Latin American Governments Targeted By Ransomware

Recorded Future examined the recent escalation of cyberattacks on Latin American (LATAM) governments from January 2022 until May 2022. We analyzed vulnerabilities, attack vectors, and indicators of compromise (IOCs), identified the most prevalent ransomware gangs targeting LATAM governments, and highlighted the lack of proper cybersecurity hygiene in the region. This report includes information gathered using the Recorded Future® Platform, dark web sources, and open-source intelligence techniques (OSINT).
Executive Summary
We identified several government entities in Latin America (LATAM) that have been affected by ransomware attacks, likely involving Russian or Russian-speaking threat actors, beginning on or around April 2022. Countries affected include Costa Rica, Peru, Mexico, Ecuador, Brazil, and Argentina, among others, all of which have publicly condemned Russia for invading Ukraine at the United Nations General Assembly (UNGA). Some of these countries also voted to suspend Russia from the United Nations Human Rights Council (UNHRC) in early April 2022. More recently, national emergencies have been issued regarding these attacks, such as in Costa Rica. Ransomware groups involved in these attacks against governments in LATAM include Conti, ALPHV, LockBit 2.0, and BlackByte. We have anecdotally identified a noticeable increase in initial access brokerage (IAB) services on top-tier Russian-language dark web and special access forums such as XSS and Exploit advertising low-cost, compromised network access methods related to entities in LATAM. We have also observed several high-profile database leaks related to entities in LATAM on low-tier and mid-tier English-speaking forums such as BreachForums, with data dumps spiking in April 2022. Additionally, we observed a significant increase in the sale of compromised credentials affecting LATAM government domains on dark web shops in Q1 and Q2 2022, relative to 2021. These observations and trends could represent a paradigm shift in the ransomware and broader cybercriminal community related to “unwritten rules” and internal group policies on the targeting of government entities.
Key Judgments
- The credibility of ransomware attacks on LATAM government entities is high, based on analysis of leaked sample data, threat actor indications, and historical activities, patterns, and trends related to tracked ransomware operators and affiliates.
- If unaddressed, ransomware attacks on local, provincial, or federal government entities in LATAM could constitute a credible national and geopolitical security risk. Entities in LATAM will remain attractive targets for ransomware operators and affiliates, as the region lacks the proper cybersecurity education, hygiene, and infrastructure to defend against such threats. If attacks on LATAM government entities were to escalate to target infrastructure and critical services, this would pose a significant national security risk.
- The most likely attack vectors employed by ransomware affiliates targeting LATAM government entities include the use of compromised valid credentials obtained via infostealer infection, initial access broker sale, or purchase on a dark web shop or marketplace.
- The targeting of LATAM government entities could represent an initial shift away from internal cybercriminal policies on the targeting of governments worldwide.
Threat Analysis
Attack Vectors
As of May 26, 2022, we can not definitively determine the attack vector employed by ransomware operators and affiliates targeting LATAM government entities. However, the most common method by which threat actors obtain initial access to networks is through the use of compromised valid credential pairs (T1078) and session cookies (T1539), which are often harvested from a successful infostealer infection (T1555, T1083) and sold by specialized “initial access brokers” on dark web and special-access sources. This is the most likely avenue by which such threat actors gained access to compromised LATAM government networks. These infostealers are often spread via phishing (T1566), spamming, the unintentional downloading of a malicious (T1204) or masquerading (T1036) file, and various other methods. We have observed a minor, sustained increase in references to initial access sales and database leaks targeting LATAM government entities on dark web and special-access sources, beginning in approximately March 2022. These observations are recorded anecdotally via Insikt Group’s daily threat leads, analyst notes, and reports. We have observed several threat actors, such as “zirochka”, on top-tier Russian-language forums XSS and Exploit auctioning compromised network accesses targeting entities in LATAM in bulk for relatively low prices (< $100).
