4 Ways to Improve Security Using Recorded Future DNS Intelligence
The Importance of DNS in Security
DNS is a powerful, but underused, tool in security. Most security teams think of DNS security primarily as using domain names as indicators of compromise (IOCs), which is a good start and certainly an important foundation for DNS security. But there is so much more insight and actionable intelligence that can be gained from DNS analysis.
The goal of this blog is to show you four ways, aside from IOCs, that Recorded Future can help you improve your DNS security:
- Creating response policy zones (RPZs) from our threat intelligence
- Using the fast flux DNS IP address list
- Monitoring new domain registrations
- Connecting the dots between malicious campaigns using WHOIS data
DNS Intelligence Is More Than Domain Name IOCs
Let’s dig — pardon the pun (the four of you who got that joke can skip this article) — into the ways that DNS can help your security team track threats and connect the dots while threat hunting. While this article focuses primarily on capabilities within the Recorded Future® Platform, I do want to start by discussing a powerful tool for DNS threat hunters: Passive DNS.
Passive DNS is used to track changes to a domain name over time. Normally, when a domain owner makes a change to a DNS record, that change is not stored anywhere. Historically, this meant that if a researcher was trying to find out what infrastructure an attacker used in the past, there would be no way of knowing.
Companies like Recorded Future partner Farsight Security allow researchers to see how a domain’s DNS profile has changed over time. For example, the image below shows the number of different IP addresses that the malicious domain pupybul[.]com has had over the years.

Displaying Farsight Security Passive DNS data in the Recorded Future platform.
The nice thing about this is, if you are Farsight Security client, you can view their intelligence directly in the Recorded Future platform. This allows security teams to quickly search through historical IP addresses associated with the domain to see if there are any matches with your organization’s logs, all while seeing the intelligence that Recorded Future has on these malicious domains and their associated IP addresses, as seen in the image below.
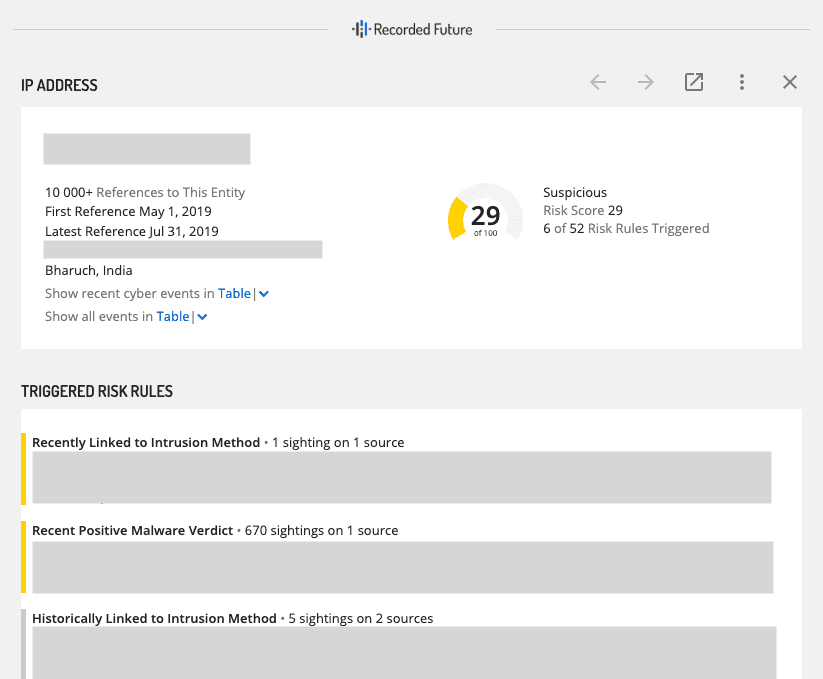
Pivoting from the Farsight Security Omni extension to Recorded Future.
