What’s in a Name? For Crimeware and DDoS Sellers, Everything!
Analysis Summary
- A recent OVERFLOW DDoS BOT Web advertisement serves as a good example for scalable threat assessment and prioritization workflow.
- Separating fact from fiction related to new crimeware legitimacy and capabilities is resource intensive.
- Quick summarization of a threat actor’s online moniker and contact detail history is a good starting point for effective analysis and crimeware verdict.
- The contact details — market@ghostmail.com, ICQ number 688122325, and Jabber address serviceactiv@exploit.im — constitute the fingerprints of an online reputation that informs the credibility of the product/service being advertised.
- Operational defenders will experience success in decreasing operational risk by hunting and prioritizing those threats with a higher likelihood of impacting the enterprise’s strategic assets.
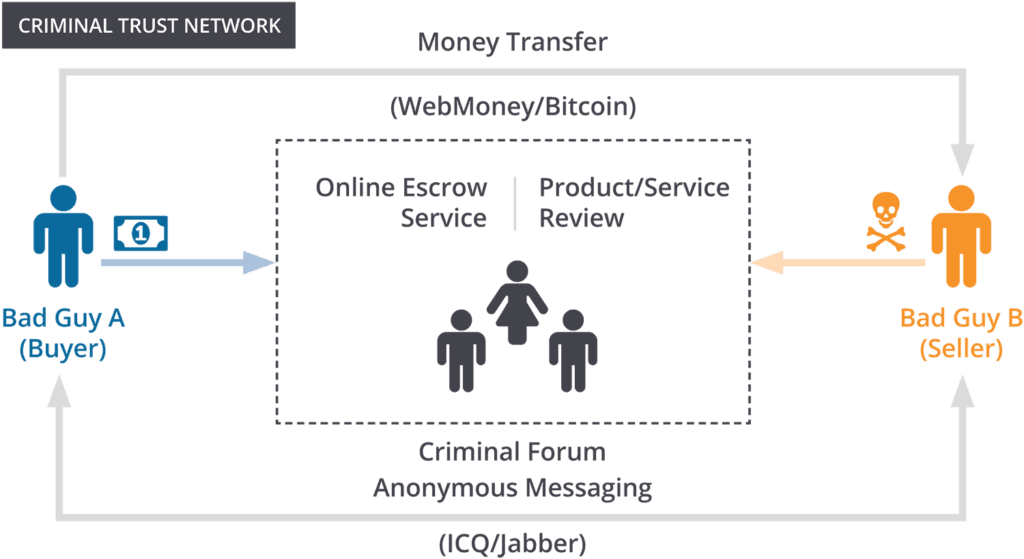
Trust is fragile on the Internet.
Bad guys leverage the Internet to ply their trade in relative anonymity, but that anonymity cuts both ways, and when it’s time to make a deal for illicit goods/services, the Internet can be a frustrating medium.
How can Bad Guy A trust Bad Guy B to deliver the agreed upon product/service following Bad Guy A’s payment? The historical reputation of Bad Guy B’s online username (moniker) is the primary mechanism for establishing trust and authenticity.

Alerting on New Bot
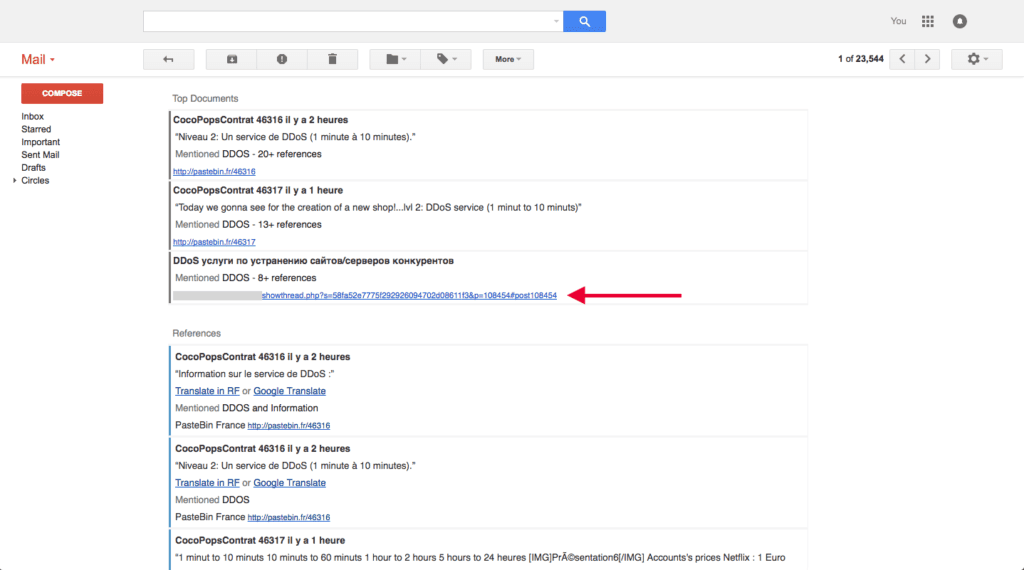
A prime example comes in the form of a recent Recorded Future alert on April 4, 2016 for the OVERFLOW BOT and distributed denial of service (DDoS) rental service.
