Hacker Forum Traffic Analysis: ‘Patch Tuesday … Exploit Wednesday’ and Other Patterns
Analysis Summary
- Forums can be analyzed at traffic level, without an analyst knowing foreign languages or tracking individual posts. Analysts can detect patterns in timing, forum participant product and vulnerability, etc. and use this knowledge to determine whether forum participants are a threat. Further, such insights can be used to set up appropriate alerting based on forum activity and help network defenders keep pace with developments around vulnerabilities and exploits.
- We analyze a prominent Russian hacker forum at the message traffic level with a dataset spanning 900 days. Forum language is by far dominated by Russians and forum product focus reflects general perceptions with focus on Microsoft and Flash but also perhaps a bit surprisingly Linux. On the other hand mobile platforms like iPhone and Android are less in focus.
- The old saying of “Patch Tuesday … exploit Wednesday” is strongly reflected in the data. Forum message traffic lights up on Wednesdays.
- Forum participants are latecomers in the day, especially when it comes to traffic concerning vulnerabilities – perhaps indicating forum activity matching off-day-job activity.
Introduction
Hacker forums can be near mythical in nature – hard to find and reach, hard to keep track of as they move around, hard to understand both language-wise, and hard to understand intent-wise.
For a network defender, forums are a place where the bad guys sell exploit kits, discuss new vulnerabilities, and generally conspire to perform illicit activities. For the defender with limited resources this may be quite intimidating – knowing that potentially dangerous activity is happening right in front of your eyes, but in a complicated-to-reach place and in a language (be it Russian, Chinese, or Arabic) you don’t understand.
In this analysis, we research a hacker forum using traffic analysis-like techniques. The forum is mainly using a language foreign to the analyst/author of this blog and there is no time to perform translation.
Data for Forum Analysis
We will not (for obvious reasons) name the forum – and it likely matters less. There are many hacker forums, and the same techniques used below could be readily reused, and perhaps even with very similar results. We do not try to replicate the results for any other (let alone body of) forums, so we could be at fault for a sample size of one.
The data has been collected in real time with Recorded Future during a time period of over 900 days (i.e. a fairly significant dataset).
We’ll mostly analyze traffic around vulnerabilities, such as the below, where the participants cover specific CVEs or Microsoft (MS-X) vulnerabilities.

Language of Participants
Language is an important differentiator to understand forum traffic. For our specific forum it’s simple, it’s completely dominated by Russian as we can see below.
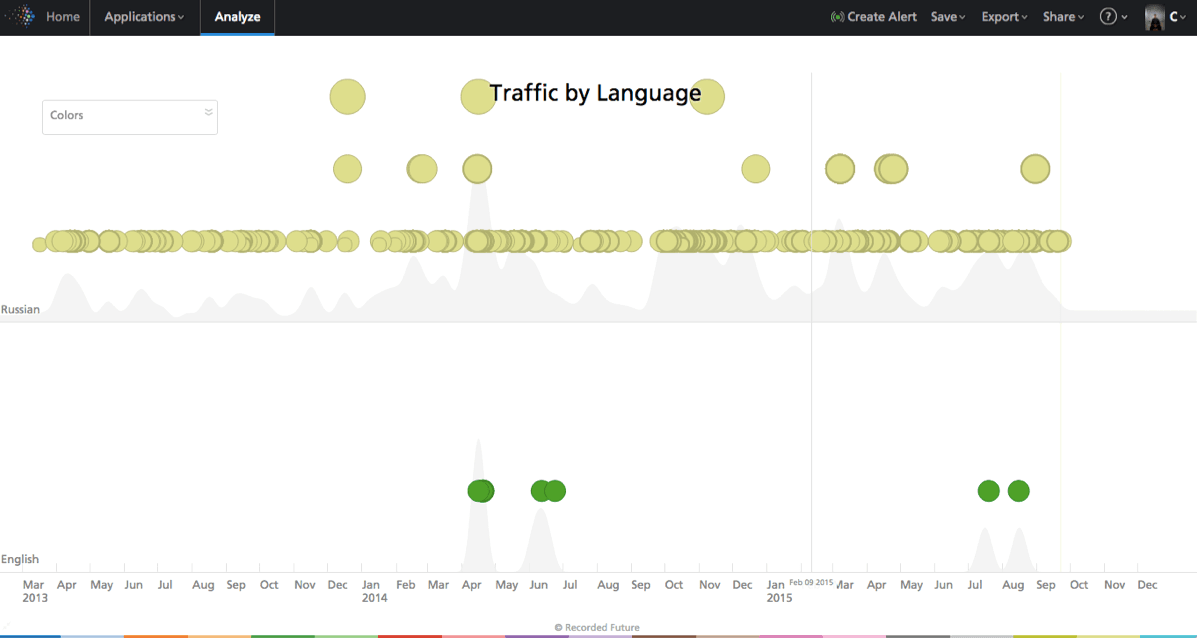
Figure 1: Language completely dominated by Russian. Nothing in other languages but a few English messages. First swimlane is Russian, second is English.
