Rapidly Discover IOCs With Maltego and Recorded Future

Webinar: How to use Maltego for better insight into cyber threats. Watch now.
Discovering and validating known indicators of compromise (IOCs) can be a daunting task for any cyber security operation. This is especially true if you do not have the luxury to pay for all of the costly closed source premium intelligence feeds, cyber threat intelligence reports, or various IDS/AV signature sets offered by a growing number of cyber security vendors.
Building out a comprehensive set of quality IOCs in order to enhance your detection and attribution capabilities is key to your success. The security analysts needs the ability to quickly determine if a digital artifact contained in a SIEM alert from the IDS or proxy firewall is malicious or benign in real time. Doing so could make the difference between an undetected system wide breach that causes irreparable damage to your organization’s public reputation and successfully short circuiting a multi-stage attack or better, preventing the adversary from gaining access to your network in the first place.
It’s for this reason we’ve developed our Recorded Future Maltego transform set (currently in beta).
The goal of our first set of transforms is simple - make it as easy as possible for the security analyst to discover and validate known IOCs in the vast expanse of online open source intelligence (OSINT) while simultaneously giving him or her a unified view and streamlined workflow between Recorded Future and Maltego Carbon.
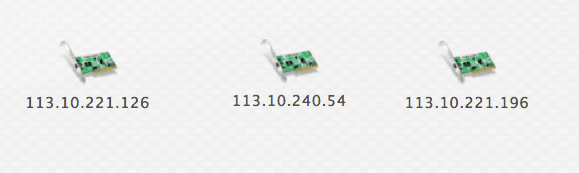
For example, say I have been alerted to suspicious network traffic originating from within my network, destined to the following IP addresses:
113[.]10[.]221[.]196, 113[.]10[.]221[.]126 & 113[.]10[.]240[.]54
I have to make a very quick decision. Are those IP addresses good or bad and what else does the world know about them?
I can easily cut and paste the three IP addresses into a Maltego graph and use them as the root of my investigation.
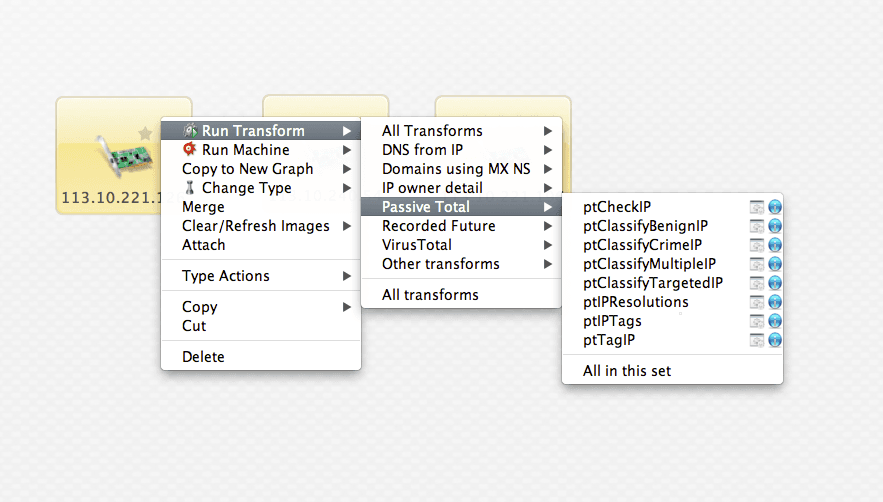
I might first use a complimentary and very nifty PassiveTotal Maltego transform set (described in more detail here) to resolve the IP addresses without worry of attribution.
