Tracking Ransomware Exploit Kits With Threat Intelligence
If you’re attending the O’Reilly Security Conference in New York this week, I’ll be presenting, along with my co-author Timothy Gallo, on November 2 at 11:20 AM ET.
The title of our talk is “How to Protect Your Organization Against Ransomware (While Ensuring No One Sends You a Christmas Card)” and ties to our upcoming book (published by O’Reilly) Ransomware: Defending Against Digital Extortion.
For those who aren’t attending the conference, below is a quick preview of the talk.
Building a Well-Trained Workforce
Ransomware is primarily delivered two ways: via email and via the web. Knowing this, there are a number of practical, though not always popular, steps that organizations can take to prevent most ransomware attacks.
Email attacks target weaknesses in the security awareness of users. The attackers from teams like those behind the Locky ransomware develop new lures and methods designed to get users to open attachments or click on scripts.
While better security monitoring at the edge can help to reduce those attacks, as can disabling macros in Microsoft Office documents and preventing script execution on workstations, the most effective prevention method is a well-trained workforce.
Making users aware of the dangers inherent in these attack vectors and keeping them up to date on changes in attack methods can significantly reduce these types of attacks.
For this type of security awareness training to be effective, it has to be ongoing. Delivering the message once a year that “attachments are bad” doesn’t help anyone learn or maintain awareness. Instead security messages should be delivered routinely and they should be actionable. For example, using Recorded Future threat intelligence, security teams can track down the latest lures used by ransomware spam campaigns and alert users to these lures.
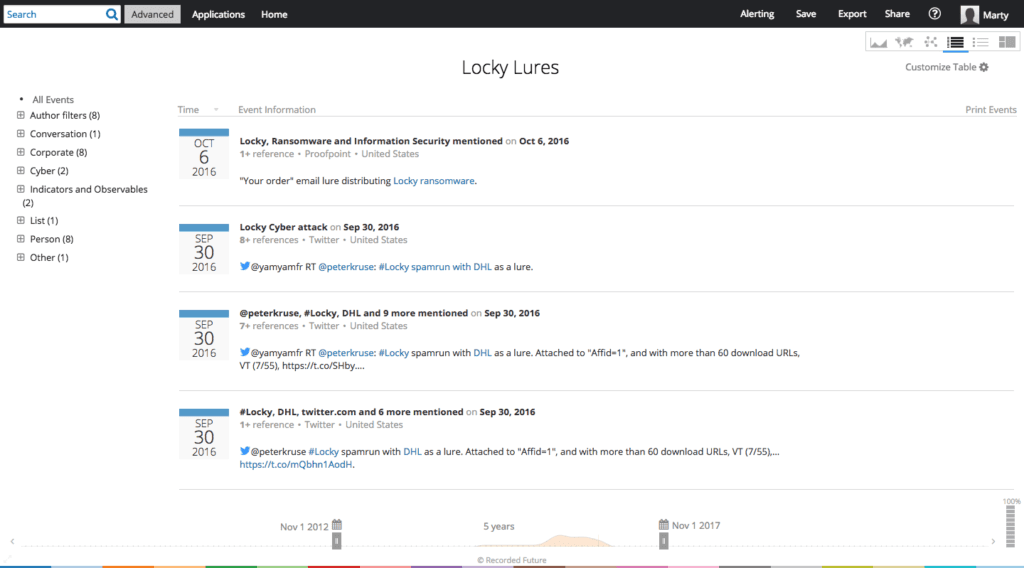
Table view monitoring real-time references to the latest Locky lures.
But, don’t just make it a passive email. Remind users to forward any emails that look suspicious that may have made it through the existing email security systems, so the security team can re-examine those systems (as always, remind users not to open any attachments before forwarding). Some security organizations even offer small prizes, such as T-shirts or Starbucks gifts cards, and acknowledgement to users that report a previously unseen spam campaign.
Tracking the Latest Exploit Kits
The other side of ransomware attacks are those that occur over the web. Ransomware families like Cerber and CrypXXX rely on exploit kits to deliver their payload and infect end users.
In these cases it’s up to the security team to track the latest exploit kits and ensure the organization is properly patched.
