Huawei CPE Vulnerability and Kiddie Fun
Like most Recorded Future users I have a list of keywords (entities created from text fragments) that generate a daily alert summary of relevant results from the Web. Recorded Future’s applied NLP (natural language processing) makes the daily foreign language results especially interesting.
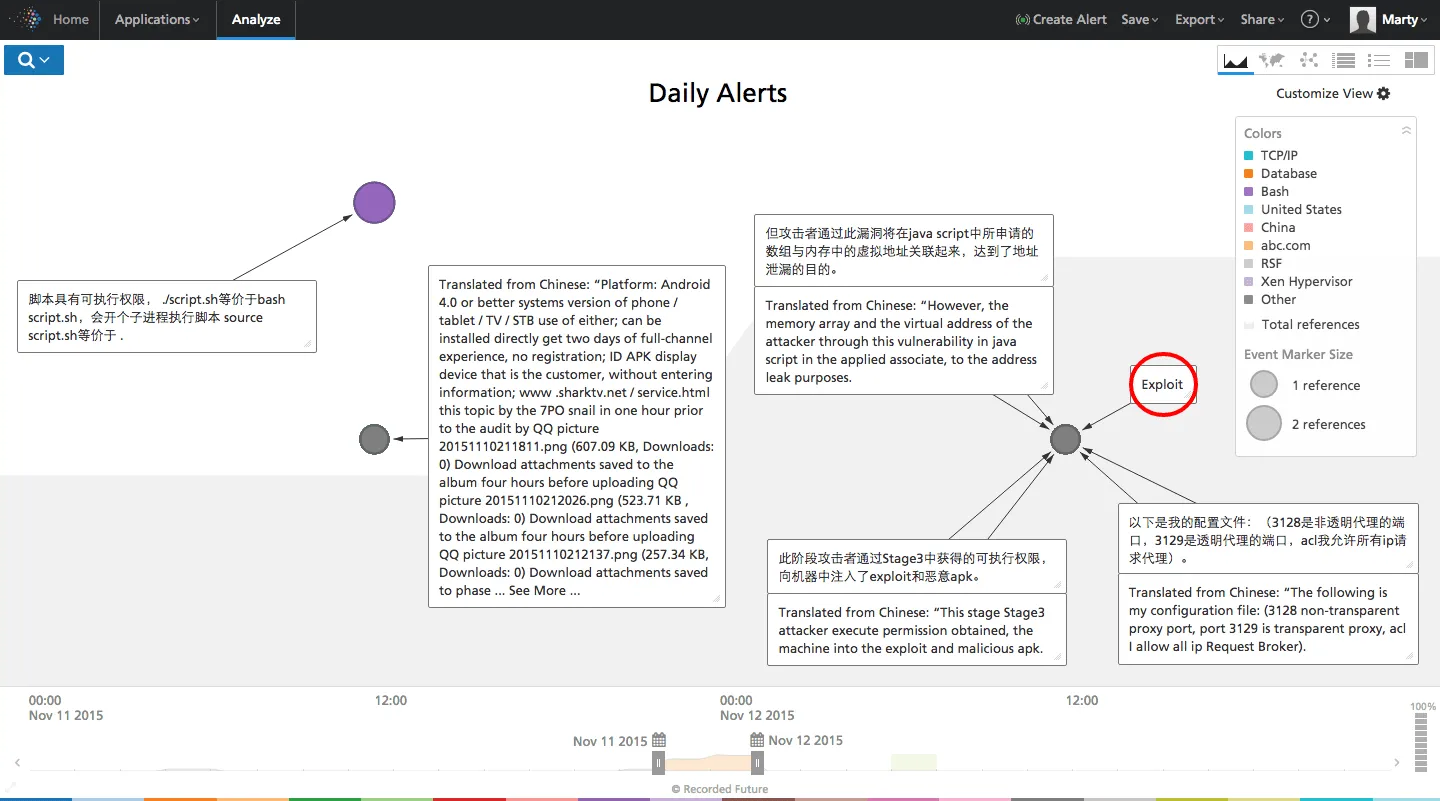
A recent alert caught my eye for its mysterious brevity (circled in red below).
