Ransomware Trends in Australia: 2021 to 2022

Executive Summary
Ransomware threat actors continue to adapt and evolve as the number of attacks increase globally. Ransomware trends in Australia have faced a similar trajectory. The expansion of ransomware-as-a-service (Raas) has made ransomware more accessible, despite global law enforcement efforts to disrupt ransomware gangs. Geopolitical events such as the Russian invasion of Ukraine resulted in dips in ransomware, but the overall trajectory continues to rise. Initial access brokers (IABs) on dark web and special-access forums are essential for ransomware affiliates to gain access into compromised networks. Before the deployment of the ransomware payload, threat actors rely on “precursor malware” for reconnaissance, lateral movement, access escalation, and exfiltration. Organizations can mitigate against ransomware attacks if they are able to identify initial access sales or detect precursor malware on their networks.
Key Findings
- Australia averages 6 reported ransomware attacks per month despite geopolitical events resulting in noticeable declines. In 2021 and 2022 LockBit has been the most prolific gang to target Australia. However, a new Russia-based ransomware group, ALPHV, emerged at the end of November 2021 and quickly became the dominant ransomware gang targeting Australia in 2022.
- To conduct a successful ransomware attack, threat actors require remote access to compromised networks. Ransomware affiliates often purchase these accesses on dark web and special-access forums. Affiliates subsequently use “precursor malware” to move laterally through systems, escalate privileges, and deploy ransomware.
Background
In recent years, ransomware has become a serious threat to most modern, IT-based economies and societies. What sets ransomware apart from other cyber threats such as espionage is its direct harm to society and the availability of affected systems.
In Australia, ransomware attacks have caused significant problems for many organizations: hospitals are unable to access critical patient medical histories, significantly delaying elective surgeries (Eastern Health); telecommunication suppliers are disrupted (Schepisi Communications); casinos are forced to close (Federal Group); sensitive government employee data is stolen (Frontier Software); and television networks are taken offline (Channel Nine). On top of the immediate effects, ransomware incidents also result in lost revenue, mistrust, and frustration.
The effects of ransomware attacks have persuaded governments around the world to recognize ransomware as a serious threat, and law enforcement around the world has cracked down hard against both ransomware operators (such as Egregor) and facilitators (such as Emotet). In Australia, new legislation has provided law enforcement with additional powers to disrupt cybercrime actors and has mandated critical infrastructure risk-management programs. However, despite these efforts, the number of ransomware attacks both globally and in Australia continues to rise. This report gives an overview of the ransomware situation in Australia from January 1, 2021 to June 30, 2022. It provides an in-depth, Australia-specific analysis based on a unique data set of past ransomware attacks. Finally, this report draws on findings from previous Recorded Future research that highlights the importance of the stages before the deployment of ransomware. By identifying Australian initial access sold on dark web marketplaces and the early-stage malware targeting Australia, the report articulates how organizations can mitigate against ransomware.
Technical Analysis
Data Collection
This report’s analysis is based on a unique data set composed of publicly available information collected over the last 2 years. Most of the ransomware attacks were detected through dedicated leak websites — websites used by ransomware operators to communicate with the public and extort their victims. A smaller number of the attacks were found manually through disclosure reports by affected organizations, news reporting, and other sources. The true number of attacks is likely significantly higher, in part because Australia (like most countries) currently does not have a reporting requirement for ransomware attacks. All of the initial access sales were observed on dark web marketplaces such as Exploit and XSS forums. The malware events were detected through network traffic analysis (NTA), an industry term for monitoring and analyzing data traveling through a network and providing a mechanism to detect and respond to adversaries. Recorded Future has developed methods to observe this midpoint traffic between the attacker and their victims as attackers build, stage, and launch attacks. This collection is only a small sample of malicious traffic targeting Australia; the actual number of Australian IPs beaconing to malicious command-and-control (C2) infrastructure is likely to be much higher.
Australian Ransomware Trends 2021 to 2022
Like most cyber threats, ransomware attacks continue to adapt and evolve. We previously reported on 5 high-level trends in victimology, technological sophistication, organizational structure, and extortion schemes that have shaped this evolution.