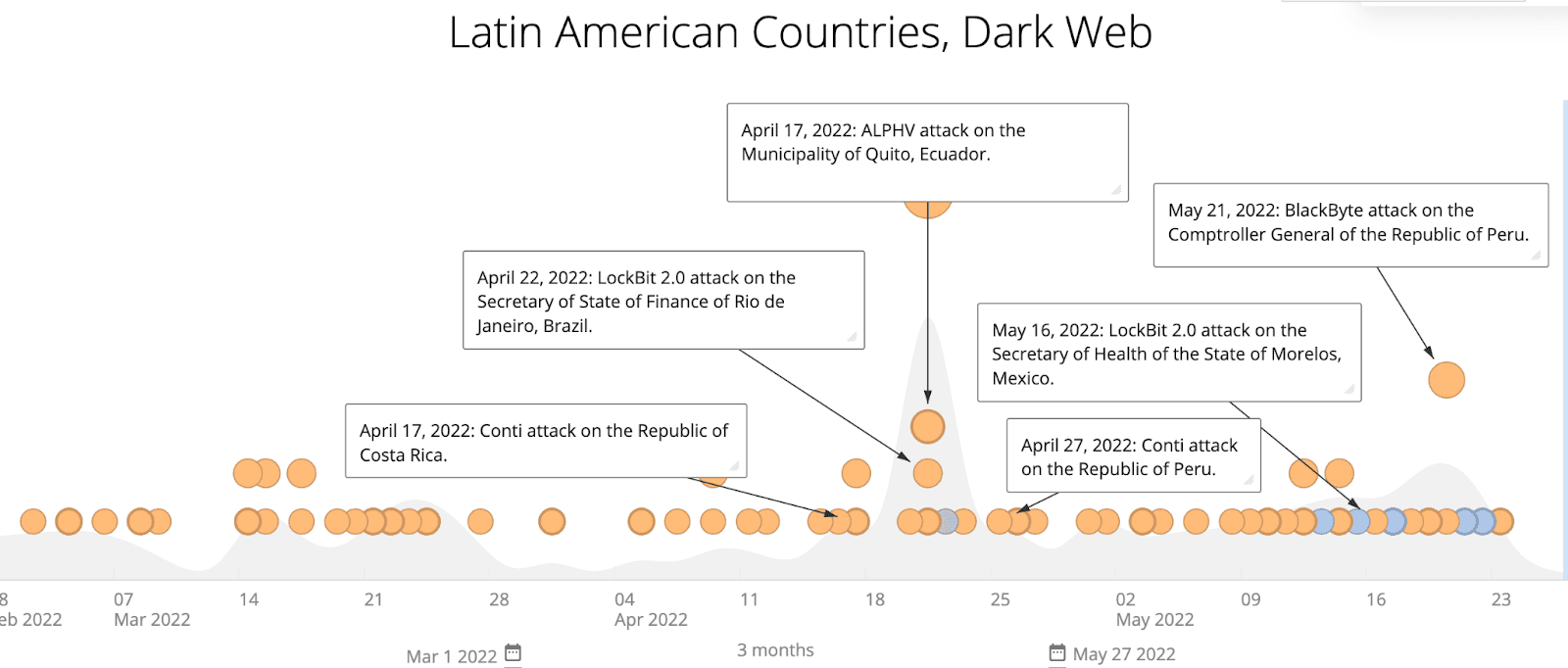 Figure 1: Timeline of ransomware attacks on LATAM government entities, mapped to references to LATAM on dark web and special-access sources (Source: Recorded Future)
Figure 1: Timeline of ransomware attacks on LATAM government entities, mapped to references to LATAM on dark web and special-access sources (Source: Recorded Future)
We have observed a slight increase in database dumps related to LATAM government entities, beginning in March 2022 and spiking on April 4, 2022. We have also identified a significant increase in Q1 2022, beginning in February 2022, of references to domains owned by government entities in LATAM on dark web shops and marketplaces such as Russian Market, Genesis Store, and 2easy Shop, relative to the same time period in 2021. These dark web shops and marketplaces specialize in the sale of compromised account credentials, remote desktop protocol (RDP) and secure shell (SSH) accesses, and infostealer malware “logs” that can be utilized to gain access to a victim’s network. While we cannot determine any direct or causal link between the increased supply, frequency, and volume of advertisements targeting government entities and domains in LATAM to ransomware attacks targeting LATAM government entities, we believe that such trends and observations warrant further research to analyze and determine any possible correlation.
