How to Reinforce Your Security Operations Center With Threat Intelligence
In today’s cybersecurity landscape, security information and event management (SIEM) systems have become table stakes for modern security teams in companies of all sizes. Bombarded with an unprecedented amount of internal logging and telemetry data, it is simply impossible for security teams to manage all of that information without the automation that a SIEM can provide.
By creating a central repository for log data and creating customizable queries for intuitive arrangement of those logs, SIEMs now enable security teams to gain visibility across their organization’s systems in a timely enough manner to turn that telemetry into actionable data points.

Popular SIEM integrations with Recorded Future.
The SIEM has become the first line of human defense from cyberattacks, where events from malicious traffic infiltrating firewall defenses can first be detected. Telemetry from firewalls, intrusion detection systems (IDS), endpoint protection platforms (EPP), and outputs from vulnerability scanners and netflow collection devices can all be ingested by the SIEM and presented to security operations center (SOC) analysts in virtually real time. It is no exaggeration to say that SIEMs are a more powerful tool today than ever before, collecting more formats of log data and at a greater scale than ever before. This is great news for the SOC — or it was, until the sheer volume of logged data and alerts began to overwhelm analysts.
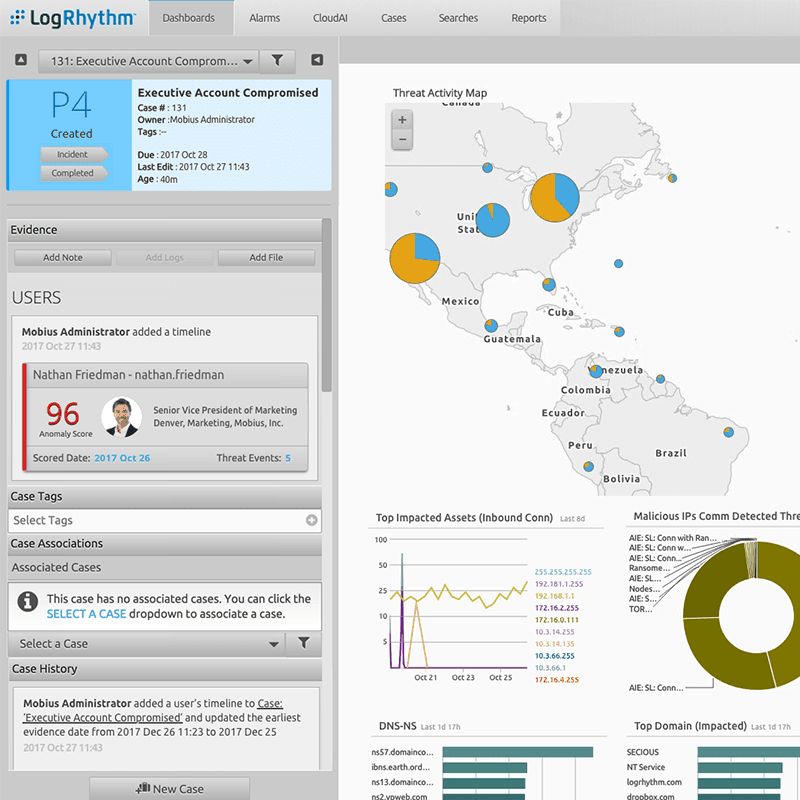
Recorded Future integration with LogRhythm.
SOC analysts’ primary problem has now become determining which alerts are truly a priority. Analysts must now ask themselves, “How many of these alerts are accurately reflecting a credible threat to the organization, and am I confident enough in my answer to bet my job on it?”
The problem is, the traditional SIEM deals with looking at internal logs — telemetry from systems owned by the organization. What is often missing is the external threat intelligence data that, when paired with that internal telemetry, can paint a more complete picture of a credible threat hiding in all that log data. By applying accurate threat intelligence to the logs coming into the SIEM and setting alerting thresholds to appropriate levels, the SOC can ensure that their analysts are only reacting to credible threats, and that the low-priority or inaccurate alerts never surface.
There was a time (not more than a few years ago) when the collection, scrubbing, processing, and consumption of external cyber threat intelligence data was so costly and time-consuming as to be prohibitive for most security organizations worldwide, much as internal telemetry was before the advent of the SIEM — but no longer. Threat intelligence feeds, providers, and aggregators have collectively brought the cost of using threat intelligence down while consistently expanding the applications of its use. This democratization of threat intelligence is no more powerfully reflected than by the widespread adoption of threat intelligence-armed SIEMs.
