Why Threat Intelligence Should Make Businesses Smarter, Not More Scared

Editor’s Note: The following blog post is a summary of a presentation from RFUN 2018 featuring A.J. Nash, global head of cyber intelligence at Symantec.
Key Takeaways
- When applied correctly, true intelligence can help cut through noisy news headlines and potential disinformation your security team may come across.
- Your goals for threat intelligence should tie directly to what’s most precious to your organization.
- Every element of a security team must collaborate to maximize the benefits of threat intelligence for the whole business.
In today’s security landscape, cyber threats are regularly making headlines — so much that they are now firmly embedded in the mainstream news cycle.
This increased awareness of attacks clearly has both a positive and negative impact for those tasked with protecting business infrastructure and data. While an increased profile encourages organizations to take addressing threats more seriously, it also risks creating unnecessary alarm among business users, especially when panic-inducing headlines are written to drive clicks rather than give any real indications of risk.
Information Overload
Symantec’s A.J. Nash is a seasoned cyber threat intelligence professional, having previously worked in financial services and for the U.S. government. This past October at RFUN 2018, Recorded Future’s annual user network conference held in Washington, D.C., Nash gave a presentation describing how his team at Symantec has been able to build an effective cyber intelligence program.
He encapsulated the challenges that those working with intelligence face when ensuring that security leaders are armed with the facts that can allow for clear-headed decision making, stating that the bottom line is, “intelligence provides context — it makes sense out of chaos.”
“Everybody’s overwhelmed. You’ve got data, you’ve got information, you’ve got news, you’ve got fake news, you’ve got misinformation. There’s just way too much coming at you. Leadership doesn’t have time to make sense of any of it,” Nash says.
Nash sees the purpose of a threat intelligence function as distilling all of the available information into what’s really important. In fact, often it’s communicating what’s not important that can ensure a measured response based on real risk. Nash summarized threat intelligence as “arming leadership with the most timely and relevant materials needed to make informed decisions” while simultaneously “helping dial down the strain and the stress” of input overload. He emphasized the importance of context as an underappreciated value of intelligence, saying, “Intelligence isn’t just about telling people what matters. It is also about helping leaders understand what they can safely de-emphasize or ignore.”
In one scenario, Nash describes how a business leader sounded the alarm at 4:00 AM in response to a cyberattack that became a large news story — what many might see as a gathering storm of attack and compromise requiring significant deployment of resources to ramp up protection.
At moments like this, threat intelligence can be the difference between a reasonable response and a series of efforts that waste time and energy. Nash described how his team works to articulate risk hidden in the headlines and contextualize a news story with the specific facts that determine whether this threat is relevant to their business. In his example, Nash explained that while a reported malware exploited a particular technology, protection was already in place at his organization, and intelligence revealed that the campaign that made the news only targeted a specific, unrelated industry.
That response, which put the threat in proper context, enabled decision-makers to react reasonably from an informed position, instead of unnecessarily expending resources to defend against a perceived threat far greater than the real one.
Focus on What’s Most Valuable
Nash is also full of advice for those looking to build their own threat intelligence program. He highlights the vital importance of clearly defining your requirements for threat intelligence before investing in people, technology, or services, saying, “If you don’t know what your needs are, you don’t know what you’re chasing. [When] everything’s important, nothing’s important.”