Ransomware attacks have not spared Australia, and the number of recorded attacks continue to grow in part due to an increase in media coverage and the expansion of the ransomware-as-a-service (Raas) model that makes ransomware more accessible to criminal syndicates. This section gives an overview of ransomware attacks against Australian organizations in 2021 and 2022.
Ransomware Is Increasing
From January 1, 2021 to June 30, 2022, the number of reported ransomware attacks in Australia has continued to follow a similar trajectory as global ransomware attacks (see Figure 1). This increasing trend in ransomware attacks is possibly attributable to the following factors:
- Higher activity: Despite fewer ransomware gangs observed targeting Australia in 2022, the larger gangs that were already active in 2021 increased their activity even further in 2022 (see Figure 2). Among other reasons, this may be related to the reinforcement effect of the RaaS model.
- Higher ransoms and more media coverage: With higher ransoms demanded, it has become harder for victim organizations to pay without attracting public attention. Also, due to government pressure to report ransomware incidents, the number of reported attacks in Australia has increased.
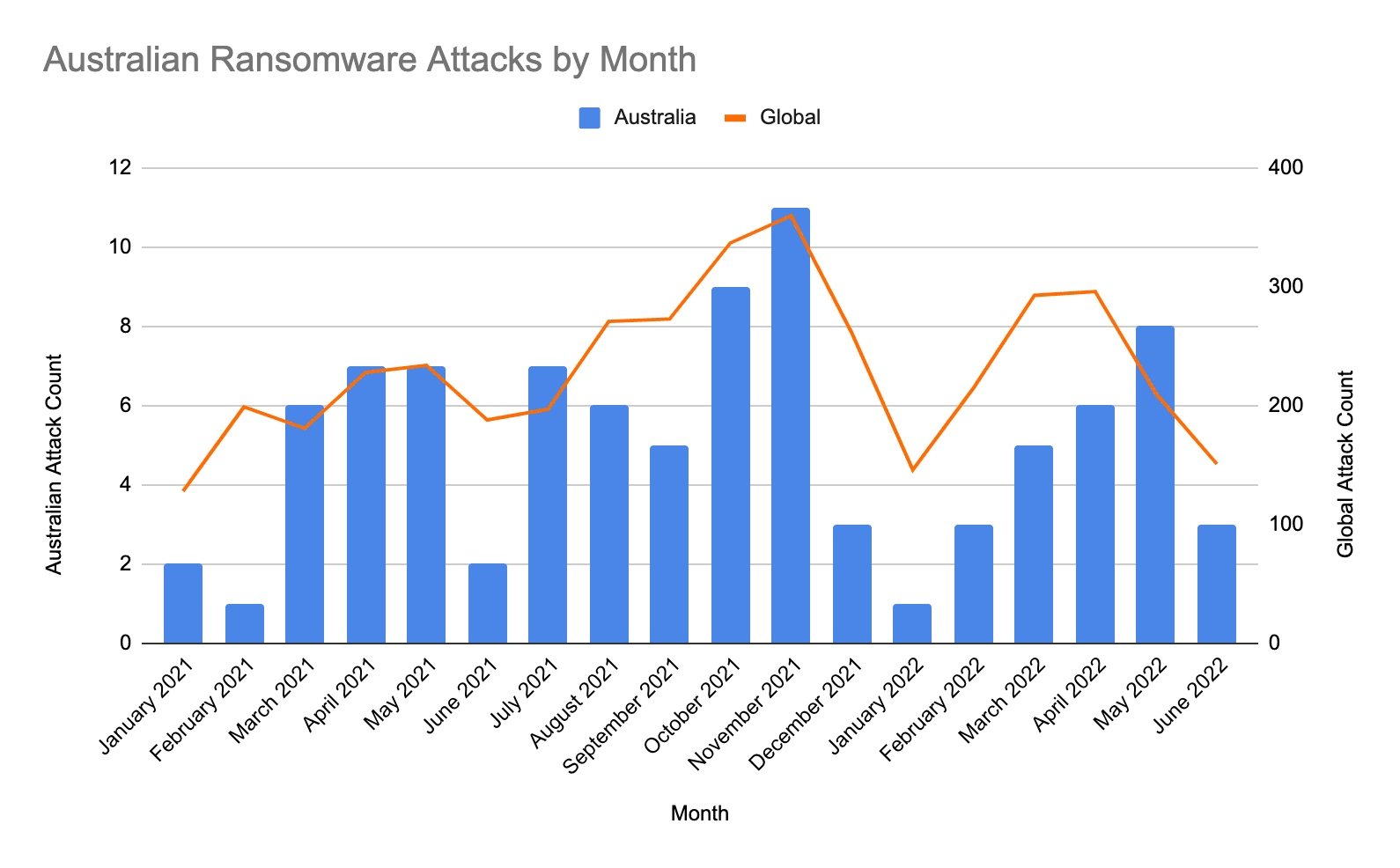 Figure 1: Ransomware attacks in Australia and globally by month from January 1, 2021 to June 30, 2022 (Source: Recorded Future)
Figure 1: Ransomware attacks in Australia and globally by month from January 1, 2021 to June 30, 2022 (Source: Recorded Future)
Reactions to Current Events
Between January 1, 2021 and June 30, 2022, there has been an average of 6 ransomware attacks targeting Australian organizations per month, with some exceptions related to:
- Russia/Ukraine conflict: Both globally and in Australia, ransomware attacks declined in the lead-up to Russia’s invasion of Ukraine in February 2022. However, ransomware numbers have steadily increased in the following months.
