Iranian Hackers’ Rising Interest in Targeting Android Systems With DroidJack, AndroRAT

The latest threat intelligence from the Web shows that threat actors on Iranian hacking forums are distinctly interested in targeting Android systems using several different variants of remote access trojans (RATs). While much of the research and reporting on mobile security focuses on widespread or critical vulnerabilities, this analysis shows how threat actors are adapting to attack popular platforms in their region, or country, with easily available tools and community support systems.
Across the range of threat actors, privately sold or open source RATs have been consistently popular choices. In the past, threat research has often identified njRAT and XtremeRAT as common variants. For example, njRAT is in widespread use for numerous criminal activities and Syrian surveillance campaigns, while XtremeRAT has been in campaigns against Israeli, Egyptian, and Saudi Arabian targets by multiple actors (e.g., SecureList, Trend Micro).
While these variants remain in common use, as recent Recorded Future research on RATs indicates, there are trends showing certain actors in the region are increasingly interested in new tools. The interest in these tools, specifically chatter around download sources, proper deployment, and features, is being primarily driven from a single community.
Looking at the last six months of activity on prominent Iranian hacking forums, discussions are dominated by interest in RATs that target Android devices. While mobile-focused malware is a growing threat, the interest also makes sense in the regional context considering Android devices comprise a significant majority of mobile devices in the Middle East.
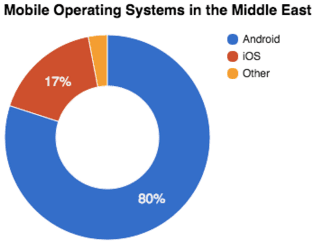
IDC mobile market share figures by operating system, July 2015.
