How Iran’s Government Gags and Frees Media’s Cyber Coverage
As the Iranian cyber story unfolds on the world stage, a tightly controlled media has revealed what its leadership is thinking.
The Iranian government has long been known to control its press. Some news agencies are outright government mouthpieces while others attempt to deliver customer-driven content. For those independent news outlets, there exists a risk of being closed down or worse should they run a story the government dislikes.
Since the 1979 revolution, dozens of newspapers have been shut down, but in 2012 the Iranian government reportedly introduced a text messaging system designed to notify journalists when not to report on a late-breaking story. While this notification system has likely been convenient for the Iranian government, it has also been helping Iran-watchers track Iran’s decisions as world events unfold.
One of the more important developments over the past two years has been Iran’s emergence as a cyber actor alongside China and Russia. Using Recorded Future, we can bring together seemingly unrelated data points and information signals to illustrate larger trends, especially within the realm of cyber security.
Establishing a Baseline
Iranian media generally follows the world news cycle, and like most news organizations is incentivized to maintain a healthy circulation to ensure a profit. For obvious reasons, Iranian press will favor more regional events, but like the rest of the world Iranian news consumers are interested in cyber security.
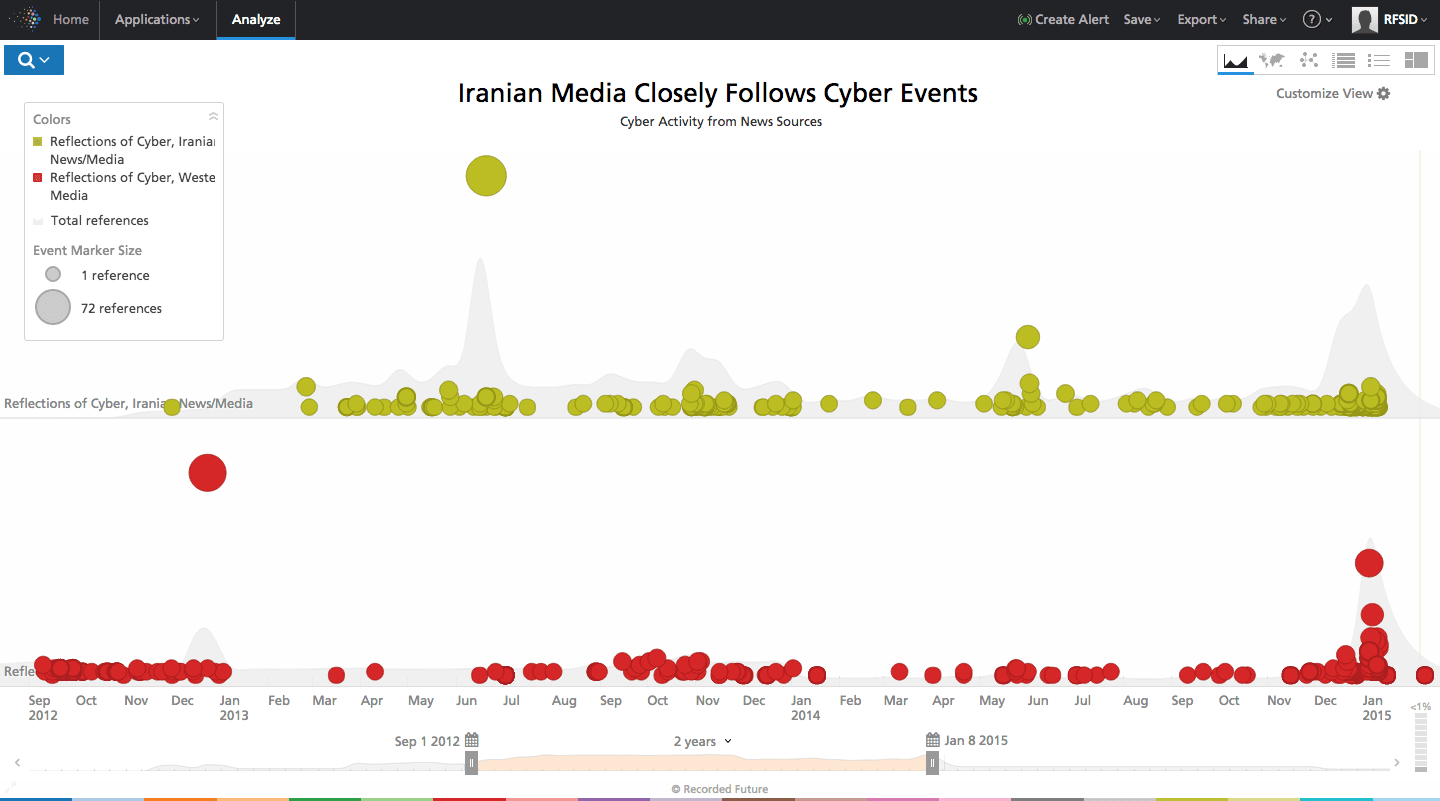
Click image for larger view
One such story was the reported breach of the US Postal Service by Chinese Hackers. Not only did government-approved press report on the event, but also released it at the same time.
