How To Assess a Potential Phishing Email

A Comprehensive Guide to Investigating Suspicious Emails
Phishing is the most prevalent type of cybercrime on the planet. In fact, according to Verizon’s 2021 Data Breach Investigations Report, phishing is the number one “action variety” observed in breaches in the last year. 96% of phishing attacks arrive via email, which makes email security a key priority for organizations of all types.
But how exactly should you investigate and act on suspicious emails? This step by step guide will show you exactly what to do.
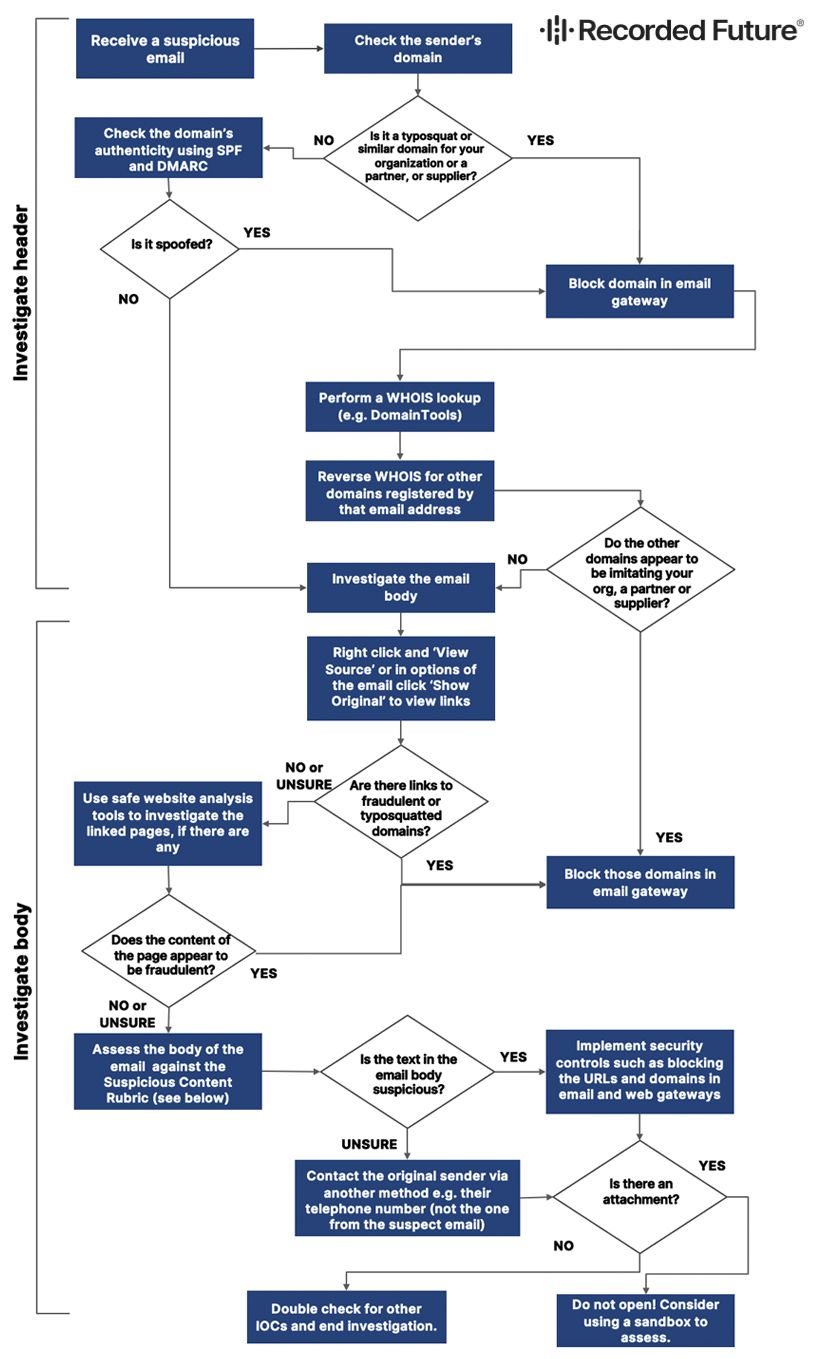 You receive a suspicious email either in your inbox or forwarded to you for investigation.
You receive a suspicious email either in your inbox or forwarded to you for investigation.
Phase 1: Investigate the Header
Step 1 Check the sender’s domain.
Does the domain appear to be impersonating your company, your suppliers, or your partners?
- If YES → Block the domain in your email gateway. Continue your investigation.
- If NO → Continue your investigation.
Check the sender’s domain authenticity using SPF and DMARC.
Does it appear to be inauthentic or impersonating another organization?
- If YES → Block the domain in your email gateway. Continue your investigation.
- If NO, continue your investigation.
Step 2
Perform a WHOIS lookup of the domain (e.g. DomainTools) to identify registrant information.
To find a unique email address with your WHOIS lookup, perform a reverse WHOIS lookup to find other domains registered by that email address, and expand your investigation to investigate whether any related domains are spoofing a legitimate domain.
- If YES, information suggests that this email is part of a phishing campaign → Block the related malicious domains and IPs.
- If NO, there are not any malicious associations → Continue monitoring the relevant domain / email address / IP address.
Phase 2: Investigate the Body
Step 3
Look for links in the email. Right-click on the body of the email and click ‘View Source’ or click in the options of the email and choose ‘Show Original’ to view links in the email without needing to hover over them.
Do not click on any suspicious URL on a production machine.
Do any of the URLs appear to be obvious typosquats or fraudulent domains?
- If YES → Investigate as you may have done above for the sender.
- If NO → Continue on.
Step 4
Compare the email text against our Suspicious Content Rubric:
| Is it asking for money, data, or otherwise making a request? (social engineering) | Yes / No |
| Are there typos or grammatical mistakes? | Yes / No |
| If there are images, are they correctly correlated to the brand they are purporting to be? | Yes / No |
| Authority - Is it claiming to be someone in a position of authority to cause you to do something? | Yes / No |
| Urgency - Is the text trying to rush or pressure you into doing something? | Yes / No |
| Emotion - Is the text trying to make you want to find out more, be fearful of consequences, or hopeful of benefit? | Yes / No |
| Scarcity - Is the message offering something in short supply, or something valuable at “better than good” prices? | Yes / No |
| Current Events - Are you expecting to see a message on this theme? Could malicious actors be using big news stories or routine events at the time of year (Tax reporting?) | Yes / No |
Based on the above rubric, do you believe the email is suspicious?
- If YES, you believe the email could be malicious → Implement security controls against the sender’s email and domain, such as blocking them in your email and web gateways.
- If MAYBE and you are still uncertain whether it is malicious → Get in touch with the original sender or organization that is attempting to contact you using their phone number, email address, or other communication method from a verified source.
Phase 3: Check for attachments
Do not click to open any attachments! If you receive a suspicious email with an attachment, we recommend using a sandbox to assess it.
Accelerate Phishing Investigations with Intelligence
Recorded Future provides intelligence to track threat actors, phishing campaigns, and the infrastructure used to deliver it in real-time, allowing organizations to accelerate their phishing investigations and better protect themselves from future attacks. Intelligence can even be integrated with your SOAR solution to automate the triage of phishing emails. If you’d like to see for yourself, try our free browser extension to access free intelligence on domains, IPs, and URLs.
Related