- Conti disbands: Prior to Conti’s official shutdown in May 2022, the group had several setbacks that may have affected their activities. In February 2022, Conti formally sided with Russia following its evasion of Ukraine. This led to over 60,000 messages from their Jabber server being leaked. In May 2022, it was reported that most of the group's servers had been shut down.
- Putin and Biden meeting: The decrease in attacks in June 2021 is believed to be linked to the then-upcoming meeting between Putin and Biden on July 9, 2021. This meeting had ransomware high on its agenda and entailed uncertainty regarding future governmental tolerance for many ransomware operators.
- Takedown of Emotet: The decrease in attacks in February 2021 is believed to be linked to the takedown of Emotet, an important ransomware facilitator, and the shutdown of Egregor around this time. In November 2021, Emotet resurfaced, with the updated variant being capable of encrypting network traffic and gathering system information from affected networks.
These exceptions can also be observed when looking at ransomware attacks from a global perspective on Recorded Future’s Ransomware Tracker.
Who’s Targeting Australia
In 2021, LockBit 2.0 was the most active ransomware gang in Australia and they continue to be active in 2022, having rebranded as LockBit 3.0 in June 2022. However, the shutdown of REvil (Sodinokibi) in October 2021 and the disappearance of BlackMatter a few weeks later opened up a new market opportunity for a sophisticated ransomware affiliate program. A new Russia-based ransomware, ALPHV, emerged at the end of November 2021 and quickly became the dominant ransomware gang targeting Australia in 2022. Similarities between APLHV and both REvil and BlackMatter are well reported. Noticeably, in 2021, there were a high number of attacks that could not be attributed to any ransomware gang. This might be due to organizations not knowing or not being willing to say what gang attacked them, or the incident not appearing on an extortion website.
