In Germany, Industrial Sector Hit Hardest by Ransomware in 2020 and 2021

In recent years, ransomware has become a serious threat to most modern, IT-based economies and societies. The monthly volume of attacks has increased significantly since early 2020. What sets ransomware apart from other cyber threats such as espionage is its direct harm to the availability of affected systems.
In Germany, ransomware attacks have caused significant problems for many organizations: retailers shut down affected business units (such as Media Markt), factories are closed and put workers on part-time work (such as Eberspächer Gruppe), counties become unable to pay out unemployment and child benefits (such as Landkreis Anhalt-Bitterfeld), or, in the worst case so far, hospitals are forced to reject emergency patients (such as Uni-Klinikum Düsseldorf). On top of the immediate effects, ransomware incidents result in lost revenue, mistrust, and frustration.
The effects of ransomware attacks have persuaded governments around the world to recognize ransomware as a serious threat, and law enforcement around the world has cracked down hard against both ransomware operators (such as Egregor) and facilitators (such as Emotet). However, despite these efforts, there has not been any measurable slowdown in ransomware attacks. In fact, globally, the number of both ransomware attacks and active operators has never been higher.
While most countries outside of the CIS states are affected by ransomware attacks in one way or another, each country has its unique dominant industries, deployed technologies, prevailing regulations, and cultural habits. This report gives an overview of the ransomware situation in Germany from January 1, 2020, until December 31, 2021. It first discusses high-level trends and common techniques used independent of country. It then provides an in-depth, Germany-specific analysis based on a unique data set of past attacks.
Trends in 2020 and 2021
Like most cyber threats, ransomware attacks continue to adapt and evolve. There are five high-level trends with respect to victimology, technological sophistication, organizational structure, and extortion schemes that have shaped this evolution in 2020 and 2021.
Trend 1: Larger, More Damaging Attacks
At first, ransomware attacks targeted individual users and demanded relatively low ransom payments. The WannaCry ransomware attack in 2017 is a well-known example. While it crippled hundreds of thousands of computers across the world and caused millions in collateral damage, it only yielded around $130,634.77 as of June 14, 2017. Especially in the past few years, ransomware attacks started focusing on networks of large organizations, a strategy sometimes referred to as big game hunting. By encrypting significant parts of the victim’s network, the overall impact and thus the attacker’s leverage and potential ransom payments were drastically increased. Nevertheless, individual users are still under attack as shown by STOP ransomware.
Trend 2: Technological Sophistication
Scaling attacks up to the current level requires new, more sophisticated technological solutions. For example, when attacking large networks instead of individual machines, attackers often need to take control over the active directory’s domain controller first from where the entire networks can then be encrypted. To reduce the time left for defenders to detect ongoing attacks, different techniques to speed up encryption are also used (for example, LockBit using intermittent encryption). In addition, payments have partially moved from Bitcoin to Monero, with the latter using privacy-enhancing technologies that obfuscate transactions to achieve anonymity. Another interesting trend is that from 2021 onwards, more Linux-based ransomware attacks have been observed (such as Defray777 or SFile (Escal)).
Trend 3: RaaS and Specialization
As ransomware operators have significantly advanced technologically, they have also reshaped their entire organizational structure. Most remarkable is the emergence and dissemination of the ransomware-as-a-service (RaaS) model, which has become the de facto standard. As a subscription-based model, it allows affiliates to use already-developed ransomware tools to conduct attacks and then earn a percentage of each successful ransom payment. For operators, advantages include the obstruction of attribution and increased return on investment. The downside is the lower degree of control operators have over the activities of their affiliates, which is often counteracted by smarter encryption schemes. The changes in organizational structure of ransomware operators correlate with the broader trend of specialization underlying the entire cybercrime supply chain. For example, it gave rise to initial access brokers, who provide paying customers with remote access to a victim’s network.
Trend 4: Multi-Faceted Extortion Scheme
In late 2019, Maze became the first publicly known, high-profile ransomware operator that threatened to publish stolen data from its victims to increase pressure on victims to pay the ransom. From an attacker’s perspective, this has turned out to be particularly effective in cases in which victims have prepared for cyberattacks by backing up their data. Other strategies to make organizations hit by ransomware pay the ransom involve threatening to contact the victim’s customers using details found in the stolen data. Ragnar Locker ransomware operators have even gone so far as to prohibit their victims from contacting the police and the FBI.
