Ransomware: Latest Developments and How to Defend Against Them
_Editor’s Note: We’re sharing excerpts from the third edition of our popular book, "The Security Intelligence Handbook."
Editor’s Note: The following blog post is a summary of a Dark Reading webinar we co-hosted with Gal Shpantzer, security analyst and advisor, and Allan Liska, threat intelligence analyst at Recorded Future.
Key Takeaways
- Ransomware is a direct monetization attack against availability, stealing something in your database and then trying to sell it back to you.
- Segmentation and segregation as well as bolstering your web defenses are among the best prevention strategies against ransomware.
- The major types of ransomware attacks are client-side, server-side, hybrid, and worms.
- It’s critical to prevent initial infection, mitigate the spread, and detect and respond aggressively to ransomware incidents.
When it comes to ransomware and its distribution, it’s critical to have a strong threat intelligence strategy in place to mitigate the latest developments, and once it gets on your network, understand exactly how it works.
During a recent webinar, Gal Shpantzer shared insight into not only why ransomware is prominent, but also how it can be better prevented. Shpantzer has over 15 years of experience as both an independent security professional and the trusted advisor to CISOs of large corporations, startups, and nonprofits, and since 2014, has focused on emerging threats to availability and confidentiality.
With ransomware, you’re not dealing with threat actors that are slow-moving confidentiality attackers, Shpantzer says. Rather, they are aiming to fully deny availability, whether it’s for money or just to destroy property and make it difficult to restore.
The world has seen its fair share of ransomware attacks — the WannaCry and NotPetya attacks were in the past year alone. These attacks were direct ransom worms that had to do with informational warfare between countries, managing to affect large entities and causing organizations to rebuild active directories.
Because ransomware is so destructive, legitimate, and timely, threat intelligence is key. It’s critical to ingest your intelligence capability and move it out to your endpoints and network devices, ensuring that you survive ransomware exposure with rapid awareness and action.
The Big Picture
So, where do we begin? It’s first important to understand the big picture. From an abstract view, Shpantzer says that information technology has a hierarchy of needs that must be met thoroughly to ensure there are no gaps in your defense strategy.
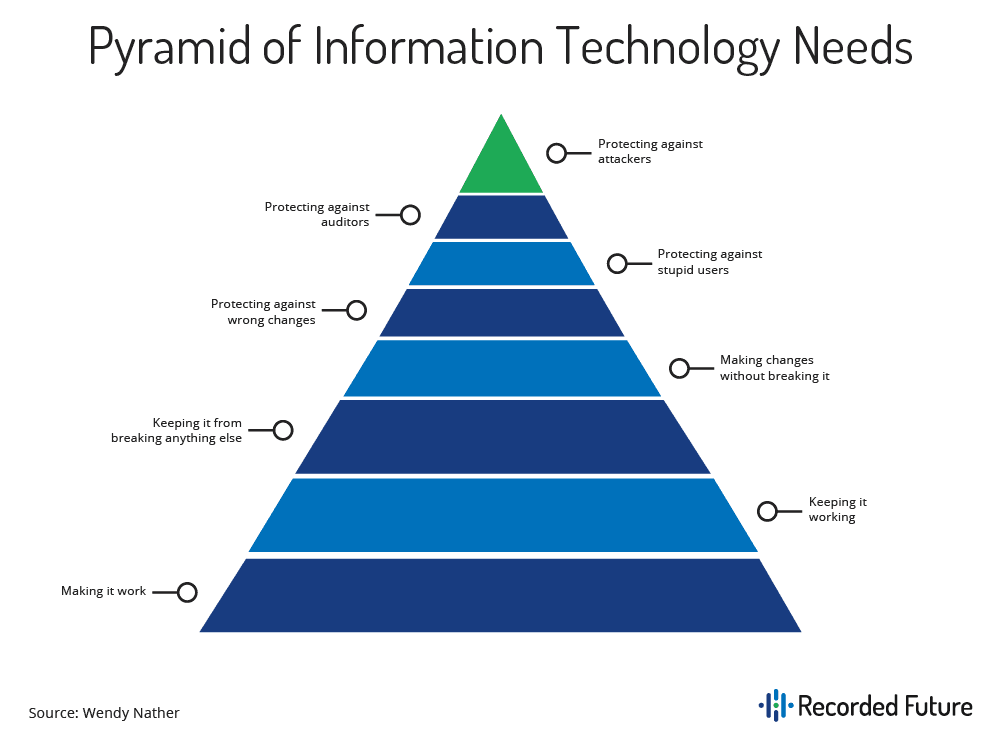
Shpantzer says that at the bottom of the hierarchy, effective threat intelligence is about making sure your security function is constantly working to patch and protect any changes without breaking the process.
