Remote Threats to Remote Employees: How Working From Home Increases the Attack Surface
In response to the COVID-19 pandemic, many organizations have shifted to working from home for the foreseeable future — this means that organizations will have a largely (or entirely) remote workforce for the first time.
This creates a situation that is ripe for cybercriminals and nation-state actors to exploit. As we have observed with the rapid adoption of COVID-19-themed scams and attacks against the Olympics, threat actors — both nation-state and cybercriminal — are quick to exploit new and evolving situations.
For security teams, the sudden change in an organization’s network topology means a vastly expanded attack surface with little time to adapt to the new reality. For employees, generally, it means having to be even more vigilant of potential attacks. In this expanded, remote working environment, there are two focus areas of attack that need to be addressed by defenders: technical and organizational.
Technical: Exploitation of Telework Applications
This new reality radically alters the network baseline. Instead of an environment where 80% or more of the employees at an organization spent most of their time at a desk in an office, everyone is now accessing the same systems, but remotely. Not only does this change the network topology, it also can create challenges for user and entity behavior analytics (UEBA) tools.
Employees will suddenly be accessing systems at unusual times, and they may be accessing systems they didn’t regularly access previously. It will also be a challenge for organizations that built their security tools to primarily monitor the edge of the network, rather than the core. Employees, especially those using their own devices to connect to a VPN, may be introducing new malware into the heart of the network, and if the organization is not monitoring for malicious activity there, it may be missed.
Common applications for remote working (telework), such as Zoom, Citrix, Confluence, Slack, Skype, and Google Suite are already frequent targets of attackers, but when the usage of these tools was kept primarily behind a firewall, there was better control over the risk. Now that users will primarily be using these tools outside of the firewall, there is more risk of exploitation, especially if users are forced to use their own laptops, desktops, and phones to connect into the office. Phones in particular can be a problem — for example, Recorded Future has already noted the presence of the CovidLock Ransomware targeting Android users, as well as Android malware that steals Google Authenticator codes. Google Authenticator is used by many organizations for two-factor authentication.