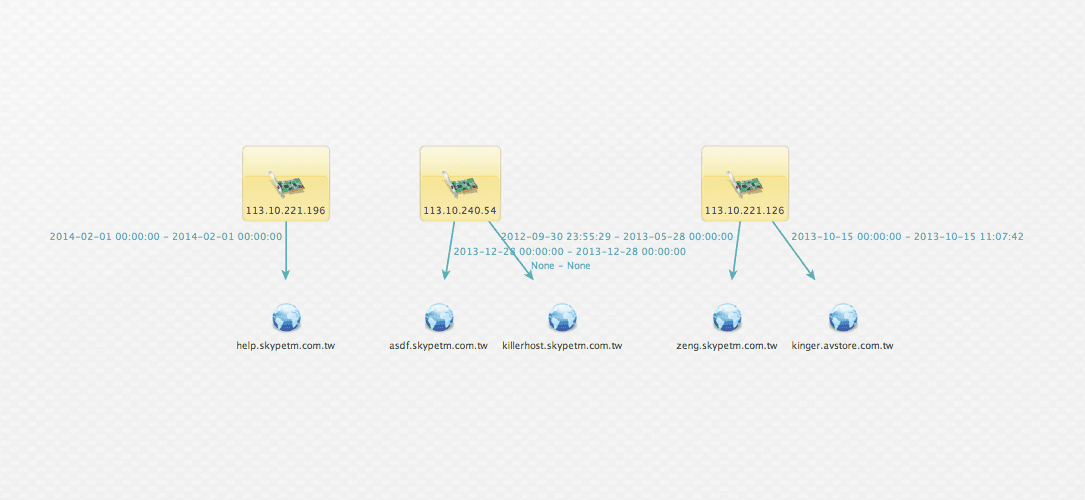
Running this transform results in five distinct domains related to our IP addresses in our graph. (Note the .tw TLD on all of them.)
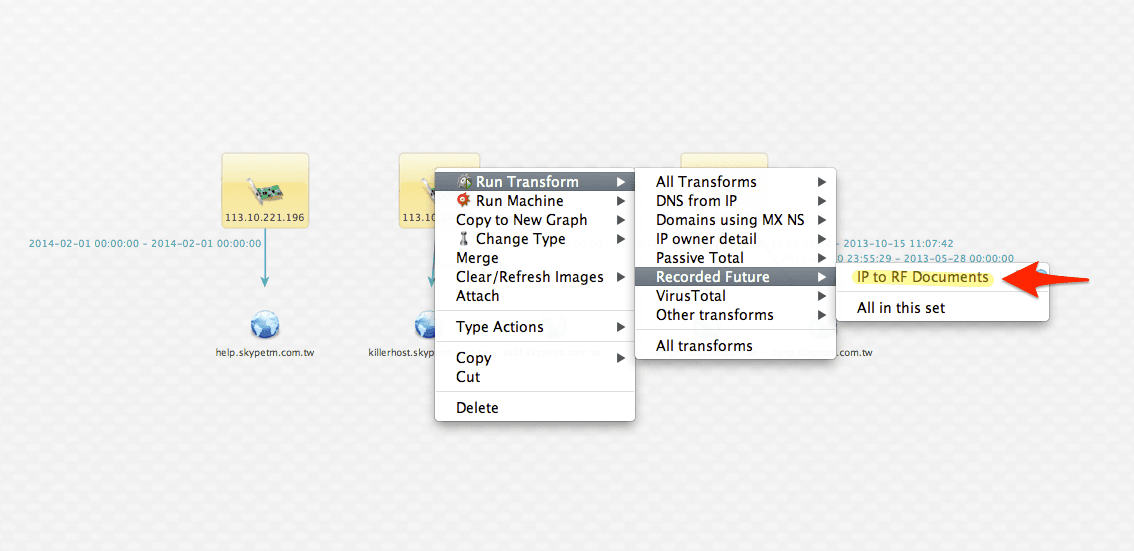
My next step is to check if Recorded Future has already mined references to these IP addresses for me. I can do so instantaneously with a single click.
My transform returns two separate documents containing the IP addresses in question.