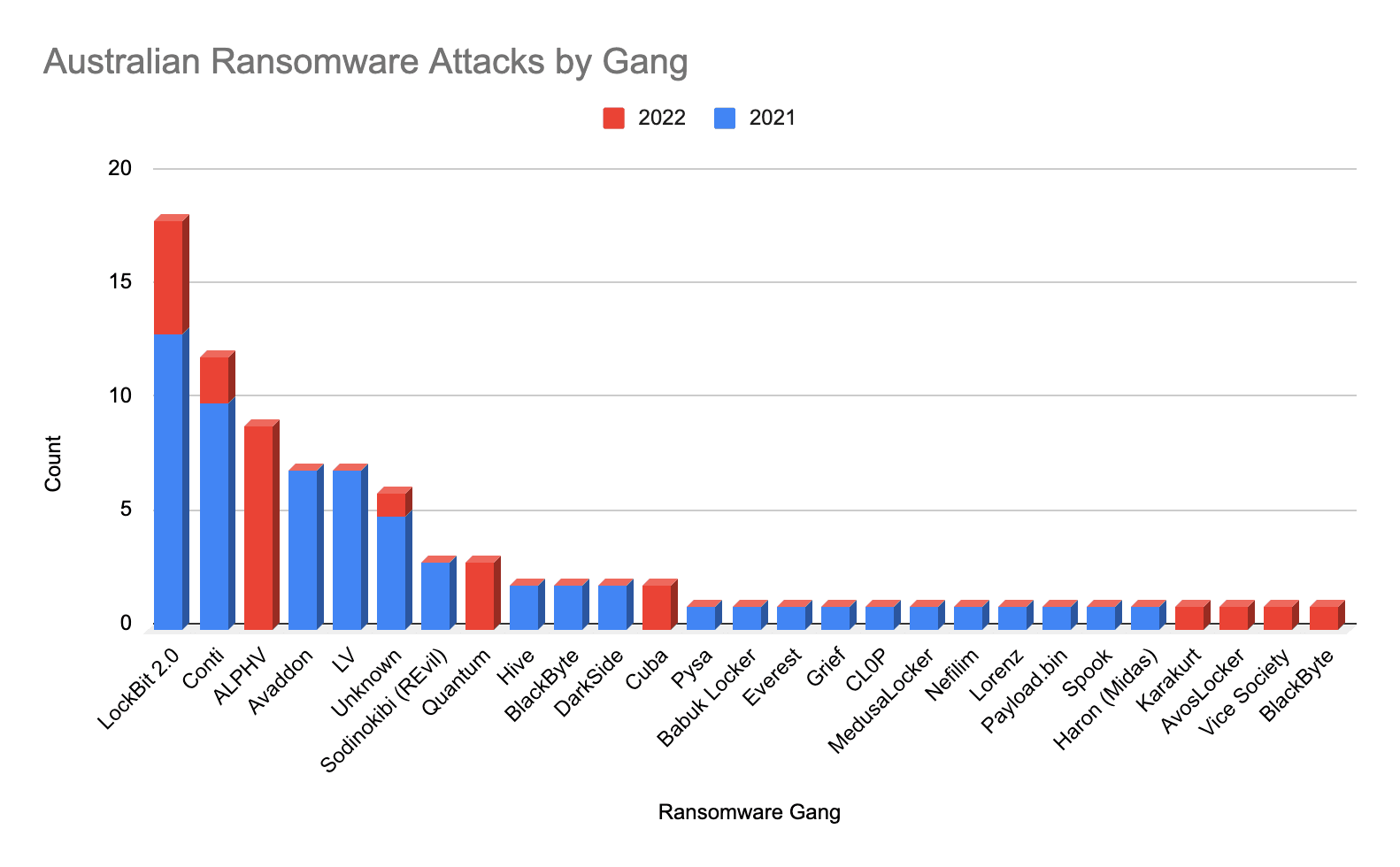 Figure 2: Ransomware attacks in Australia by group and year from January 1, 2021 to June 30, 2022 (Source: Recorded Future)
Figure 2: Ransomware attacks in Australia by group and year from January 1, 2021 to June 30, 2022 (Source: Recorded Future)
Initial Access
Once an organization falls victim to ransomware, it is too late for mitigation and prevention strategies to be effective; organizations shift instead to damage control. Previous reporting has highlighted the importance of “initial access brokers” (IAB) who sell remote access to compromised networks and compromised credentials on dark web and speak-access forums. These accesses are required for threat actors to conduct successful attacks such as malware loader deployment, data exfiltration, and ultimately ransomware deployment. It is in these early stages of the attack that mitigation and prevention strategies can be the most effective. Through identifying leaked credentials, access to sales, or malware on networks, organizations can reduce their risk of ransomware attack.
Australian Access for Sale
Access to Australian corporate networks is often sold on top-tier Russian-language forums such as Exploit, XSS, or Ramp, but it is possible to purchase access on low-tier or mid-tier English-speaking forums such as BreachForums or the now-defunct Raid Forums.
