Inside Malware Markets: Current Trends and Competitive Forces

Good leaders need a positive agenda, not just an agenda of dealing with crisis.- Michael Porter
Regardless of location, legitimacy, or legality, markets of all kinds act in accordance with a prevailing set of forces. Made famous by business management guru Michael Porter, his eponymous Five Forces generally dictate how markets will operate — that includes markets for malware.
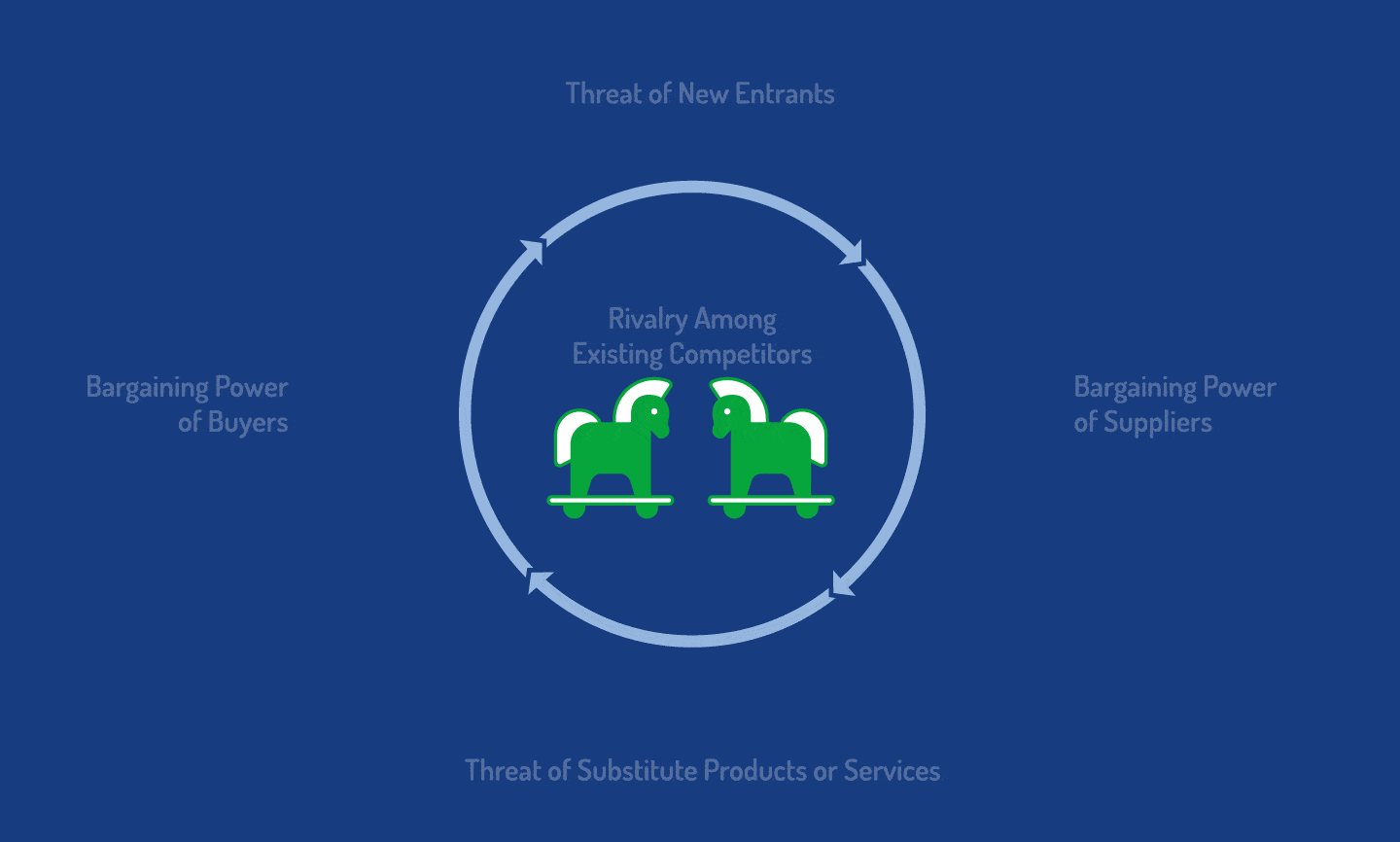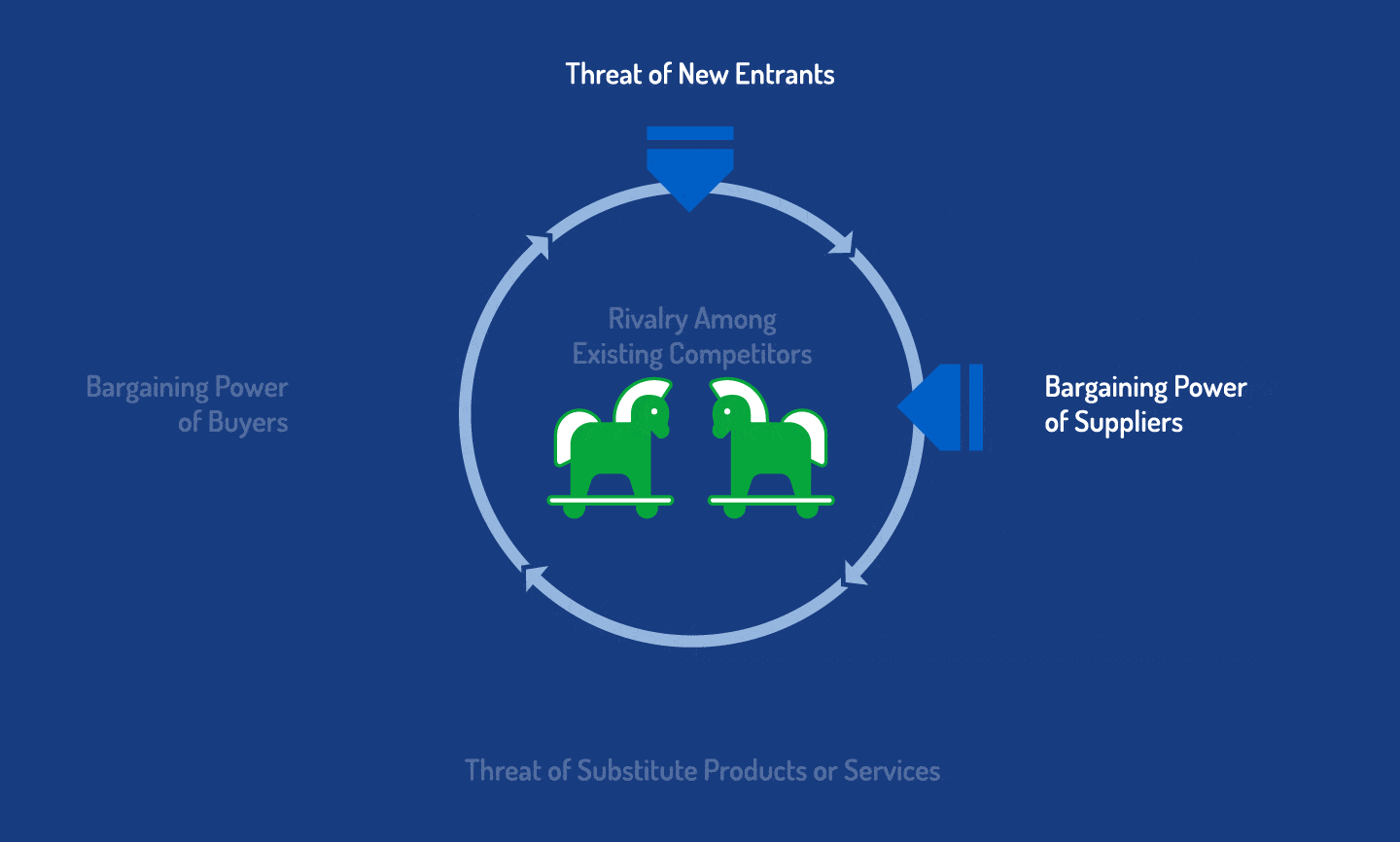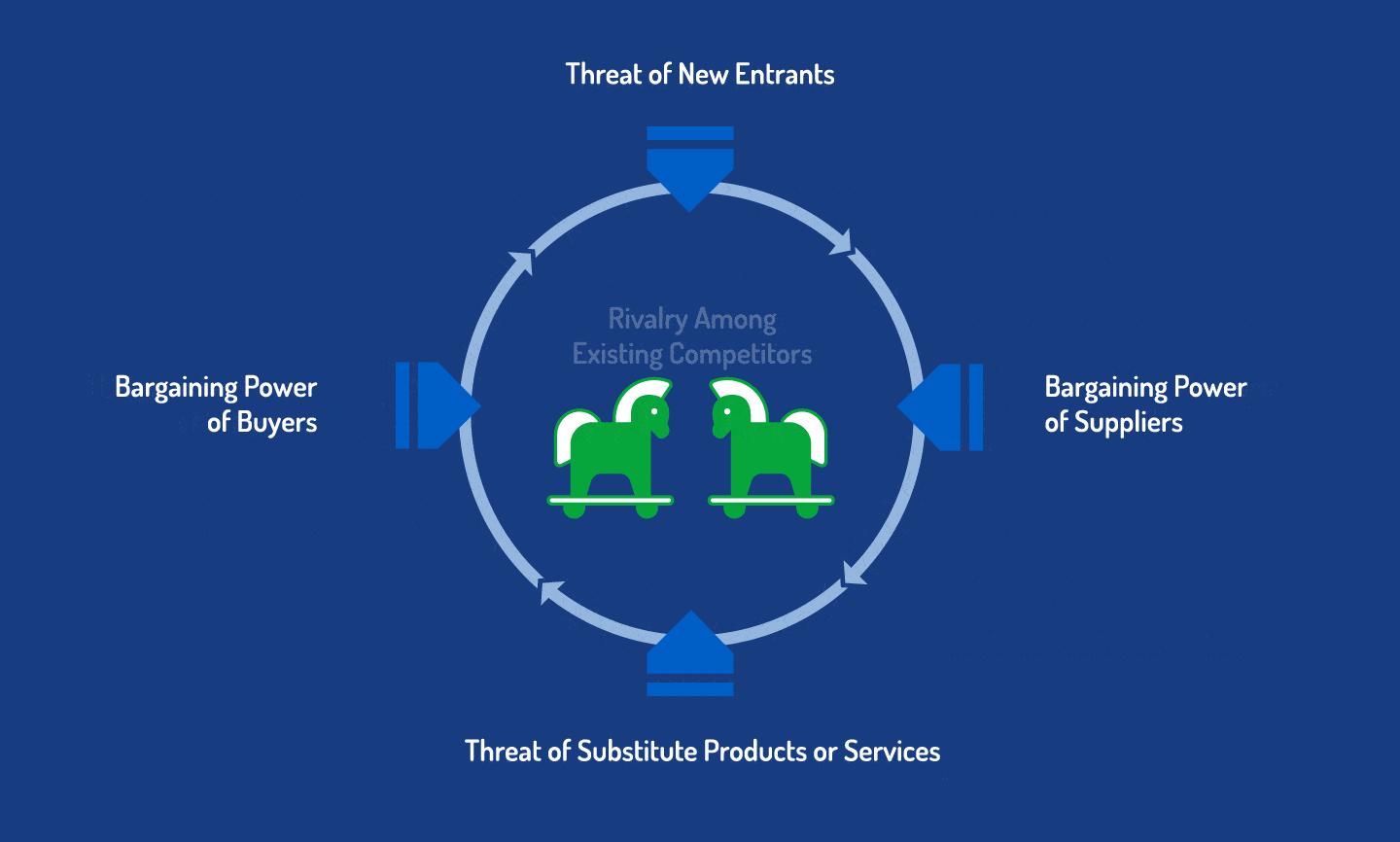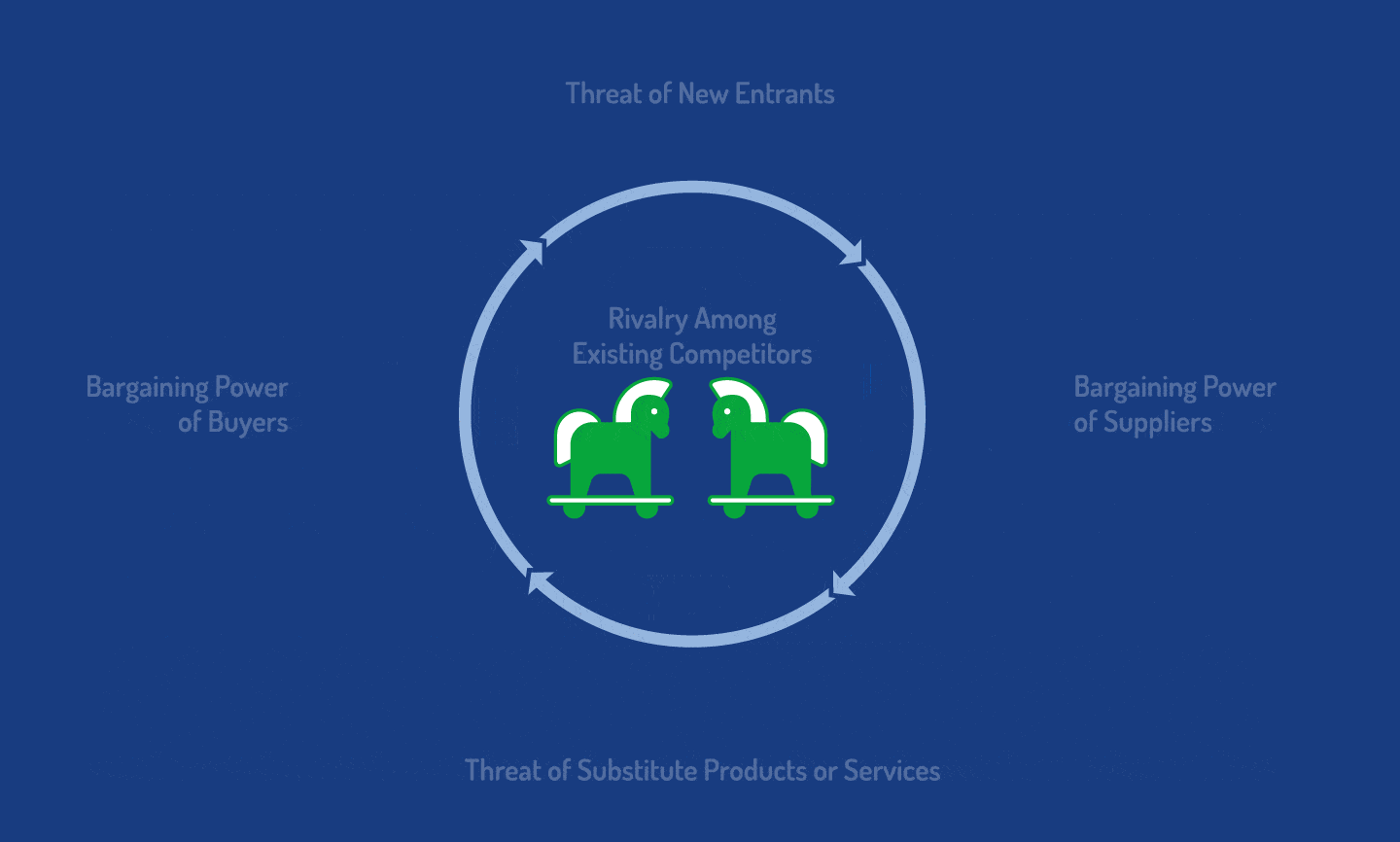
Porter’s Five Forces
- Rivalry Among Existing Competitors
- Bargaining Power of Suppliers
- Bargaining Power of Buyers
- Threat of Substitute Products or Services
- Threat of New Entrants
Throughout underground forums, there are buyers, suppliers, new entrants, substitutes, and rivalries, all dependent upon and responsive to varying degrees of bargaining power and threats.