What Do They Care About?
Since we’re analyzing CVE messages we can readily aggregate message traffic into a treemap to see product focus. We quickly identify Microsoft focus in messages along with Adobe Flash. Perhaps surprisingly Linux raises to the second spot – likely driven by Shellshock. On the other hand, iPhone and Android stands out as not being in focus for this crew.
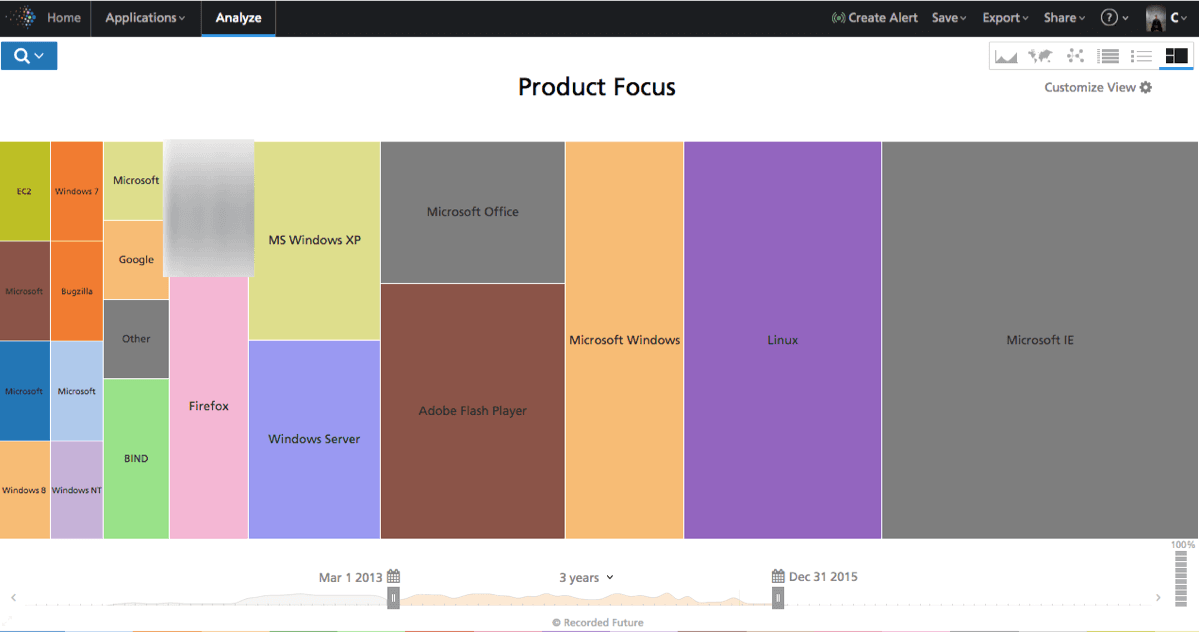
Figure 2: Product focus of the forum is certainly Microsoft products, but Linux and Adobe Flash stands out as well.
In terms of vulnerabilities, Heartbleed and Shellshock raises to the top, not surprisingly, but then follows a vast set of vulnerabilities and intensive discussion around many of them.
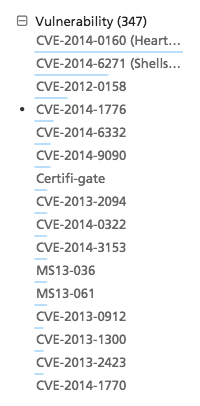
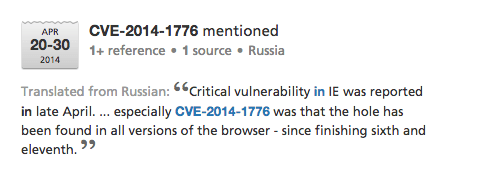
By aggregating message traffic on these CVEs we can plot them the over time and reveal how some of them (e.g., Heartbleed) generates ongoing traffic, some come-and-go, and some are posted but fail to generate interest.
