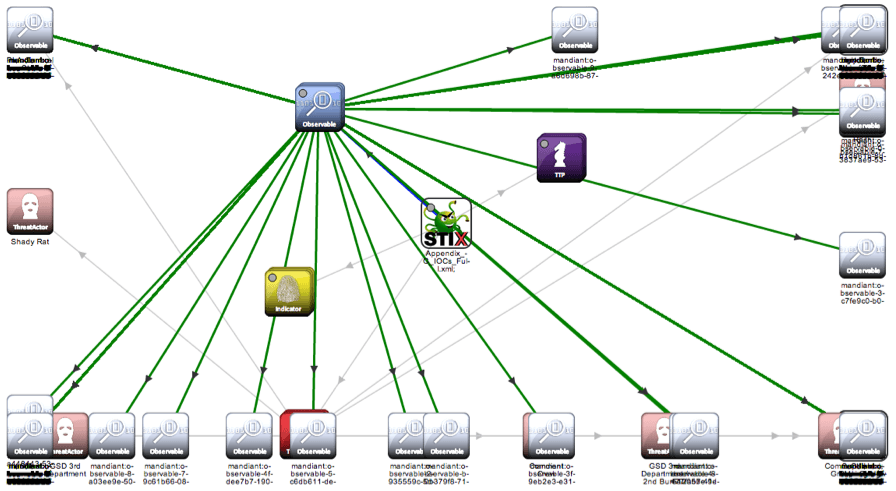
Figure 1: STIX-Viz running on OSX Mavericks.
STIX and Recorded Future
By managing information security threat indicators in structured formats, like STIX, defenders can automate the process of finding connections between internal incidents and external sources. This can work bidirectionally: searching Recorded Future for more context around internally observed indicators, or testing trending indicators from open source reporting against internal datasets.
Related