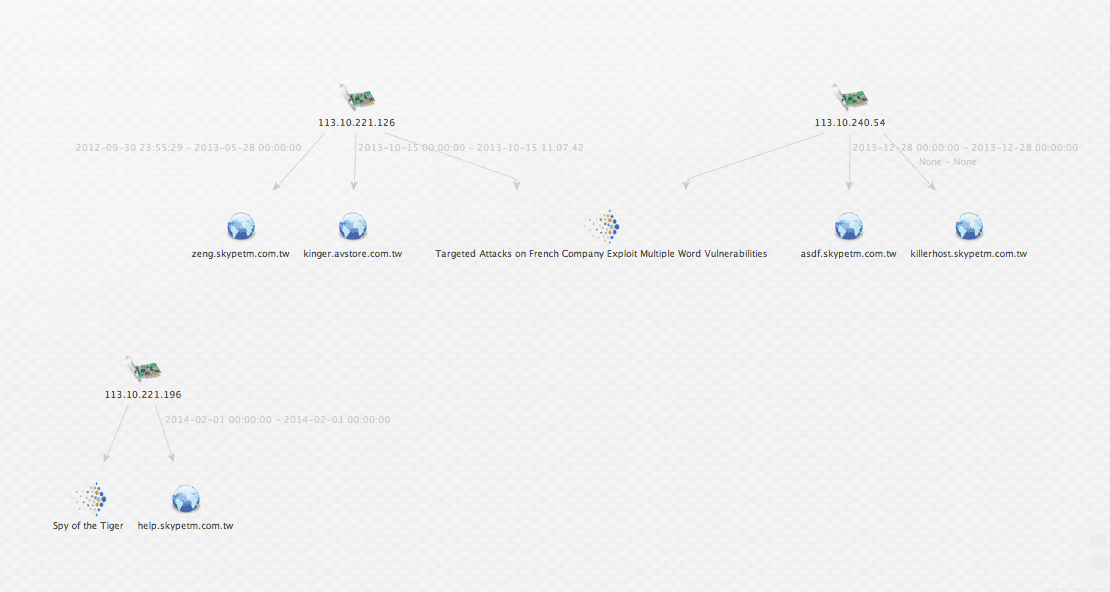
Since PassiveTotal has given me more domains to work with, I’ll want to see if I can find reference to those domains in Recorded Future as well.
