Lizard Squad: Two Bot Thugs

Analysis Summary
Web intelligence has led to an analysis of Lizard Squad’s Linux botnet, LizardStresser or lizardstresser.su. Further link analysis of an email address associated with LizardStresser led to the discovery of a Windows botnet on ernsthaft.su.
Analysis of key cyber personas in Lizard Squad via their Twitter accounts through Recorded Future illuminated their interest in illegal drugs, thugs, guns, and Nazis.
Lizard Squad has been in the news for the past month as a rapidly evolving story since their Christmas day distributed denial of service (DDoS) attacks against Sony and Microsoft left customers unable to use their new merchandise. Lizard Squad also released a buy-a-DDoS botnet on December 30 and claim to be battling TOR after the Christmas day hacks. According to a recent CNN Money article, “Lizard Squad is a curious modern day phenomenon. With little technical skill and zero finesse, a mysterious group has affected more than 150 million lives by wreaking havoc on popular gaming networks in the last year.”
But who are these Lizards and what makes them tick? Although this article isn’t going to dox these hackers, it will help to identify them by their interests, vernacular, and lifestyle to provide insight into how they operate and what threat they may cause to corporations.
Utilizing Recorded Future to analyze the Twitter pages of the Lizards has provided valuable insight about the hackers. Lizard Squad’s leaders and key members are most interested in guns, drugs, gaming, and of course, hacking. It would also be easy to think the thing these lizards had in common was their gang/thug lifestyle instead of their hacking culture. Like most hackers, an incredibly inflated ego is another characteristic in common with these gangsters. Many of Lizard Squad’s members proudly use the coined phrase “R.I.U.” in their Twitter identities, which stands