Trend 5: Internationalization
Ransomware is becoming an increasingly international concern, affecting most countries around the world in some way. According to data on ransomware attacks collected by Recorded Future, prior to 2021, roughly 70% of all publicly reported ransomware attacks were on US targets. This number has steadily decreased, with known US targets now only accounting for roughly half of all reported ransomware attacks according to analysis conducted by Recorded Future. As ransomware actors broaden their horizons, the danger rises for organizations across the globe, especially those with attractive traits such as large revenues, particularly vulnerable IT infrastructure, and critical societal relevance for leverage.
Analysis
Ransomware attacks have not spared Germany. One example is the University Hospital Düsseldorf. In 2020, IT systems were encrypted by a ransomware gang known as DoppelPaymer, forcing the hospital to reject emergency patients and making this attack possibly the first instance of death by ransomware after a patient died while critical hospital systems were offline due to the ransomware attack. This section gives an overview of ransomware attacks against German organizations in 2020 and 2021.
Data Mostly Collected on Dedicated Leak Sites
The analysis is based on a unique data set based on publicly available information collected over the last two years. Roughly 80% of the attacks were detected through dedicated leak sites, websites used by ransomware operators to communicate with the public and extort their victims. A smaller number of the attacks was found manually through disclosure reports by affected organizations, news reporting, and other sources. The number of unrecorded cases might be much higher, however. One difficulty in identifying ransomware attacks is that they are often reported as regular security incidents.
Number of Ransomware Attacks Up
Overall, the number of reported ransomware attacks in Germany increased by 83% from 60 in 2020 to 110 in 2021 (see Figure 1). This increase is possibly attributable to the following factors:
- More ransomware gangs: The number of observed active ransomware gangs in Germany more than doubled from 14 in 2020 to 30 in 2021, with most of them adopting the RaaS model and professional strategies.
- Higher activity: Most ransomware gangs that had already been active in 2020 increased their activity even further in 2021 (see Figure 2). Among others, this might be related to the reinforcement effect of the RaaS model.
- Higher ransoms and more media coverage: In addition, with higher ransoms demanded, it has become harder for victim organizations to pay without anybody noticing it, and the pressure to report incidents has increased.
- Ongoing pandemic: The ongoing pandemic increased the attack surface for many organizations as they rushed to undergo digital transformation and many more employees began working remotely. The related dependence on a working IT infrastructure has increased the leverage for the ransomware gangs.
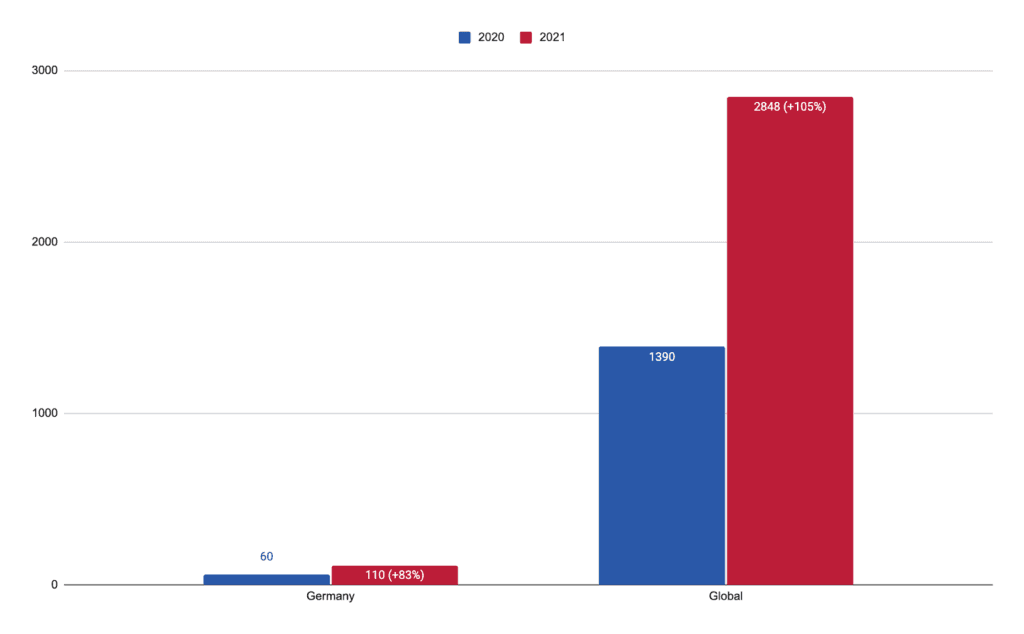 Figure 1: Number of ransomware attacks in Germany and globally from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Figure 1: Number of ransomware attacks in Germany and globally from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Changes at the Top
In 2020 CL0P, Egregor, and MAZE were the most active ransomware gangs in terms of number of attacks in Germany. However, MAZE’s shutdown of its operations in late 2020 for unknown reasons and law enforcement’s actions against the operators behind Egregor and CL0P paved the way for LockBit, Conti, Avaddon, and Ragnarok to take the lead in 2021. What stands out and deserves further research is the significantly higher number of attacks in 2021 that could not be attributed to any ransomware gang. This might be due to organizations not knowing or willing to say what gang attacked them.