Recent research1 by Recorded Future’s Insikt Group explored underground markets to find the world’s most popular malware variants.
The team began by defining malware as “operational pieces of code used to conduct illegal activity.” In order to rank and assess the most popular malware in underground forums spanning multiple families and languages, researchers analyzed nearly four million posts, identifying more than 100,000 variants of malware across 61 categories between May 2018 and May 2019.
What Insikt Group found was a bustling plaza where buyers and sellers interact much like they do in traditional markets. They introduce new products and features, use advertising best practices, and even provide customer service. Of course, there were a few peculiar aspects of in-demand products. For instance, the most popular malware tended to be openly available, dual-use, cracked, and open-source, rather than new or custom-built. Many instances were over three years old, indicating that a significant number of known vulnerabilities continue to go unaddressed — consignment shops have nothing on the levels to which malware vendors will go to market vintage items.

Peculiarities aside, evidence of the influence of Porter’s Five Forces can be found everywhere in underground marketplaces. With more than 100,000 variants spanning 61 categories, a significant challenge for any malware seller is how to deal with competition, especially with substitute products. Sellers primarily address this by packaging various tools in bundles, known as “malware collections.” A buyer waffling between two similar types of malware could choose one as a part of a collection and thereby acquire and test out other malware included in the bundle. This tactic works out well for buyers because market forces simultaneously drive down costs for concurrent acquisition. The same principle can be found in late-night infomercials in which jovial men shout, “But wait! There’s more!”
In malware markets, sellers went even further to challenge rivals. As new entrants came to peddle wares, their posts would be given precedence in forums. By advertising versions and offering updates to generate renewed interest, older sellers could edge out market entrants by reminding buyers they were not only popular, but new and improved! And just to cover their bases, malware sellers tested new markets, delivering advertisements to fresh forums, and going so far as to translate posts into other languages to reach prospective international customers.
It can be strange to think of participants in black markets as exhibiting the same fundamental behaviors as those on major online markets, classified ads, or even at the local grocery store. But in any central exchange, there will be buyers with a problem looking for a solution, and in doing so, generating demand. There will be sellers with a product they need to package and advertise. And market forces will dictate what is sold, where it is sold, and what the price will be.