Shown below, the initial analysis focused on filtering all forum chatter in the last six months by malware type. While conducting threat intelligence analysis using foreign language sources can be difficult, focusing specifically at tools (within those forums) makes it easier to characterize the technical sophistication and types of attacks that certain groups or sources are interested in. In this case, separating out all mentions of RAT tools was useful to assess if variants like njRAT or DarkComet were still popular choices.
As seen in the graph below, there are small bursts of interest in njRAT (also known as Bladabindi) and few conversations about DarkComet. Instead, there has been sustained and popular interest in two variants of Android RATs.
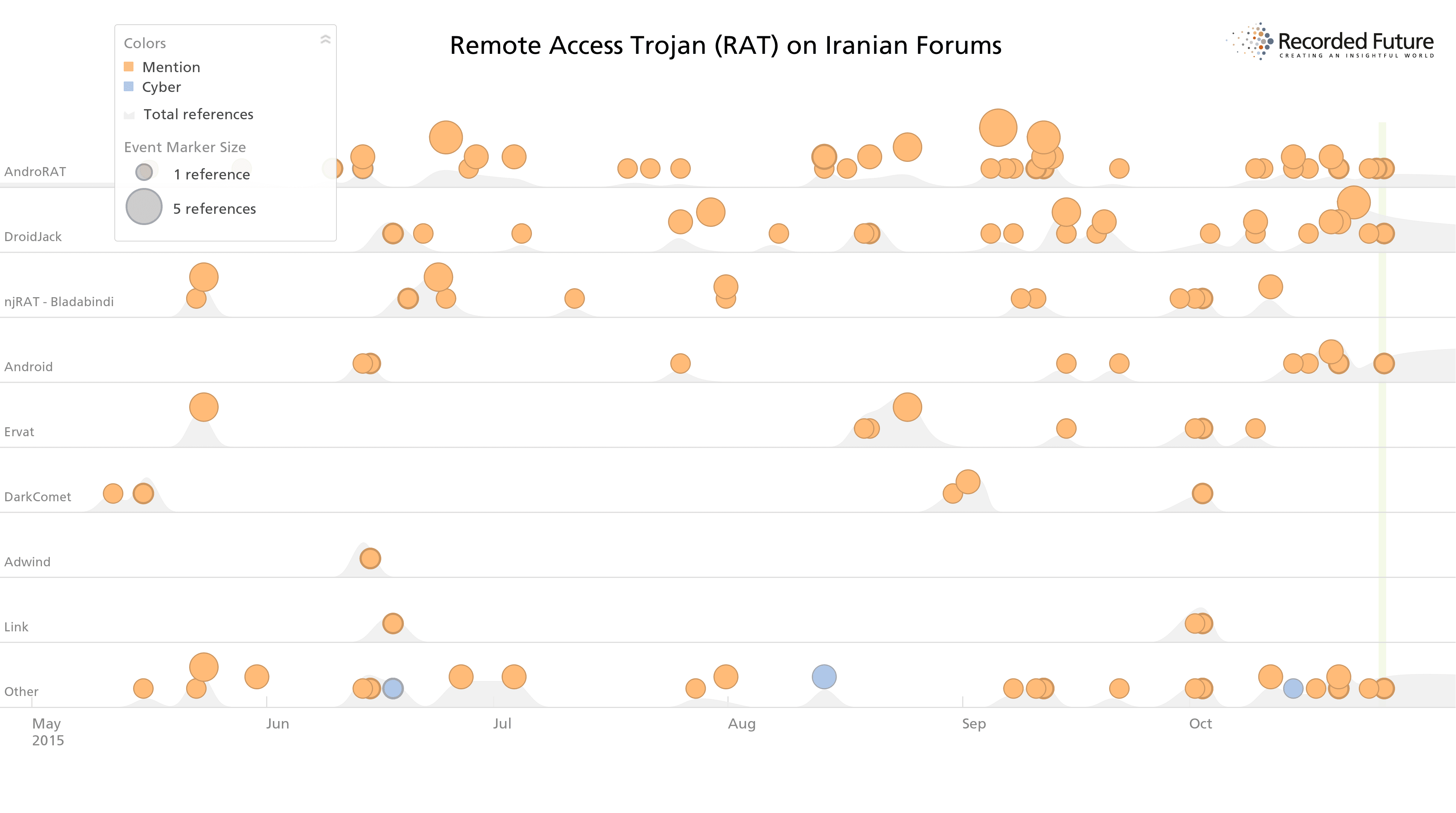
Last six months of discussions on Iranian forums show majority of chatter around two specific Android RATs (AndroRAT, DroidJack) over common platforms like njRAT or DarkComet.
If we drill down on the top two tools discussed, AndroRAT and DroidJack, we also see a time difference in when interest began. Given the origin history, with AndroRAT originating on hacker forums several years before the related DroidJack malware appeared, it follows that the forums would pick up on the originating tool first. The sustained Iranian interest in AndroRAT, despite its age and declining chatter from other sources, could be due to the easy download access, including GitHub repositories, and available community support for deploying the malware.
The two RATs in particular, AndroRAT and DroidJack, are likely popular among hacking forum members due to the same reasons as njRAT – open access to download or purchase, strong community support, and ease of use.
The malware history is linked to the same family, with AndroRAT originating on hacker forums in late November 2012. The malware possibly originated from open-source posted online, with a GitHub repository for AndroRAT dating back to the same month. A variant of the AndroRAT malware named SandroRAT was available in 2013, found in campaigns targeting Polish banking users, which the authors transitioned into DroidJack in 2014.
All variants come with dozens of features, including the ability to intercept SMS messages, contacts, call logs, browser history, and user credentials on visited websites.