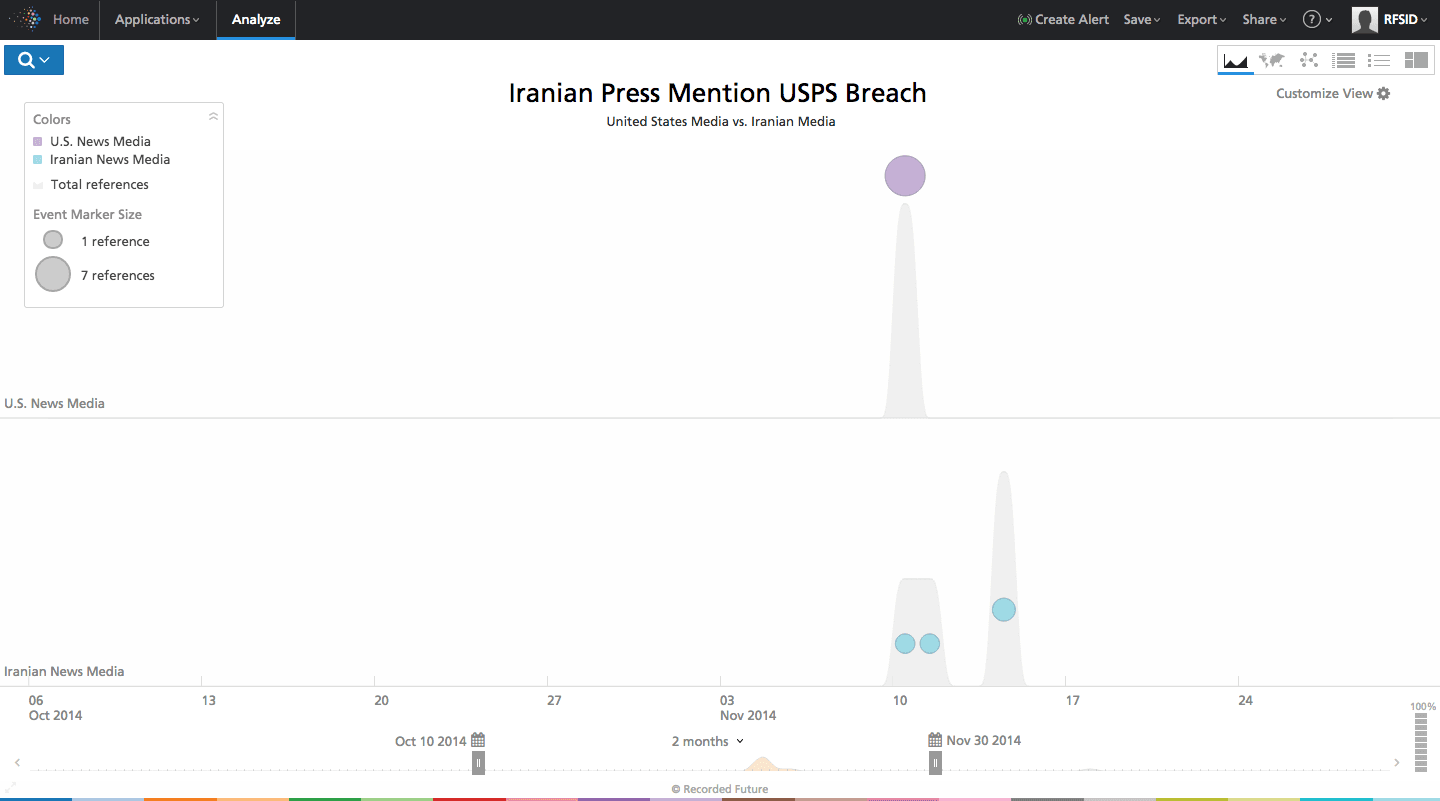
Click image for larger view
When it came to reporting on a downed US drone, the RQ-170, Iranian press immediately reported it. Long after the US news cycle lost interest, however, Iran’s press kept the story in play. This went beyond simply reporting the news, since there was little to add. The heavy syndication was indicative of the Iranian government’s desire to go beyond informing and influence its constituency.