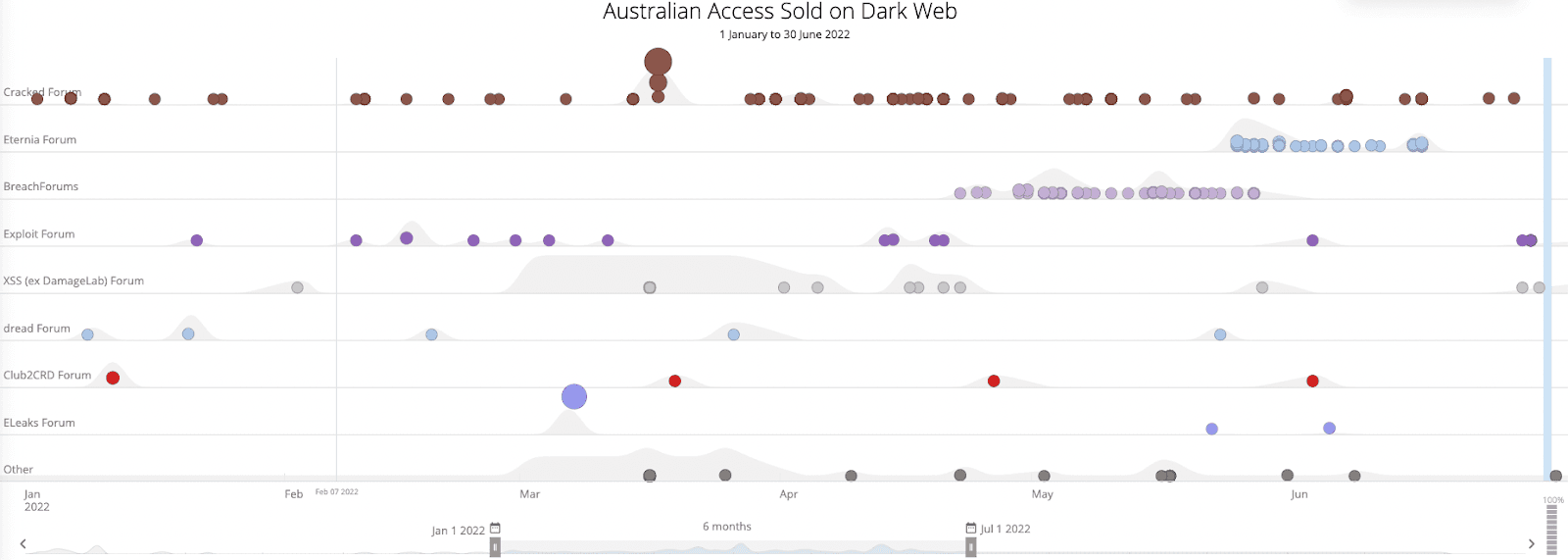 **Figure 3: **Australian accesses for sale on dark web and special-access forums (Source: Recorded Future)
**Figure 3: **Australian accesses for sale on dark web and special-access forums (Source: Recorded Future)
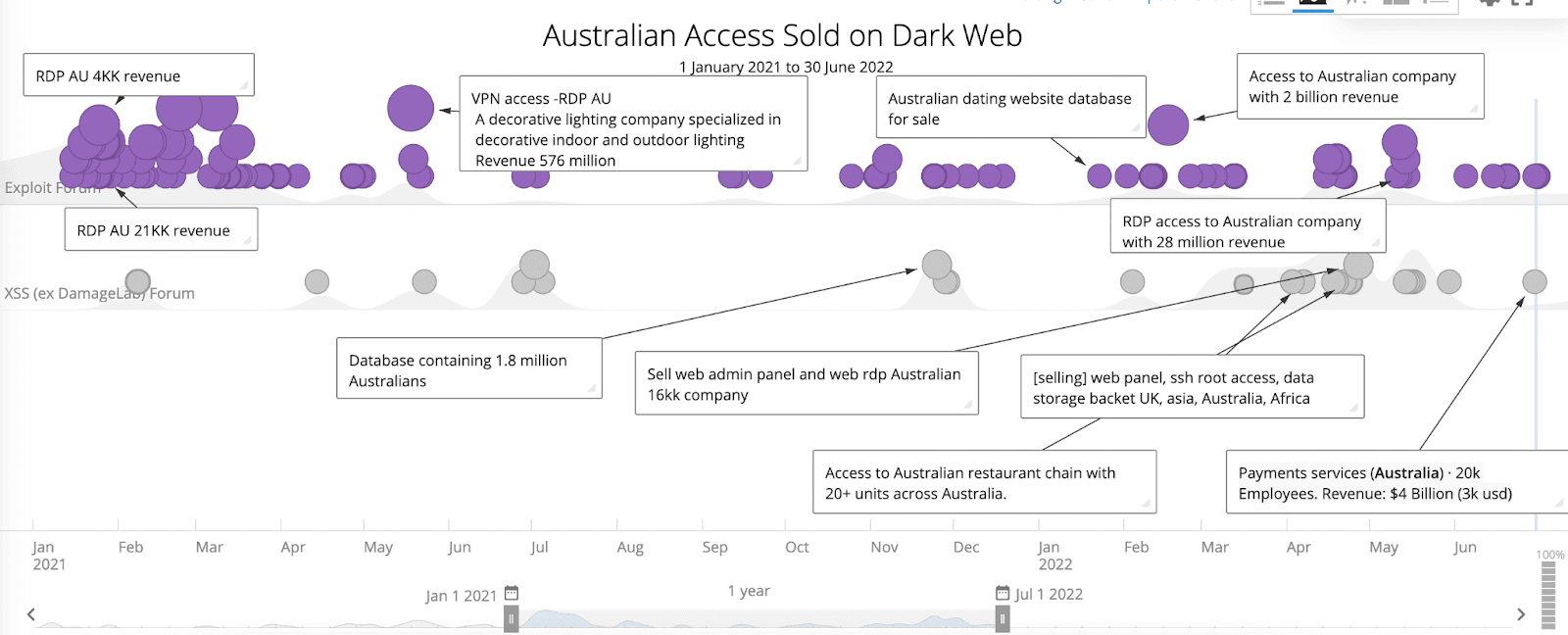 Figure 4: Australian accesses for sale on Exploit and XSS Forums (Source: Recorded Future)
Figure 4: Australian accesses for sale on Exploit and XSS Forums (Source: Recorded Future)
There aren’t any obvious trends in terms of threat actors consistently selling Australian access; these threat actors may simply be opportunistic, and they frequently change monikers to avoid arrest.
Precursor Malware
Ransomware is the last stage of the initial attack; threat actors often rely on “precursor malware” for reconnaissance, lateral movement, access escalation, and exfiltration prior to deploying the ransomware payload. Trickbot and Emotet have previously been observed as precursor malwares for Conti and Ryuk ransomware, respectively. Before their shutdown, IcedID was associated with Egregor and Maze ransomware attacks and had subsequently been observed in the deployment of REvil. QakBot has been used for lateral movement in recent Black Basta ransomware attacks and has previously been observed in Prolock and Egregor ransomware attacks. Early this year Dridex was linked with an Entropy ransomware campaign, but it was previously associated with Evil Corp and their WastedLocker and Hades ransomwares. If organizations can detect and remediate precursor malware through the deployment of detection rules or network monitoring, it may help mitigate against ransomware. To take one example, on November 27, 2021, Australian energy provider CS Energy was listed on Conti ransomware’s extortion website (Conti.News) following a successful ransomware attack. The previous day, an IP address that resolved to CS Energy’s VPN was observed communicating with IP 149.154.159[.]165, which at the time was suspected to be a Cobalt Strike command-and-control (C2) server.