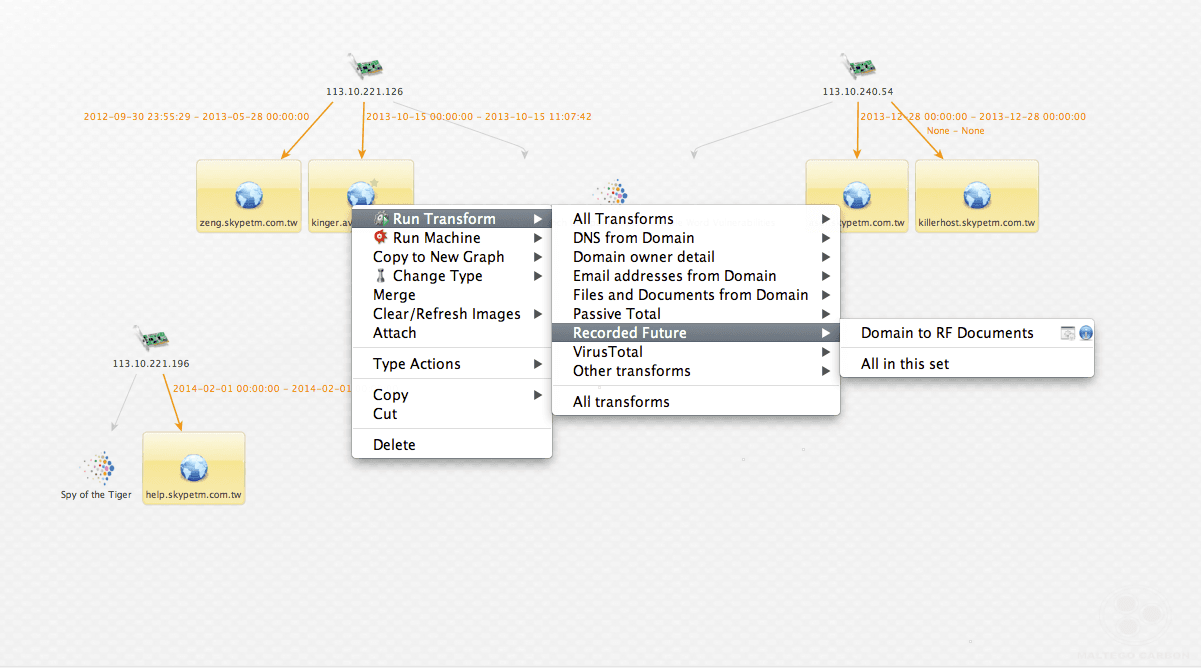
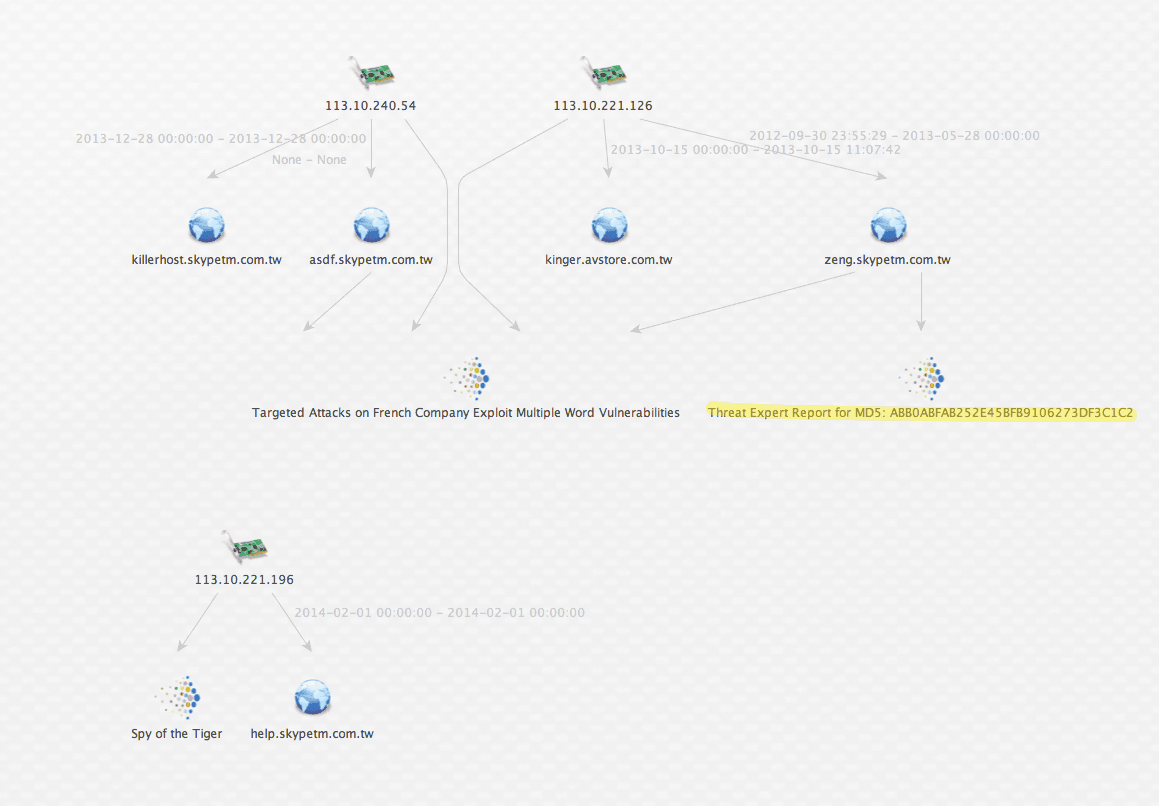
Not only do I find a new Recorded Future link, but I notice one of the domains from PassiveTotal is now linked to two Recoded Future links.