for “Resting In Undoxability.” Nearly every other tweet from the lizards is about how they have yet to be doxed, in a very taunting and naive fashion. And whether or not they have been doxed remains unknown, many are trying to dox them, including Anonymous and Finest Squad, both rivals of Lizard Squad.
LizardStresser
After the attacks on Christmas, Lizard Squad finished the final days of 2014 by releasing their buy-a-DDoS tool available for purchase at lizardstresser.su. For a small fee anyone can purchase Lizard Squad’s botnet for inflicting mayhem.
LizardStresser is an IRC Linux bot compiled for various home and high-capacity enterprise routing devices. The botnet client code has a function named getRandomIP that generates random public IP addresses. After generating random IPs, the code attempts to connect to each through telnet using numerous default usernames and passwords including: “root”: “”, “toor”:”admin”, “user”:”guest”, “login”:”changeme”, “1234”: “12345”, “123456”:”default”, “pass”:“password”.
In attack mode, the IRC-based bot client has four main flooding mechanisms: “TCPFlood”, “UDPFlood”, “HoldFlood”, and “JunkFlood”. Each mechanism seeks to overwhelm a targeted network with a massive DDoS attack from hundreds to thousands of poorly secured devices. Here are three known IP addresses for lizardstresser.su:
2014-12-31: 217.71.50.57 – Bosnia and Herzegovina
2014-12-30: 5.39.90.132 – France
2014-12-30: 198.100.144.122 – Canada
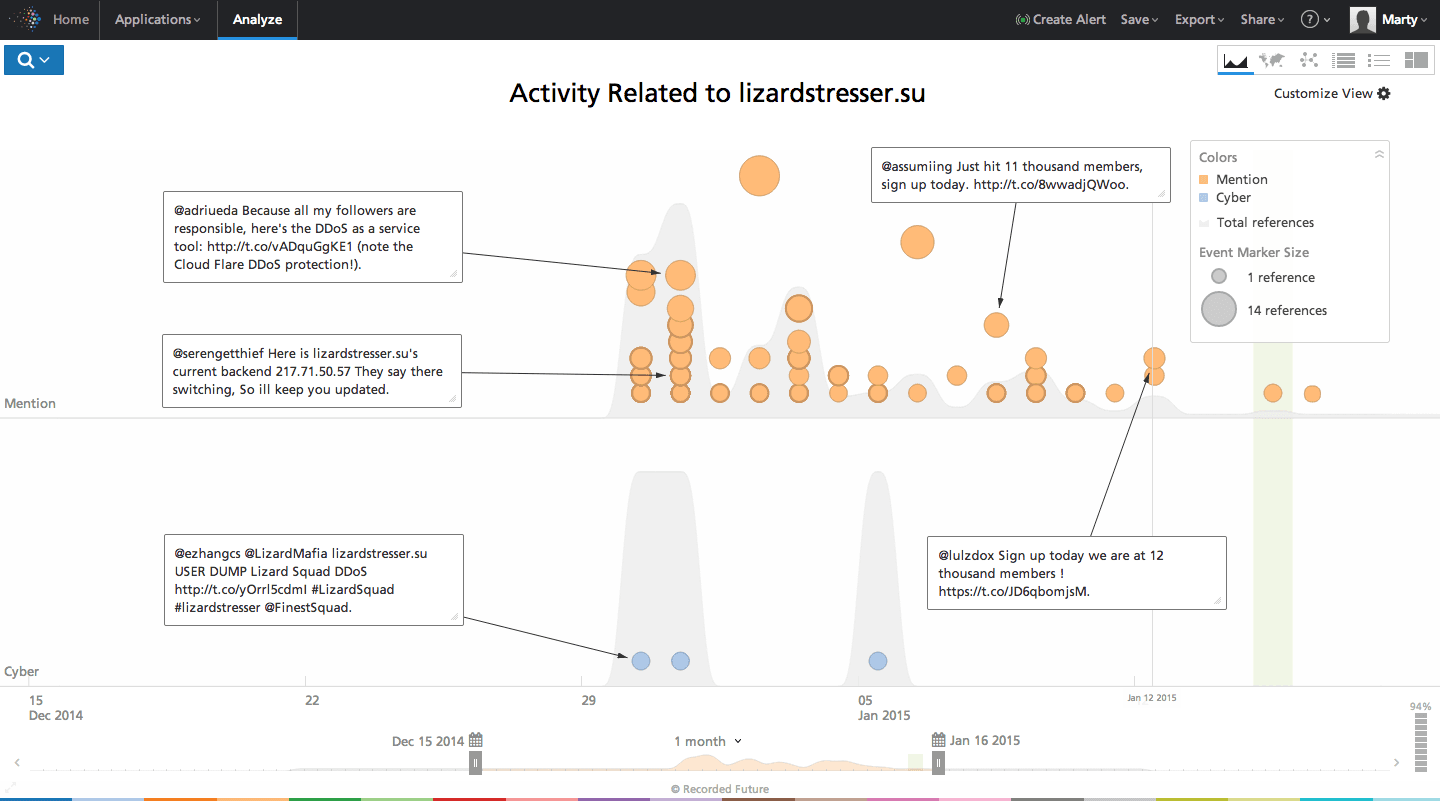
Click image for larger view
The source code for the LizardStresser botnet was posted on GitHub by pop-pop-ret, and appears to be leaked by packetprophet (Twitter handle @packetprophet) and Chippy 1337. Many other outlets have characterized the code as unoriginal and unimpressive. Not surprisingly, despite their own website being protected by CloudFlare anti-DDoS protection someone turned LizardStresser on itself, as posted on Twitter on January 12 by @packetprophet.