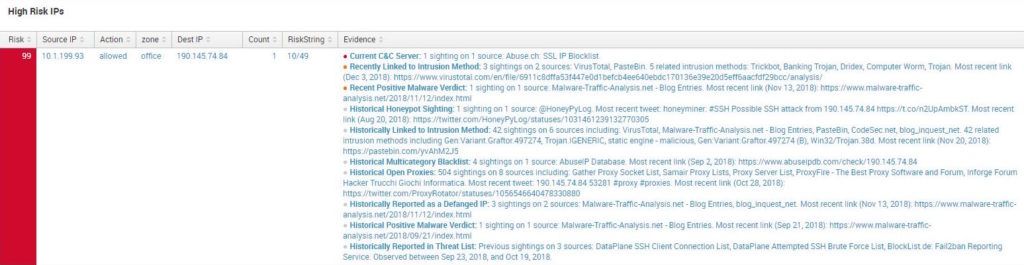
An IP address enriched within Splunk through the Recorded Future API.
By arming SOC analysts with an accurate snapshot of the true level of malicious activity known to be attributed to a particular indicator of compromise (IOC) logged by the SIEM, the analysts can approve decisive action at the SOC level, shielding the organization without wasting precious exposure time or needlessly engaging higher-tier engineers. Equipped in real time with the knowledge that an IP address is, for example, of Russian origin and is part of a suspicious subnet that has no legitimate business communicating with the network, a SOC analyst can confidently take actions that would otherwise be cloudy judgment calls fraught with political risk to their jobs.
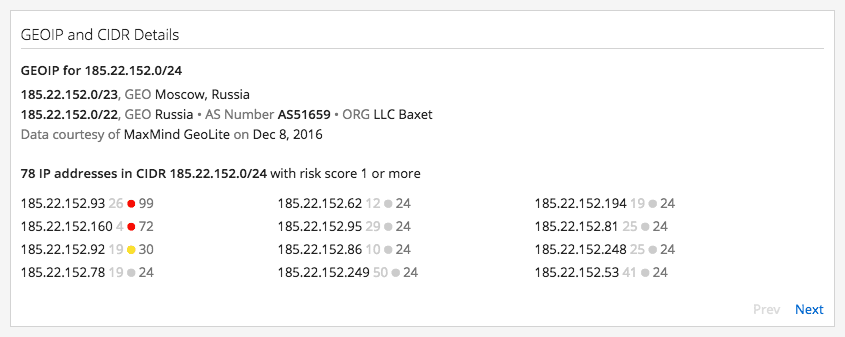
Geolocation information about suspicious IPs within Recorded Future.
Finally, tapping into cyber threat intelligence enables SOC analysts to feed tangible, empirical evidence of malicious activity associated with an IOC into after-actions and incident response workflows. This eliminates massive amounts of manual collection labor and time as this data moves through the rest of the organization’s security ecosystem. When the blocked activity is reported to the next tier, an enormous amount of forensic data gathering has already been executed at the SOC level, and in a timely enough fashion to be actionable during incident response.
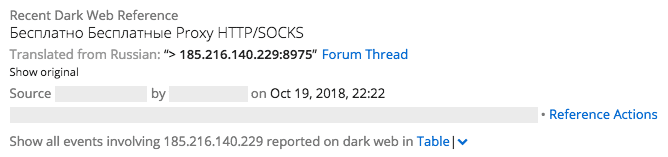
Dark web chatter and more context surrounding suspicious IPs detected by the SIEM, enriched by Recorded Future.
Enabling SOC analysts to take timely and decisive action at key junctures of a cyber event is a force multiplier for all organizations. Equipped with threat intelligence on their SIEM, SOC analysts can greatly reduce the window of time that their organization is exposed to malicious cyber activity, empowering them to confidently take blocking actions and initiate the next phase of forensic investigation. With modern massive data breaches triggered and executed in mere minutes, every second counts, especially on the front line of the modern security operations center.
To see how Recorded Future can help bring the power of threat intelligence into your SOC with our many technology partners in the SIEM space, request a personalized demo today.
Related