After ensuring your security function is operating well, users who are more at risk of getting attacked must be protected — these are the kinds of users who are not necessarily made aware of the latest and greatest trickery, Shpantzer explains. For example, people in human resources or finance have the job of clicking things all day long, as well as invoicing and dealing with forms, so that means you have to architect against that.
Lastly, there’s the auditors and attackers. When it comes to security versus audit and compliance, there are difficult things to juggle, and when attackers come into the mix, suddenly they’re sending malicious stuff your way and trying to demolish your networks or steal from you — or both.
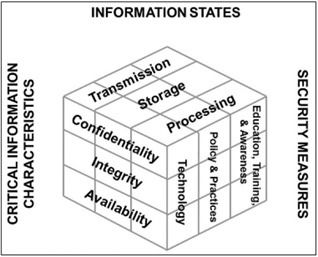
As seen in the McCumber model pictured above, Shpantzer explains that there are critical information characteristics to hone in on when dealing with certain information states, and this is implemented through specific security measures.
People in the information security field tend to focus a lot on technology and confidentiality, but understanding the balance between confidentiality, integrity, and availability is where the gap needs to be filled. It’s critical to understand how to use technology along with policy and practices.
But how does this tie back to ransomware? One of the hazards that ransomware causes is endangering your availability, Shpantzer says.
For example, if a retailer unwittingly gets infiltrated, they keep the lights on and continue bringing in customers. Everything is great until they figure out that somebody got in, exploited stuff, copied it, and exfiltrated it. So when a ransomware attack strikes, they’re not only trying to focus on availability to be able to stay up and running, but they’re also trying to keep the infiltration a secret.
So Why Ransomware, and Why Now?
According to Shpantzer, ransomware is a direct monetization attack against availability.
Confidentiality breaches are full kill-chain attacks — there has to be some skill involved for fencing stolen goods and indirectly monetizing the attack because it’s manual, whereas with ransomware, a grenade gets thrown in your LAN or server farm and you are instantly in a business relationship, having a conversation with the attacker.
For example, MedStar Health is a 10 billion dollar healthcare group that was affected by a server-side ransomware in 2016. Following that, they made a decision on their public website to take down all of their IT systems, effectively taking them a month or more to recover.
That time frame can severely affect not only your SLAs and costs for recovery, but also who’s getting fired. It’s critical to understand who was responsible for this, what incentives can be aligned, and how it can be prevented and mitigated.
Ransomware is a security issue, but it’s also a disaster recovery and business continuity issue, Shpantzer says. It’s important to look at your backup infrastructure and data, because backups are going to get detonated, and then the rest of your server farm will be gone. Attackers do this on purpose because they want the leverage, and because you can not restore from backup.
Major Types of Ransomware
What are the major types of ransomware, and how do they come in? Shpantzer lists the top four:
- Client-side (desktop, laptop, tablet, phone)
- Server-side (data center, cloud)
- Hybrid (client-side plus fileshares)
- Worms (Wannacry, NotPetya)
Client-side ransomware can involve your browser, an email with attachments and links, instant messaging spam through texting — tactics that try to plow into your endpoints through the weaponizing of docs and attachments. This type of ransomware deals with exploit kits targeting vulnerable tools in your browser, such as Adobe Flash and Acrobat, among other plugins. You can’t just patch your OS and your browser, you have to patch all the plugins that are vulnerable and directly touching the malicious stuff on the web.
With server-side ransomware, the method is manual hacking where attackers come in through the data center or cloud. Server-side attacks will get opposition inside your data center quietly, do a little recon, and grab some credentials. Attackers then pivot internally, enumerate servers, target the backup infrastructure, and then detonate.
Hybrid ransomware is client-side that jumps onto file shares or servers and anything network accessible — like a database — that has an open network port visible from the client. Hybrid attacks are very common in the sense that someone in an accounting department could just click on a fake invoice and their fileshare blows up.