The domain lizardstresser.su was purchased on December 26, 2014 by the email address 9ajjs@zmail.ru. A domain search for this email finds that email address also registered 15 other domains which are listed below:
- BKCN.SU
- BTC-DMPS.SU
- BUSINET.SU
- GAIN-ACCESS.SU
- GETVERIFIED.SU
- INFORMATIONS.SU
- MADDOCS.SU
- MADSTORE.SU
- MSUPDATE.SU
- WEBRES.SU
- NIGHS.SU
- MADC.SU
- E6L.SU
- CCPOWER.SU
- ERNSTHAFT.SU*
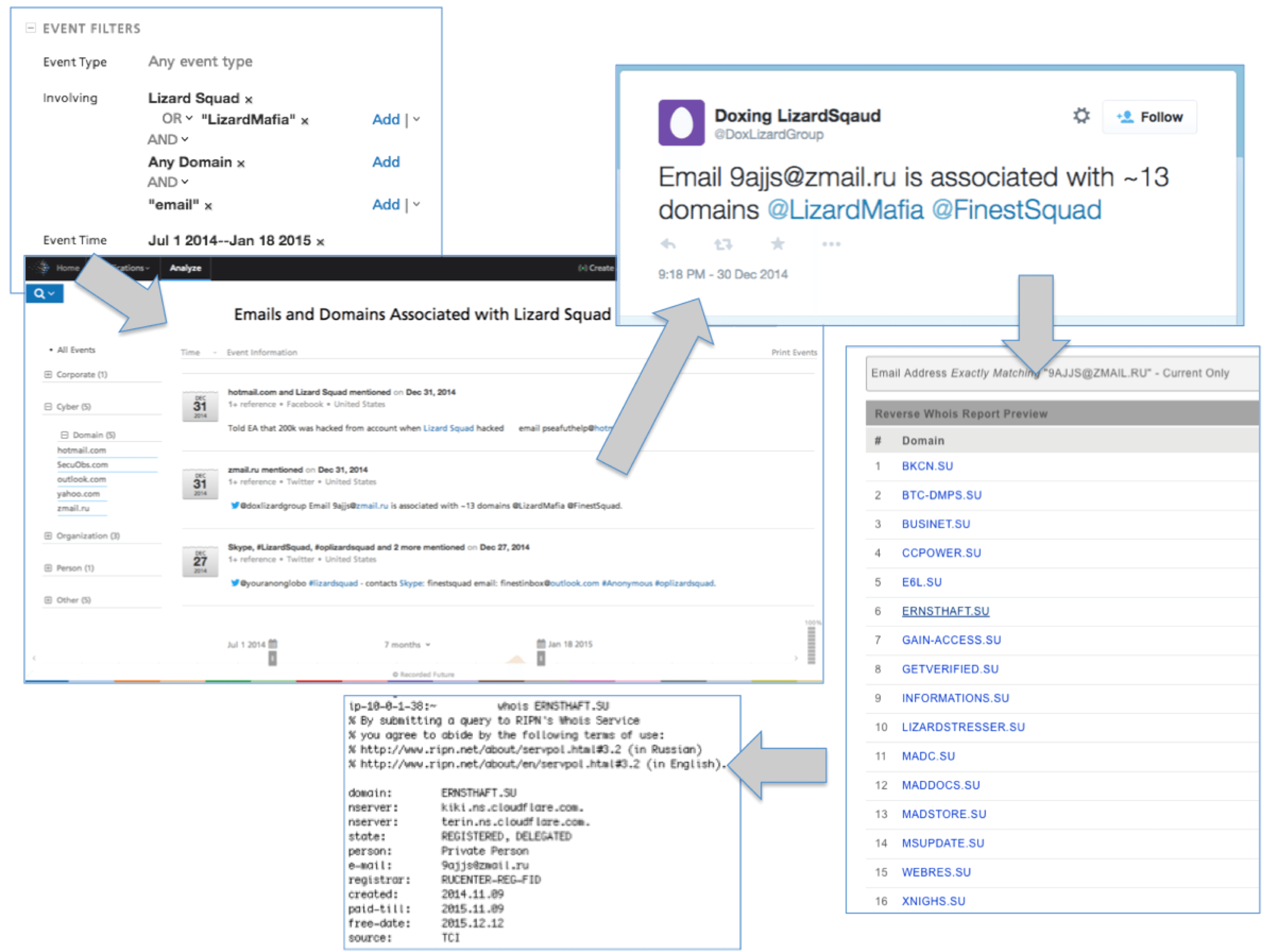
*Windows Botnet
The last of these domains, ernsthaft.su, Ernsthaft being German for “serious” or “sincere,” contained a directory listing of files. The file ert.exe is a Windows-based IRC bot client that connects to irc.ernsthaft.su which resolves to IP address 5.254.99.225 hosted on FlokiNET in Romania. At runtime ert.exe creates a new folder named C:WINDOWS1756410959 and drops the IRC bot to the newly created folder as C:WINDOWS1756410959lsass.exe. It then sets up a Auto Start Entry Point (ASEP) run key as HKLMSOFTWAREMicrosoftWindowsCurrentVersionRunOnce*1756410959: “C:WINDOWS1756410959lsass.exe.” Finally, it deletes the originally run file, in this case ert.exe.
The IRC bot features a host of capabilities including: “Skype Mass Messenger” that can send a message to multiple contacts simultaneously, “Open/Visit a URL” with a browser, “Download and Execute” a file, “Download and Execute Scheduled” file on a recurring basis, “FTP Upload” a file, “IRC War” to kill or flood one or more users, “Website Status” to check the status of a website, “File Search” to search the local file system for files of interest. In DDoS attack mode, the bot has a capability to “HTTP Flood,” “UDP Flood,” “ECF Flood,” and “Browser Based Flood” a target. On January 15 there were 13 clients connected to the irc.ernsthaft.su, although it remains unclear if all 13 were actually malicious botnet clients.