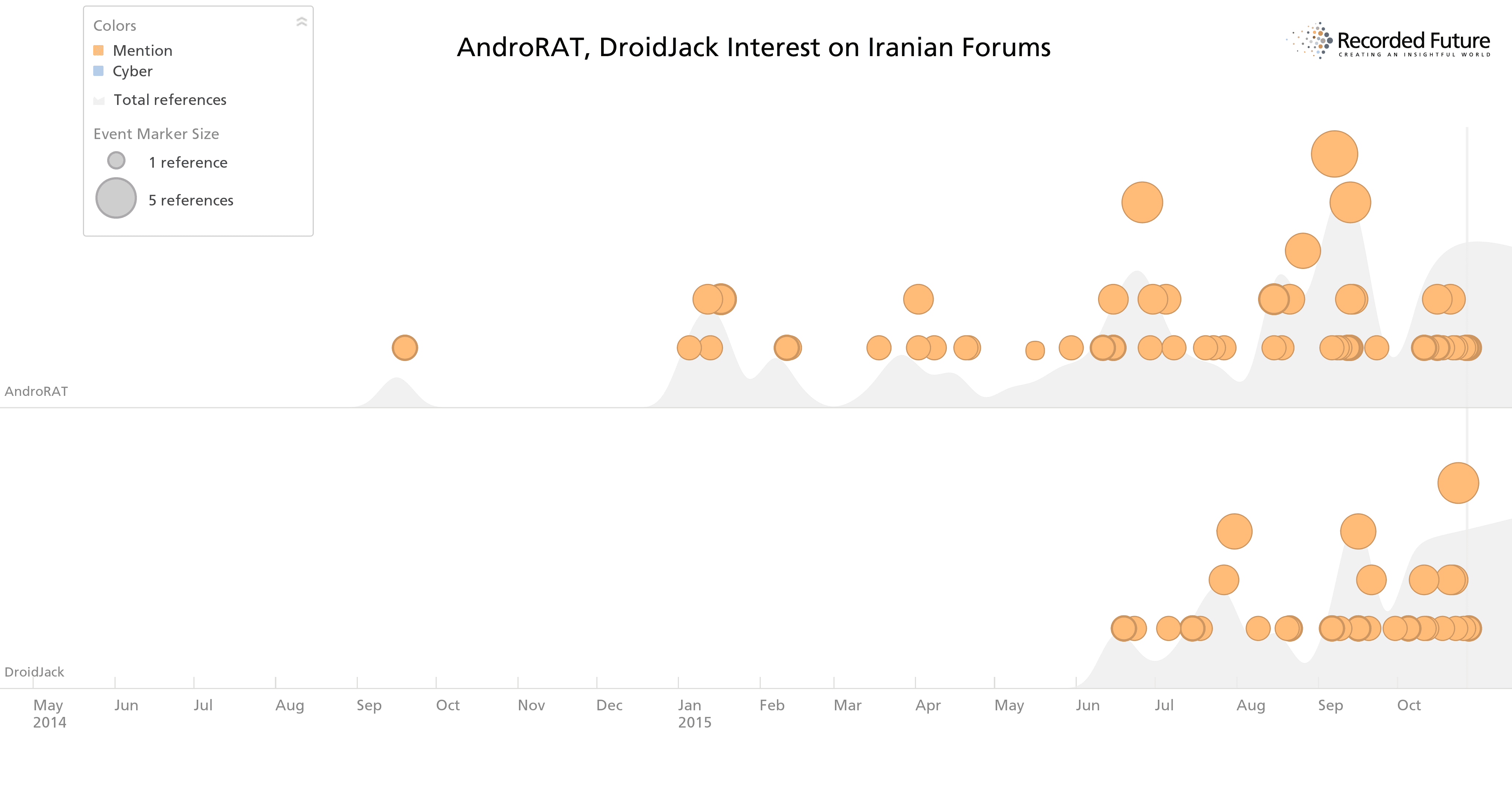
Forum chatter on both tools since May 2014.
Taking a step back, the past year of activity around both tools shows that the Iranian hacking community comprises most of the open chatter compared to other hacker forums, on the open or dark Web.
The second figure below also shows how this trending interest is an outlier among most sources discussing RAT use and activity. The three-month gap between first reporting, represented in the initial cluster of activity, and later conversation among hacking forums and social media is also notable. That most hacking forums have not picked up on these tools, and Internet-wide chatter has significantly dropped in the last year, makes the Iranian interest more of an outlier.