Again, Recorded Future threat intelligence can help security teams track the latest exploit kits and better understand adversary TTPs (tactics, techniques, and procedures) to ensure the organization has the right protections in place. Recorded Future maintains curated Intelligence Cards™ for a number of the most prominent exploit kits and can provide security teams with actionable information about those exploit kits and the methods they’re using to gain access to their victims.
For example, the Intelligence Card™ for the Magnitude Exploit Kit shows both the CVEs and the products that it’s currently exploiting; it also shows the ransomware families it has been associated with at one point or another.
By tracking the different exploit kits, security teams can work with IT or patch teams to help prioritize patching based on the threat posed by the vulnerabilities these exploit kits are targeting and the impact ransomware infections may have on the organization.
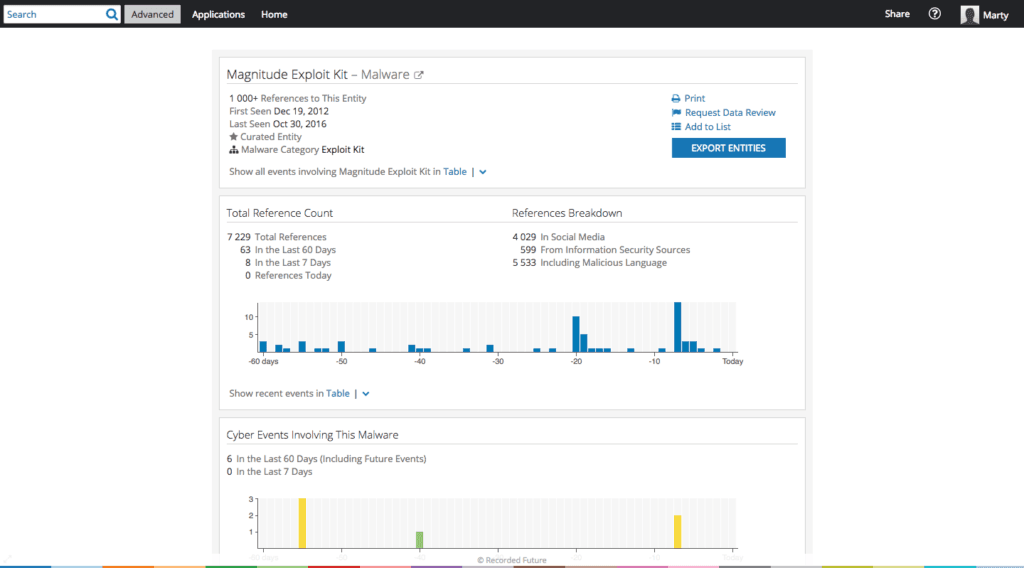
Intelligence Card™ for the Magnitude Exploit Kit.
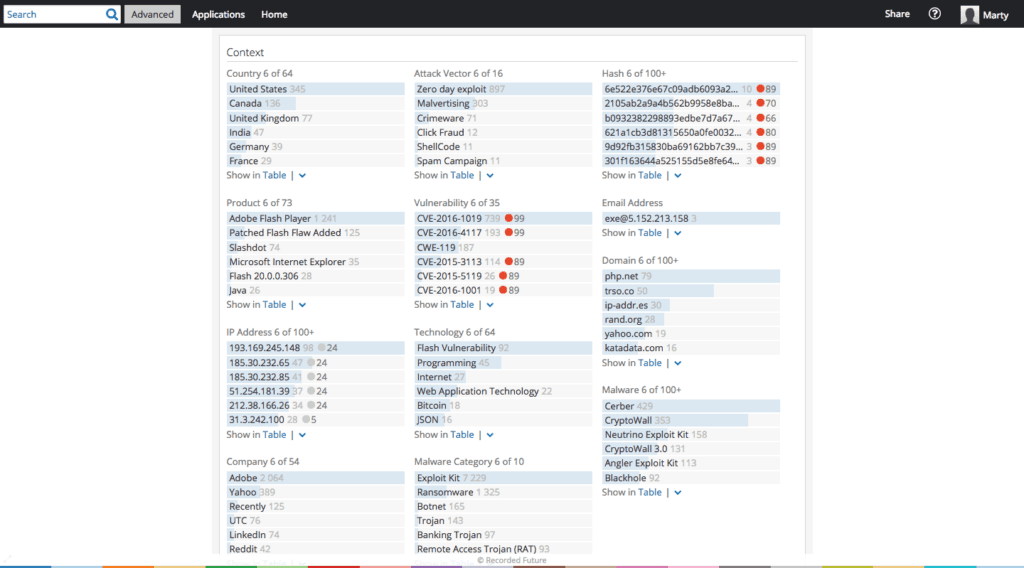
Additional threat context for the Magnitude Exploit Kit.