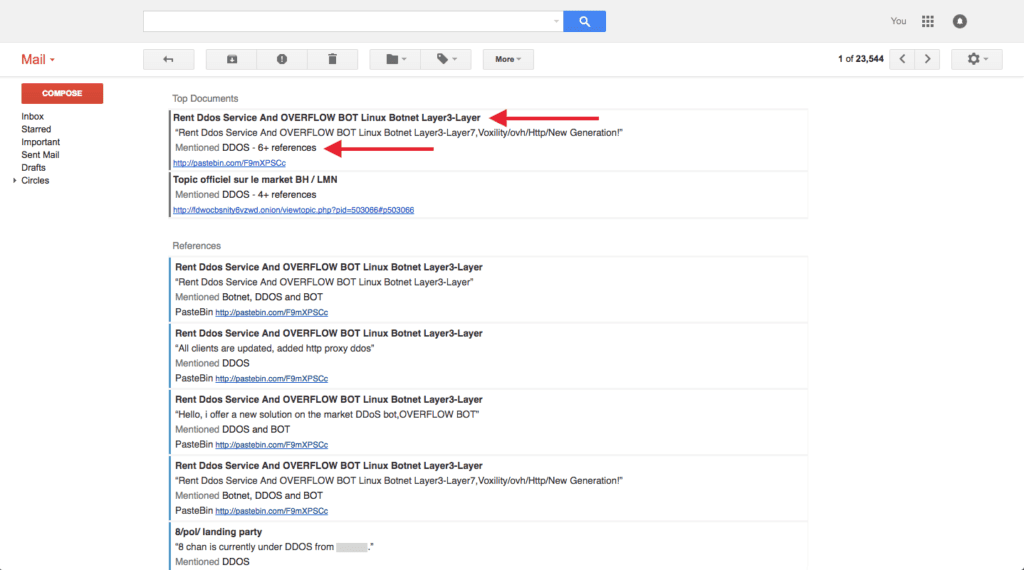
The alert references an identical Pastebin and Skidpaste advertisement (all Pastebin posts are cached in Recorded Future for historical viewing).
