Mazar Android Bot: Threat or Not? Quick Threat Identification and Assessment Example

On Monday, November 16 we released a white paper detailing the facets of a world-class enterprise threat intelligence capability. Proper identification and analysis of a threat’s relevance to the business is the fundamental responsibility of fulfilling a mandate to reduce operational risk.
A timely example of one such threat appears on the web in a recent Russian language post (a cyber crime forum) advertising the Mazar Android bot.
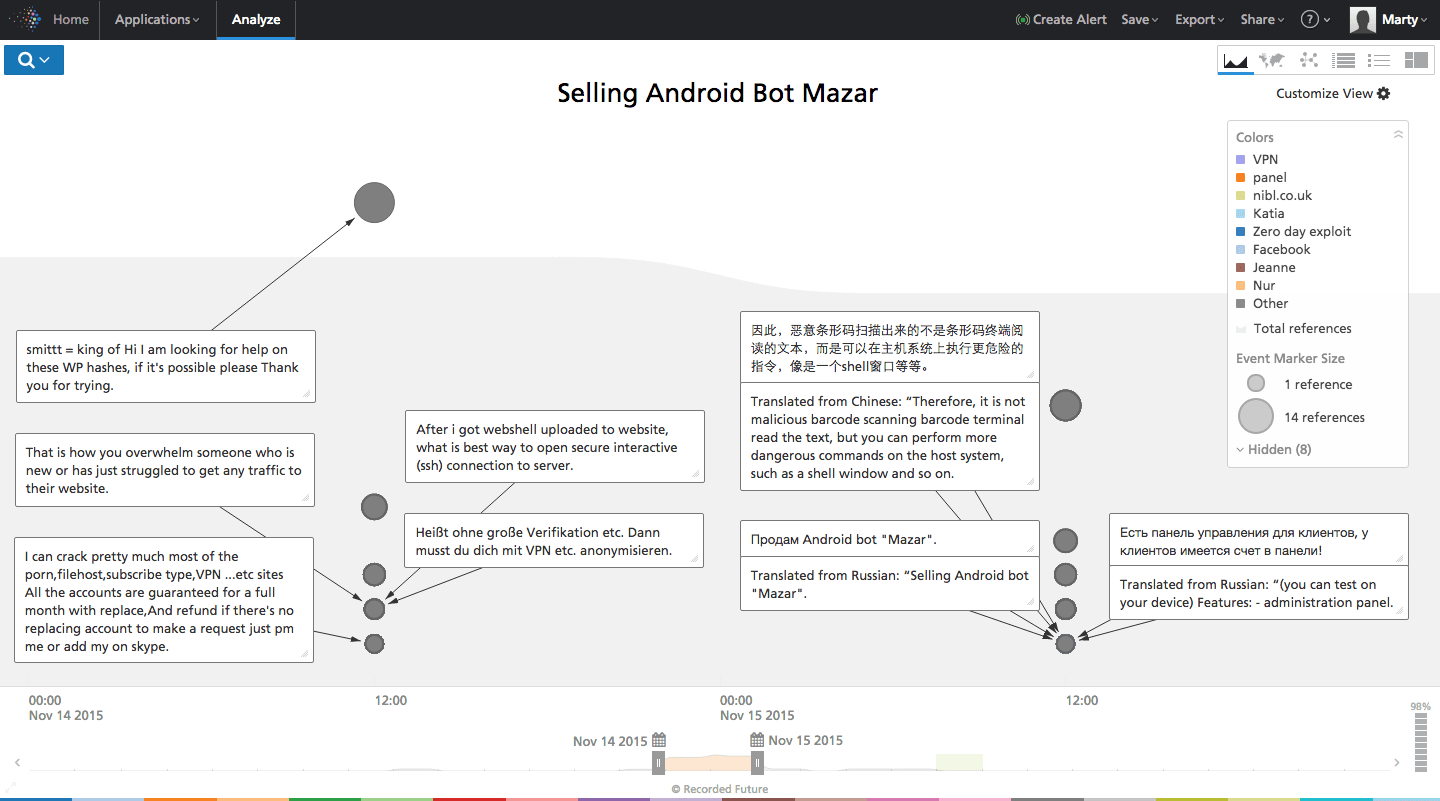
At first glance, this bot appears to intercept SMS messages on victims’ phones and specifically mentions Sberbank.