Lastly, and more recently, we’ve seen worms that are seeking a ransom. Wannacry, NotPetya, and others, are a little bit of client-side and a little bit of server-side. Worms are not manual, and when an attack hits you’re going to be chasing the clock. The main thing with worms is understanding how you are going to prevent an initial infection from destroying the rest of your company, which calls for segmentation, segregation, and understanding how lateral movement works.
Prevention Strategies
Spear phishing is becoming more advanced, and attackers know everything about us — they have all the analysis tools to know who we are, who we work for, and who we talk to. You can have 100 percent effective awareness and still get infiltrated via your browser, or through an attacker using a real email account to send a weaponized file or link.
Having the correct prevention strategies in place can ultimately save your organization time and energy in being proactive against ransomware attacks.
Segmentation and Segregation
According to Shpantzer, segmentation and segregation is one of the top strategies for ransomware prevention. That doesn’t mean just network segmentation — it’s also critical to understand segmentation using identity.
Having a local admin password that is different for everybody is one proactive step to take, that way there’s no skeleton key to the entire LAN, because if one client catches fire, the rest of the network does too. To prevent that, it’s critical to segment and segregate by creating small islands using identity, network, and the hardening and patching of endpoints to bolster a much stronger defense.
Web Defenses
With email servers, you can obtain a lot of useful threat intelligence about exactly what new mechanisms are out there, how attackers are embedding things in documents, and how they’re rewriting attachments, allowing them to take over websites and distribute malware. Knowing this, it’s critical to understand how to inspect and strip content and attachment types in your email servers.
Browser app hardening is another important defense, especially with Adobe Flash and PDF readers being at risk. Shpantzer suggests patching, or better yet, removing Flash entirely because of the risk associated with it. Few people need these macros for work and they’ve been exploited for a while now, Shpantzer says.
DNS
A lot of ransomware relies on DNS, which is essentially a parking lot for malware, so it’s critical to understand what’s out there and how to mitigate it.
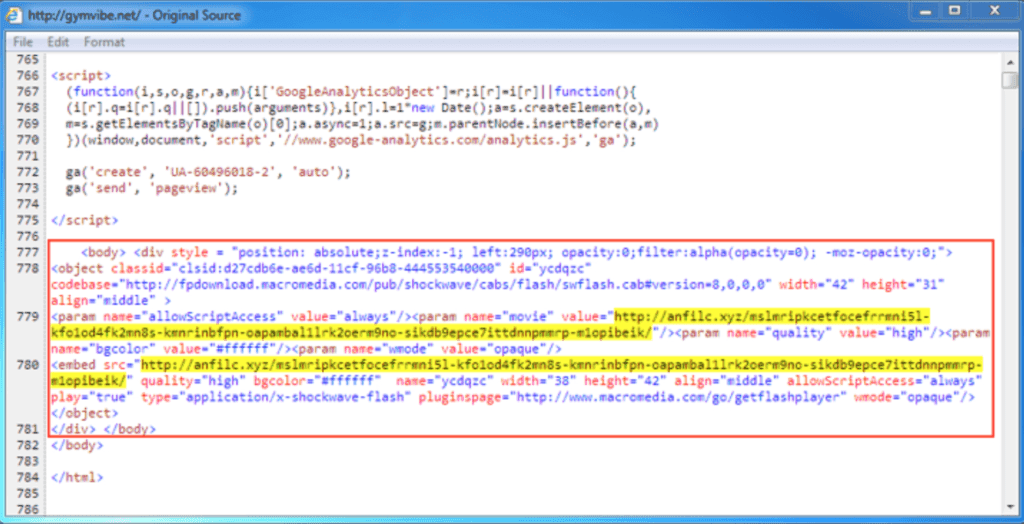
For example, a DNS redirect from an otherwise decent website can go to a .XYZ domain. When a user goes to the website, they get their browser hijacked, and suddenly they are infected with ransomware.
There are over 1,500 DNS TLDs (top-level domains), and the vast majority of them have no business context to your servers, printers, or other network devices. In many cases, they don’t even have context to your endpoints that are used by people. How many of these are you allowing on your client, server, or printer networks? If you don’t know, you’re probably allowing most of them, if not all.
Fight the Threat
It’s critical to prevent initial infection, mitigate the spread, and detect and respond aggressively to any incidents. Pregaming those actions with good communication with executives across information security and IT will only bolster your defenses, Shpantzer says.
How else can you can better fight against ransomware threats? Well, according to Allan Liska, with good threat intelligence.