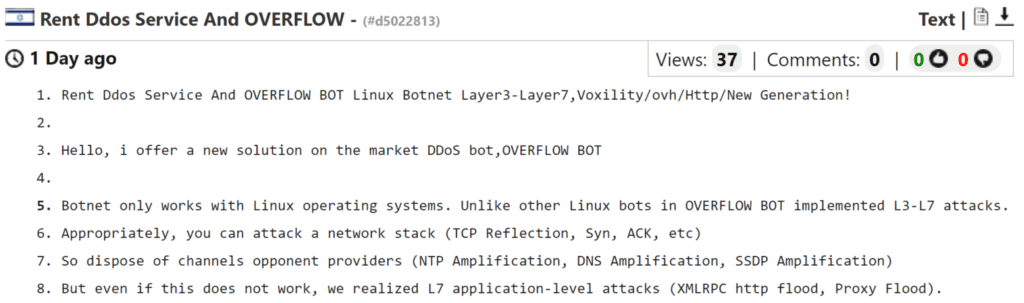
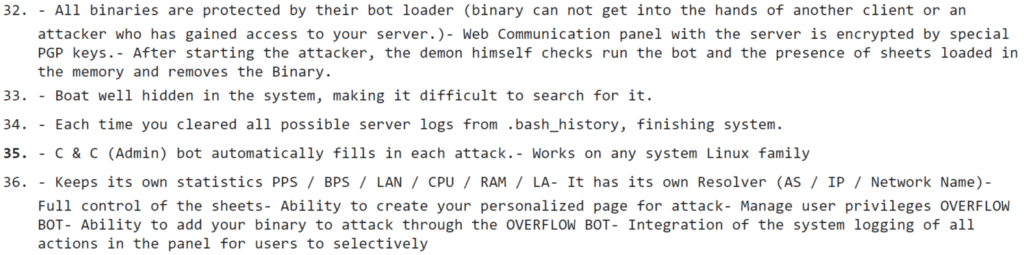
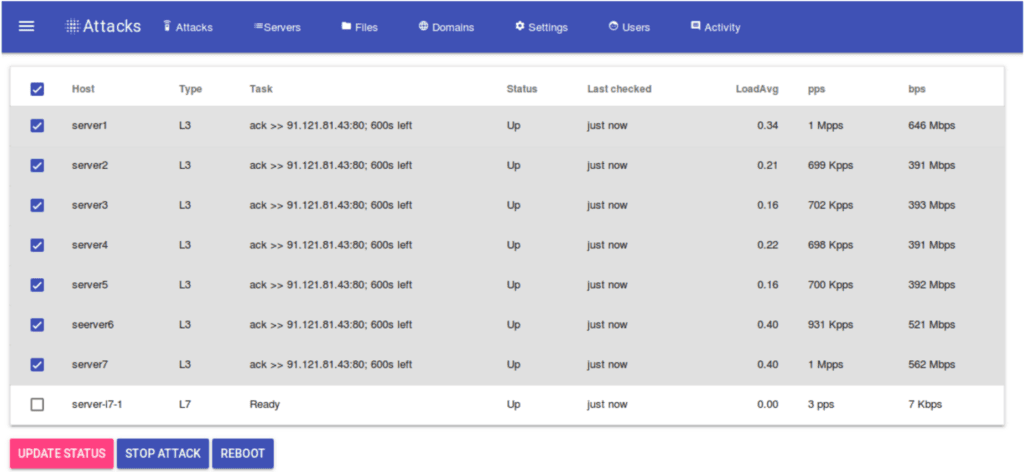
The OVERFLOW BOT represents a potential new legitimate threat to the enterprise, but operational defenders should assess the validity of the crimeware product before initiating subsequent plays in the playbook.
The most efficient method for assessing the advertisement is qualifying the threat actor. In this case, the contact details include email address market@ghostmail.com, ICQ number 688122325, and Jabber address serviceactiv@exploit.im.
A Recorded Future search for “serviceactiv” returns the first observed reference on March 28, 2016 with a following spike in activity beginning on April 4, 2016.
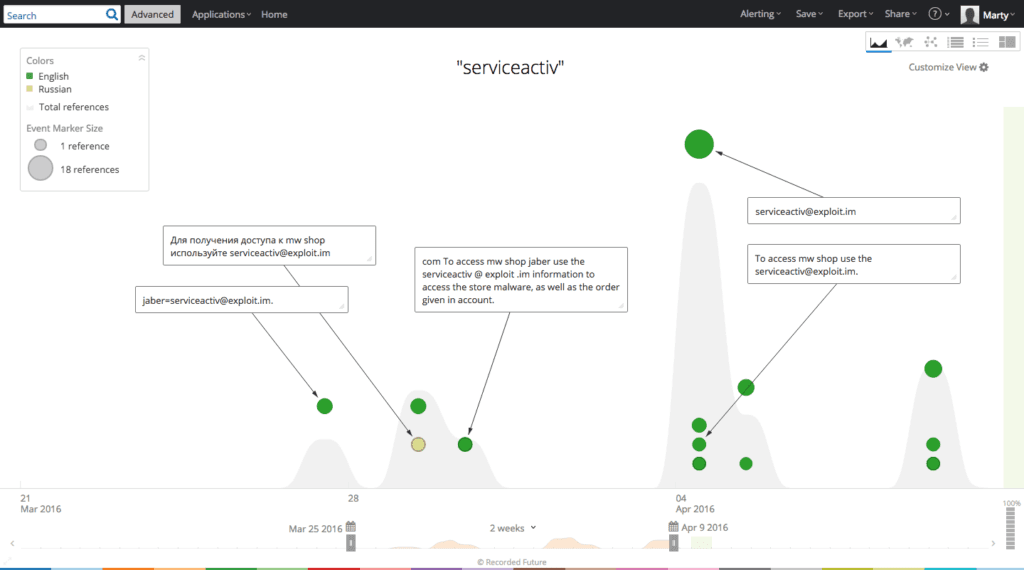
A Recorded Future search for “688122325” reveals a similar pattern.