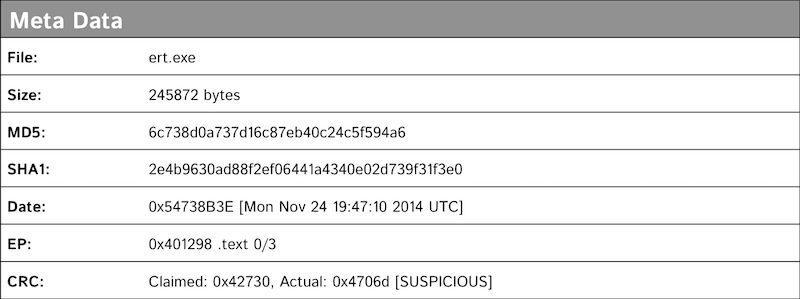
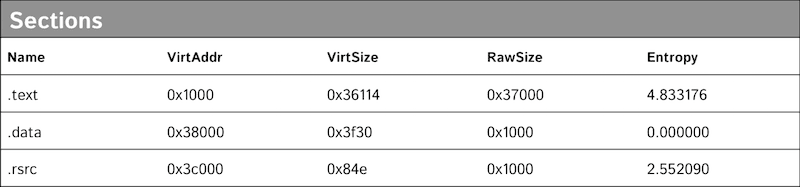
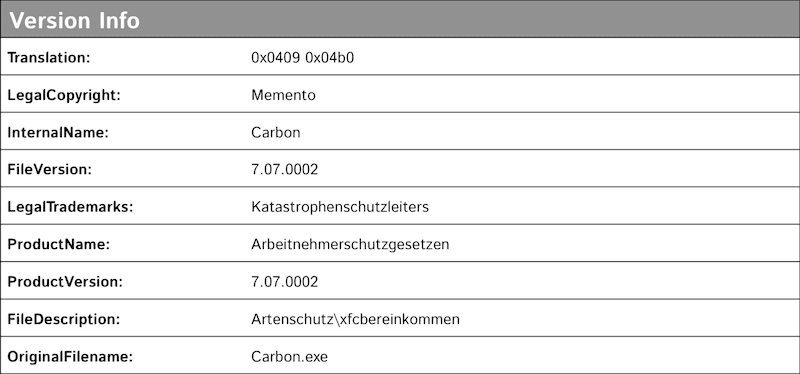

LizardStresser itself is predominantly based around the cross compiled Linux botnet client targeting routing devices. The ernsthaft.su finding of a Windows botnet is significant as both are registered to the user of 9ajjs@zmail.ru. The compilation date of the Windows based bot client malware was November 18, 2014, and the domain ernsthaft.su was purchased on November 9. This malware has not been publicized in previous reporting and so it remains unclear what will come of this botnet, but it’s related to Lizard Squad and is more capable than LizardStresser.
Who is Lizard Squad?
Website: lizardpatrol.com>
Twitter: https://twitter.com/lizardmafia
Email/XMPP: lizards@riseup.net
Chat: http://chat.lizardpatrol.com
IRC: irc.lizardpatrol.com #LizardSquad
On December 30, 2014 Eric Zhang, a student at Georgia Tech, posted an enumerated list of all of LizardStressers’ users. According to Zhang’s website, ericzhang.me, the enumeration revealed usernames, many which correspond with Twitter and or Facebook identifiers. While some users on the list may be those who have purchased LizardStresser, the first several usernames are probably members of Lizard Squad. This list was on Pastebin. There are nearly 300 names on Zhang’s list.
The key members of Lizard Squad are likely the users of Twitter handles TakenTheGod, GDKJordie, and ChF. Given their vernacular it’s likely these individuals are from the United Kingdom, Canada, or the United States. It’s also possible other members of the squad are from other countries.
TakenTheGod
@TakenTheGod
TakenTheGod is believed to be the current leader of Lizard Squad. He’s also the founder of a group called NaziSec (@NaziSecurity), as stated on his Twitter page. NaziSec has a website, ugnazi.com, which describes how their main target is Operation AntiGov, #OpAntiGov, but also target ufc.com, coach.com, and coachfactory.com because they support the Stop Online Piracy Act (SOPA) and other sites supporting the Cyber Intelligence Sharing and Protection Act (CISPA).
GDKJordie
R.I.U. Jord #GiLU
@GDKJordie
#JordGang
According to posts on Pastebin, GDKJordie was at one time the leader of Lizard Squad but is now more of a figurehead to the group. It’s unclear whether or not this is true, but from analysis of his Twitter page he continues to operate on behalf of Lizard Squad, often while boasting about being under the influence of illicit drugs.
