How To Triage Leaked Credentials
What To Do When You Discover Leaked Credentials
Leaked and stolen credentials pose a critical risk to organizations everywhere. In fact, 61% of breaches involve compromised credentials. Every year, billions of credentials appear on the dark web, paste sites, and in data dumps shared by cybercriminals. These credentials are often used for account takeover attacks, exposing organizations to breaches, ransomware, and more.
But what do you do if you’ve discovered leaked employee or customer credentials? This step-by-step guide will show you exactly what to do.
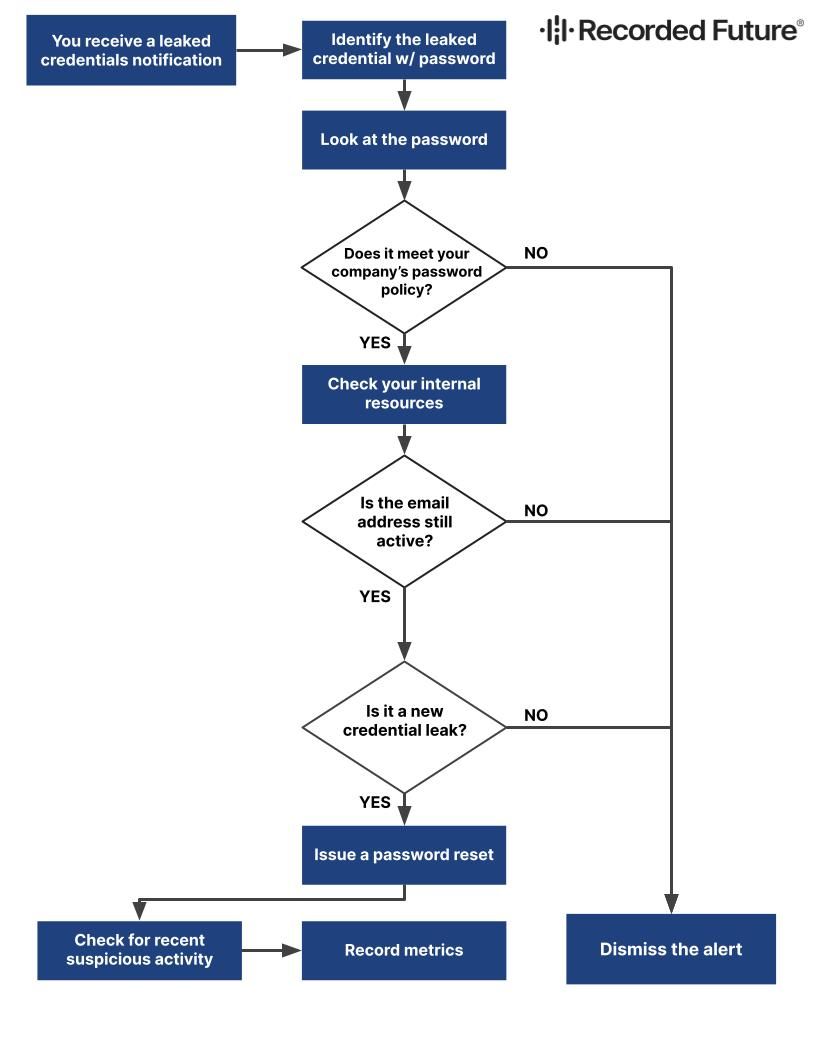
You identify leaked credentials that include a password. Proceed to the next step.
Step 2
Does the password adhere to your company password policy, or can you not confirm because it’s a hashed password?
- NO, the password does not meet company policy → Dismiss the alert.
- YES, the password meets company policy or you cannot confirm → Proceed to the next step.
Step 3
Check internal resources to see if the email address is still active.
- NO, the email address is not active. → Dismiss the alert.
- YES, the email address is active. → Proceed to the next step.
Step 4
Have the same Email Address and Password been identified in the past (e.g., in an older breach)?
- NO, they have not been identified in past events. → Dismiss the alert. Exclude the email and password string from future alerts.
- YES, the email and password were identified in past events. →
- Issue a password reset
- Check for recent suspicious activity
- Record metrics
Resetting passwords for leaked credentials isn’t too difficult, but maintaining the widespread visibility necessary to discover when leaked credentials appear is far more challenging. Brand Intelligence from Recorded Future automatically identifies and alerts you to leaked credentials from over 1 million unique sources including paste sites, GitHub, and the dark web. Request a demo to see how you can reduce account takeover risk for your organization.
Related