Staying 1 Step Ahead of the Bad Guys: How to Identify New Tools and TTPs
Gathering intelligence is a never-ending job — there are always more leads to find and connect to the ever-increasing web of analysis. That’s why automated collection is a force multiplier for gathering intelligence, helping analysts collect data from all parts of the internet at a speed and scale impossible for a human.
But automated collection on its own is not enough for understanding the inner workings of criminal groups and the methods by which they carry out cyberattacks. For this type of advanced research, Recorded Future has Insikt Group®, our team of highly trained analysts whose name bears the Swedish word for “insight.”
Insikt Group is comprised of threat intelligence professionals with an average of 10 years of experience in fields such as law enforcement, national intelligence, malware reversing, and private sector threat intelligence. They deliver to our clients expert research on malware, APTs, and nation-state actors that is built directly into our product, in addition to customized finished intelligence tailored to a client’s specific interest.
Our threat analysts use Recorded Future’s data collection, sandboxing, and alerting capabilities to generate original intelligence for our clients. From sources like no-distribute scanners, our team can often uncover malware samples a full month before they’re seen by mainstream file analysis tools that share file metadata. This type of intelligence helps our clients benefit from the combination of automated and human-generated intelligence to be proactive in their cybersecurity defense.
Insikt Group Research: Tools and TTPs
Recorded Future is constantly innovating to stay one step ahead of the adversaries. Recently, we introduced a new feature to our home screen that highlights Insikt Group’s research on newly observed tools and TTPs (tactics, techniques, and procedures) that are either currently being used by adversaries, or are likely to be used by adversaries in the future.
Recorded Future clients can access analyst-written TTP notes (which include relevant MITRE ATT&CK categories) directly in the product, or they can export this information via our API to programmatically import new TTP instance notes into existing tools and workflows. Using this information, threat hunting or red teams can test new adversary tools and TTPs in their attack scenarios to help proactively identify security control gaps.
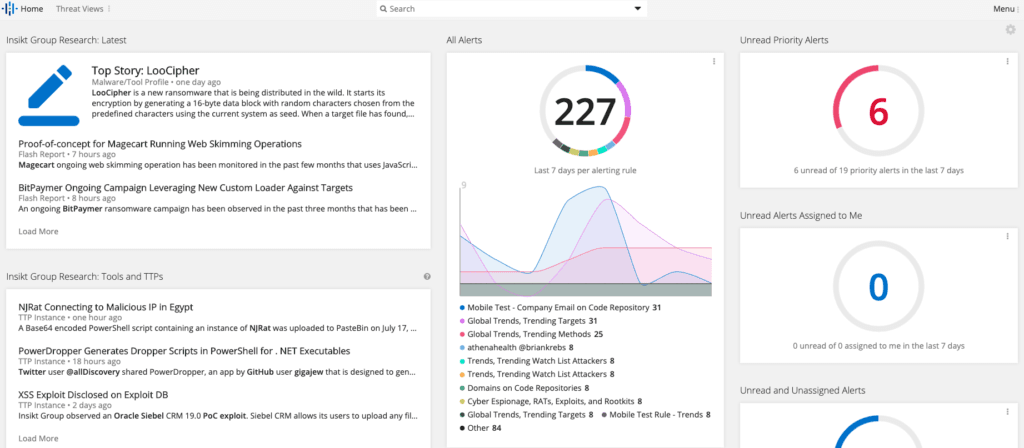
Recorded Future home screen.
The world needs smart people to help protect from the bad guys, but people alone aren’t enough to effectively defend against adversaries. Using machines to collect data and connect the dots arms researchers with the information they need to generate unique insights and helps them focus on the high-value work for which they’re trained. This combination of machine-generated data and human analysis turns information into actionable intelligence for a proactive security strategy.
Learn More
For more information about how Recorded Future can help organizations better understand and prevent threats, request a personalized demo today.
Related