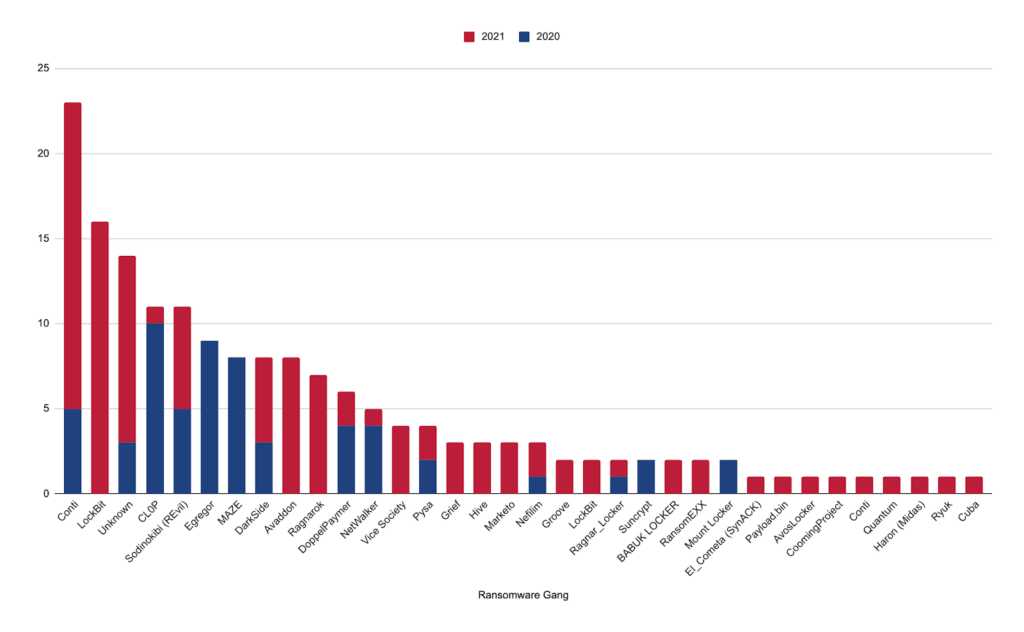 Figure 2: Ransomware attacks in Germany by group and year from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Figure 2: Ransomware attacks in Germany by group and year from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Number of Attacks Per Month Stable, With Some Exceptions
Over the last two years, the number of ransomware attacks per month has remained around 10, with some exceptions:
- The beginning of 2020 shows a low level of activity, which coincides with a lack of reporting and a lower diffusion of dedicated leak sites. This corresponds with previous reports by Germany’s Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, abbreviated as BSI). Given that dedicated leak sites are the main data source for this report, sparsity in this data indicates the actual attack numbers for early 2020 are higher than shown. We can still draw some meaningful conclusions by considering not only lower attack rates, but also the limited nature of the data sources in early 2020 as factors in observed low activity.
- The decrease in February 2021 is believed to be linked to the takedown of Emotet, an important ransomware facilitator, and the shutdown of Egregor around this time.