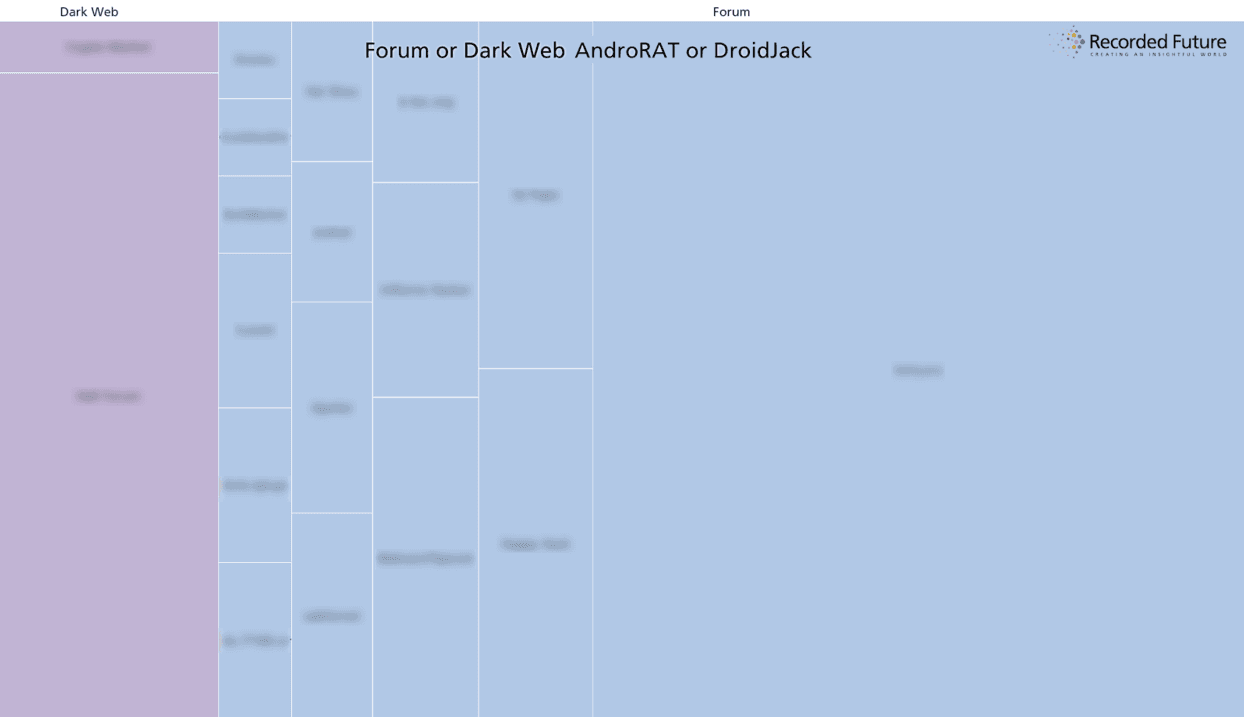
Past year of all hacker forum activity for both tools, from open and dark Web sources.