Next, I’ll want to validate the source documents and ensure they contain legit intelligence. Fortunately, Maltego also makes this as easy as one click.
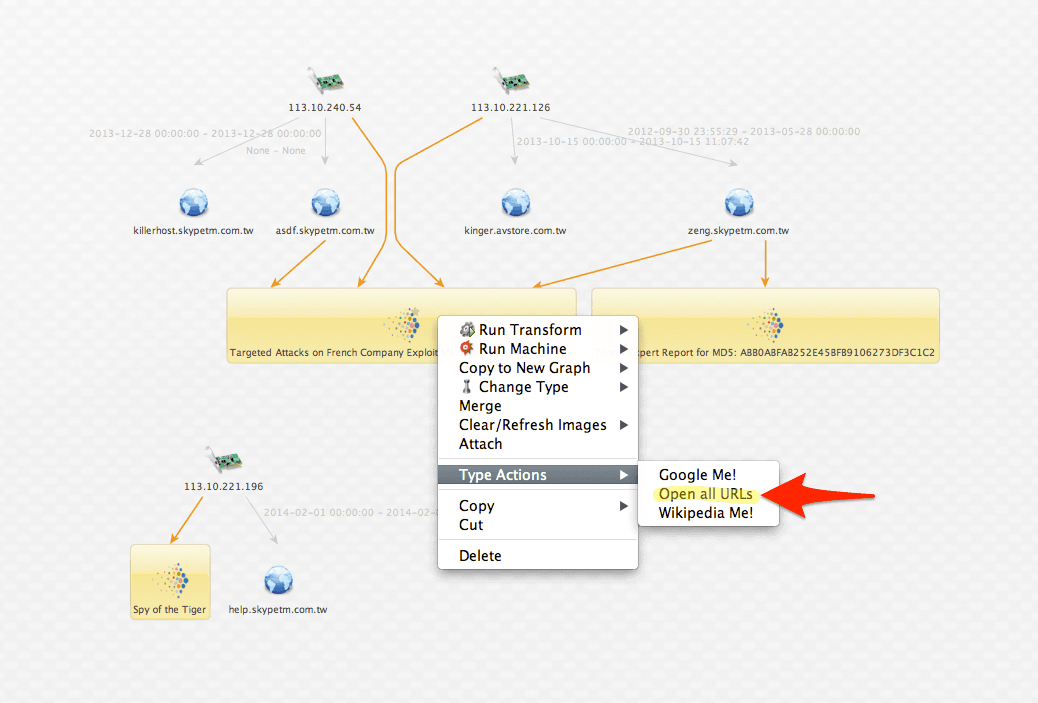
Upon opening the URLs I find a:
- McAfee blog post titled, "Targeted Attacks on French Company Exploit Multiple Word Vulnerabilities."
- FireEye blog post titled, "Spy of the Tiger."
- Threat Export report titled: "Threat Expert Report for MD5."
All three prove to be excellent write ups and good sources of intel. Additionally all three mention the chinese hacking group known as "PittyTiger" and contain within them IOCs attributed to that group including the IP addresses I’m investigating.
Now for the really fun part. My next step is to extract the IOCs that Recorded Future has already mined from those sources and made available to me for light speed retrieval via a simple API call or in our case, a Maltego transform.
(Note our current transform set can extract nine different indicator types and this list will grow.)