Get Cross-Organizational Buy-In
But there’s another aspect to this, and this is the part that often makes security teams unpopular. If an application is repeatedly being targeted by these exploit kits should it be allowed to run in the network?
Adobe Flash is the perfect example of this.
Over the last few years, dozens of Adobe Flash exploit kits have targeted dozens of vulnerabilities in Adobe Flash. It seems that every time Adobe patches one vulnerability the teams behind exploit kits start using a new one. The easy security answer to this problem is to disable or remove Adobe Flash across the network. That won’t go over well with the users in the network.
So, the better solution is to work with different groups inside the organization to understand their needs and, whenever possible, get their buy-in.
This way the security team can move from being the department of “no” to a more collaborative stance. Many teams in the organization will not have a business need for Adobe Flash, but others will. Understanding those needs and helping the teams either find alternative solutions or creating exceptions to the security policy for them means that users will be less likely to try to bypass the security policy, thereby putting the organization at great risk.
Threat intelligence can help security teams better justify their decisions, which makes them seem less arbitrary. Instead of saying, “Adobe Flash is a risk and it needs to be disabled,” security teams can now say that, “Adobe Flash has had 91 reported vulnerabilities in the last 90 days and there are currently 12 loaded into the RiG exploit kit.”
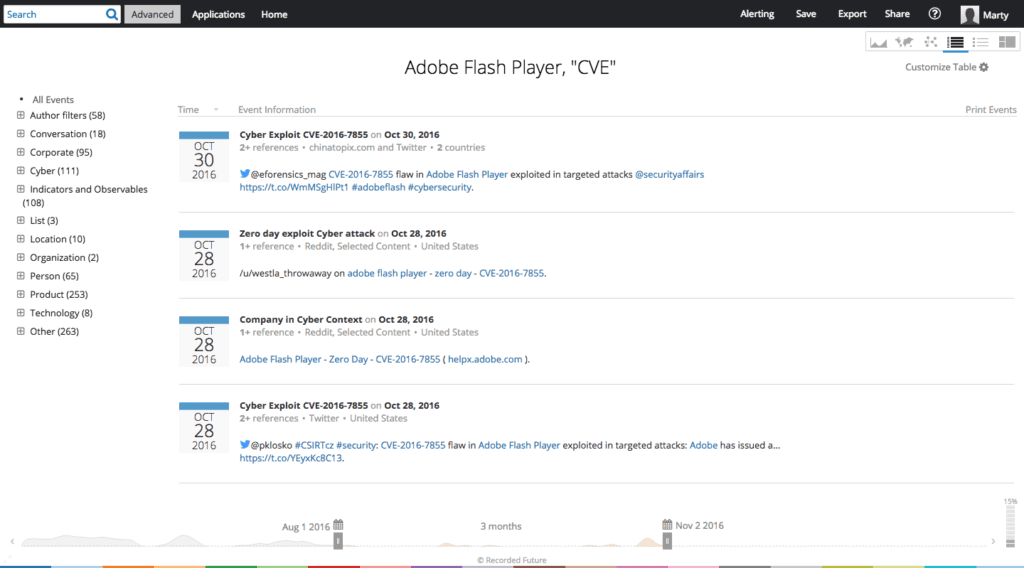
Table view showing a list of CVEs associated with Adobe Flash.
If you’re in New York the next few days, the O’Reilly Security Conference has a lot of great speakers and content. I highly recommend attending. If you do, please make sure you stop by and say hi!
Related