Passive DNS is a powerful tool that more organizations should take advantage of during hunting sessions, as it is still a reactive tool. As organizations work to become more proactive and automated in their protections, Recorded Future can offer ways to do this with DNS. One of those ways is our first “DNS trick” — creating response policy zones (RPZ) using Recorded Future Fusion.
Creating RPZs From Recorded Future Intelligence
RPZ is a tool created by Vernon Schryver and my hero, Paul Vixie, as a way to build an overlay onto DNS that allows for automated custom responses to queries. RPZ is often referred to as a DNS firewall. By using RPZ, your organization can block attacks at the DNS level, before they have a chance to do any damage. RPZs are also nice because they are automated and time-limited. Just as with any DNS zone transfer, when a new RPZ is downloaded it replaces the old one, meaning that any indicators that are no longer at risk are automatically removed, reducing the chances of false positives.
RPZ is also a very flexible solution. While most organizations choose to block, that is not the only option. RPZ allows your organization to configure RPZ files to block access to malicious domains, redirect to an internal server (often referred to as a walled garden), or allow the traffic to continue unimpeded, but log it for later analysis. That flexibility continues with the ability to create white lists that override all other RPZs. If there are critical domains to which your organization needs uninterrupted access, you can add them to an RPZ white list and ensure that they will not be inadvertently blocked.
RPZ capabilities are built into BIND and other Enterprise DNS servers. Recorded Future has created a template available on our community site to build out three different RPZs using our Fusion product. The three RPZs we offer to clients are:
- Newly Registered Domains: Approximately 90% of all newly registered domains are malicious. Rather than take a chance, this RPZ allows you to block traffic to all domains registered within the last 24 hours. After 24 hours, the most malicious domains have found their way to other block lists and can be picked up by other detection mechanisms.
- Punycode and Recent Punycode Domains: Punycode is a Unicode representation used in the domain registration and the larger internet hostname creation process. Punycode domains are used to enable the use of Unicode characters in domain registrations. Unfortunately, malicious actors have used punycode to create lookalike domains. For example, the words “löök” and “look” appear to be the same in a web browser, but the representation of the first is “xn--lk-fkaa.” Recorded Future tracks newly registered and malicious Punycode domains, and you can use these to create an RPZ.
- Very Malicious Domains: Finally, we have also created an RPZ from our very malicious domains, domains that trigger at least one of our “very malicious domain” risk rules. This list is particularly dynamic, as domains are constantly being added and dropped depending on a variety of factors. This is a great use of the automation capabilities built into RPZ, because you don’t have to worry that you might still be blocking a domain that is no longer malicious — it will be automatically dropped as it falls out of our “very malicious domains” set.
Using RPZs built from Recorded Future risk lists allows your organization to automate the process of proactively blocking malicious and potentially malicious domains in a manner that is transparent to others in your organization and seamless for your security team.
Using the Fast Flux DNS IP List
Some malware families use a constantly changing stream of IP addresses associated with malicious domains in order to mask their true infrastructure. This is called a fast flux network. These networks hinder investigations and can make it difficult to detect the IP addresses that are truly malicious, as opposed to simply serving as a redirect or not being associated with malware at all.
There are two types of fast flux networks. The first is a single flux, which is a single domain set up to have its records changed frequently, often as fast as every five minutes. Single flux networks often rely heavily on less-than-reputable hosting providers located in countries that don’t require the provider to respond to law enforcement requests, making them very difficult to track down and stop — though not too difficult to block, since those IP ranges are usually well known.
The second type of fast flux network is known as a double flux network. These are significantly more difficult to track and block; double flux networks are built around botnets controlled by the attacker, and these botnets are usually legitimate machines that have been infected by malware or worms. These infected systems serve as redirectors and don’t host any malware functionality. These systems are also infected for short periods of time, as they either get cleaned up or the routers get rebooted.
The Recorded Future fast flux threat list is a high-volume list with a very high turnover. The fast flux list is collected based on our observation of DNS data, and it currently has more than 170,000 entries and sees more than 50% turnover every 24 hours.