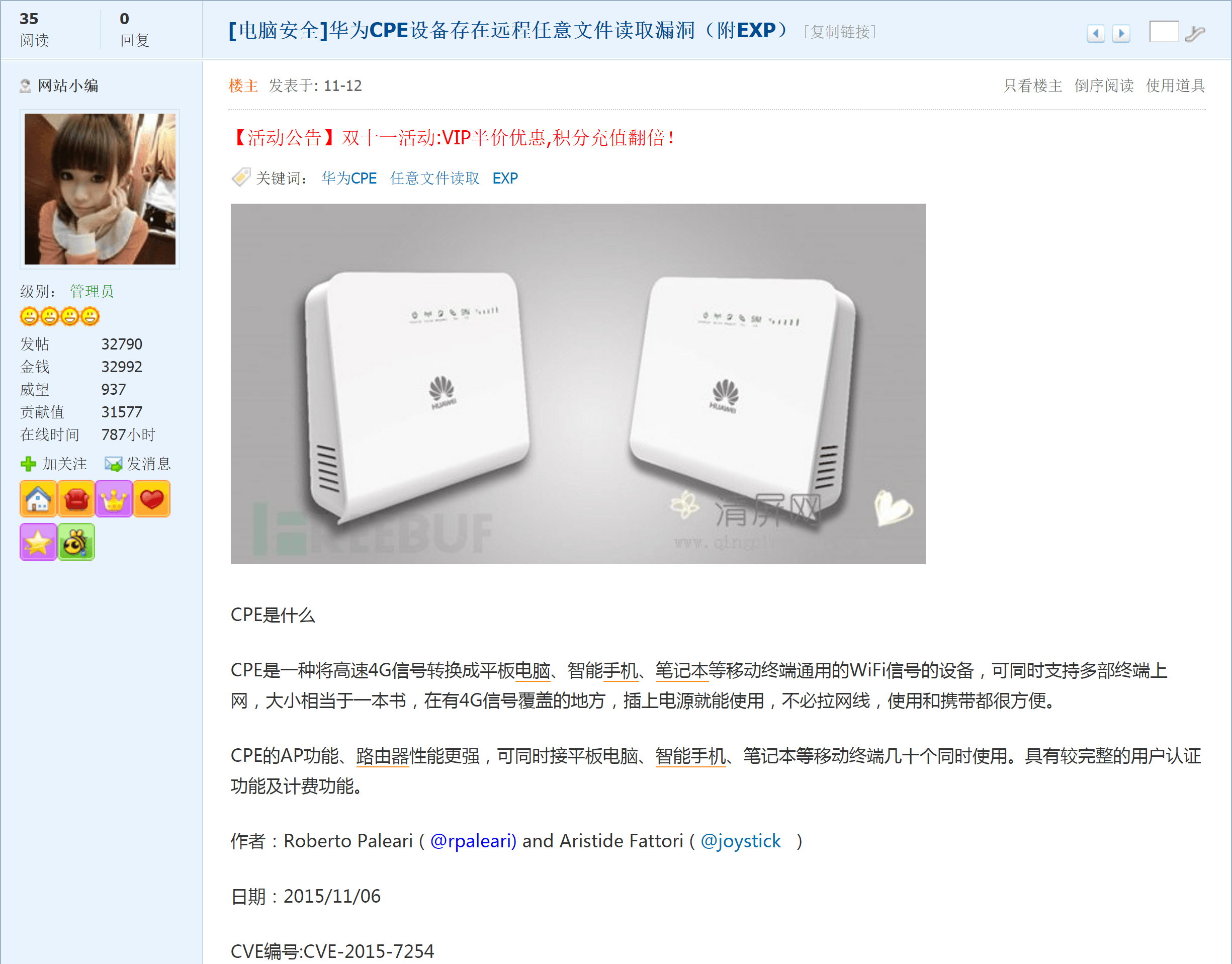
Following the source of the “exploit” statement led to the below forum and a reference to CVE-2015-7254, which is a directory traversal vulnerability on specific Huawei CPE (Customer Premise Equipment) models. (Cisco claims CPE models HG532e, HG532n, and HG532s are affected.) Remote attackers are able to navigate to arbitrary directories starting from an absolute URI path ending in /icon. Obviously if an affected device is storing sensitive information, the subsequent theft and potential exposure of the data is effortless.
The CVSS impact base score of 5.0 (medium) belies the potential for maliciousness as the exploitability subscore is 10 (out of a possible 10). Further, access complexity is rated low and authentication is not required to successfully exploit.
The Chinese language forum post also includes a 52-line Python script by Roberto Paleari and Aristide Fattori which exploits the vulnerability. It would be trivial to add an argument to the script that accepts a file containing a list of vulnerable Huawei CPE locations and additional arguments that spider and locate all directories containing data.
