Take the Hard Work Out of Security Operations With the Intelligence Goals Library

At Recorded Future, we follow a few core tenets: One, that threat intelligence is only useful when it gives you the context you need to make informed decisions. Two, that threat intelligence is for everyone. And three, that people and machines work better together.
That’s why we launched the Intelligence Goals Library. It’s got all the threat intelligence use cases anyone needs, regardless of security role, all in one place.
Intelligence Goals are grouped under the umbrella of seven main security roles — threat analysis, incident response, vulnerability management, security operations, risk analysis, fraud, and security leadership — and within those goals are over one hundred use cases.
These use cases compile all kinds of preconfigured queries in one place so that it’s easy to search, browse, and discover new or relevant alerts. Activating a use case will send you real-time alerts relevant to your organization, including transparency into sources, helping you quickly understand why the alert was sent. Because they’re preconfigured and automated, the focus stays on intelligence requirements already aligned with established best practices rather than the granular details of setting up alerts and custom queries.
And Watch Lists, which are custom, configurable lists of your organization’s assets, are a central point to customize what the alerts are monitoring specific to your organization.
In this blog post, we’ll explore the security operations role category in the Intelligence Goals Library, looking at the different Intelligence Goals and their use cases within it.
Intelligence Goals for Security Operations
For security operations, Intelligence Goals help monitor for potential threats and alert on threats relevant to the specific organization.
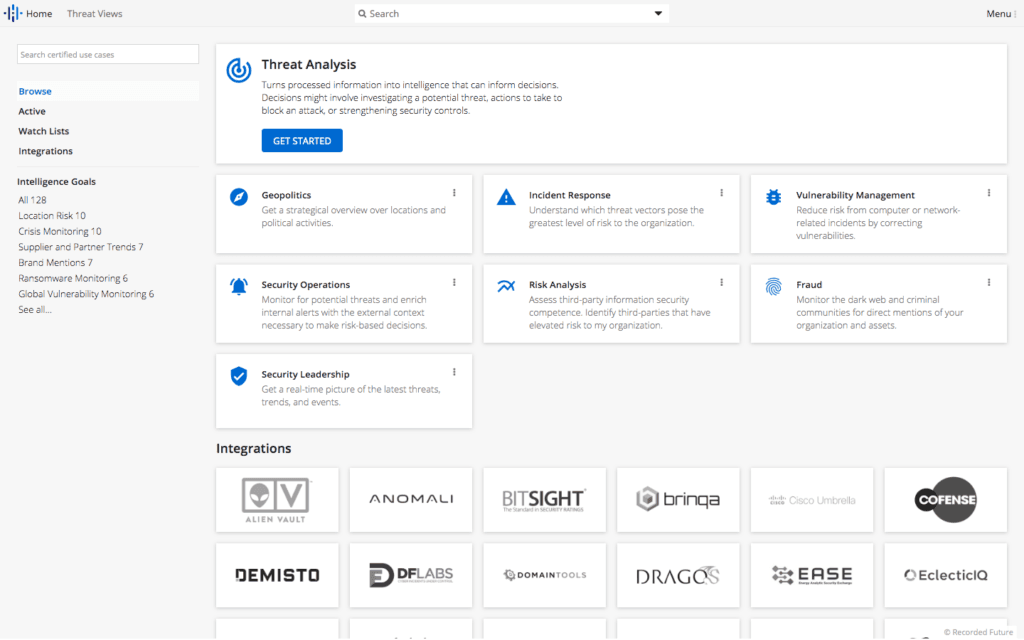
The Intelligence Goals Library home screen.
Security operations centers represent the first line of defense for the network of any organization that has one. SOC analysts perform many essential tasks, like log monitoring, incident response, compliance, penetration and vulnerability testing, key and access management, and more, all with the overall goal of monitoring network activity and protecting it from threats of all kinds.
As anyone who actually works or has worked in a SOC knows, it’s not an easy job. Any one of those tasks can take years of experience and specialized knowledge to do well. A lot of the work is both critically important to get done and extremely time sensitive, making it hard to know what to prioritize without more context than what many get from a series of terse alerts. Endless streams of data can overwhelm even the most experienced SOC analyst.
