Tracking the Clandestine Fox
Analysis Summary
- FireEye Research Labs reports targeted attacks using a new IE zero-day against defense and financial services.
- Early details on malware in the wild and threat actor behind it are slight.
- FireEye links to Pirpi provide an interesting clue, while Websense analysis of IE crashes points in a different direction.
The Vulnerability: Internet Explorer CVE-2014-1776
Last Saturday, FireEye Research Labs flagged an Internet Explorer (IE) zero-day being actively exploited in targeted attacks. This Microsoft Internet Explorer vulnerability, CVE-2014-1776, broadly impacts IE versions from 6 through 11, and is trending strongly in open source.
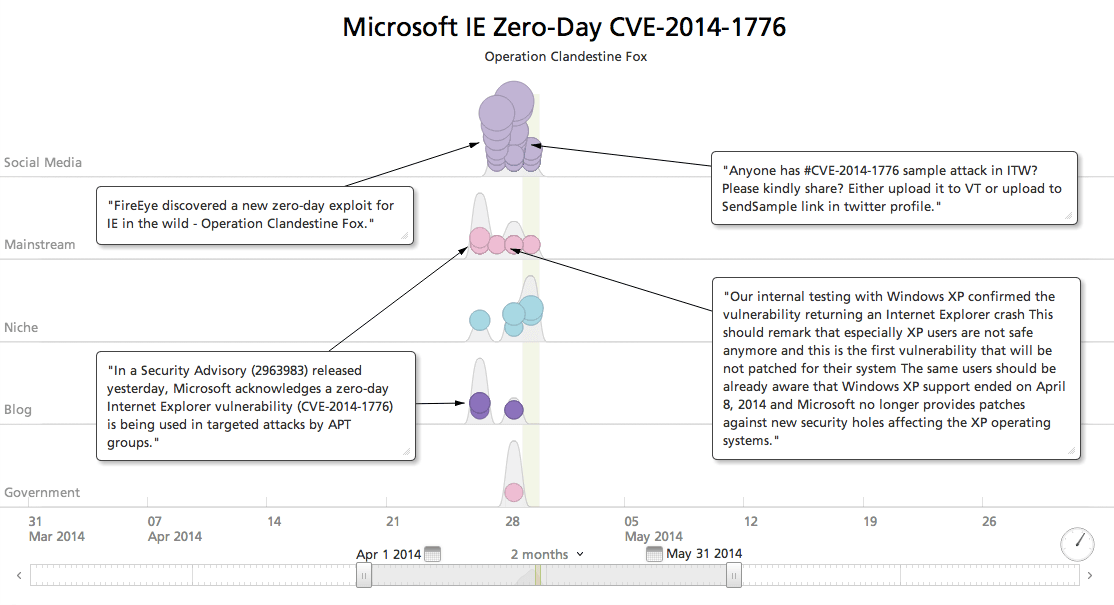
CVE-2014-1776 is the highest profile vulnerability yet to hit Windows XP, which recently passed out of support. This increases risks for home PCs, but more significantly for ATM systems and the like that are built on Windows XP. Workarounds for protecting XP are documented, such as deregistering the vulnerable DLL, but Microsoft will not ship a general availability patch.
The Campaign: Operation Clandestine Fox
After filtering out reports linking CVE-2014-1776 to Windows XP, we are watching the emerging discussion about Operation Clandestine Fox.
FireEye has so far said little, except that the targets are in defense and financial services. FireEye links the Operation Clandestine Fox threat actors to their 2010 research on the Pirpi malware. Pirpi exploited the same zero-day as Hupigon, with very similar GIF mechanisms. Very early reports of Hupigon identified China as possible country of origin.
Later malware detected as Hupigon (and variously cross-identified as GrayBird, Formador, Emogen, etc.) span the four years back to CVE-2010-3962 and before, with malware served from many other geographic locations. It seems unlikely the activity long after the Pirpi zero-day was exposed is indicative of the original cyber actors, especially as FireEye warns that these threat actors “are difficult to track, as they typically do not reuse command and control infrastructure.”
Websense Security Labs shares their analysis of IE crashes in VGX.DLL, the vulnerable library. Pending any conclusion these crashes do result from exploitation of CVE-2014-1776 in the wild, the data provides a lead for further investigation by identifying targeted geographic regions, and additional industry targeting: “Anomalous application crashes from VGX.DLL have been observed originating from the USA, UK, and Brazil. Specific industries with anomalous application crashes include telecommunications, tier-1 financial and municipal government.”
Related