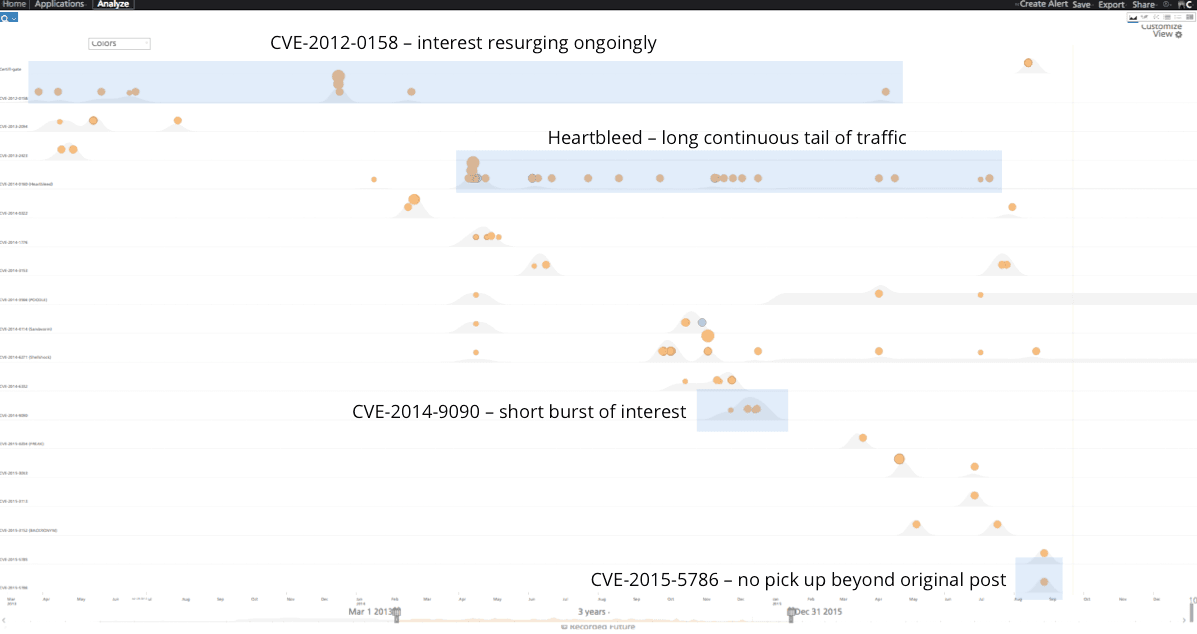
Figure 3: Forum CVE message traffic timelined to reveal patterns of communication – ongoing, bursty, point-in-time, etc.
Timing: Patch Tuesday … Exploit Wednesday
In 2006 Trend Micro wrote a blog entry (“Patch Tuesday … Exploit Wednesday“) stating, “Some industry experts have coined a new term – ‘exploit week’ – to call the days following the release of a Microsoft Security Bulletin.” Is this behavior still true and can we view this in our observed forum?
Turns out we can. We pull three samples of forum data for a long time period, from March 2013 until September 2015 and plot them (Figure 4). First sample (blue below) is general forum traffic, second sample (green below) is for traffic concerning CVEs in general and third sample (red) is for traffic concerning Microsoft products specifically. The forum sample below displays the traffic regarding a specific CVE.

We can clearly observe a differentiated pattern. General forum traffic is pretty much equal each day Monday through Friday, lower on Saturday, and shrinks to less than half Sundays. Russian language plus weekends off, especially Sundays, points us pretty clearly at a specific demographic. On top of the indication of Russia this may also point us to a crew that treats activity on the forum as a job (with odd hours as we’ll see below) as opposed to weekend amateurs sitting around noodling on a forum.
Perhaps more interestingly we observe a very clear pickup in traffic on Wednesdays(!) for vulnerability-oriented traffic (green and red below). Patch Tuesday … exploit Wednesday holds true.