We’ve talked before about how threat intelligence is vital for quickly identifying relevant threats to your organization. But even with threat intelligence, there’s previously been a certain level of experience needed to know where and what to look for and sort through alerts to determine what’s relevant and what’s a false positive, and then prioritize which alerts to respond to first.
The Intelligence Goals Library makes this process much simpler for the SOC and does the heavy lifting for you. Instead of needing an experienced analyst to set up and configure alerts, all of the alerts are already set up within the library as use cases that can be turned on or off with one click. And these alerts are automatically updated when new sources are added, keeping them relevant.
Security Operations Intelligence Goals and Their Use Cases
There are nine different Intelligence Goals within the security operations role section of the Intelligence Goals Library, which include over 40 use cases. We’ll dive into a few examples of use cases within those goals.
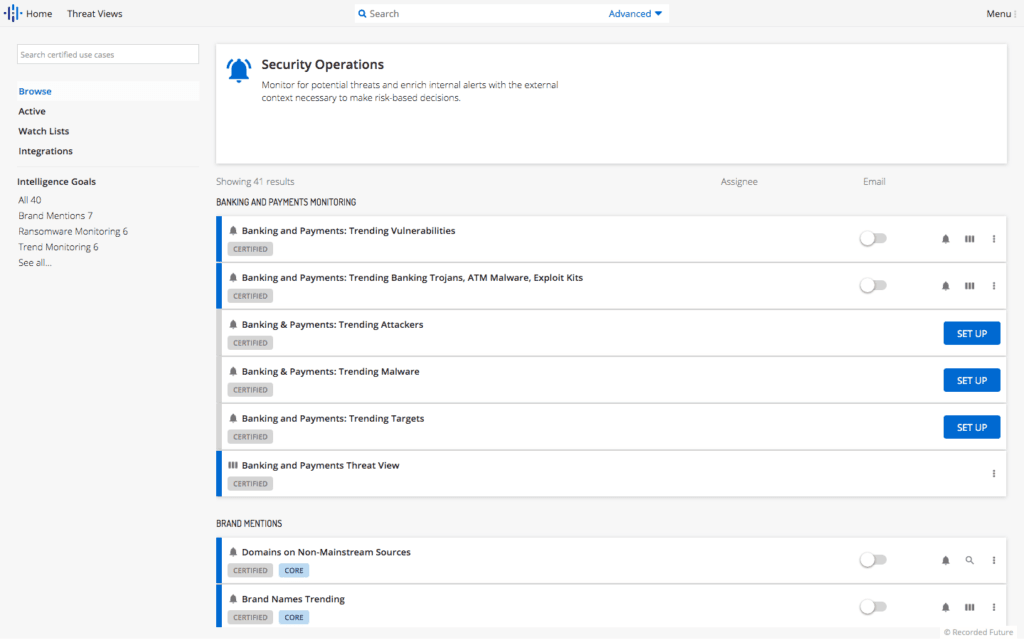
The security operations category within the Intelligence Goals Library.
1. Brand Monitoring
Keeping a lookout for mentions of your organization across the internet is an essential way to head off all sorts of attacks. A typosquatted domain, for example, can be a solid indicator of an impending phishing attack. Even simpler, threat actors on some forum in the criminal underground might directly discuss your brand in the course of planning an attack.
Through the Intelligence Goals Library, it takes just one click to set up automatic alerting on security operations use cases like mentions of your brand or domains across the web, URLs appearing on code repositories, cyber events that can affect your brand, and more.
2. Ransomware Monitoring
It’s a safe bet that ransomware will continue to trend as a popular method of attack in 2019 and beyond. In the Intelligence Goals Library, you can set up alerting on use cases around ransomware topics like trending exploit kits, targeted software, or the addresses of payment sites and command-and-control (C2) domains that are known to be associated with ransomware attacks.
3. Cyberespionage
Not all threat actors are motivated only by money — or at least, not in such simple terms. Stopping other forms of attack, like efforts to steal data or disrupt your organization’s vital systems and processes, is easily done with the use cases in this Intelligence Goal.
Use cases in this goal include alerts for trending advanced persistent threats (APTs) in your industry or area, targets or vulnerabilities that might be related to your organization and the systems you use, or relevant results on remote-access trojans (RATs), exploits, and rootkits.
Learn More
Keep an eye out for future blog posts exploring how the Intelligence Goals Library helps with other security roles — we’ll look at vulnerability management next.
Related