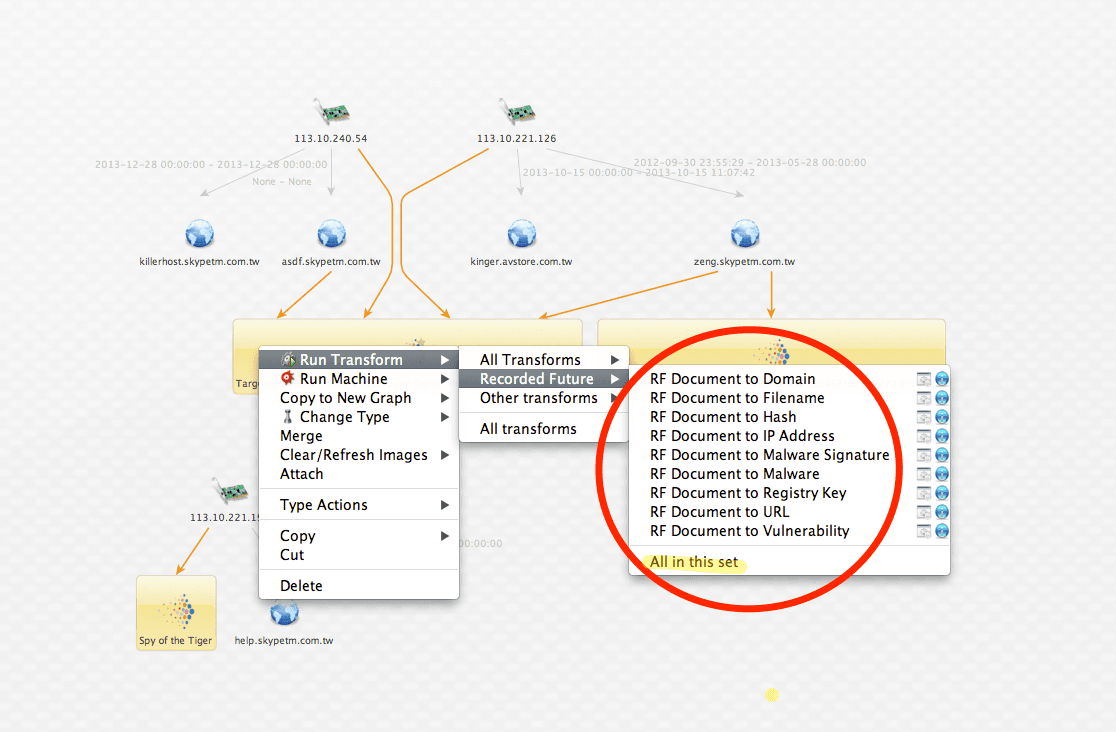
The result is not only a rich set of IOCs associated with our IP addresses but notice I now have linkage between all three Recorded Future document entities.
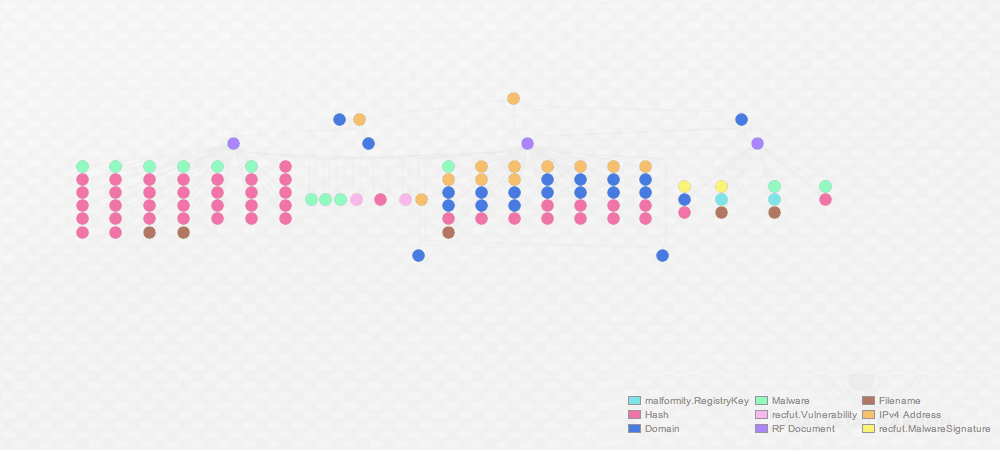
Now let me zoom in and take special note of the linkage between the following entities.