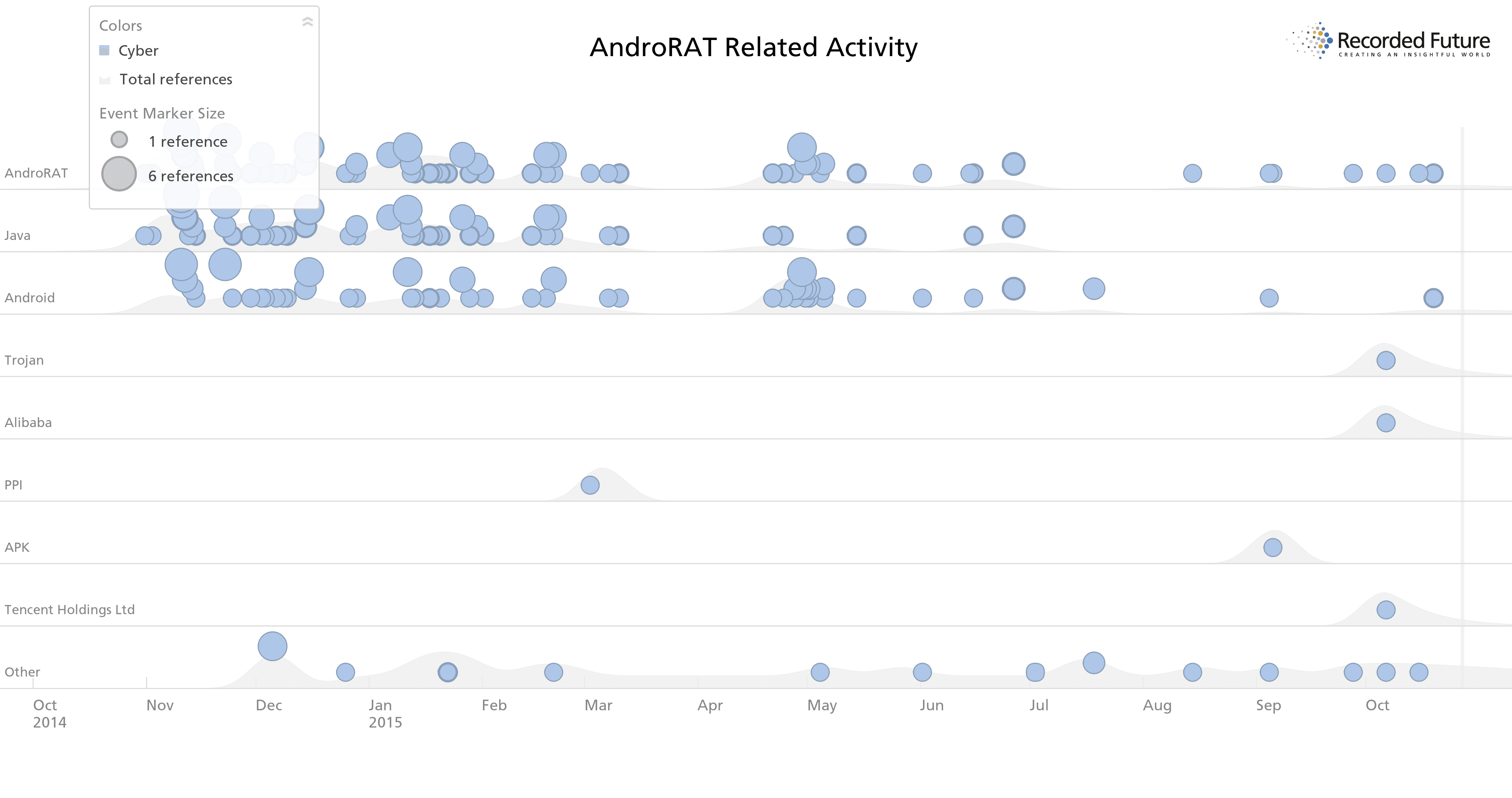
The past year of AndroRAT activity shows declining interest from most sources.