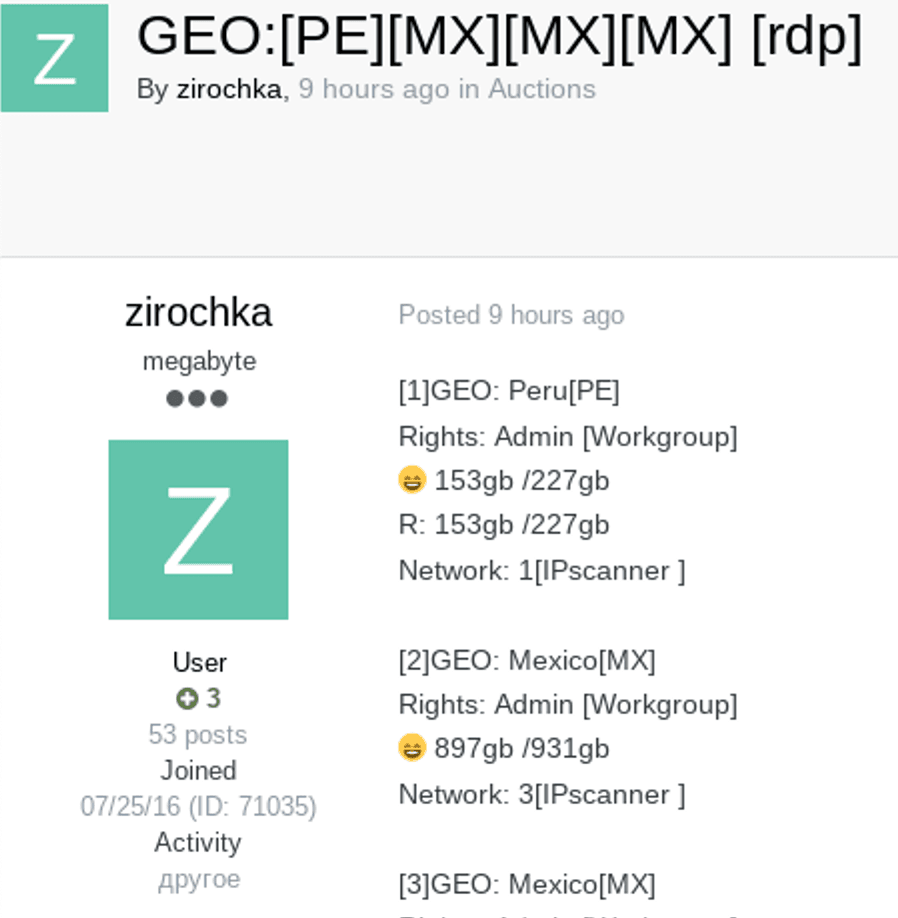
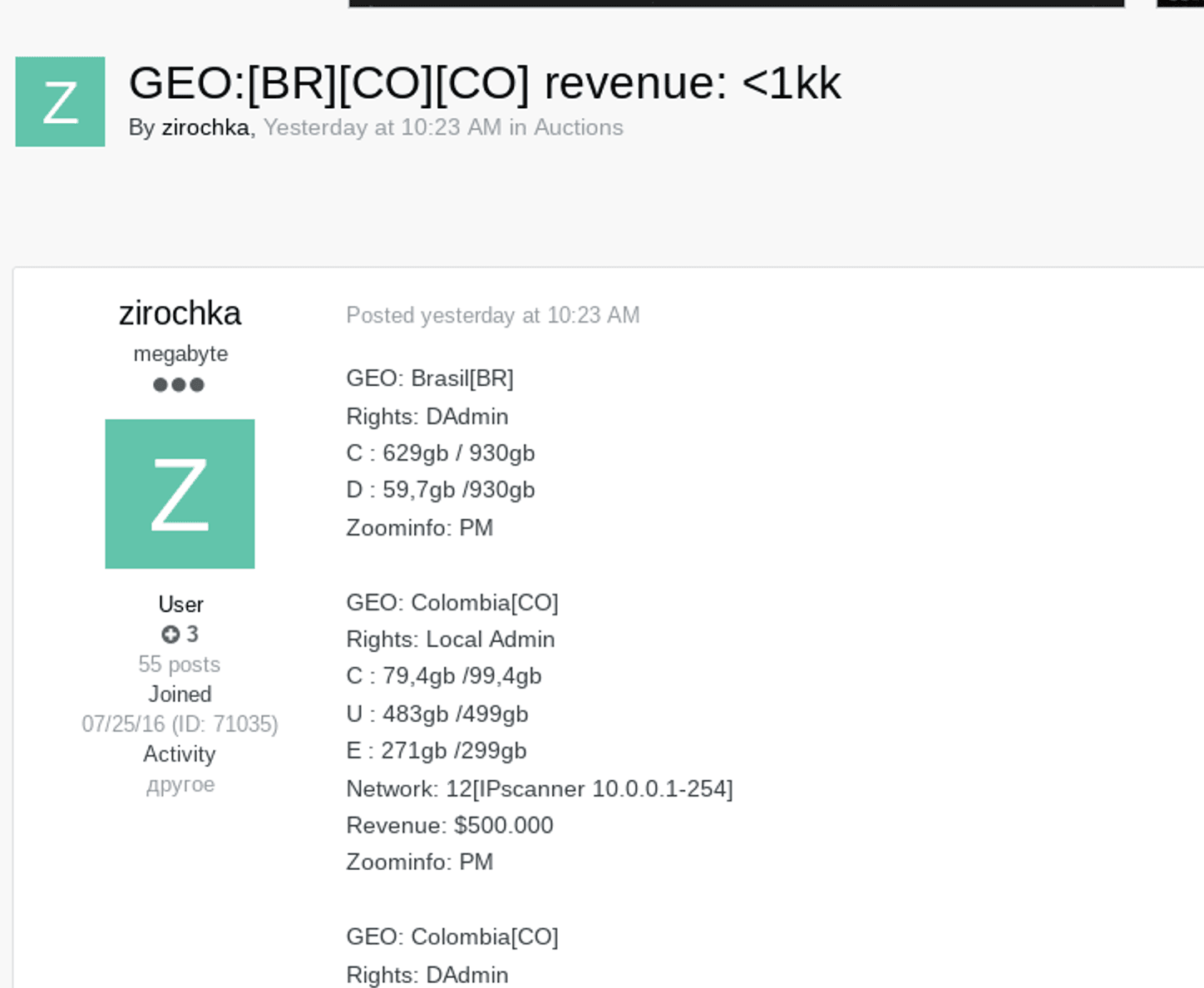
Figure 2: Examples of bulk initial access auctions targeting unspecified entities in LATAM (Source: Exploit Forum)
Ransomware Gangs Targeting LATAM Government Entities
We have observed at least 4 high-credibility ransomware gangs targeting LATAM government entities during a period of time beginning on April 1, 2022. These gangs include Conti, ALPHV (BlackCat), LockBit 2.0, and BlackByte. These incidents constitute a significant escalation in the severity and impact of ransomware targeting. Generally, ransomware affiliates avoid targeting healthcare facilities, K-12 educational institutions, international organizations and coalitions, and local, provincial, or federal governments. The risk of negative publicity and stigmatization on dark web and special-access forums, mainstream media attention, and international law enforcement activity increases dramatically once targets in these industries are attacked. It is possible that the targeting of LATAM entities by presumably Russian or Russian-speaking ransomware gangs could mark the beginning of a paradigm shift in which targets that were previously internally sanctioned by the group could now become viable targets for ransomware operations.
Conti
