4 Ways Alert Logic Leverages Open Source Intelligence
Last week, we were thrilled to present a webinar featuring threat intelligence expert Stephen Coty. Stephen is the Chief Security Evangelist of Alert Logic, a well-known managed security service provider (MSSP). His presentation examined four ways Alert Logic leverages open source intelligence (OSINT) to improve the security of their clients. In case you missed it, here’s my recap.
1. Global and Industry Analysis
Alert Logic uses OSINT to increase awareness of the cyber threat landscape around their clients. This begins with the global threat landscape of threat actors, methods, attack targets, and operations. Recorded Future gives Alert Logic continually updated dashboards of threat entities that are trending in open source reporting.
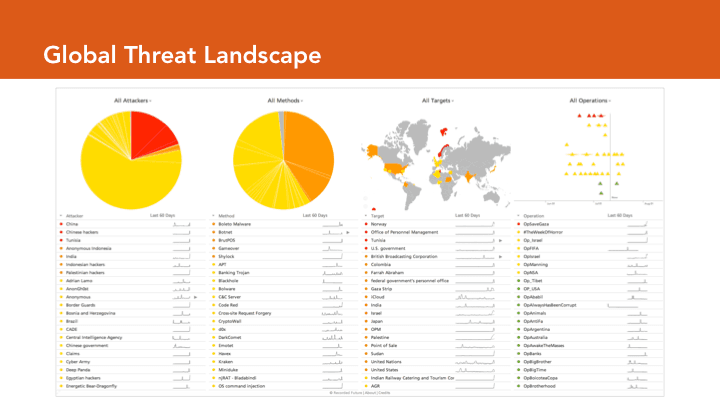
In addition to this baseline of global awareness, Alert Logic focuses on specific industry groups — top banks, for example — to detect threats and incidents at industry peers. This earlier detection gives Alert Logic a head start in defending their clients. OSINT further helps Alert Logic to assess industry-specific risks, where the considerations often cross boundaries between IT security and the physical world. Stephen used security incidents involving pipelines as an example, where IT security incidents are best understood in the larger context of geopolitical and kinetic events. Alert Logic uses OSINT to jump start their assessments of these very specific risks, and maintain awareness going forward.
2. Searching Current and Future Cyber Threats
Stephen highlighted the importance of tracking current cyber threats, and the threat actors behind them, before Alert Logic clients are targeted. Hacker teams improve their capabilities and change the targeting of their attacks, so a threat actor that seems less relevant today may be critical to understand tomorrow. The SEA is a high-profile example, having evolved from targeting media companies to ISPs, DNS providers, and other website services. OSINT gives Alert Logic effective tools to stay current, instead of playing catch up.

Stephen cautioned that OSINT alone is an incomplete picture. For example, a hacktivist operation may publicly announce the timing and target to drive recruitment, then move to private channels to communicate specifics. OSINT complements other collection approaches the Alert Logic team leverages in a back-and-forth pattern. Finds from public sources initiate investigations on other channels. Later, open sources can enrich and add context around individuals, attack vectors, infrastructure, etc. identified using other approaches.
- Mining for Lost and Stolen Data
Stephen observed public posts on data dump sites give a window into lost and stolen data. Although these advertisements don’t include full details, they can tip defenders to relevant breaches and credential dumps. As an example, a recent dump of credentials taken from Forbes primarily exposed customer accounts. Human nature ensures that some of these people have used predictably similar passwords on enterprise accounts, making these user accounts vulnerable to brute force attacks. Awareness of the specific accounts involved helps IT security teams detect suspicious login attempts or account access.
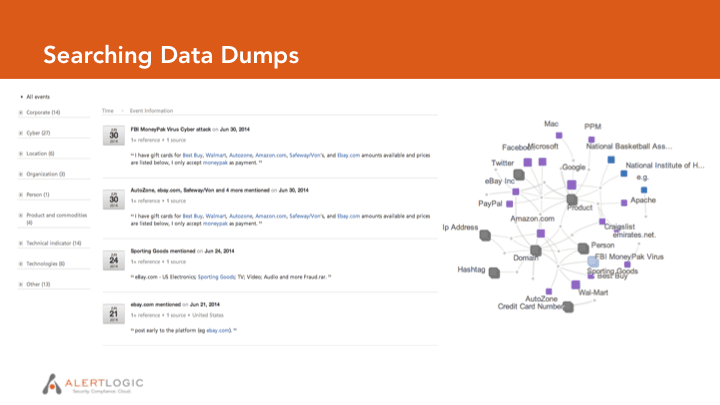
Upleveling from risks to specific client user accounts, Stephen pointed out the value of regular threat reporting about credential dumps and data leakage that is specific to each client’s industry and peer group. Defense in depth means deploying many security controls, and combating “security fatigue” around use of these controls. By highlighting incidents at comparable peer companies and which security controls are effective defenses against these incidents, Alert Logic gives their clients a fresh supply of data to reinforce the business case for IT security.
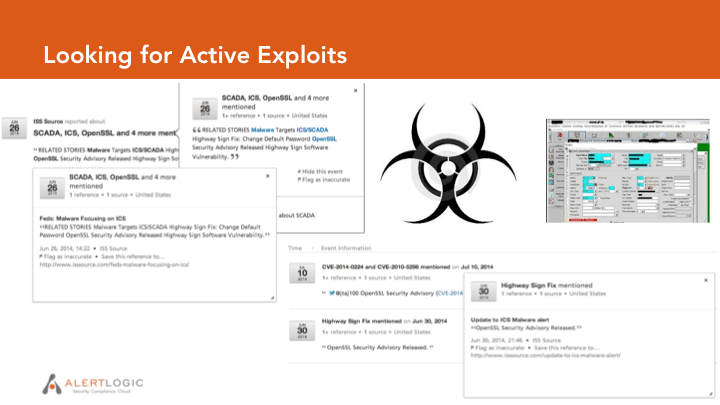
- Looking for the Latest Vulnerabilities and Exploits
There is obvious value in rapidly detecting new malcode and exploits, so the Alert Logic team can put effective detection and blocks in place. Open source is full of reports about announced vulnerabilities, of course. It’s also full of reports about exploits – proof of concept exploits, malcode in the wild, exploits advertised as integrated into exploit kits, reverse engineering deep dives, and reports of unidentified zero-day exploits. By capturing and analyzing this information in bulk, open source intelligence provides trend signals for high-risk vulnerabilities that deserve analyst attention — and a list of relevant documents as a springboard for that investigation.
This article was co-authored by Alert Logic Chief Security Evangelist Stephen Coty, and Recorded Future VP of Product Matt Kodama.
Related