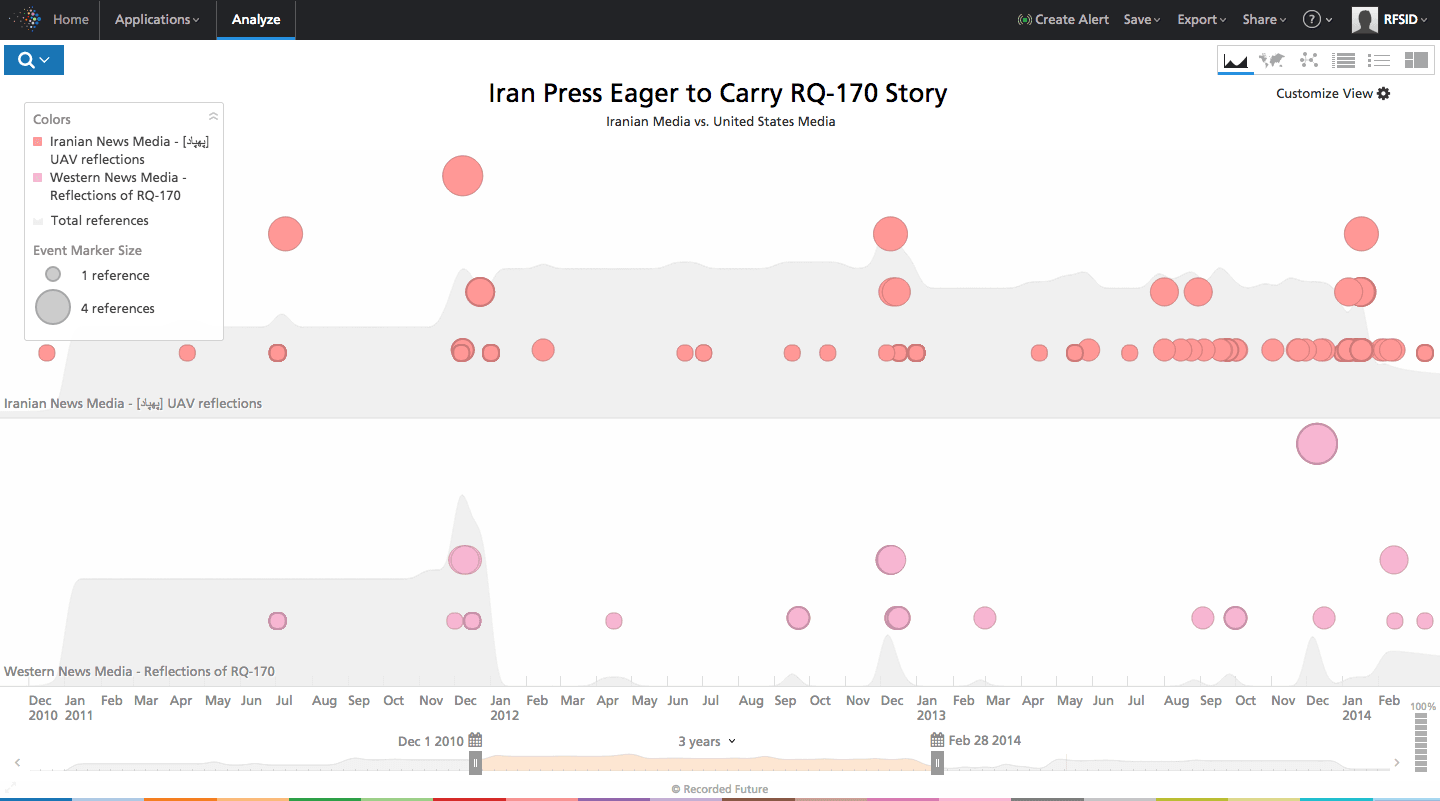
Click image for larger view
Something to Hide
In August of 2012, a devastating destructive cyber attack using the Shamoon malware destroyed over 85% of Saudi Aramco’s client hardware. This cyber attack was one of the worst ever against a company, and it took almost a month for Iranian press to cover the story and, even then, only in English. Compared to Western news outlets, the Iranian media was clearly under reporting the event. A few weeks later, the same malware struck RasGas – a Qatari natural gas company.
