Petya: The Sophisticated and Multi-Pronged Ransomware Attack
A new cyber attack that originated in the Ukraine and is quickly spreading throughout the world appears to be delivering ransomware and a trojan information stealer.
Petya has been around since early 2016 and is delivered primarily via phishing attacks. It is a particularly nasty piece of ransomware because it does not encrypt specific files; instead it overwrites the master boot record rendering the victim’s computer inoperable. We are still gathering information on this attack, but at first glance it appears to be very sophisticated and multi-pronged.
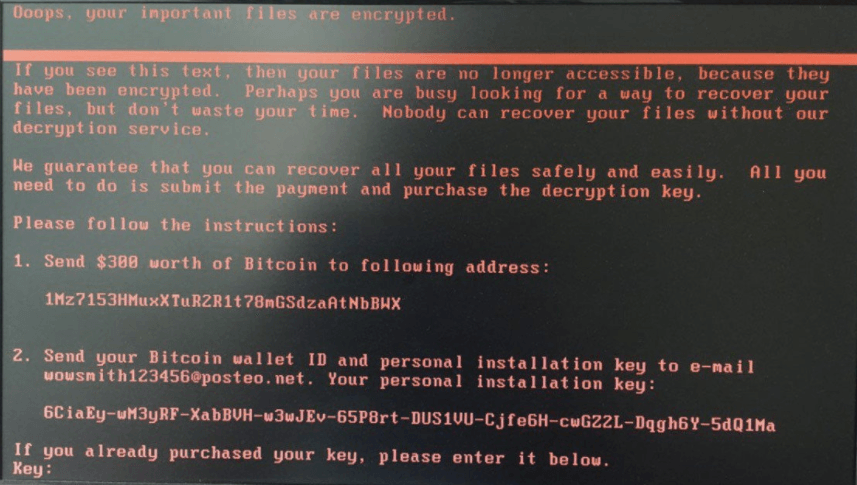
Ransom note on Petya-infected machine.
How Petya Spreads
According to reports, the initial delivery method was via phishing but it is very quickly spreading through networks, most likely using the same EternalBlue exploit that WannaCry used last month. There appear to be two payloads associated with the attack: the Petya ransomware and a trojan information stealer (early reports list this as Loki Bot, but we have not confirmed that). The Loki Bot information stealer grabs usernames and passwords from victim computers and sends the data to a command-and-control server controlled by the attacker. If confirmed, that would mean that while the computer is completely inoperable because of the Petya ransomware, the attackers have full access to the usernames and passwords stolen from the computer.
This attack is spreading quickly — initially targeting the Ukraine, but there have already been reports of attacks in Spain, France, India, and the United States.
The Petya ransomware appears to be taking advantage of unpatched systems that are still vulnerable to the EternalBlue exploit. This has allowed the worm to spread through networks and jump across interconnected networks. There is also a backup mechanism for spreading within the network. The code calls the WMIC (Windows Management Instrumentation Command-line) executable for lateral movement. WMIC is a command-line tool that is used to execute system management commands on Windows systems. Using WMIC requires a username and password, but because the payload includes an information stealer, the attackers may be able to scrape usernames and passwords from the victim machine and use those credentials to jump from one box to the next, even boxes that are patched against the EternalBlue exploit.
There have also been a number of payments made to the BitCoin wallet already. It appears the attackers are charging the same $300 ransom that the WannaCry attackers charged. We are tracking the transactions.
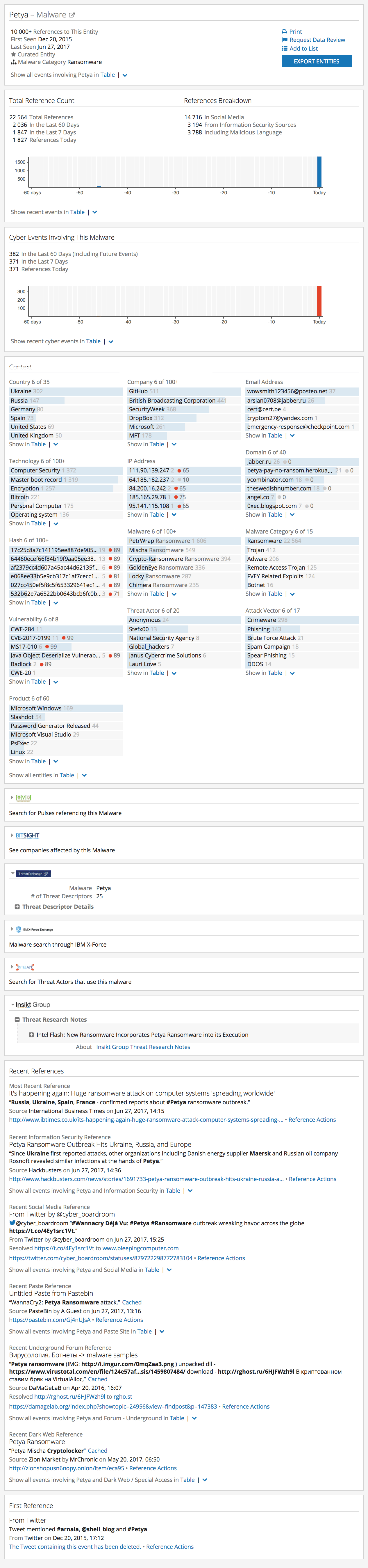
The Petya Intelligence Card™ on Recorded Future.