The most noteworthy of these targets is the attack on the government of Costa Rica by Conti, which resulted in the world’s first nationwide emergency declared as the result of a ransomware attack. The attack, likely perpetrated and publicized by ransomware affiliate or affiliate group “unc1756”, also likely known as “wazawaka”, has garnered widespread media and law enforcement attention. Since affiliates often work independently from the larger ransomware “brand”, it is possible that the attacks on Costa Rica that were claimed by Conti are not the work of the larger group. Conti has claimed to have exfiltrated, encrypted, or destroyed approximately 1TB of sensitive information related to the administration and operations of several Costa Rican entities including the Ministry of Finance (hacienda[.]go[.]cr), the Ministry of Labor and Social Security (mtss[.]go[.]cr), the Development Fund and Family Allowances Bureau (fodesaf[.]go[.]cr), and the Interuniversity Headquarters of Alajuela, Costa Rica (siua[.]ac[.]cr). Previous Conti posts also made vague references to controlling public utilities such as water and electricity, likely indicating indirectly that the group had access to Costa Rican industrial control system / supervisory control and data acquisition (ICS/SCADA) environments. However, we are not able to verify these claims. Conti followed their claims of an attack on Costa Rica with an attack on Peru that affected the General Directorate of Intelligence (digimin[.]gob[.]pe) and Ministry of Economics and Finance (mef[.]gob[.]pe).