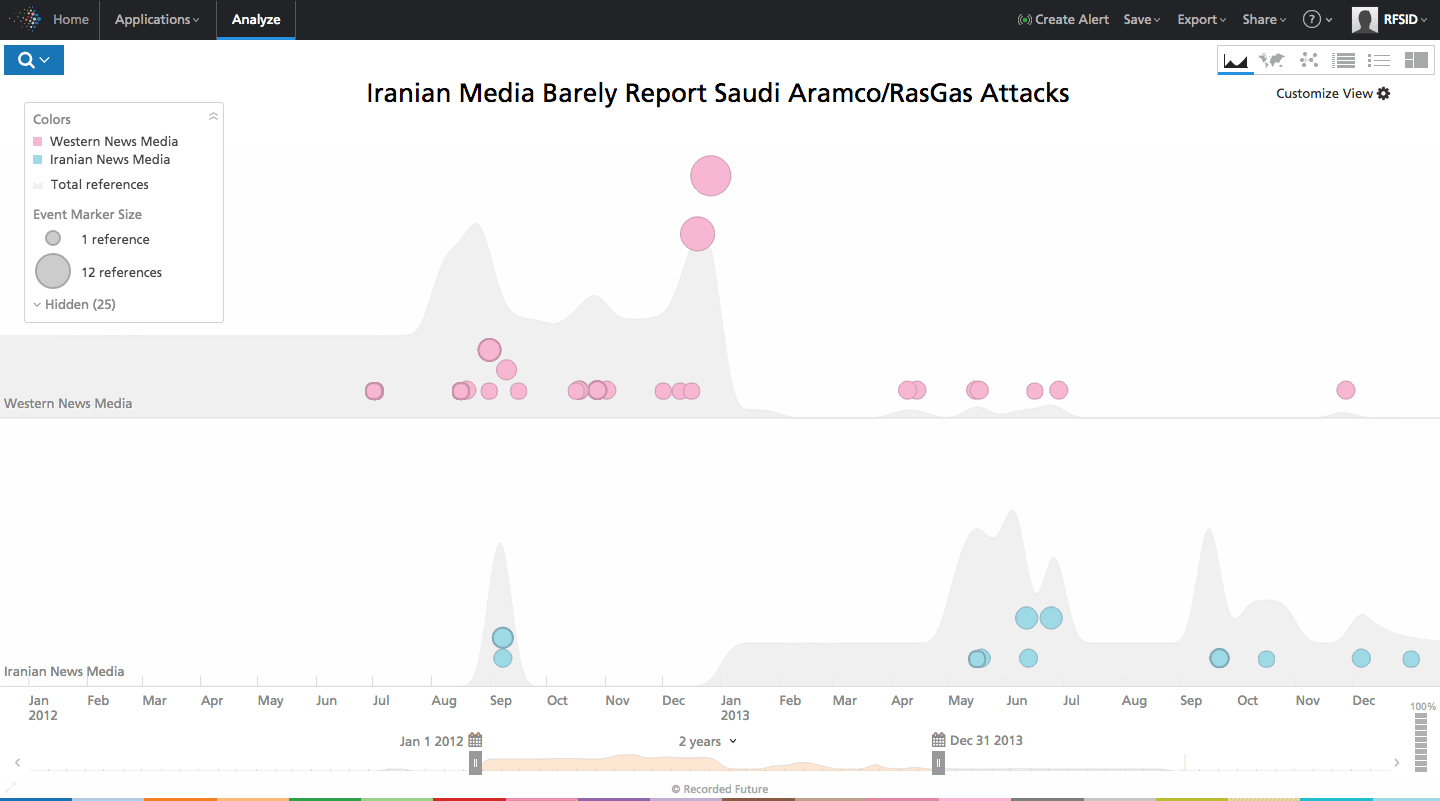
Click image for larger view
Additional research by cyber security companies suggests the Iranian government was involved, but even in 2012 the data revealed Iran was trying to hide something. By issuing gag orders on their media they tipped their hand – and when we contrast different views on Recorded Future that pattern is evident.
Soon after the attack on Saudi Aramco, hackers began a campaign they called OpAbabil targeting US banks and financial institutions with distributed denial of service attacks (DDoS). Again, the attacks received significant attention from US media, however Iranian press didn’t cover the story until spring. Incidentally, around the same time Iran’s press also began reporting on the Saudi Aramco and RasGas attacks.