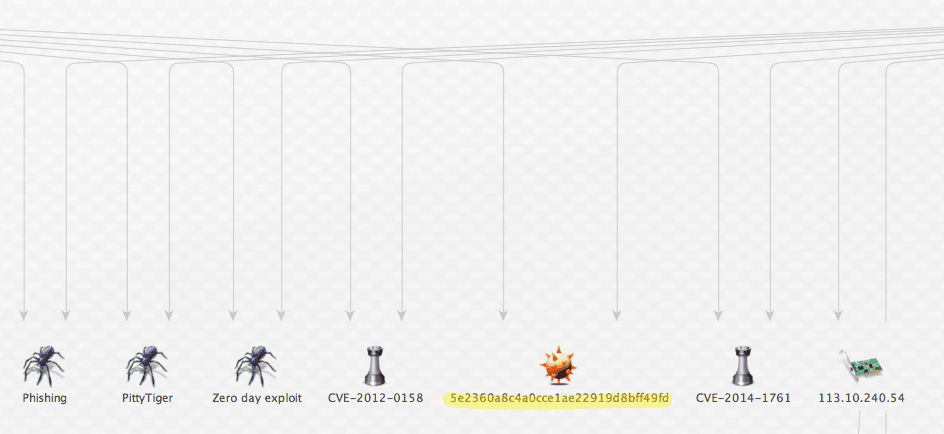
I see generic malware names for phishing, PittyTiger, two CVE's, and an additional IP address; all useful data points for my investigation. What really stands out is the hash entity. I'm able to easily validate these IOCs by simply taking the hash and running it against a virus total search.

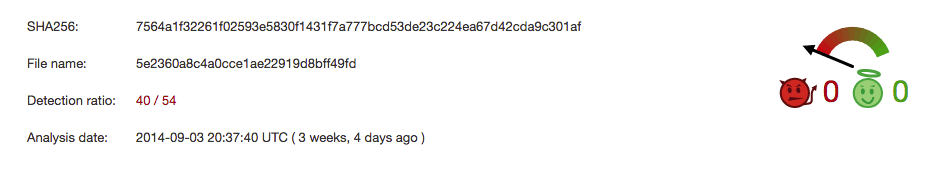
Sure enough, we discover the hash is a malicious PE file attributed to the PittyTiger group. The intelligence we have confirms this backdoor has been successfully exploited in a previously recorded attack against a French company.
Now looking at the bigger picture of PittyTiger in Recorded Future we see references to this group dating all the way back to 2008. Much of the groups activity went largely unreported until recently where we begin to see attribution on specific RAT variants and backdoors.