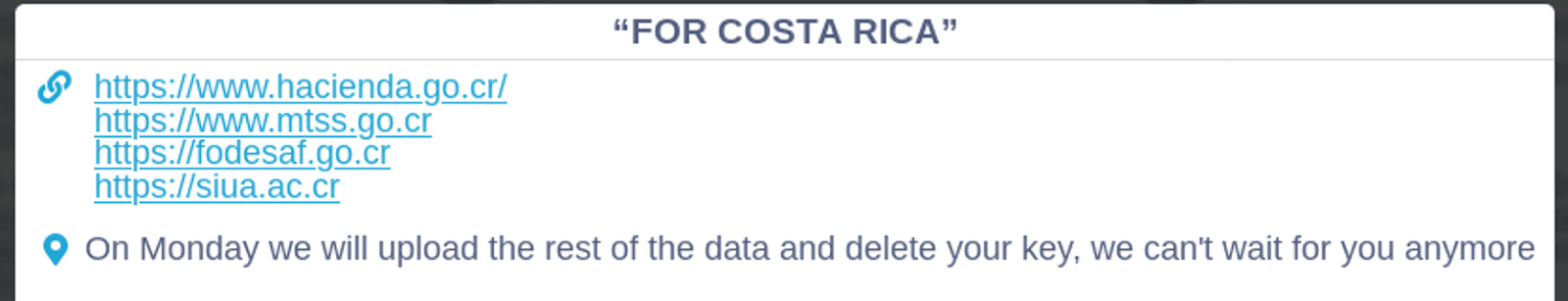
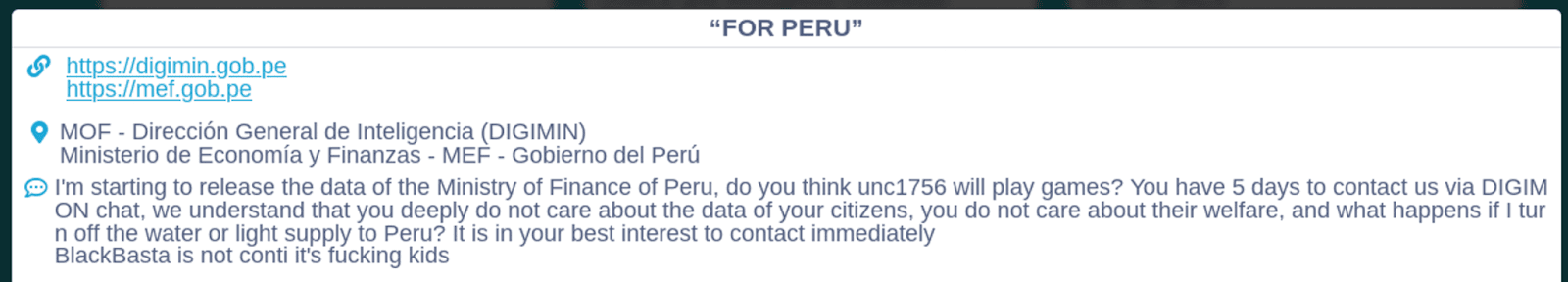
Figure 3: Announcements of attacks on Costa Rican and Peruvian government entities by the Conti Gang (Source: Conti.News)
ALPHV (BlackCat)
On April 16, 2022, the ransomware gang ALPHV (BlackCat) leaked an unspecified amount of compromised data related to the Municipality of Quito, Ecuador (quito[.]gob[.]ec). This marked the first time that ALPHV targeted a government entity located in LATAM. According to Ecuadorian media, this attack took several services offline for an unspecified amount of time. This is a noteworthy event, as the Mayor’s Office of Municipality of Quito and State Attorney General’s Office confirmed that the initial attack caused the “suspension” of several critical government services, which caused an “inconvenience to users who have not been able to carry out procedures.” As of April 25, 2022, all of the information claimed to have been exfiltrated by ALPHV is available to download for free on a .onion domain provided on the public-facing ALPHV extortion website with the same name. Compromised information likely includes sensitive financial, legal, and political documents related to the operations and administration of the Municipality of Quito, Ecuador. This information, if leveraged by an opportunistic threat actor, criminal, or nation-state, could prove to be damaging to Ecuador’s national security.