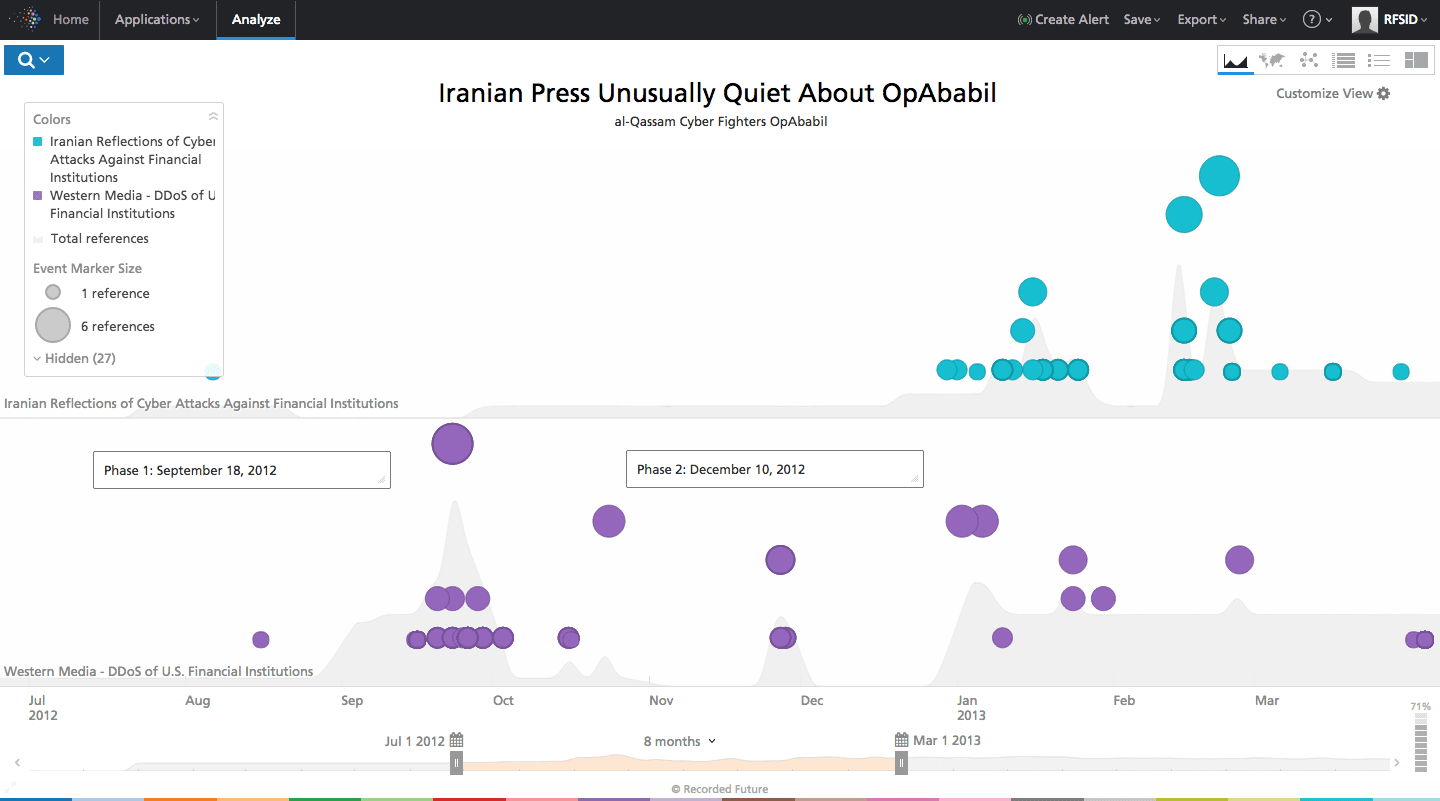
Click image for larger view
Changing Tack
In the Spring of 2014, Iranian press began covering cyber events in which the Iranian government was suspected. The first was significant – the Wall Street Journal published an article detailing the compromise of the US Navy’s unclassified networks, reportedly one of the largest in the world. It appears Iran was more confident, and like the story of the RQ-170 drone, it wanted internal recognition. After all, the US reportedly attacked Iran’s nuclear program via a cyber attack – breaching Navy networks was likely perceived as justifiable – why not let this story circulate internally too?
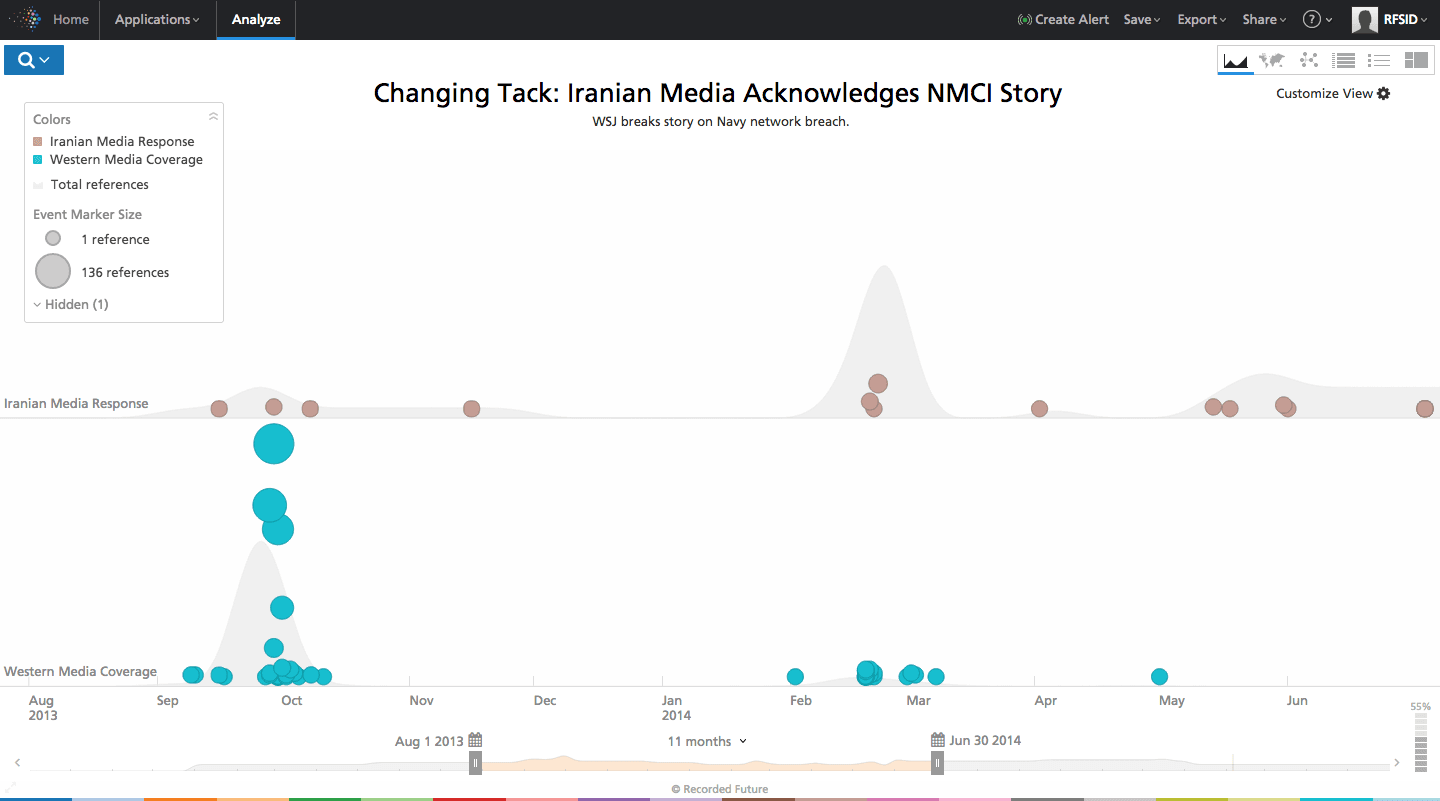
Click image for larger view
Six months later, two cyber security firms published detailed reports on cyber attacks against the US. The first, named Saffron Rose, targeted the US defense industrial base. The second, called NEWSCASTER, was a social media/hacking campaign targeting high-level individuals in the US. Iranian media controllers did not mind these reports circulating either.
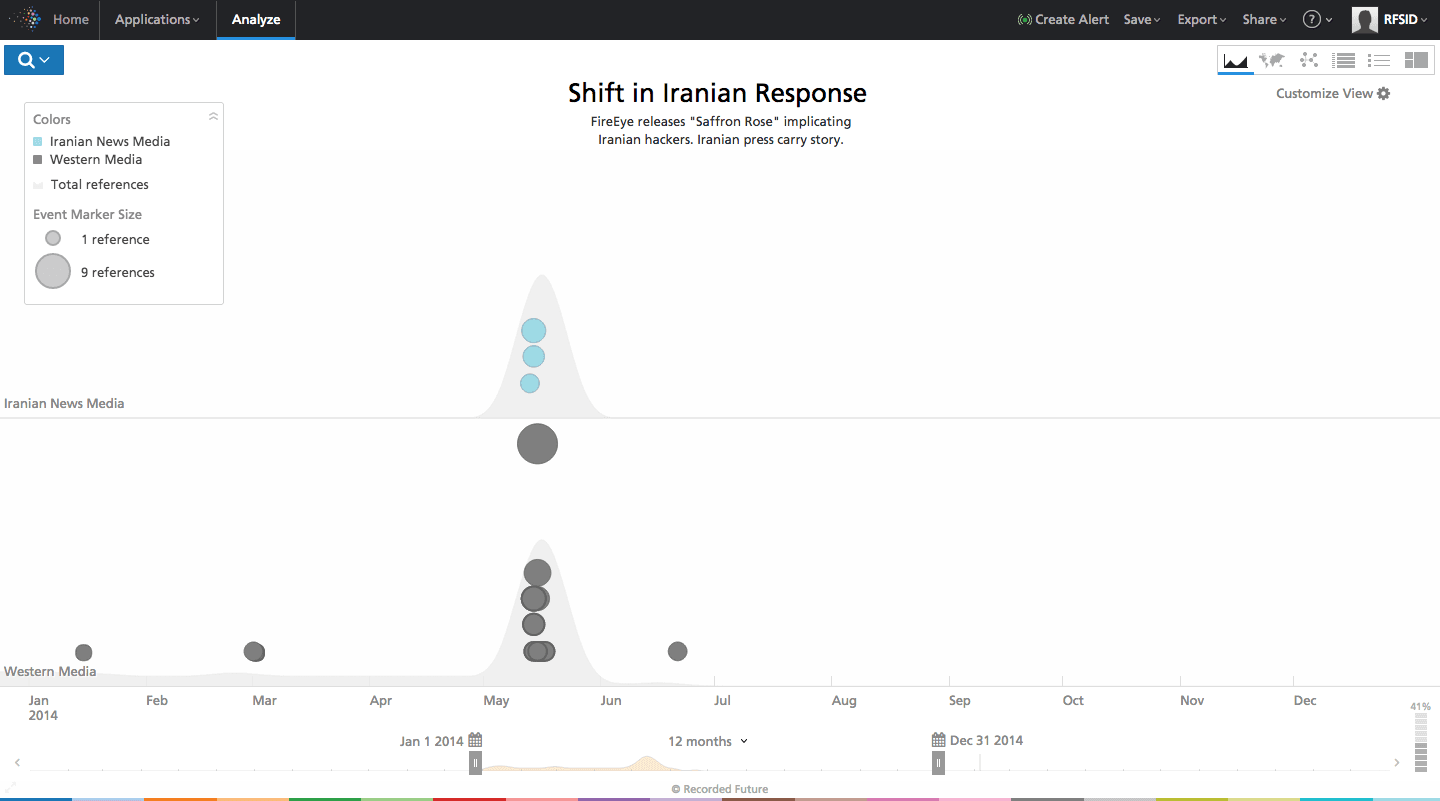