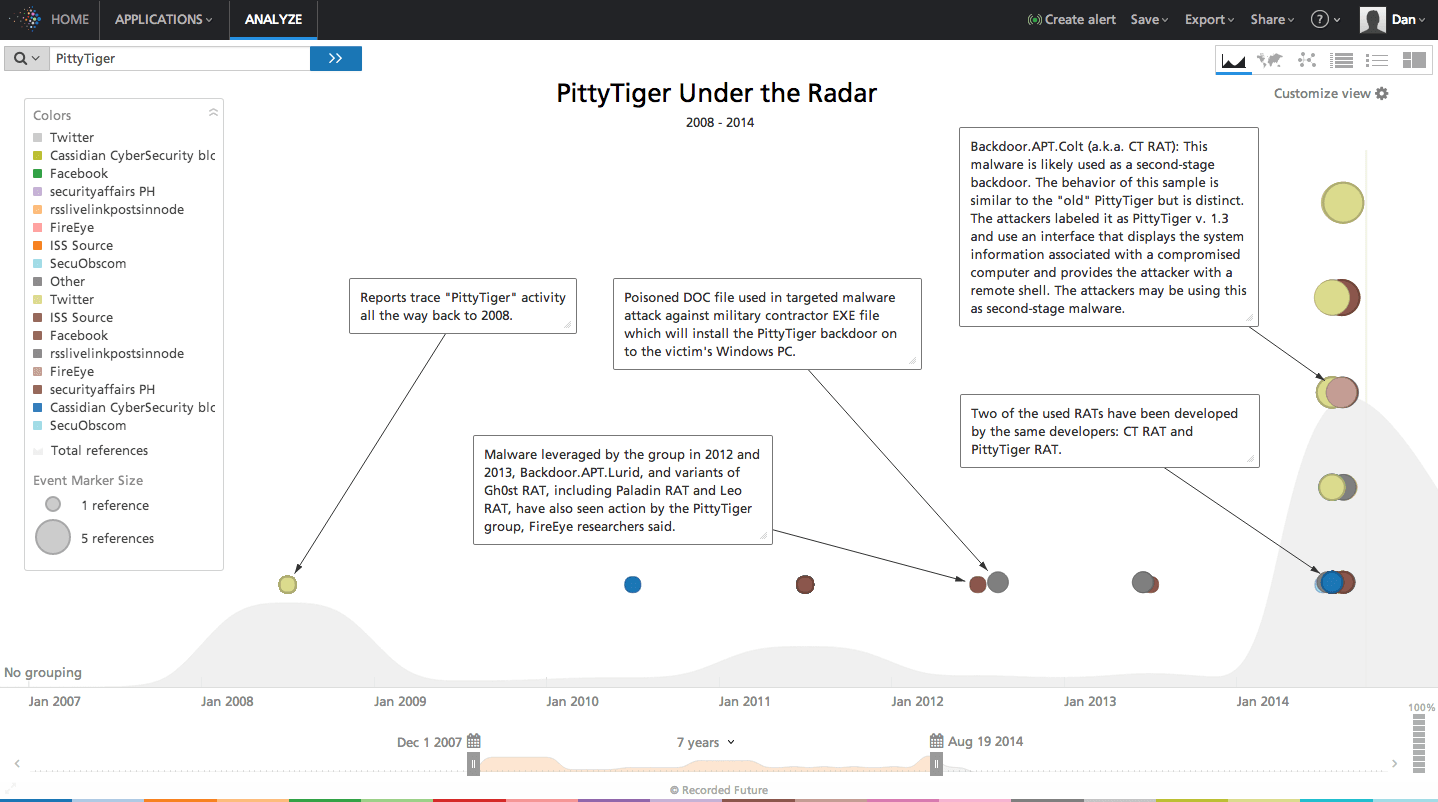
Click image for larger view.
So what’s next? There are three concrete actions I can take without any further analysis.
1. Block
I can immediately block access to the three IP addresses or the entire net-block. This will effectively short circuit any multi-stage attacks in progress.
2. Analyze
I now have a rich new set of relevant threat indicators. I can use these indicators in conjunction with other data sets for additional research, or I can use them as new pivot points in Maltego and continue my analysis with any additional third-party transforms I might have such as Malformity Labs.
3. Prevent
I now have new search criteria and content in the form of specific technical indicators I can use to develop more accurate detection logic for my SIEM correlation engine, IDS/IPS/AV signatures or use as content with any other network security monitoring and detection solutions.
Join Our Maltego Beta Program
Recorded Future Customers: Are you interested in joining our Maltego integration beta program? Contact us to schedule a demo and participate in our latest method for advanced threat detection and analysis.
IT Security Community at Large: I hope this quick preview inspires you to learn more about applying OSINT to threat intelligence, and how Recorded Future products support those methods. We recently hosted a webinar that provided a demo of our beta Maltego transforms. You can watch the on-demand version here.
Related