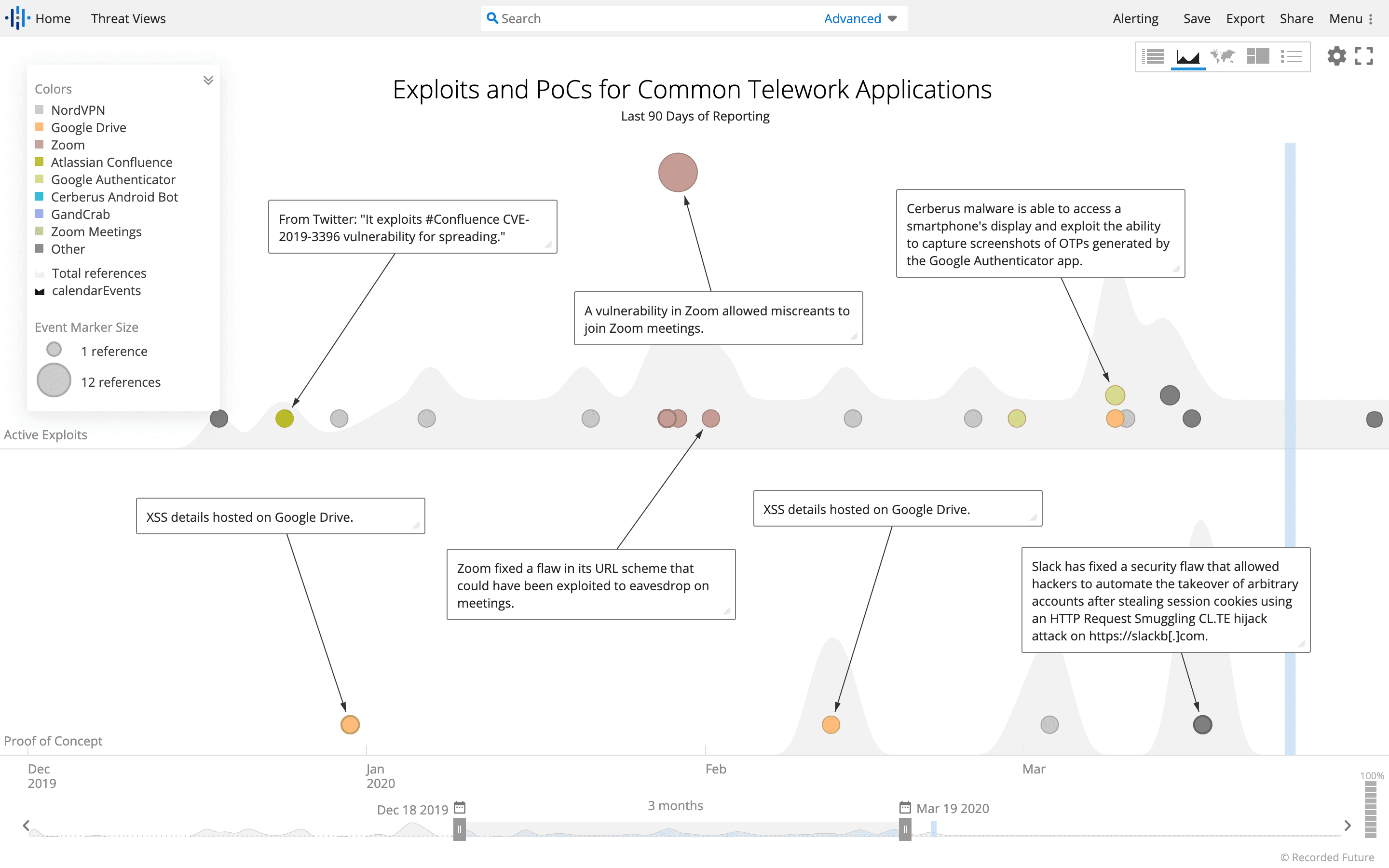
Attacks against common telework applications over the last 90 days. (Source: Recorded Future)
As the image above shows, in the last 90 days alone, there have been several published vulnerabilities exploited by malicious threat actors against these common teleworking tools. Recorded Future has also noted an uptick in DDoS attacks against some VPN providers, as confirmed by the Cybersecurity and Infrastructure Security Agency (CISA). Even before the sudden influx of new teleworkers, there had been an uptick in attacks against Pulse VPN by threat actors using Sodinokibi ransomware. Successful attacks like these could allow attackers to gain access to an organization through compromised VPN connections.
While there has been a notable uptick in attacks against VPNs and other telework applications in recent months, these tools have been the target of cybercriminals and nation-state actors for much longer than that. The new reality of expanded telework simply gives these threat actors a chance to capitalize on the techniques they have already been developing for years.
In February, cybersecurity company ClearSky reported on a three-year campaign they dubbed Fox Kitten, conducted by Iranian operators to infiltrate organizations in the IT, telecommunications, oil and gas, aviation, government, and security sectors. The campaign exploited known flaws in Palo Alto Networks (CVE-2019-1579), Pulse Secure (CVE-2019-11510), and Fortinet Inc (CVE-2018-13379) systems to gain access to their targets.
Iranian actors are not the only ones targeting these vulnerabilities. According to a 2019 report by FireEye, the Chinese state-sponsored group APT5 has been exploiting many of the same vulnerabilities, looking to gain access to targeted organizations. The target of this APT5 campaign has been primarily telecommunications and technology companies. The United Kingdom’s National Cyber Security Centre (NCSC) also reported on other nation-state actors exploiting these vulnerabilities.
It’s not just nation-state threat actors who are exploiting these vulnerabilities. Cybercriminals have been heavily targeting Citrix vulnerabilities, especially CVE-2019-19781, as a method of gaining access to their victims. The ransomware threat actors behind DoppelPaymer used the Citrix vulnerability to gain access to Bretagne Télécom. The Ragnarok ransomware team has also focused on scanning for and exploiting CVE-2019-19781 as a way of gaining access to target organizations. The Credit Union National Association (CUNA) was also the victim of a ransomware attack that exploited this vulnerability. These are just a few of many more examples of threat actors exploiting VPNs and remote login and/or work technologies.