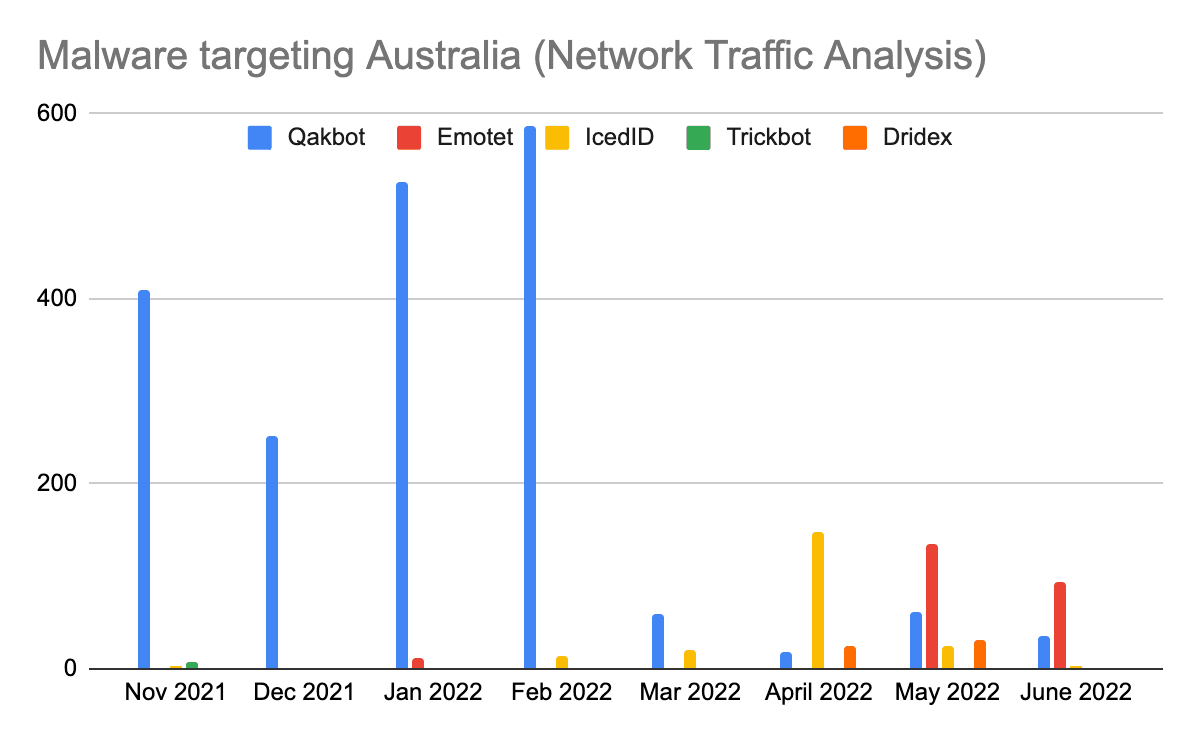 Figure 5: Malware targeting Australia (network traffic analysis) (Source: Recorded Future)
Figure 5: Malware targeting Australia (network traffic analysis) (Source: Recorded Future)
In malware events detected through NTA targeting Australia since November 2021, Qakbot has had an active campaign between November 2021 and February 2022, following a global disruption campaign. Recently, in May and June 2022, Emotet has been targeting Australia, following the reestablishment of its infrastructure after it was taken down by law enforcement in January 2021.
Outlook
This report on ransomware in Australia discussed the high-level trends over the last 18 months. These trends include the inclination to attack larger organizations, increasing technological sophistication, organizational specialization with RaaS becoming the de facto business model, multi-faceted extortion schemes, and increased internationalization. Amid these trends, the number of ransomware attacks in Australia increased between January 2021 and June 2022.
Based on previous trends, ransomware attacks will most likely continue to increase despite global efforts to disrupt ransomware gangs such as Egregor, REvil, and Darkside, and voluntary disbandments as in the case of Conti. As previous groups fall, other groups such as LockBit will rise to take their place and new groups like ALPHV will emerge.
Threat actors will continue to use IABs and precursor malware as they seek to gain new accesses and develop existing ones. One of the most effective methods for ransomware affiliates to gain initial access to a compromised network will continue to be through the use of an IAB on dark web and special-access forums. Once this access is gained, ransomware actors will use precursor malware for privilege escalation, lateral movement, and data exfiltration. The most effective way for organizations to mitigate against a ransomware attack is by identifying initial access sales or detecting malicious activity in their network.
Related