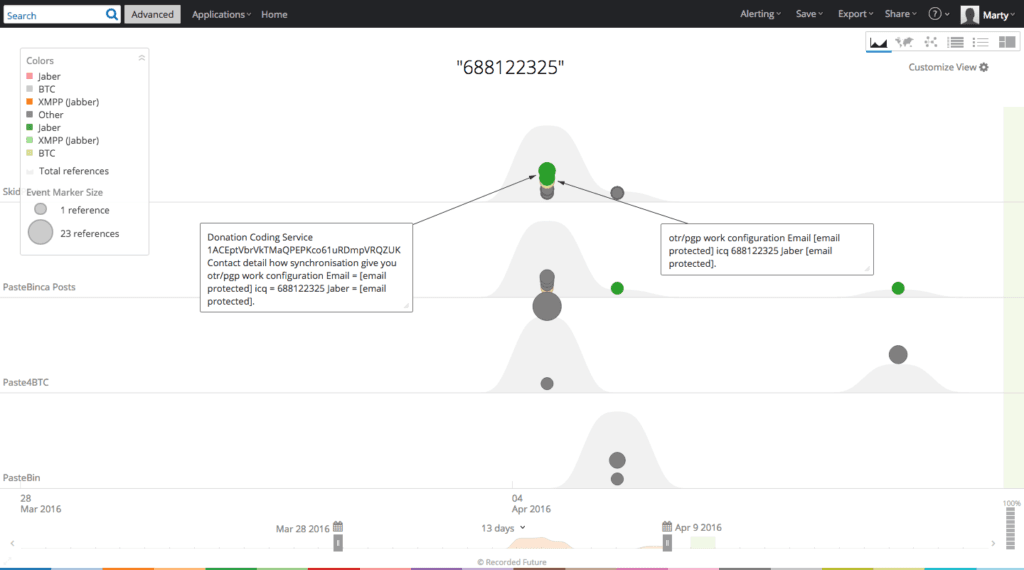
A more detailed Recorded Future view suggests that this particular threat actor persona is confined to paste sites and recently began increasing the volume of daily advertisements for an assortment of criminal services.
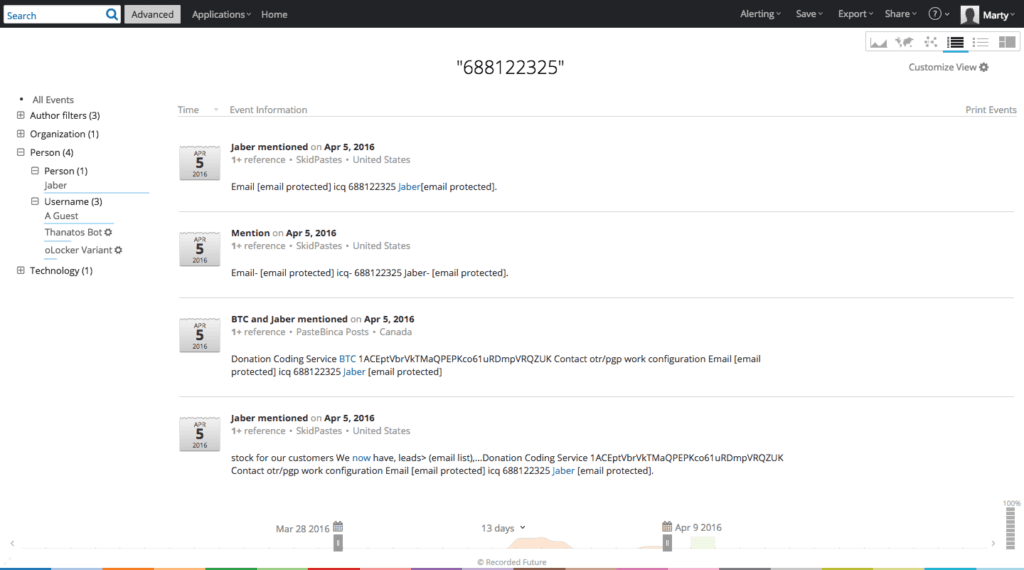
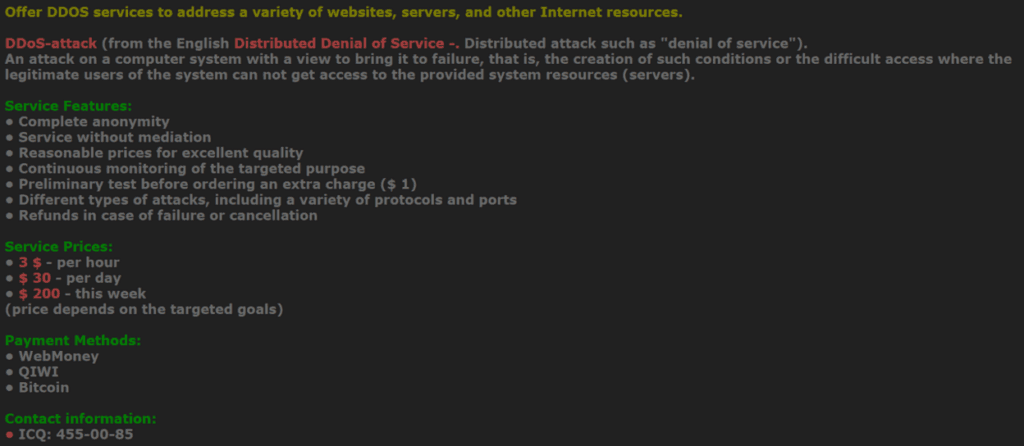
In addition to DDoS services, Serviceactiv is advertising bank accounts from Zeus and Kins, custom Android/Windows malware, email address lists, fully undetectable (FUD) crypting of binaries, victim remote desktop protocol (RDP) instances, and more.
At this point separating fact from fiction is difficult. The advertising is limited to paste sites versus criminal forums where other threat actors verify the veracity of products/services. In this case there is an absence of criminal feedback likely meaning that this individual is a “ripper” (an individual defrauding other criminals).
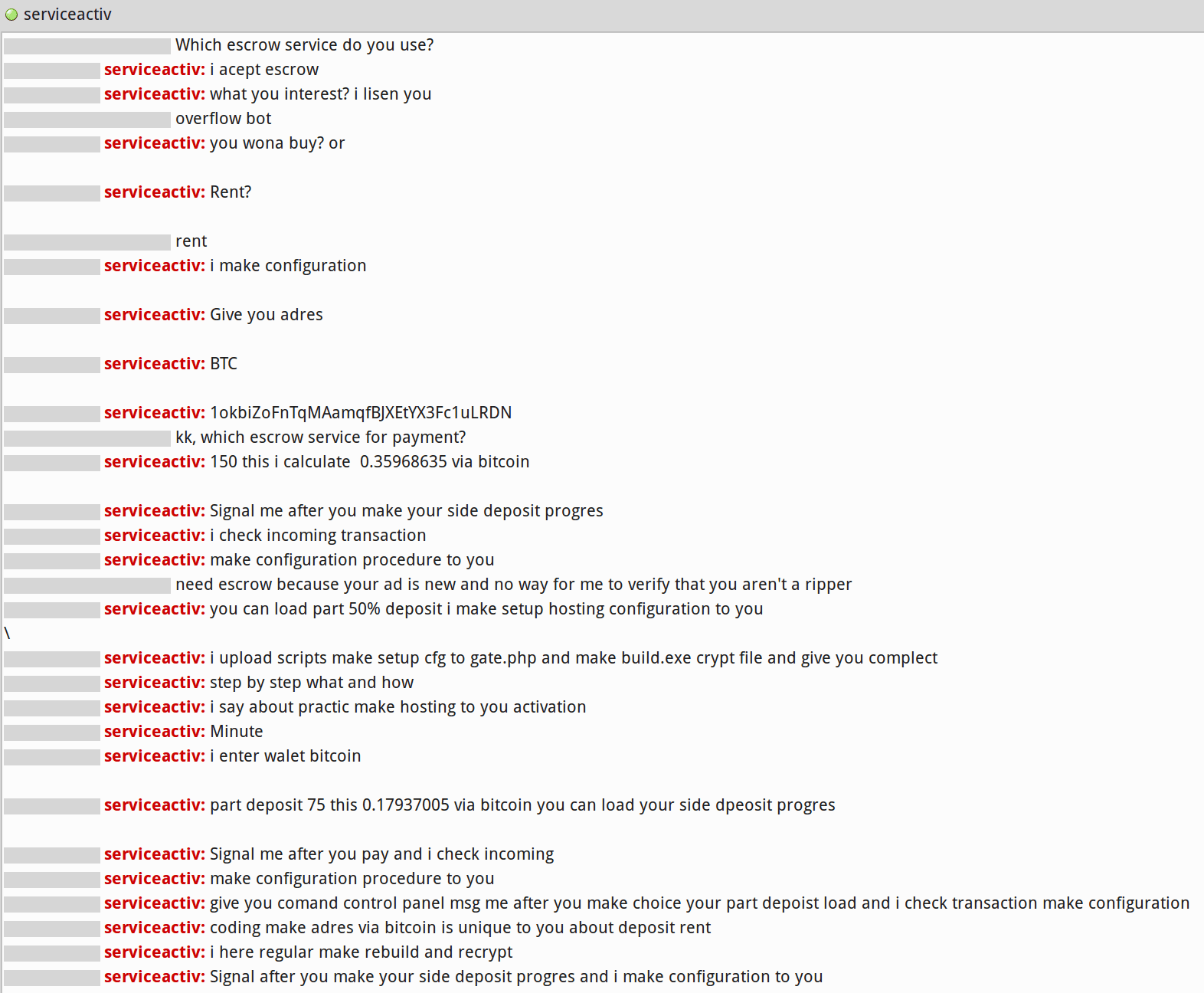
Direct contact with the threat actor may add an additional data point to the analysis.
In firsthand conversation (see below), Serviceactiv continually requests Bitcoin without providing an escrow service, and proactively continues the conversation without further counterparty reciprocation — increasing the odds that he/she is in fact a ripper.