Click image for larger view
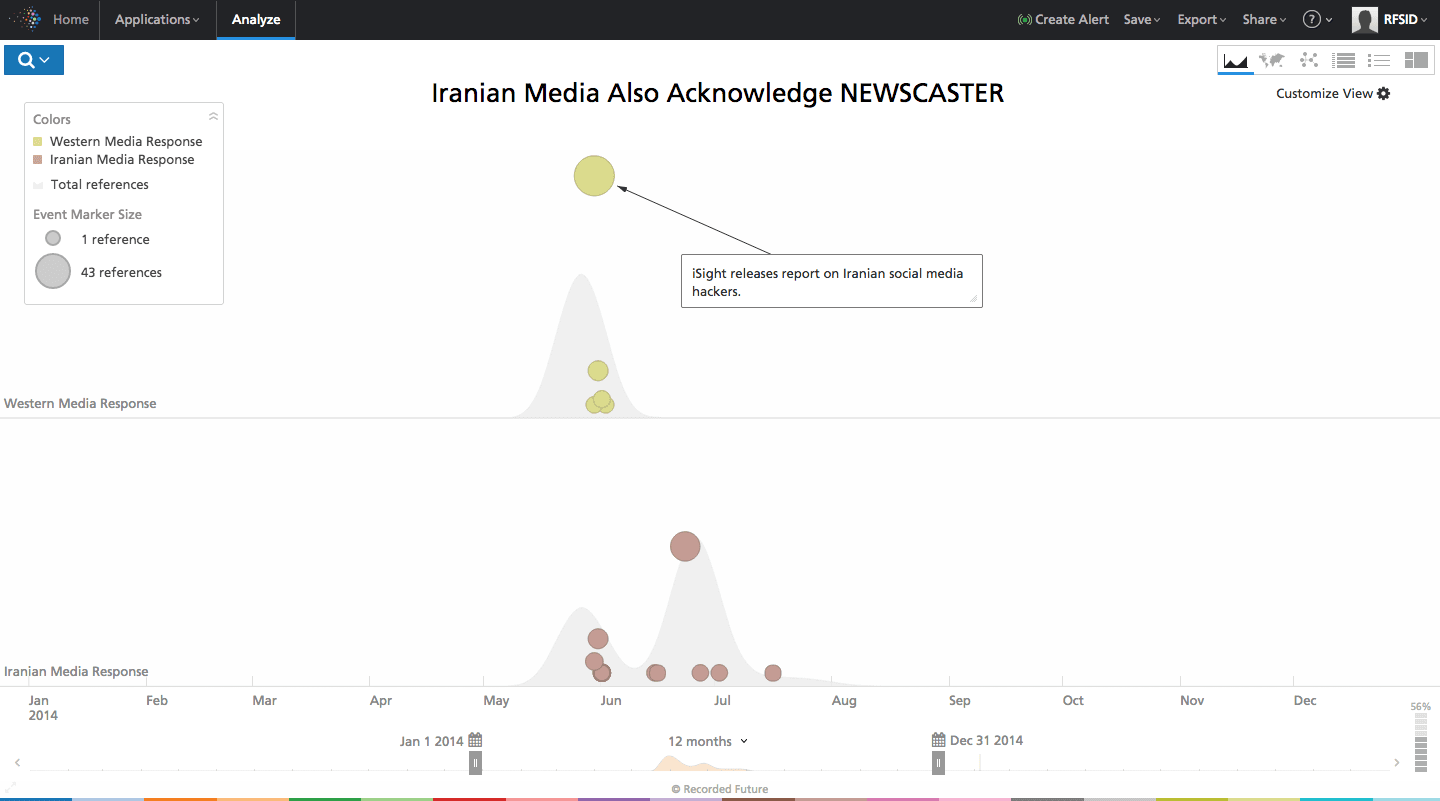
Click image for larger view
The last significant cyber report on Iran, however, did not seem to resonate well with Iranian censors. Released in December of 2014, the Cylance OpCleaver report asserted Iran was waging a comprehensive cyber campaign against the US, among other countries. The scope and breadth of targets, to include civilian targets such as airlines, appeared to be too sensitive for the government. As evidenced by the chart, Iranian press did not reference the story at all.