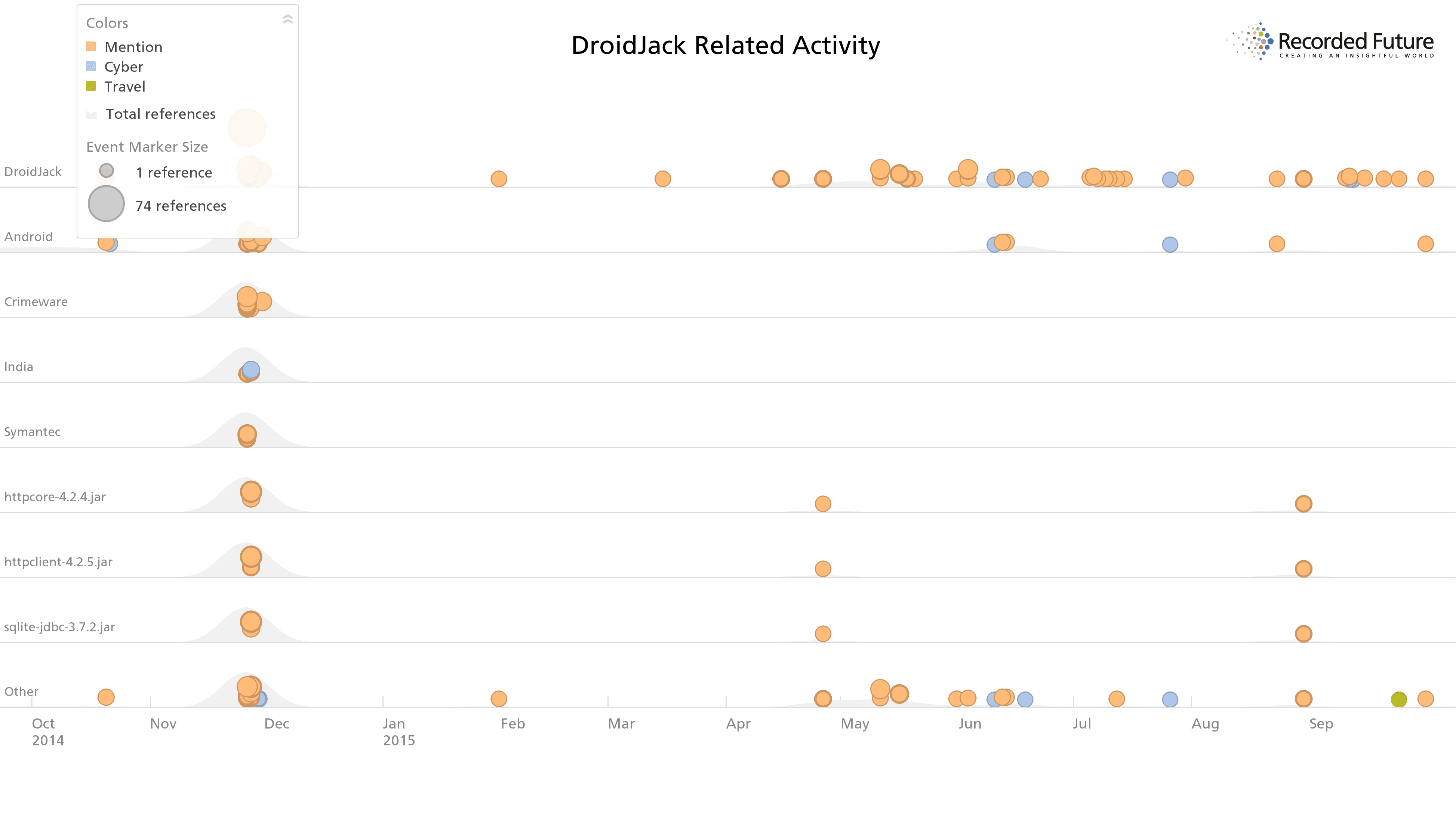
DroidJack interest across Internet sources saw initial interest, a three-month gap, and sustained interest primarily from Iranian forums.
Today, users can still find multiple for-purchase sites for both tools from basic search engines. Recorded Future research found samples available for open download across multiple hacking forums as recently as September 2015. Samples were also found on open download sites, including forked versions on GitHub.