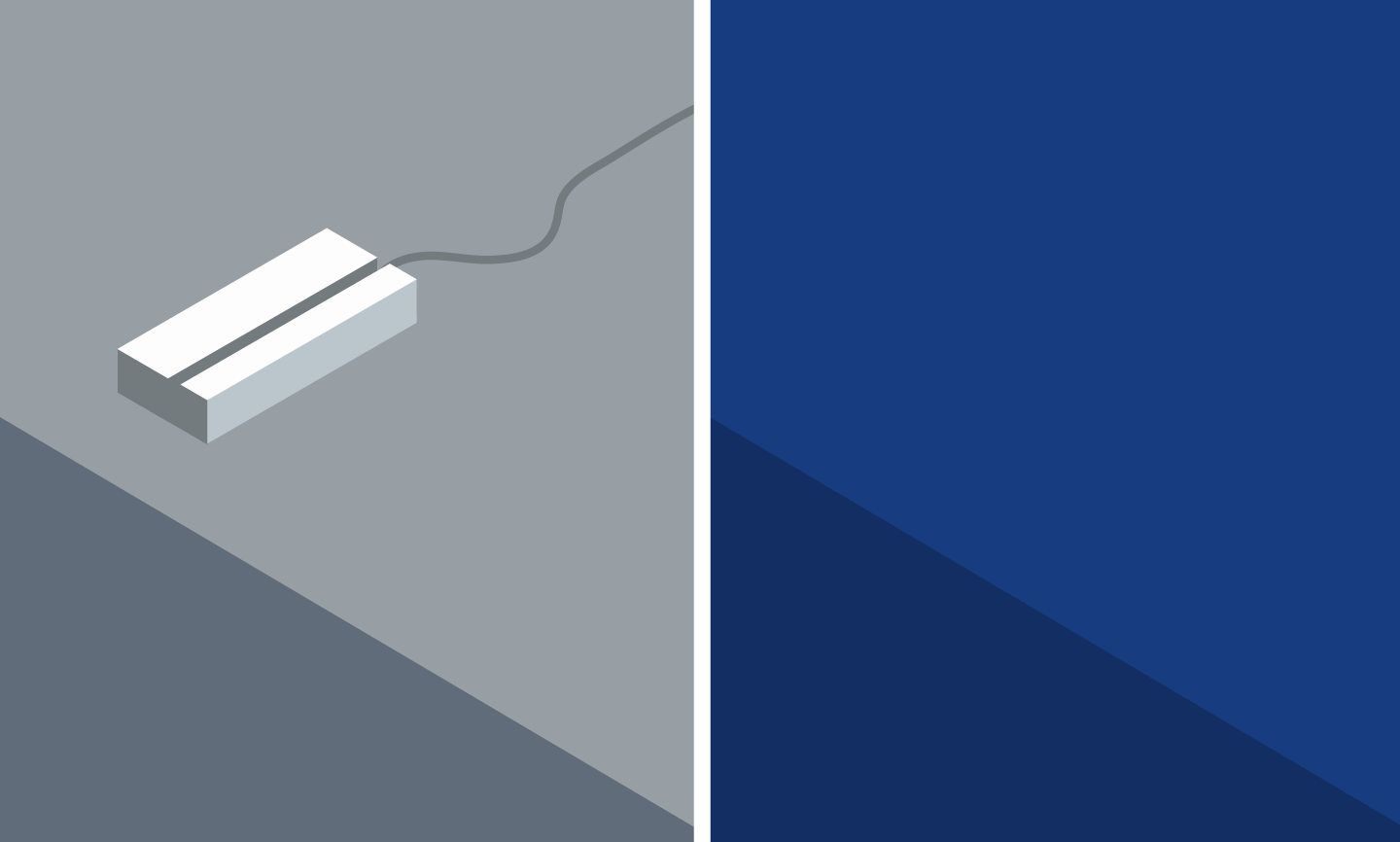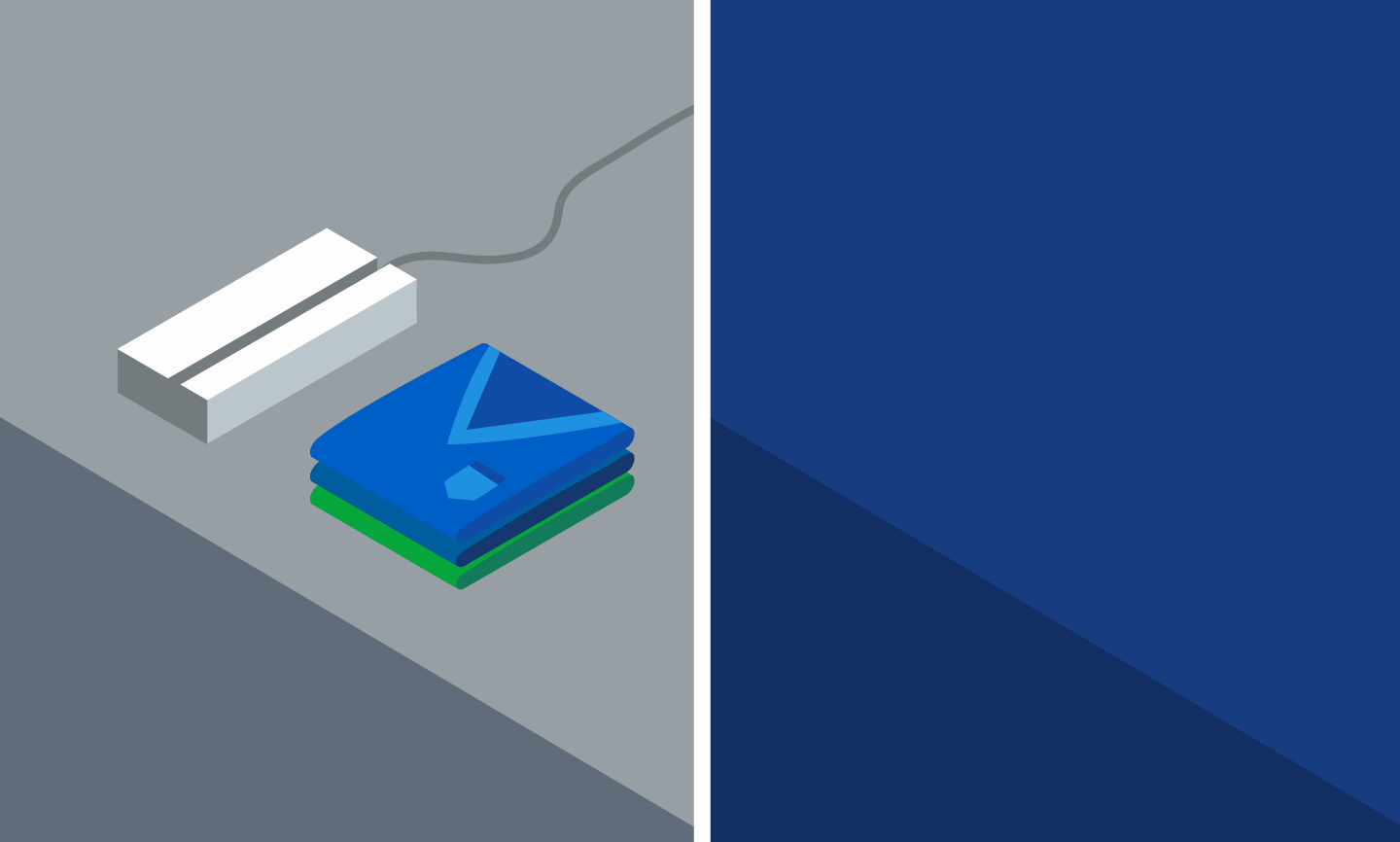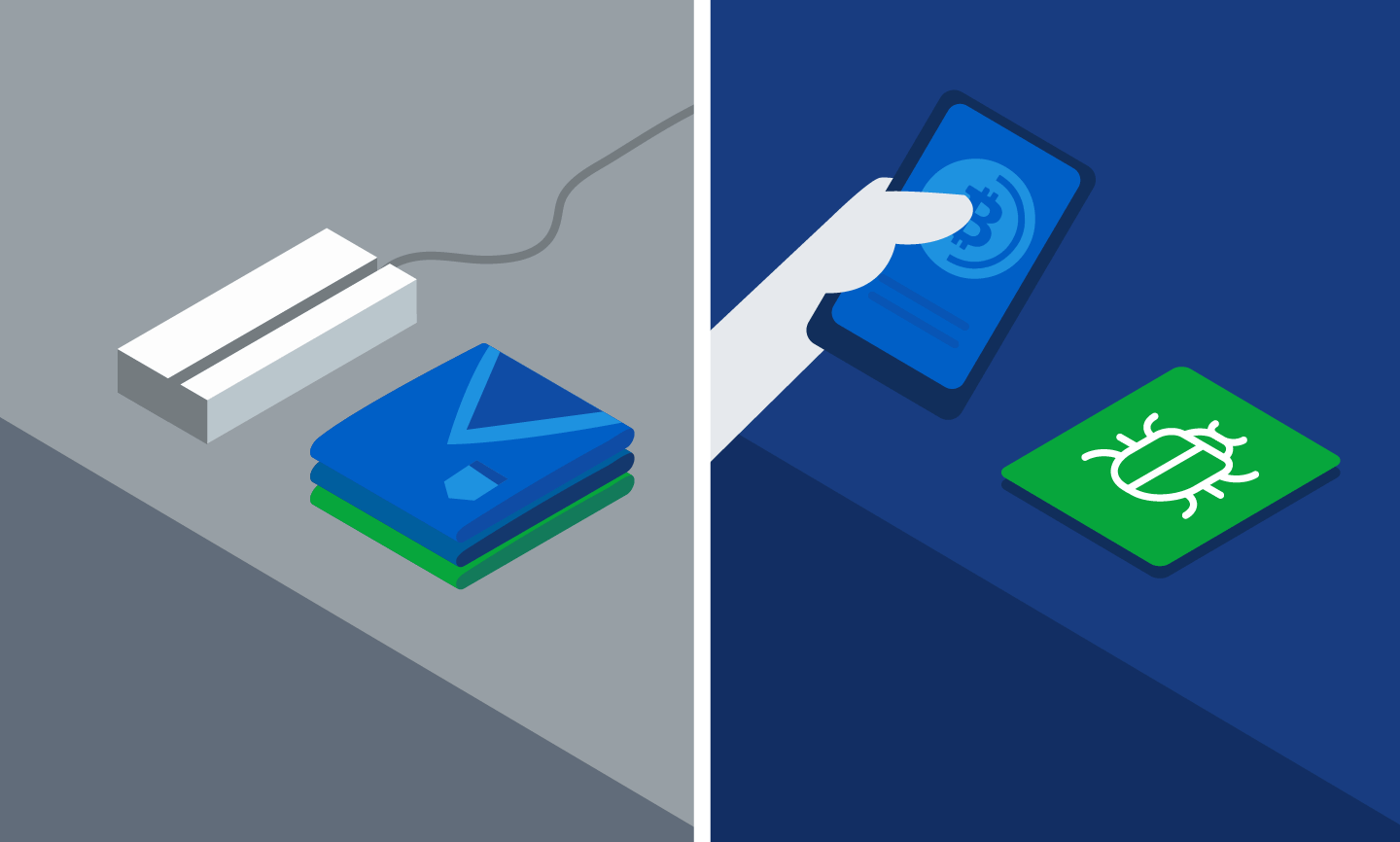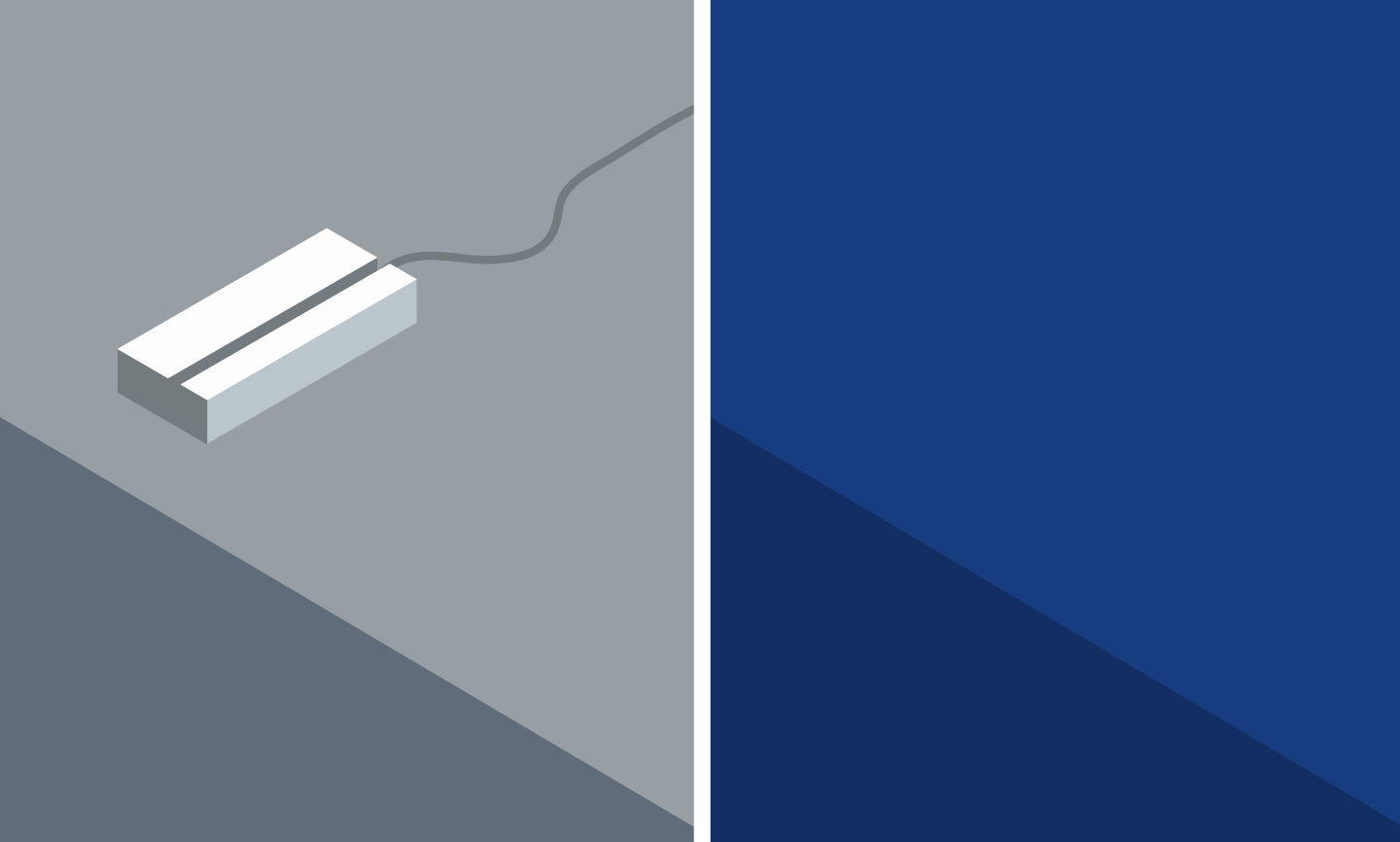
Insikt Group did observe at least one scenario that is likely unique to malware markets. A buyer looking for ransomware found a willing seller who met certain requirements and