Fortunately, as with WannaCry, the team behind this attack has so far used a single Bitcoin wallet. This makes it easy to track ransom payments and will make it difficult for the attackers to remove funds from their Bitcoin wallet without coming to the attention of authorities. There is some discussion that the tool is built in such a way that the attackers could swap out Bitcoin addresses, but at this point they have chosen not to do so.
The first samples of the new payload have been uploaded to VirusTotal.
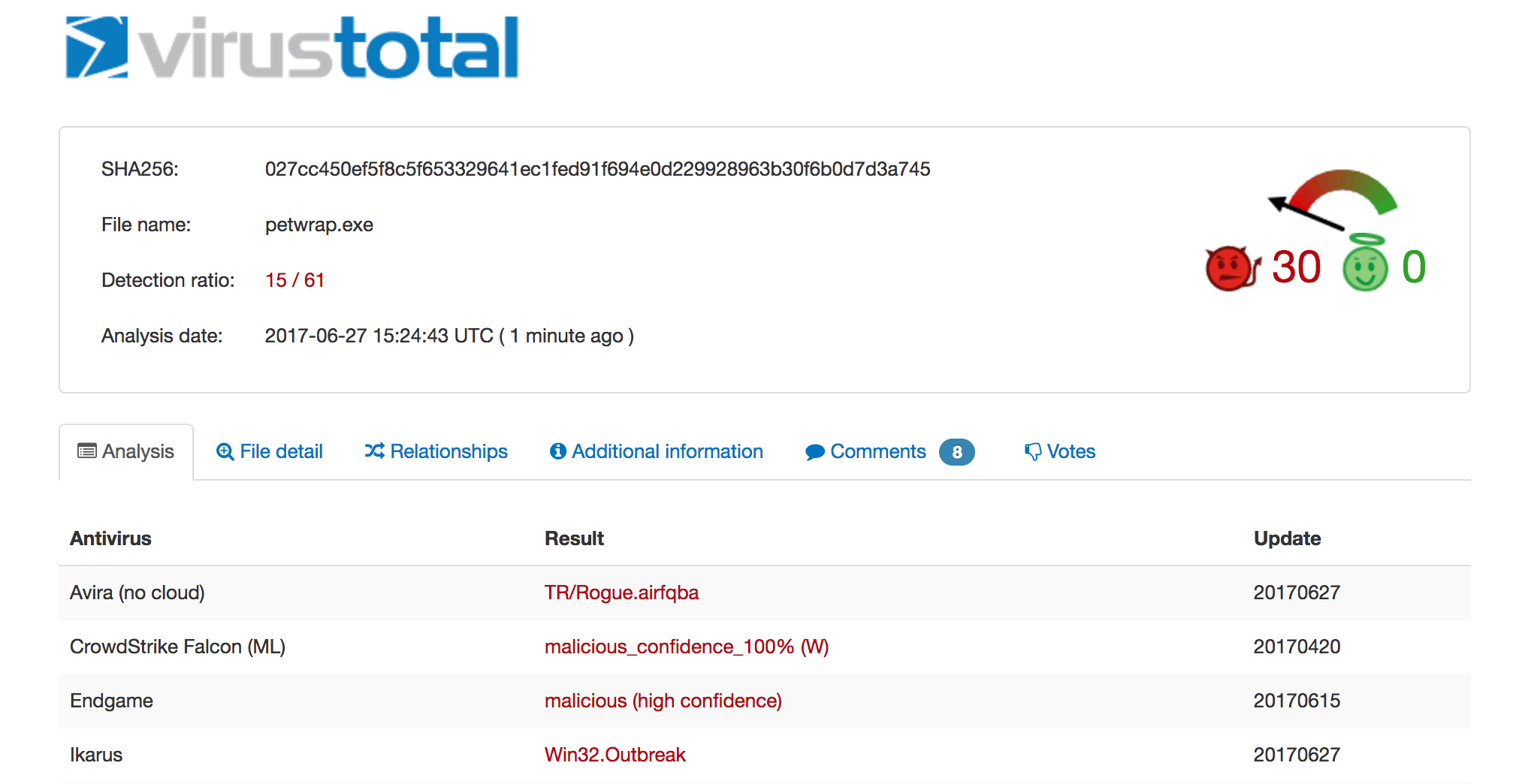
Petya payloads being tracked in VirusTotal.
Protecting Against This Attack
First and foremost, any organization that has not patched against Microsoft Security Bulletin MS17-010 please do so immediately. This may not stop the initial infection, but it will stop the attack from spreading across the network.
In addition, WMIC should be disabled across the organization — at least temporarily. After the initial rush of this attack, organizations can selectively re-enable WMIC, but it should only be enabled on system administrator’s boxes and any commands should be run from those boxes, rather than have them run locally using administrator’s credentials.
Finally, it is very important to quickly educate users about this attack, letting them know to be wary of suspicious emails and not to open any attachment that they do not trust.
Related