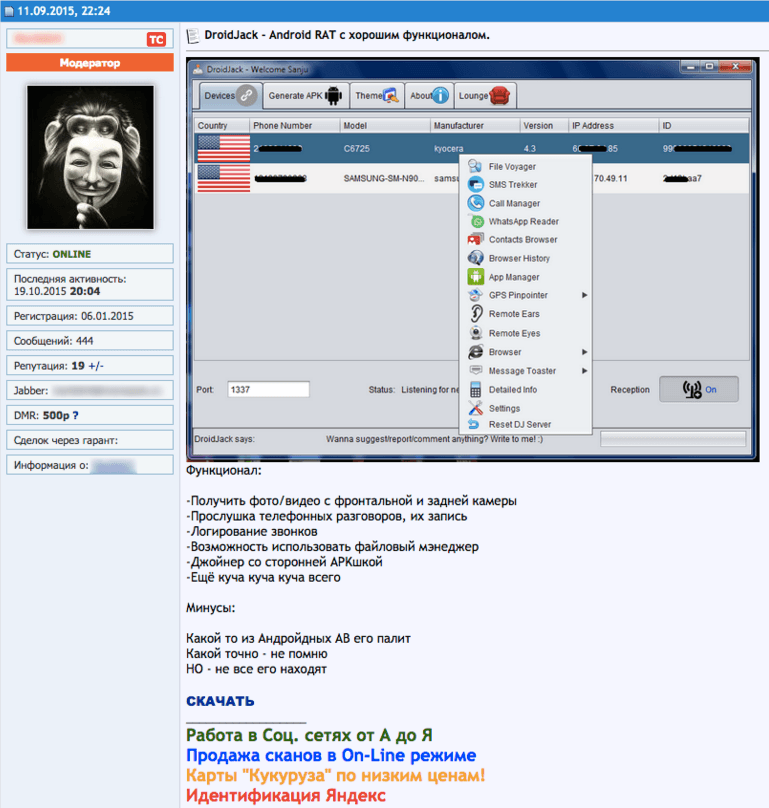
Russian hacker forum with DroidJack download links and list of features, September 2015.

DroidJack versions with support available, for sale on the open Web.
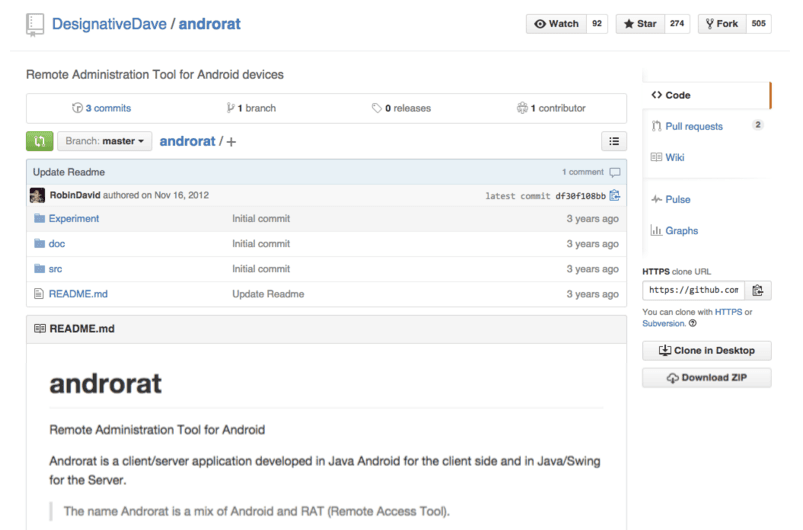
AndroRAT source code has been available on GitHub since 2012, with multiple forks.
Final Thoughts
DroidJack and AndroRAT represent a minority of total RAT activity, but the analysis illustrates the nuances of conducting threat intelligence at Web-scale. While previous research by Recorded Future showed a variety of popular choices, like njRAT, drilling down on particular actors demonstrates certain regional or even forum-specific trends which provide rich context.
With a low level of technical skill needed, open availability, and strong community support on hacker forums, DroidJack and AndroRAT are likely to remain popular choices for threat actors seeking to take advantage of Middle Eastern mobile systems.
These trends match the general nature of cyber criminals who often seek to attack platforms that are popular in the market, like PCs, from which they have a larger pool of targets. As Android currently comprises a majority market share – in regions like the Middle East, Asia, and Africa – and continues to grow, we’ll likely continue to see growing interest and new mobile malware campaigns in these regions.
Related