provided the requested malicious payload. Unfortunately, it came equipped with a hidden Bitcoin miner that did its drilling on the purchasing party’s system — buyers beware!

Initial research and the majority of follow-on analysis used the Recorded Future® Platform, which collects, organizes, and displays vast amounts of data, including posts from a diverse array of underground forums in multiple languages. Recorded Future aggregates and processes this information on a continuous basis, greatly improving the accuracy of this kind of research.
Below are the top 10 most popular types of malware from Insikt Group’s recent research piece.
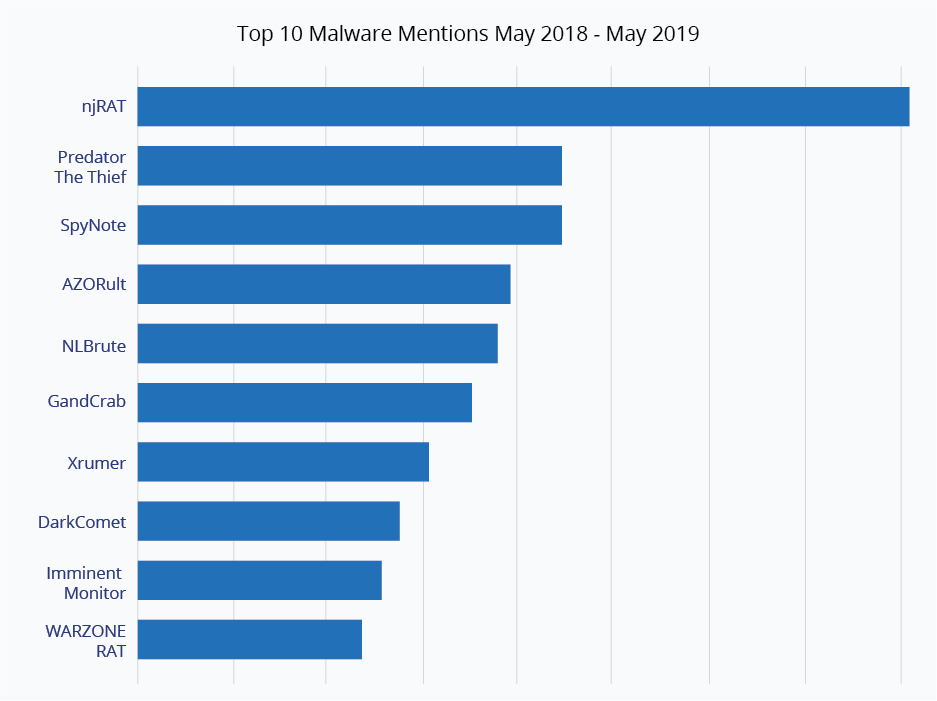
For more charts, including top malware by language, check out the full report by Recorded Future’s Insikt Group, “Bestsellers in the Underground Economy: Measuring Malware Popularity by Forum.”
Footnotes
The full report includes a list of known vulnerabilities for exploit kits used to deliver the top 10 most popular types of malware.
Related