Increase the Power of Splunk With Threat Intelligence From Recorded Future
Security teams around the globe and across industries — from financial services, to manufacturing, to healthcare, to the public sector and beyond — rely on Splunk SIEM solutions to collect and analyze their internal security data. As a longtime certified integration partner, we’re proud to work with Splunk and empower SOC analysts with real-time threat intelligence to drive even smarter, faster security decisions.
Today, we’ll explore Recorded Future’s integration with Splunk Enterprise. But first, here’s a look at the current situation in the SOC.
Alert Overload in the SOC
Organizations are drowning in data, and it’s not hard to see why. As companies go deeper into their digital transformation initiatives, their IT infrastructures are made more complicated by new solutions, systems, apps, and processes that are frequently added to the mix. The average organization now uses 1,427 distinct cloud services, and it’s estimated that 73% of data goes unused.
As data chaos abounds and infrastructure expands, so too does the cyberattack surface. As a result, SOC analysts see thousands — even millions — of security alerts and events each day. Strapped for time and resources, most can only investigate 56% of the alerts they receive. And of the investigated alerts, only 34% are deemed legitimate — often after hours of manual triage.
Recorded Future brings real-time threat intelligence directly into Splunk, giving SOC analysts additional, rich context with full transparency. We surface and deliver threat intelligence in real time from the widest breadth of open, technical, and dark web sources, helping analysts make fast and informed incident verdicts, expand detection incidents within the network, and gain external threat awareness beyond the network.
Adding Threat Intelligence to Splunk: A Step-By-Step Guide
Recorded Future’s unique combination of automated data collection and human analysis generates high-quality intelligence that can be seamlessly correlated with Splunk data to identify high-risk threats before they impact the business.
Risk Scores: The First Part of the Story
With billions of indexed facts, threat intelligence from Recorded Future applies machine learning and natural language processing (NLP) to continuously analyze threat data from a massive range of external data sources. Every IP address, domain, URL, hash, or vulnerability it identifies is assigned a risk score, which can be seen as part of a Recorded Future Intelligence Card™. Intelligence Cards™ bundle essential information related to a specific investigation topic (a malware family, for example) and serve as a starting point for triage and pivot points during an investigation.
The following Intelligence Card™ shows a risk score of 98 out of 100, which is considered very malicious. With most solutions on the market, this is where the story stops. But with Recorded Future, the risk score just the beginning. We also tell you why this particular IP address was given such a high risk score — and why it deserves your attention.

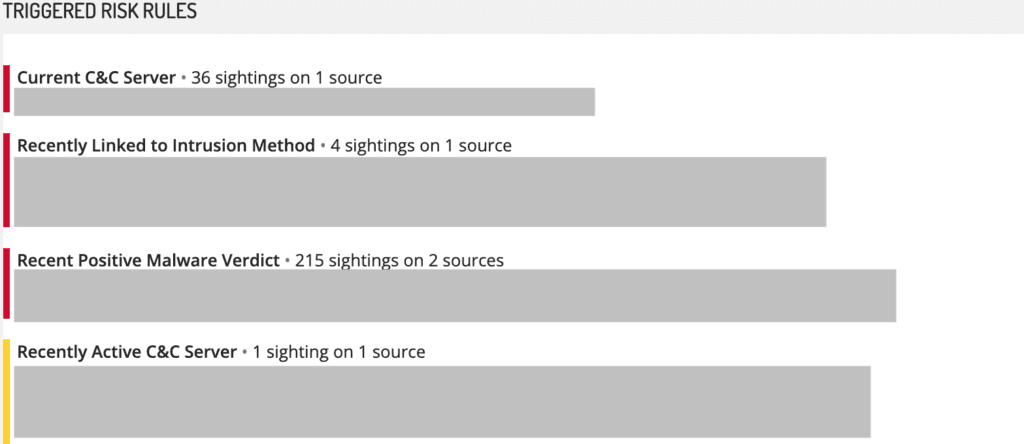
Risk Rules Paint a Bigger Picture
Rather than using black-box threat feeds, we use clear risk rules that factor into our risk scores, helping analysts quickly identify high-risk security events and minimize false positives. These risk rules are sourced from over 800,000 web sources and over 60 external threat feeds, and can be seamlessly correlated with Splunk to add valuable context to internal network observables.
Correlation can be critical for discovering new threats, but because indicators of compromise (IOCs) may only be valid for a certain amount of time, it’s important to correlate threat feed data with internal logs in as close to real time as possible within the time frame the threat intelligence is discovered.
Below, you can see a summary of all infrastructure and entities associated with this particular IP address, and how frequently they were recorded. Analysts can easily pivot into each entry for additional information as needed for their investigation. This information helps analysts to rapidly enrich alerts and refocus on the high-risk incidents that matter most.
Seamless Integration With Splunk
With the industry’s only complete threat intelligence solution powered by patented machine learning and artificial intelligence, Recorded Future delivers more context than threat feeds, updates in real time so intelligence stays relevant, and integrates seamlessly with Splunk.
With flexible deployment options, you can drop our dashboards into your Splunk Enterprise deployment, or use our commands and lookups to configure the dashboards and alerts that precisely fit your needs. It’s important to note that our integration with Splunk is done via extensible API, which means we are not adding any data on the Splunk side and no additional storage is required.
The three most common use cases for the Recorded Future Splunk integration are:
- IOC Enrichment
Rapidly contextualize alerts by enriching them with the broadest set of external data sources to ensure all detection gaps are closed.
- Correlation Identification
Achieve correlation between internal Splunk data and external threat intelligence to detect important incidents in your network that you might have otherwise missed, and drive rapid response — all while reducing the burden on security teams.
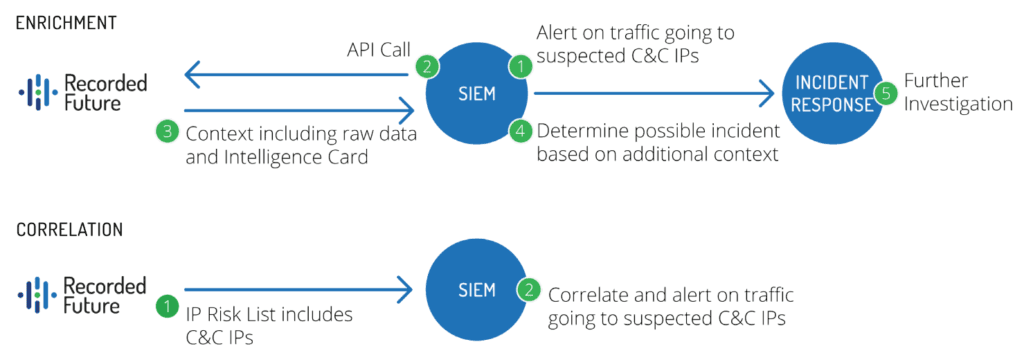
- Targeted Alerts
Continuously monitor for external intelligence directly relevant to your IP ranges, domains, and company, and receive contextualized, risk-prioritized alerts in real time that can be added to Splunk.
Here’s a look at the Recorded Future integration with Splunk in action:
- There’s increased traffic to a suspicious IP address — what should you do?
- Investigate that alert directly from Splunk and discover it’s a command and control server.
- Take quick, decisive action to block that IP address.
Learn More
Want more information about how Recorded Future can supercharge your Splunk Enterprise deployment with real-time threat intelligence? Email us at [email protected] for a demo or quote.
Related