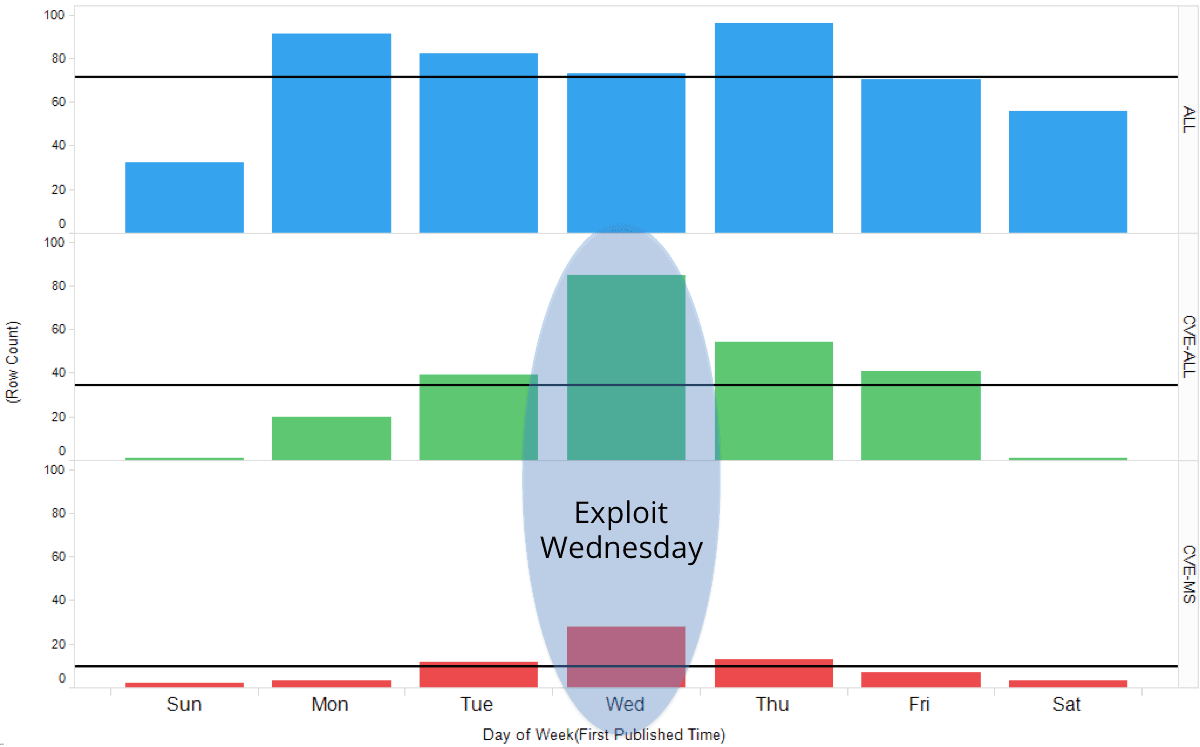
Figure 4: Visualizing day-of-week patterns for segmented forum traffic. Line in each trellis segment is the average traffic volume of segment.
Workday Analysis
Analyzing Internet traffic for attribution is neither new nor without controversy. In this case, we’re not trying to perform attribution beyond the complete dominance by Russian language which very likely maps us to Russia and former Soviet republics.
But we can still observe time of day of message traffic with interest. Initial analysis indicates that the timezone of the forum is Moscow, but this can surely be argued. Patterns below will indicate timestamps are non-random (it would be awfully inconvenient to even just display random timestamps in a message board). The message board is built on a well established, commercial, message board toolset. Even if we’re a few hours off in timezone, for the below that will matter less. Russian language speakers are by far predominantly located in the very western parts of Russia.
Forum participants are certainly not a morning crew. We see some early morning activity but it’s not until 3:00 PM we see real activity kicking in, as we can observe below in Figure 5. But it’s in the following chart (Figure 6) it gets really interesting.
In Figure 6, we have traffic that involves CVEs and likely a more technical discussion and even a more technical crew. The forum message traffic on vulnerabilities is completely missing between 4:00 AM and noon. This certainly implies the participants are burning the midnight oil. This could mean a few things:
- It’s a typical, late-night hacker crew.
- It’s a hacker crew with day jobs, and during after-work hours they make money via illicit online activity.