Serviceactiv may change online monikers and contact details, but it’s difficult to bypass the verification mechanisms that the criminal community has put in place to establish trust between buyers and sellers. Advertising solely on paste sites is probably an attempt to short circuit the criminal feedback process, but it’s unlikely to result in serious revenues because discerning criminals will steer clear of the scam.
Traditionally, criminals advertise on forums, where, after testing a specific product or service, other forum members will vouch for validity.
Further, escrow services provide buyers confidence that e-currency funds won’t be released until the buyer confirms that the product/service was delivered in the pre-agreed manner specified.
If forum administrators game the system and abuse their constituents, the erosion of trust leads to the decline of the forum and everyone makes less ill-gotten gains.
Operational defenders can use the same criminal trust system to validate new crimeware and prioritize response efforts. An April 10, 2016 Recorded Future alert for the DDoS entity produced a forum discussion verifying a denial of service offering.
A forum vouch (or multiple vouches) for a criminal service does not guarantee that it’s legitimate, but it’s a data point potentially supporting further discovery and analysis.
Conclusion
Operational defenders must build a mature process for quickly identifying and assessing the legitimacy of new advertised threats at scale. A quick historical summarization of an actor’s online moniker is a good start.
In this case, the Recorded Future OVERFLOW BOT alert triggered additional analysis on the author. Serviceactiv is likely a ripper based on the totality of the evidence available, which by extension means that the OVERFLOW BOT isn’t a legitimate product. Therefore, no additional resources should be directed at assessing the potential impact.
OVERFLOW BOT may prove to be legitimate at some future point, but operational defenders are on solid footing with a detailed articulation of why the illegitimate verdict was made at the time of analysis. Threat centric operational defenders will experience continued success in decreasing operational risk by hunting and prioritizing those threats with a higher likelihood of impacting the enterprise’s strategic assets.
Related