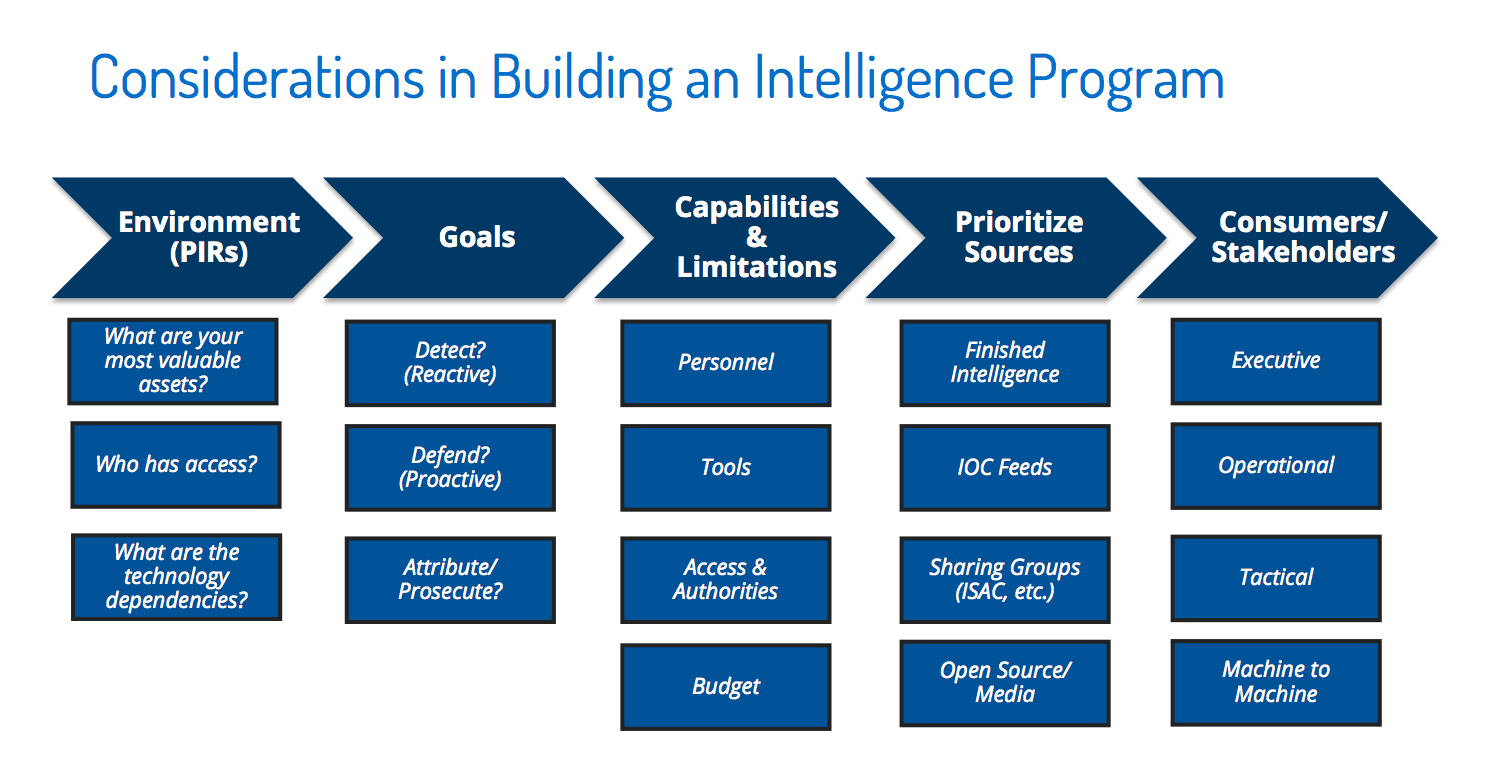
A lack of focus at this early stage creates the risk of being distracted by what Nash describes as “shiny objects.” One example of this is seeing the attribution of threats to particular actors as anything other than a way to better understand how to respond to the threat itself.
As Nash explains, even if you know who a bad guy is — maybe you have his name and his home phone number, or even a picture of him on Facebook with his girlfriend — you still need to keep your intelligence requirements front and center. Does this actor target your industry or the technologies you use? It’s answering this kind of question that provides insight into the real threat.
The Risks of Segregating Intelligence From the Rest of Security
Ensuring that intelligence sits at the center of security is also a key requirement identified by Nash, who says, “You can’t be segregated from your network security folks. If you don’t know your environments, you’re going to have a hard time mapping intelligence back to that environment to figure out the impact.”
While the specifications or speed of a particular technology or software are probably not of value, understanding the risks from exploitation is vital in producing useful threat intelligence. Some of this comes down to establishing strong working relationships, not just with those who will influence the nature of the intelligence you produce, but also with those who will consume and apply it.
Incident response is a good example. Teams fulfilling this role have the potential to become important “customers” of the intelligence program, so making sure intelligence is usable to them matters.
There is a personal element in making threat intelligence a vital component in security. As Nash puts it, “Go to lunch, hang out, get to know each other. It’s important. You’re going to both be much more successful.”
Threat Intelligence for All
You can find more useful advice on developing a threat intelligence program, as well as how intelligence can be consumed and used by all of security, in our “Threat Intelligence Handbook,” so be sure to download your complimentary copy today.
Related