IP addresses that land on the fast flux threat list are scored at the “unusual” level, unless the IP address also triggers another risk rule. The fast flux list is also unique to other sources. On average, Recorded Future sees a 0.17% to 1.07% overlap with other open or community threat lists that we monitor. The image below shows the fast flux list in the Recorded Future platform, and the image below that shows what the triggered risk rules look like in the platform.
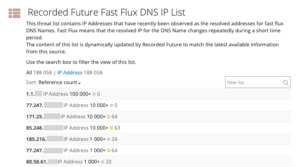
“Fast Flux DNS IP” list in Recorded Future.
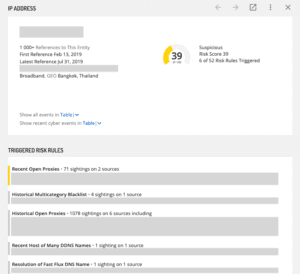
The fast flux rule triggered on an IP address.
Monitoring New Domain Registrations
Recorded Future collects new domain registration information on more than 500 generic top-level domains (gTLDs) and 12 country code top-level domains (ccTLDs). We currently collect between 225,000 and 250,000 new domain registrations each day. Detailed information about our collection capabilities are available on our community support site. As this information is constantly changing, it is recommended to check the document frequently.
New domain registrations are included in the domain/DNS technical reporting source type and serve as a useful tool for not only tracking potentially malicious domains, but also those domains that may be used to target your organization or your customers.
New domains are searchable by free text, or by using existing company entities, which allows you to use our existing typosquatting rules and restrict matches by pattern search. In other words, Recorded Future allows clients to use the power of our machine learning capabilities to specifically focus on finding new domains that may be relevant to their organization, without having to put in extra work.
In a very public example of how this can be used by organizations, last year, ESET reported on ties between Industroyer and NotPetya. The group behind the attacks liked to use ESET-domains for their command and control (C2) infrastructure. Specifically, in their reporting, ESET called out um10eset[.]net and esetsmart[.]org. Looking through new domain registration just a couple of months after the linked report was released, we see that the domains eset-nod32antivirus[.]net and eset-smartsecurity[.]net were also registered, as shown in the image below.
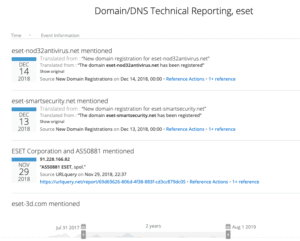
Newly registered domains containing the text “ESET.”
Tracking new domain registrations allows your organization to stay ahead of potential threats and stop attacks using typosquat domains or domains similar to your existing domains before they start. We at Recorded Future had the opportunity to take advantage of this feature a few months ago.
Connecting the Dots Using WHOIS Data
WHOIS services are provided by registrars and registries for the domain names that they sponsor. Originally, WHOIS provided contact information as well as registration information for domains. With the advent of GDPR and the growth of WHOIS privacy services, the value of WHOIS has somewhat diminished, but there is still important data available.
Using WHOIS data allows security researchers to “connect the dots” from one campaign to another using common artifacts in the WHOIS registration data. WHOIS information is available for tens of millions of domains registered in 2017 and early 2018. Details about the capability are available on our community support page.
All “WHOIS Update” events include a domain name and an event date, and most also include the contact email address listed on the WHOIS record after the update. Data from WHOIS registrations can be pulled into a tool such as Maltego to connect the dots between different domains and tie activity to an actor or group, as shown in the image above.
Learn More
Using DNS information to create IOCs is a powerful tool, but it is just the start of how DNS can be used to protect an organization. Hopefully, this post provided you with some ideas for other ways Recorded Future’s DNS intelligence can be used to better protect your organization.
For a closer look at how Recorded Future can improve your security processes and save you time and money, request a complimentary demo today.
Related