Organizational: Support Chaos
Over the next couple of weeks, help desks at many organizations are going to be overwhelmed (assuming there is a helpdesk and not simply the IT person). Remember, these teams are suddenly responsible for keeping up a network of remote users, using these to an extent that has not been seen before at this organization. They may be out of their league, and as Recorded Future has documented, misconfiguration of services is a top risk to cloud services, thus increasing an organization’s risk. Many of these remote work setups were designed and implemented on the fly to work at a large scale, often with little documentation. This can leave users confused and unsure what to do, but still with a job to carry out.
This type of scenario is ripe for workarounds that may inadvertently expose sensitive information. For example, if an organization requires that all internal video conferences be conducted over the VPN, but users are having trouble configuring their VPNs, they may opt to hold those meetings outside of the VPN or switch to a different, unauthorized, video conferencing system.
Similarly, if users cannot reach internal file sharing systems, they may decide to share sensitive documents using consumer file-sharing solutions. It’s common for individuals to reuse passwords between different accounts and applications, so it is likely that at least some people would sign up for these services using passwords already exposed on marketplaces in the criminal underground. Without the proper security controls in place, it may be impossible to know where all of these sensitive files are stored.
As shown by the examples provided above of how threat actors are manipulating the fear around COVID-19 to scam individuals and organizations, this increased level of confusion and uncertainty, leading to a desire for more information, may make users more susceptible to phishing attacks — especially well-crafted ones. Given the potential for chaos, it is likely that users will be more likely to click on a fake tech support email or open a Word document that purports to be “VPN Instructions.”
In fact, employees are undoubtedly already expecting to hear from the helpdesk or IT team during this transition, so threat actors are trying to exploit this expectation. Users also might be more likely to fall for whaling emails, as seeing other users’ personal email accounts in use could become more common during this transition period. Threat actors on dark web forums are openly advertising and discussing phishing content related to COVID-19. For example, FalosOfTanos, a member of a dark web forum, is selling a phishing method using an interactive COVD-19 map to deliver a malicious payload.
Another potential problem could be the influx of more commodity malware into your organization. As more users are connected to your network, often using their own computers that don’t have the same security profile as your organization’s systems, they could introduce new malware to your network via VPN. Even if your normal defenses could easily squash these new attacks, the introduction of so many new machines, along with the increase in potential threats, could lead to threats being missed by an overwhelmed SOC.
Combating These Attacks
Combating these attacks requires planning and awareness on the part of everyone in the organization. We recommend the following steps:
IT and security teams should have a well-documented plan for working from home, as well as backup solutions if the primary solutions don’t work. This documentation should include a minimum security profile (fully patched operating system, antivirus protection, and so on) for any system connecting to the organization.
Security teams need to plan to ensure parity of security controls between the remote workforce and the on-premise workforce.
Combined with security controls, incident detection tools should work equally well with remote and on-premise systems.
Both incident response and security controls should be tested regularly to ensure they are working as expected.
Helpdesk support should ramp up, perhaps recruiting more technically savvy users to assist.
Telework applications need to be prioritized for patching and configuration changes, and monitored closely for announcements about vulnerabilities, proof-of-concept (PoC) exploit code, and configuration vulnerabilities in those applications.
If your organization is monitoring password dumps for employee email addresses, consider expanding that monitoring to include personal email addresses.
Monitor for VPN activity from strange locations. Especially with all the travel restrictions in place, there should be more homogeneity in VPN connections.
During this period, it may be more likely that an attack will slip through the cracks. Test to make sure that your security or IR team can effectively remediate these attacks remotely.
Employees should be even more vigilant about incoming email. There will be a spike in phishing and whaling emails, so be suspicious of everything and don’t hesitate to pick up the phone and call someone if you suspect an email is fraudulent.
Since, as discussed above, there is an increase in phishing and social engineering attacks during this period of expanded telework, communicate clearly with your workforce about the threats, what they should be looking for, and plan simulated attacks.
Keep in mind that your security and IT teams are going to be under even more pressure than usual during this time. Management should be sure to provide for the emotional wellbeing of the team to help reduce stress levels as much as possible.
Related
