Evidence: Emergency Patching Sways Community Sentiment

Yesterday, Microsoft announced MS14-021, addressing CVE-2014-1776 on many versions of Internet Explorer (IE) including Windows XP.
The patch was headline news even in business publications like the Chicago Tribune and drove a swift reversal in online sentiment.
Starting from zero-day, sentiment involving Microsoft and this vulnerability rapidly soured as reporting of the IE vulnerability gained traction. This timeline only visualizes reports published before the Microsoft patch announcement.
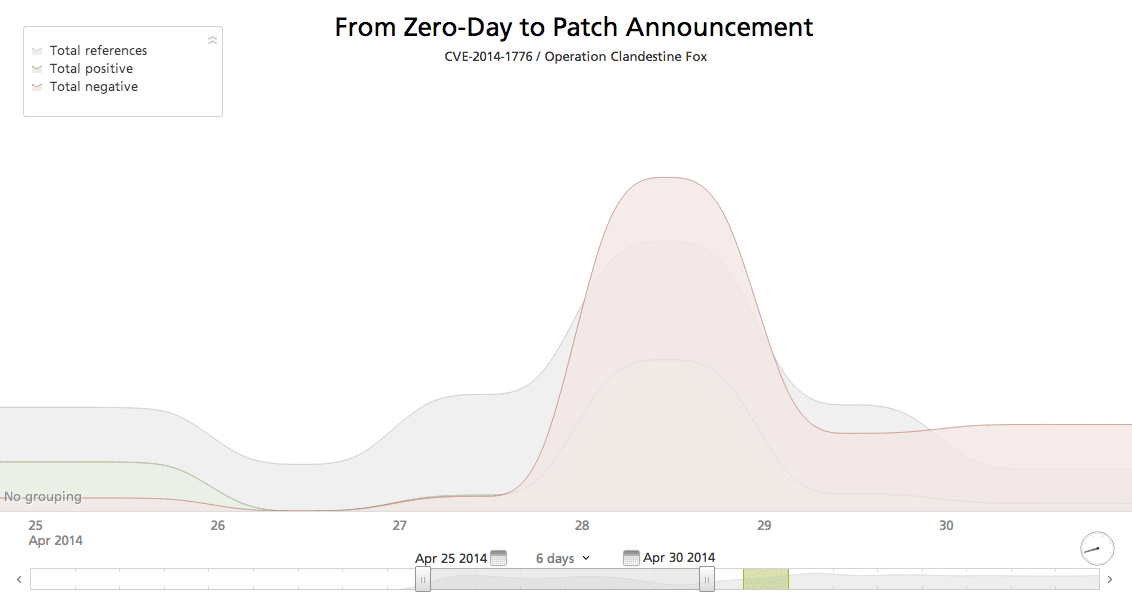
Click image for larger view
After the patch announcement, we observed a swift and significant positive impact on sentiment. This timeline includes forward looking references published on Thursday, May 1, the day MS14-021 was announced.
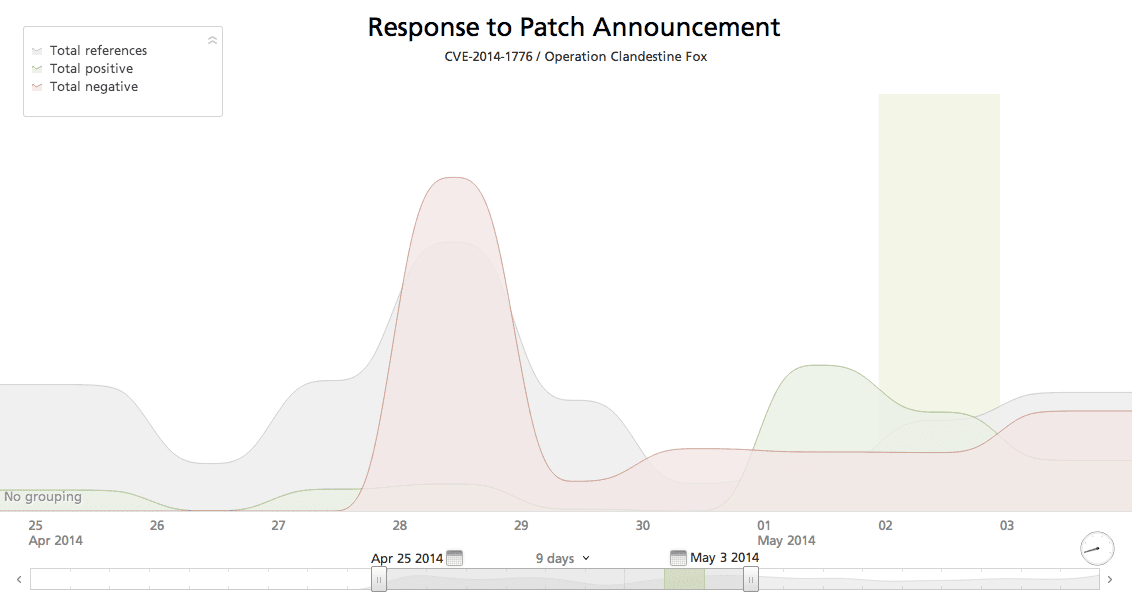
Click image for larger view
Also Noteworthy
Two detailed analyses of the exploit mechanism are published by HP Security Research and Sourcefire Vulnerability Research Team.
DHS CERT identifies spearphishing as the vector of the targeted attacks.
And, poor wording in our previous post suggested CVE-2014-1776 specifically increased risks to ATMs and other systems based on Windows XP, versus increased risks simply from XP end of support. But is targeting IE vulnerabilities in ATMs actually a valid risk, or just a paranoid fantasy? We enjoyed this tweet exchange.
Related