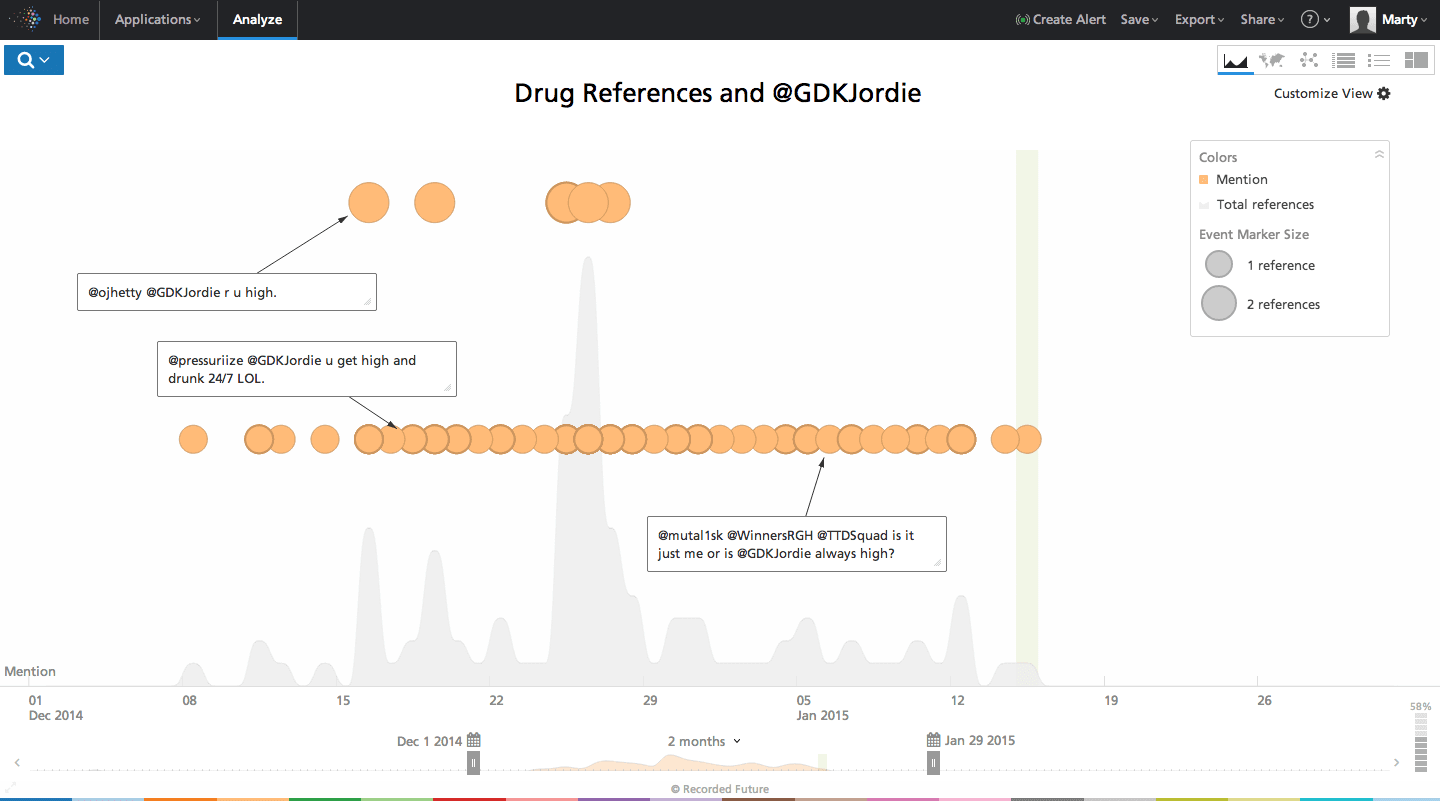
Click image for larger view
ChF
R.I.U. chF #iAC
@notchF
Member of the #LizardSquad CyberCaliphate
ChF is also a key member of Lizard Squad and is very into his thug lifestyle. Based on an analysis of the picture below that ChF (@notchF) tweeted on January 11, he’s likely in the United States or Canada because of the weapons he poses in the photograph.

Conclusion
Lizard Squad, despite their obsession with staying “undoxable” pose a serious threat to network providers worldwide. Not only does Lizard Squad possess a Linux capability but they also have crafted a Windows botnet variant giving their operations cross-platform capabilities. The convergence of the thug-life culture and pro-Nazi sentiments is perplexing. It’s possible the new leadership of TakenTheGod, who also runs NaziSec, is changing the dynamics and possibly the focus of Lizard Squad in the future. The likely unused malware botnet on ernsthaft.su containing images of a lizard in Nazi uniform may be an indication of things to come from the kids at Lizard Squad. Many of Lizard Squad’s previous attacks have come with forewarning. It would be prudent to heed these warnings as a serious threat as they appear over the coming months of 2015.
Related