Allan Liska is a threat intelligence analyst at Recorded Future. Liska has more than 15 years of experience in information security and has worked as both a security practitioner and an ethical hacker, and he’s also the author of “Ransomware: Defending Against Digital Extortion.”
There are two ways that threat intelligence enables better security, Liska says. The first is that it helps organizations identify the known bad, and the second is that it also helps find the unknown bad or the potentially bad. However, it’s important to understand that just because you have a list of the known bad, such as IPs, domains, or file hashes, that doesn’t necessarily make it threat intelligence. The context missing is how these indicators are tied to specific ransomware attacks, because there are very different actions that you can take.
As far as paying a ransom goes, Liska recommends you don’t. Paying the ransom fuels more ransomware, and sometimes you don’t get your files back. Knowing that specific types of ransomware are built by attackers that don’t give the files back, or that the ransomware itself is so broken you won’t get your files back even if you do pay the ransom, is critical because that helps you take the right action.
Indicators associated with different ransomware families should be integrated into your existing systems, because tying that threat intelligence into a SIEM or TIP can help you take more practical action with it post-threat, or possibly, pre-threat. Indicators can even be pushed down to different types of end-point platforms, hopefully stopping an attack in its tracks. The idea is to incorporate threat intelligence into your existing workflow so that you’re able to operate more efficiently.
New Methods of Attack
You want to be able to use threat intelligence as a research tool too, right? But what are up-and-coming threats, and what are the developing types of ransomware attacks? Understanding these methodologies and how the attack flow works will make you more able to protect your organization against it.
Liska shares a stat from Kevin Beaumont, a security researcher who says one out of every three ransomware attacks disguised as phishing emails are now using the dynamic data exchange (DDE) as delivery method. This type of ransomware is especially intriguing to attackers because so few organizations are protecting against it.
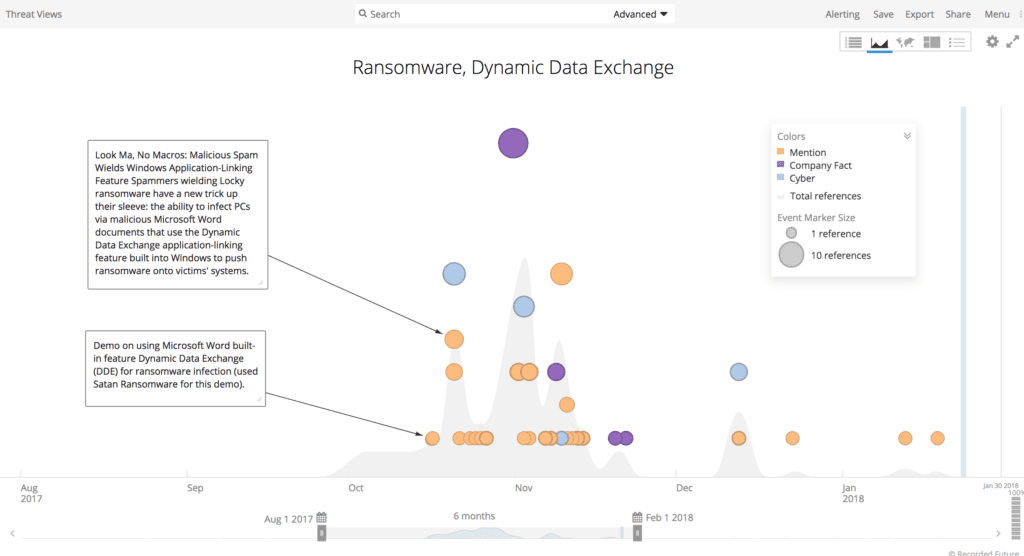
As an example, the timeline above shows ransomware specifically using DDE attacks. On October 16, there was a built-in feature of a Microsoft Word demo using DDE for a ransomware infection, using the Satan ransomware. That was a proof of concept and a demo, and less than a few days later, Locky was using DDE in live attacks. The group behind Locky is active and aware of new types of attacks, and they quickly incorporated that methodology into their delivery system, plugged it into their phishing exploit kit, and started sending out millions of emails at a time, all with these Word documents that have DDE.
If you’re tracking this type of activity, you’d be able to make sure you had the necessary protections in place. Threat intelligence helps you take steps to make changes to protect your organization and make better decisions not only on attacks that are happening, but attacks that are coming in the very near future.
Related