- Last, the decrease in June 2021 is believed to be linked to the then-upcoming meeting between Putin and Biden on July 9, 2021. This meeting had ransomware high on its agenda and entailed uncertainty of future governmental tolerance for many ransomware operators. All three exceptions can also be observed when looking at ransomware attacks from a global perspective on the Ransomware Tracker.
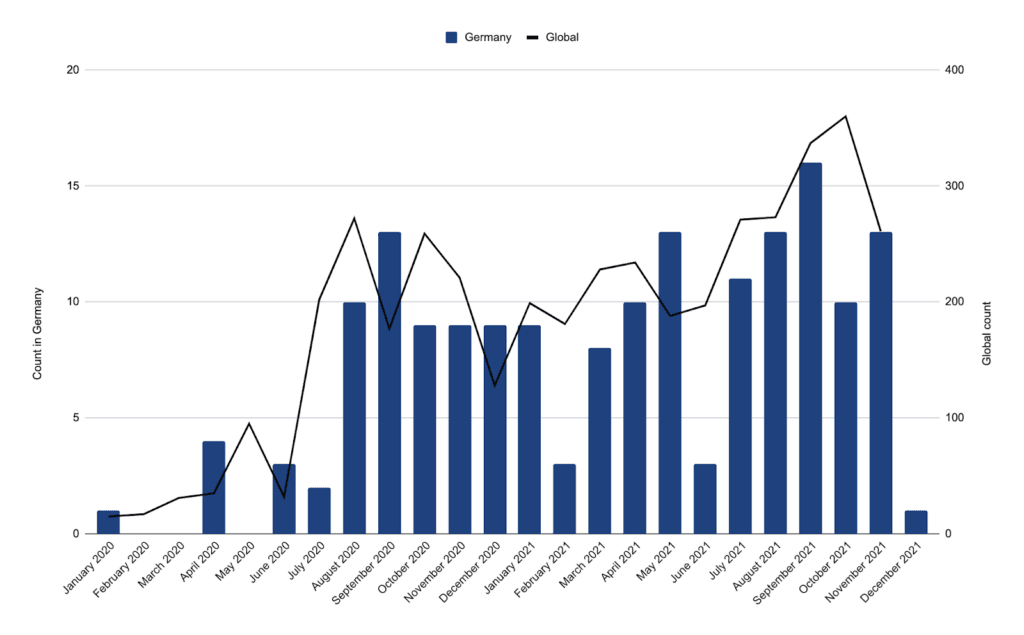 Figure 3: Ransomware attacks in Germany and globally by month from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Figure 3: Ransomware attacks in Germany and globally by month from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Public Holidays and Weekends
While it is not new that cyberattacks often take place during weekends and holidays when IT security teams are understaffed, there is rarely sufficient public data. Recorded Future’s unique data set allowed us to conclude that roughly 60% of all ransomware attacks for which the attack date is known took place during a weekend, shortly before it, or very close to a public holiday. In addition, many of the attacks that took place during the week took place at night. Since attackers so often strike at times of low staffing, this implies special care is to be taken in automating security wherever possible in addition to general security best practices such as network segmentation, comprehensive monitoring, timely patching, and hardening.