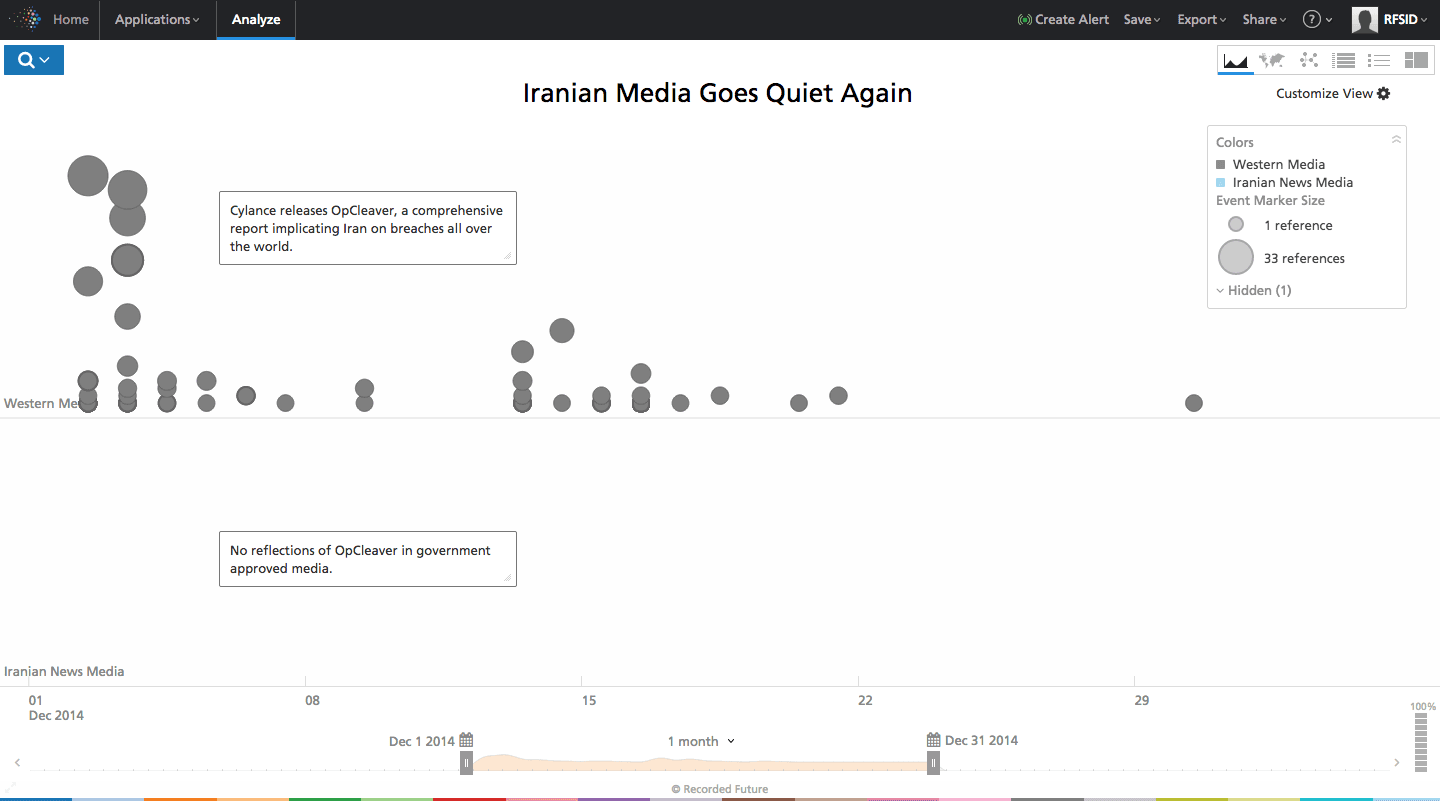
Click image for larger view
Capturing Trends
Using threat intelligence from Recorded Future, we are not only able to keep abreast of significant cyber stories, but see larger trends and patterns unintended by their sponsors. As the Iranian government makes future cyber moves, we can continue to follow their actions and comfort level, both abroad and internally.
Related