Figure 4: Announcements of an attack on the Municipality of Quito, Ecuador from the BlackCat Ransomware Group (Source: ALPHV)
LockBit 2.0
On May 23, 2022, the LockBit 2.0 ransomware gang published to their blog leaked files related to the Secretary of Health of the State of Morelos, Mexico (saludparatodos[.]ssm[.]gob[.]mx), a breach that was initially disclosed on or around May 16, 2022. This disclosure followed a previous claim on April 22, 2022 that LockBit 2.0 had compromised the network of the Secretary of State for Finance of Rio De Janeiro, Brazil (fazenda[.]rj[.]gov[.]br). Neither of these incidents were widely reported in either Mexican or Brazilian media. As of April 25, 2022, it is unclear whether the attacks resulted in a significant disruption of critical services related to the government entities. Additionally, also as of April 25, 2022, all of the information claimed to have been exfiltrated by the LockBit 2.0 ransomware gang is available to download for free on the public-facing LockBit 2.0 extortion website called LockBit 2.0 Leaked Data. The compromised information likely includes sensitive financial, legal, and political documents related to the operations and administration of these entities. This information, if leveraged by an opportunistic threat actor, criminal, or nation-state, could prove to be damaging to the national security of Mexico and Brazil.
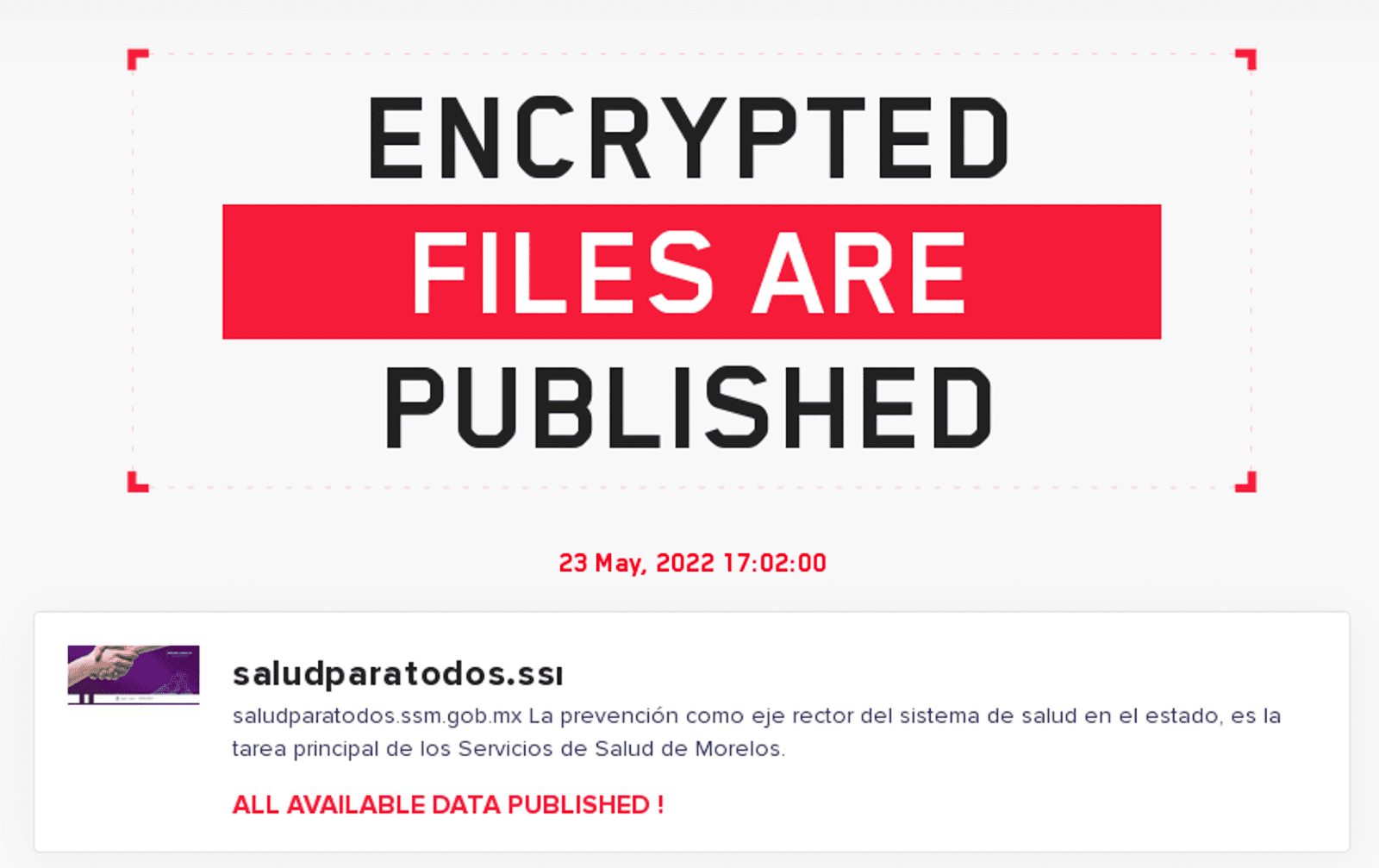
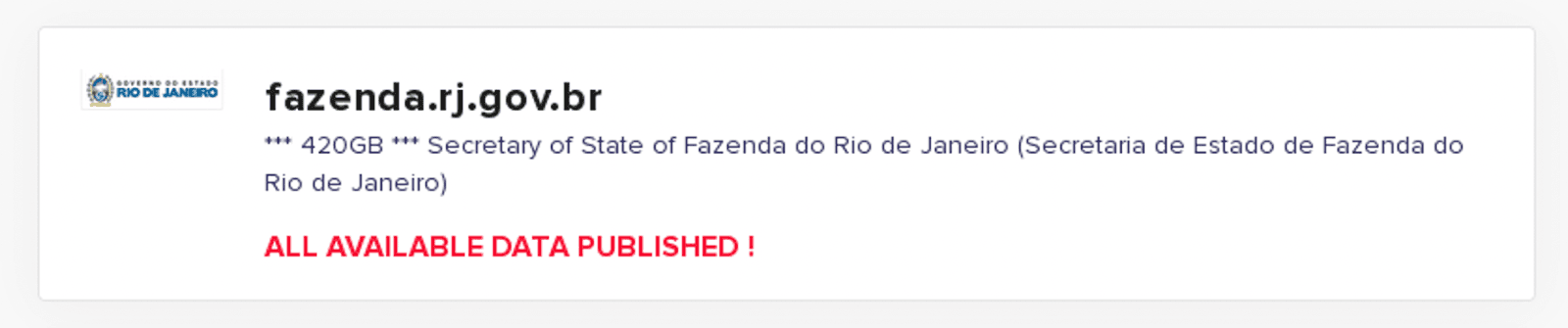
Figure 5: Announcements of attacks on Mexican and Brazilian government entities by the LockBit Gang (Source: LockBit Blog)
BlackByte