Industrial Sector Hit Hardest
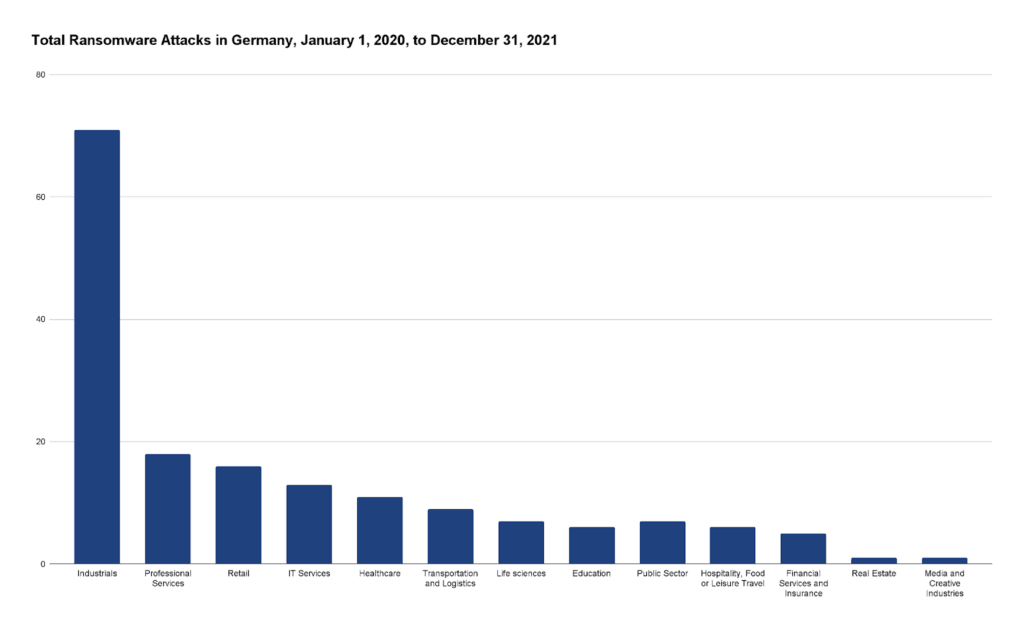 Figure 4: Total ransomware attacks in Germany by industry from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Figure 4: Total ransomware attacks in Germany by industry from January 1, 2020, until December 31, 2021 (Source: Recorded Future)
Roughly 42% of the ransomware attacks concern organisations in the industrial sector, considered to be the linchpin of Germany’s economy (Figure 4). For this analysis, the industrial sector comprises engineering and manufacturing of automotive, metal, electronic components as well as construction. However, when splitting the attacks by the four most active ransomware gangs, the picture changes substantially (see Figures 5–8).
Most interestingly, while most attacks by Conti, LockBit, and CL0P still affect the industrial sector, the group of Unknown seems to focus more on education, the public sector, and health. This may be for various reasons: While unlikely, in theory there could be other gangs still not known focusing on these sectors. What is more likely is a mix of two causes: First, most of these attacks were found not from dedicated leak sites, but from media reporting. Since the public sector