- That activity, in particular around vulnerabilities, kicks in after vulnerability disclosures happen in the U.S. We can’t make that assertion here, but as follow-up research we could perhaps map timestamps of CVE publications to message board traffic on said CVEs.
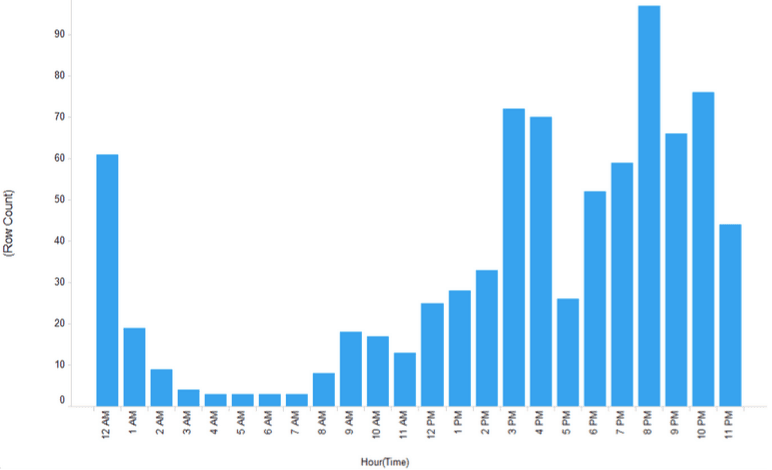
Figure 5: Forum message traffic kicks in for real after 3:00 PM.
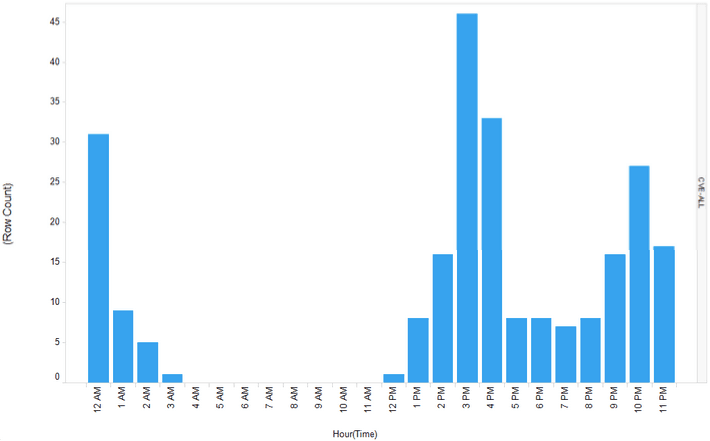
Figure 6: Forum message traffic on vulnerabilities is completely missing between
4:00 AM and noon.
Conclusion
This research demonstrated how forums can be analyzed at the message/post-traffic level, without the analyst knowing foreign languages or tracking individual posts. Analysts can detect patterns in timing, spikes in forum participation, mentions of products or vulnerabilities, etc. and use this knowledge to determine whether forum participants are a threat.
Furthermore, such insights can be used to set up appropriate alerting based on forum activity. This helps network defenders keep pace with potential vulnerabilities and exploits in real time instead of after deployment.
Also, we analyzed a prominent Russian hacker forum at the message-traffic level with a dataset spanning 900 days. Forum language is by far dominated by Russian, and forum product focus reflects general perceptions of Microsoft and Flash – but also, perhaps a bit surprisingly, Linux. On the other hand, mobile platforms like iPhone and Android are almost missing.
The old saying of “Patch Tuesday … exploit Wednesday” is strongly reflected in the data. Forum message traffic lights up on Wednesdays. Forum participants are late comers in the day, especially when it comes to traffic concerning vulnerabilities, perhaps indicating forum activity matching off-day-job activity.
There’s much further work to perform, especially comparing this dataset to that of other forums which should yield interesting results. In particular, threat intelligence analysts will be interested in comparing different geographies and cultures from a targeting perspective.
Further Reading
There’s more to dive into on this subject for those interested. Below are some resources.
- Brian Krebs regularly covers Russian (and others) forum activity on his blog and closely engages in their activities … a must-read resource.
- Imperva analyzed a forum at content level in 2011 trying to understand topics, areas of interest and expertise, etc.
- Benjamin et.al [2015] compares and contrasts various underground forums.
- Benjamin et.al [2013] reviews approaches to identifying key actors in forums.
Related