On May 21, 2022, the BlackByte ransomware operators published claims on their public-facing extortion website named BlackByte Blog that they had compromised the internal network of the Comptroller General of the Republic of Peru (contraloria[.]gob[.]pe). As of April 25, 2022, the BlackByte ransomware operators have not published any noteworthy data related to this government entity. This attack has yet to be confirmed by any representatives of the Comptroller General of Peru and has not been extensively reported on in Peruvian or Spanish-language media. As of this writing, we cannot determine if this attack caused the disruption of critical services provided by the comptroller general, although it is likely that any detected service disruptions on the domain are related to this attack.
Figure 6: Announcement of an attack on a Peruvian government entity by the BlackByte Ransomware Gang (Source: BlackByte Blog)
Cybersecurity Hygiene and Trends in Latin America
Although most countries in LATAM have adopted a national cybersecurity strategy, there is still much work yet to be done in terms of improving the cyber capacity and security posture in both the private and public sectors; at the moment, only 3 LATAM countries (Brazil, the Dominican Republic, and Mexico) are members of the 30-plus-country ransomware task force. The most effective investment would be to give residents in LATAM and the Caribbean in-person or remote access to IT security-oriented schools and training institutions. Educational and training institutions in the region simply cannot keep up with the current demand for IT security professionals. Investments in education, training, and apprenticeship programs would make the most difference in building capacity, closing the cyber skills gap, and getting more individuals into the cyber talent pipeline. Supporting and encouraging younger individuals to seek an education and training within the cyber realm can drastically affect the skills shortage and improve public awareness on cyber threats; the region has been particularly affected by cybercrime and fraud during the pandemic.
