Stagefright Exploits Hit the Web
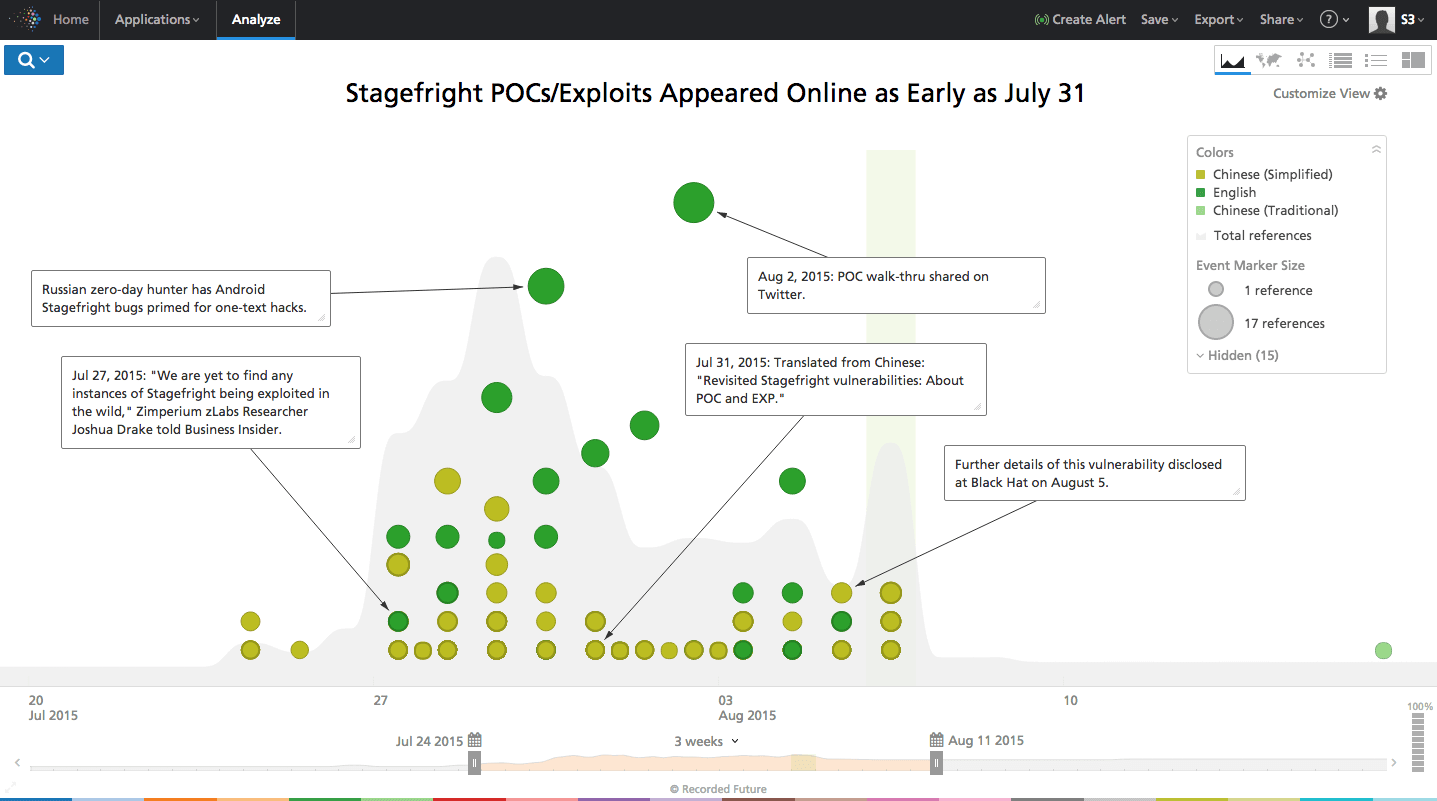
Exploits and proof of concepts (POCs) are appearing on the Web for Stagefright, hyped as the "Mother of all Android vulnerabilities" capable of gaining remote code execution privileges via a malicious MMS (e.g., a picture message). This collection of 10 vulnerabilities reportedly impacts 95% of all Android devices - over 900 million phones.
Recorded Future has identified shared exploits and POCs appearing on the Web 10 days after the July 21 announcement by Zimperium zLabs researcher Joshua Drake.
Click image for larger view
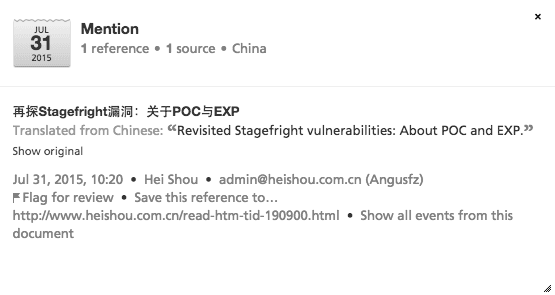
The first known publicly available POC appeared on Chinese language forum heishou.com.cn on July 31 and was subsequently shared on Twitter and reposted on other forums.
Packaged exploits for use by lower skilled cyber criminals do not appear available, but an increasing level of detail became available and shared on the Web over the past week.
The seven vulnerabilities tied to Stagefright (CVE-2015-1538, CVE-2015-1538, CVE-2015-1538, CVE-2015-1538, CVE-2015-1539, CVE-2015-3827, CVE-2015-3826, CVE-2015-3828, CVE-2015-3824, CVE-2015-3829) impact Google’s “Stagefright” media playback engine introduced in Android 2.2 (Froyo).
Google claims that Android 4.0 and higher aren’t as susceptible due to built-in protection against a buffer overflow attack.
Drake and Zimperium posted further details on August 5 and pledge to release an exploit on August 24. Carriers including Sprint and AT&T are scrambling to release patches.
Disabling auto-download for MMS mitigates this risk until a patch is available for Android users.
Related