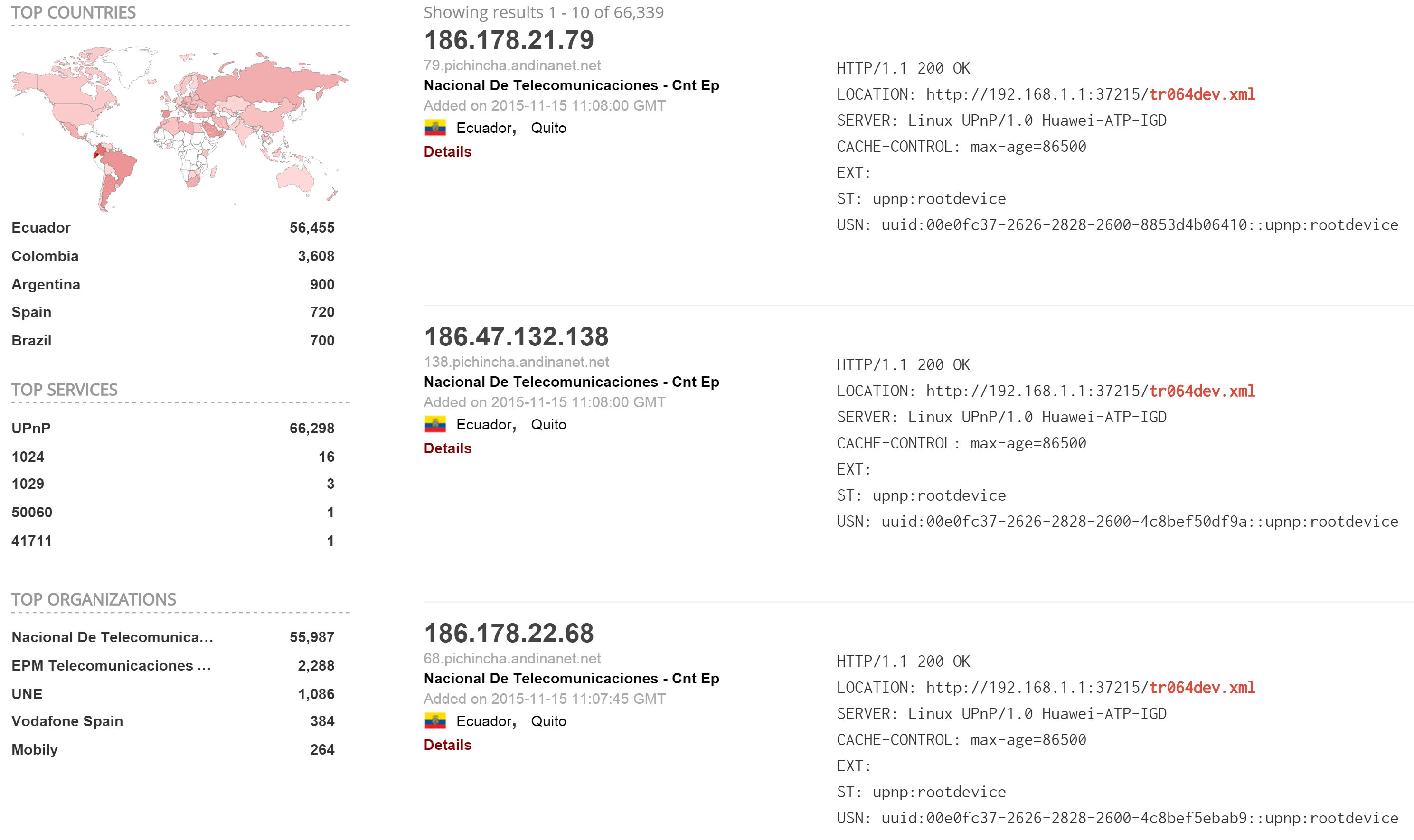
To compile such a list of vulnerable devices we start with Shodan. A query for tr064dev.xml returns approximately 66,000 devices. Some percentage of those devices are potentially vulnerable Huawei devices. The majority of the Shodan results are located in Ecuador, 55 are located in China, and interestingly, there are zero results for the U.S. and Russia.
The probability of sensitive data theft on one of these Huawei CPEs is high, but the likelihood of sensitive data storage occurring on one of these devices is low. This example affects consumer devices, but it’s always prudent to be aware of the past, because the next secure code lapse may involve enterprise equipment.
CVE-2015-7254 is a recently disclosed vulnerability with corresponding exploit code (although one could argue that in the U.S., enumerating open Web directories is not a violation of 18 U.S.C. § 1030 and does not constitute “unauthorized access,” meaning this is not an actual exploit) that’s actively being discussed in Chinese forums and may portend future mischief.
Related