While it is difficult to evaluate countries given their alternative approaches to cybersecurity, some have decided to leave cybersecurity to private firms while others have leaned on government agencies and the military to combat cybercriminals. According to the Organization of American States (OAS) cybersecurity observatory, most LATAM countries are in the early stages of cybersecurity development. As a result, there is still a lot to accomplish and implement in terms of cyber security policies in Central American and Caribbean countries. Nevertheless, countries such as Argentina, Dominican Republic, Ecuador, Panama, and Peru, among others, are making significant efforts to advance their cyber capabilities. However, there is a small list of countries with established policies, legal frameworks, institutional capacity, and human capital resources, including Brazil, Uruguay, Colombia, and Chile. And although they are still developing, countries such as Brazil, Colombia, Chile, and Mexico have taken the lead in broadening their institutional capacities, including the development of cyber laws, policies, and regulations. There is also increased expertise in the private sector, primarily the financial sector, within these nations.
Mitigations
It is crucial to maintain offline backups of your organization’s data and ensure that these backups stay up to date to prevent data loss in the event of a ransomware infection. Additionally, we recommend the following mitigations to reduce overall risk and impact:
- Ransomware often follows a specific pattern of behavior that can be detected with a robust threat intelligence system that is integrated with SIEM platforms.
- Implement YARA rules such as the ones found in Recorded Future Hunting Packages to identify malware via signature-based detection or SNORT rules for endpoint-based detections.
- The IOCs provided throughout this report can be used to proactively query or scan environments for items such as file hashes, registry keys, and IP traffic associated with ransomware.
- Network segmentation can halt the propagation of ransomware through an organization’s network. This solution involves splitting the larger network into smaller network segments and can be accomplished through firewalls, virtual - local area networks, or other separation techniques.
- Implement intrusion detection / intrusion prevention (IDS/IPS) systems and endpoint detection and response (EDR) systems.
- Provide robust anti-phishing training for employees and staff.
- If remote access solutions are crucial to daily operations, all remote access services and protocols such as Citrix and RDP should be implemented with two-factor or multi-factor authentication.
- Exposed RDP servers are also abused by threat actors to gain initial access into a target’s network. Threat actors will look for networks that have internet-facing servers running RDP and then exploit vulnerabilities in those servers or use brute force password attacks. Once inside the network, the threat actors move laterally and install ransomware on target machines, often disabling backups and other protections.
- Through the use of process monitoring, monitor for the execution and command of binaries involved in data destruction activity, such as vssadmin, wbadmin, and bcdedit.
- Monitor for the creation of suspicious file modification activity, particularly large quantities of file modifications in user directories.
- Consider keeping sensitive client information on systems that are disconnected from the internet or segmented from the rest of the corporate network. Since ransomware will encrypt all files on a victim system and often will search for directories on the network (such as networked file shares) to also encrypt, moving highly sensitive customer data to a system with no internet access or access to the rest of the network will minimize ransomware’s access to those files.
Outlook
Ransomware will likely continue to be incorporated into the attack methods of threat actors targeting public and private entities in LATAM due to their availability as ransomware-as-a-service (for non-technical threat actors) and highly successful infection rates. Compromised accounts and networks are highly sought after by threat actors and will remain in high demand because they can be used in a number of attack vectors, including but not limited to account takeovers, identity theft, social engineering, credential stuffing, and brute forcing. As LATAM is an up-and-coming region whose security posture is not as sophisticated or developed as some other regions for various reasons (geopolitical circumstances and developing infrastructure, among others), threat actors may view LATAM entities as easy targets for harvesting sensitive and financially lucrative accounts via infostealer infections.
As incident response teams in the region build up their security posture, threat actors are likely to continue to enhance and create infostealer variants to target organizations in LATAM with the intent of harvesting personal and corporate account login details and other important data.
Related