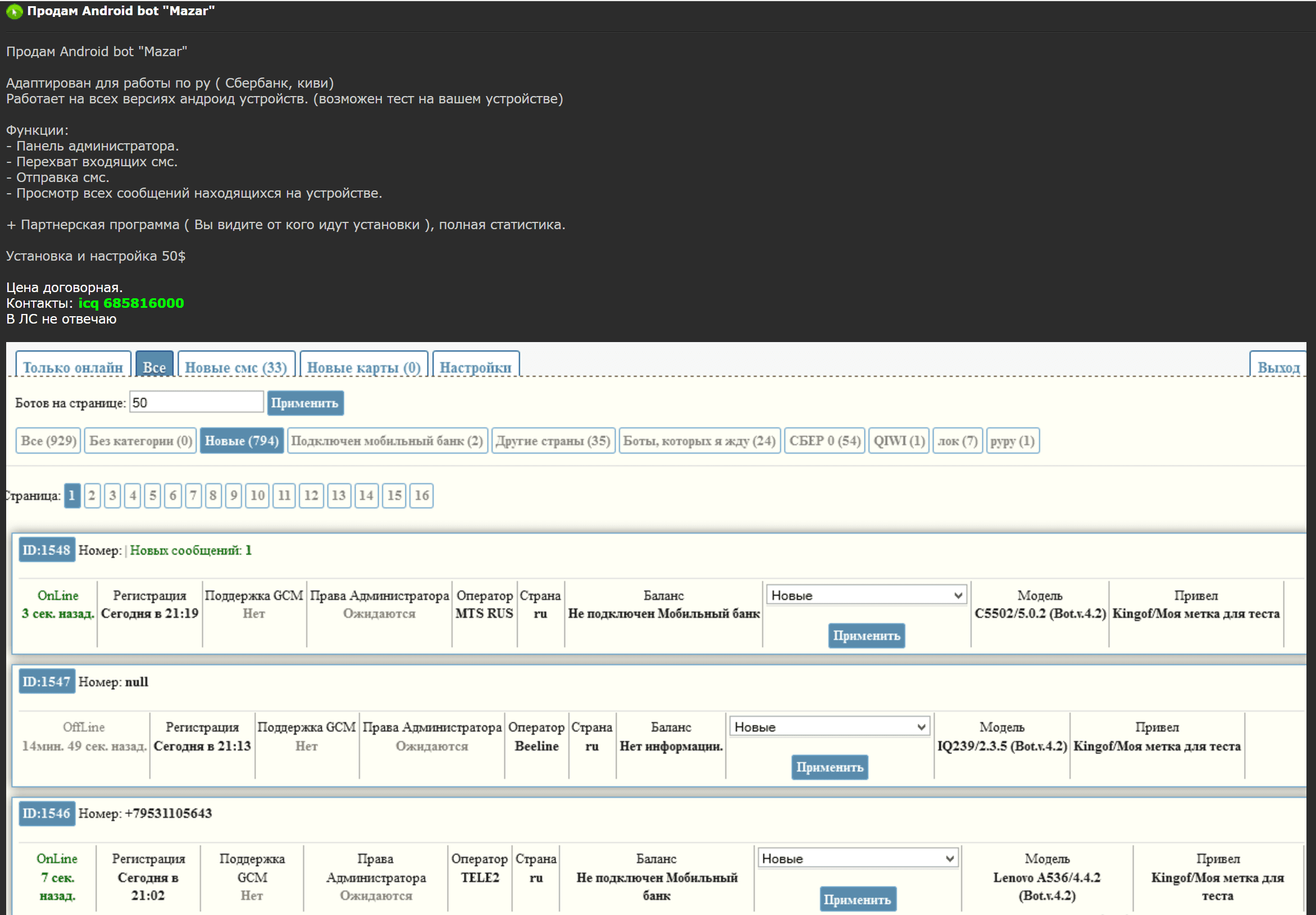
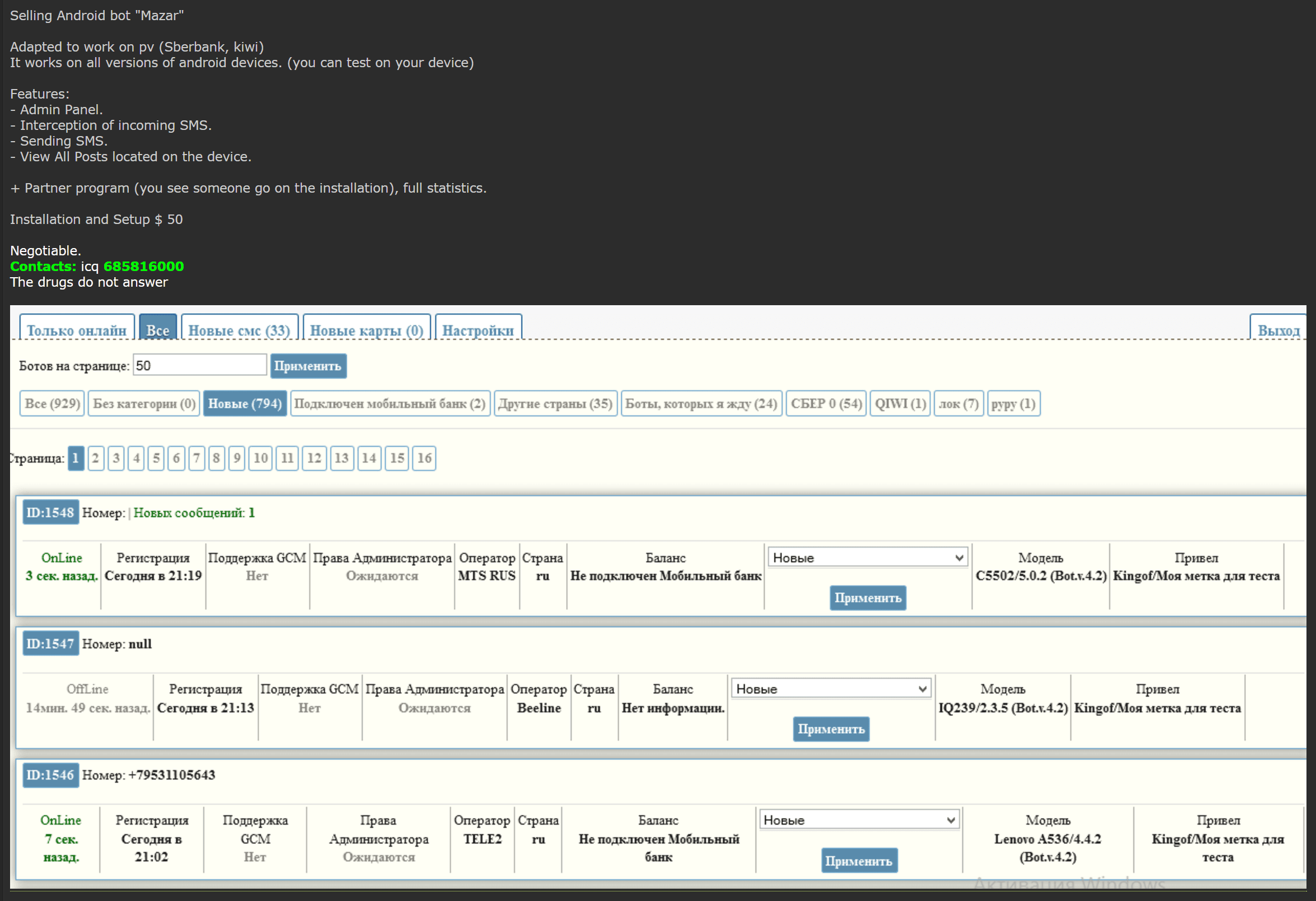
Mazar is a city in Northern Afghanistan and also a Muslim shrine. Beyond the meaning of “Mazar,” significant time is needed to understand if the forum post author is credible, and if the actual bot and/or control panel can be located “in the wild.”
Depending on the first round of answers, derivative questions crop up, such as, if this bot is in fact legitimate, will it affect our employees or customers? Will it affect competitors in our industry? Are there currently any customers reporting fraud that includes the mobile channel? If current fraud is absent, is this a threat that deserves broad business awareness?
Time is our most valuable asset and sometimes funds are the better trade-off to solve problems like the above when potential threats appear daily in a volume that few organizations can manage.
Related