and education are open to the general population, a lack of availability due to a ransomware attack is obvious. This leads to increased reporting in these areas. However, victims may either not know or not wish to disclose the ransomware gang by which they were attacked at the time of reporting. Thus, with increased reporting comes more attacks attributed to unknown attackers. A second possibility is an unwillingness or inability to publish the ransomware gangs in reporting.
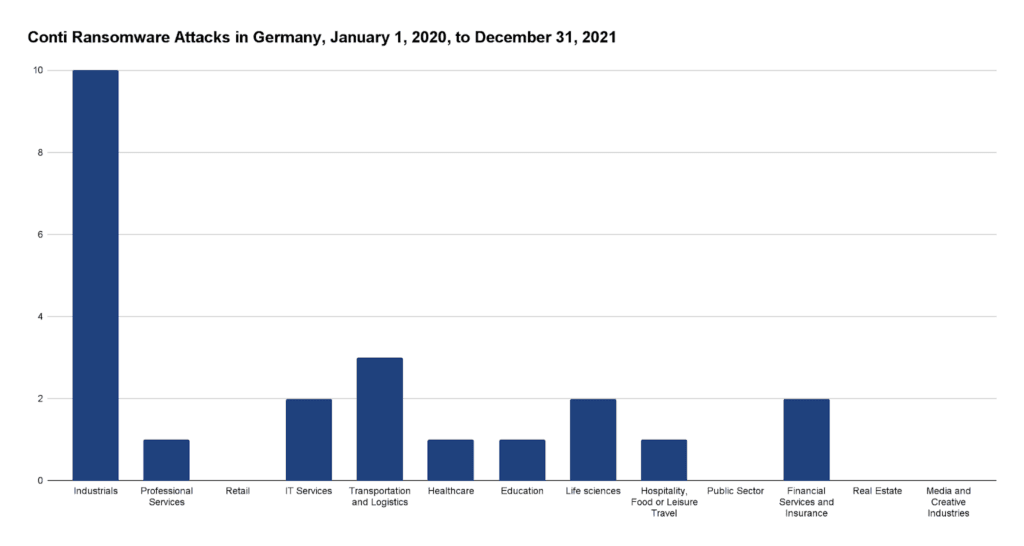 Figure 5: Conti ransomware attacks in Germany by industry from January 1, 2020 until December 31, 2021
Figure 5: Conti ransomware attacks in Germany by industry from January 1, 2020 until December 31, 2021
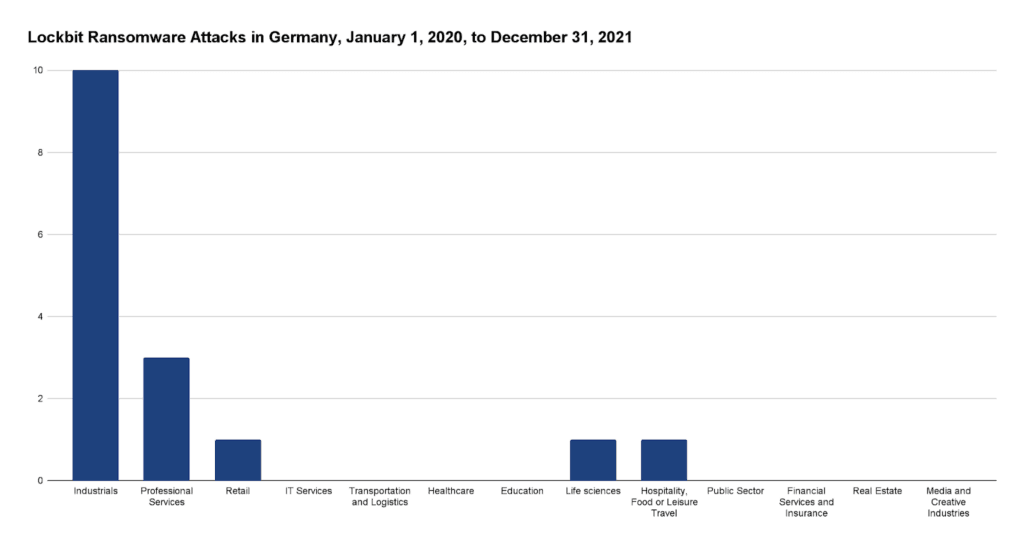 Figure 6: Lockbit ransomware attacks in Germany by industry from January 1, 2020 until December 31, 2021
Figure 6: Lockbit ransomware attacks in Germany by industry from January 1, 2020 until December 31, 2021
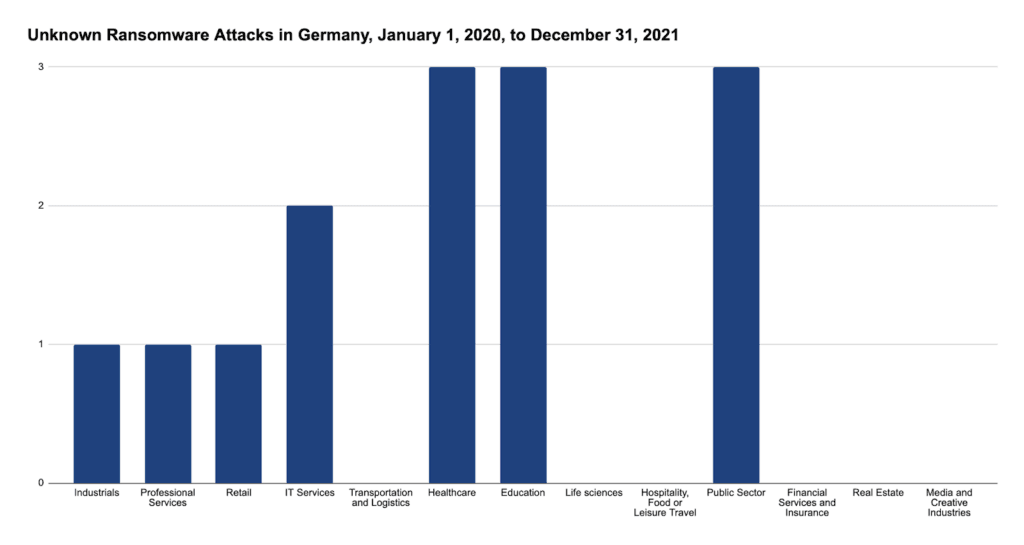 Figure 7: Unknown ransomware attacks in Germany by industry from January 1, 2020, until December 31, 2021
Figure 7: Unknown ransomware attacks in Germany by industry from January 1, 2020, until December 31, 2021
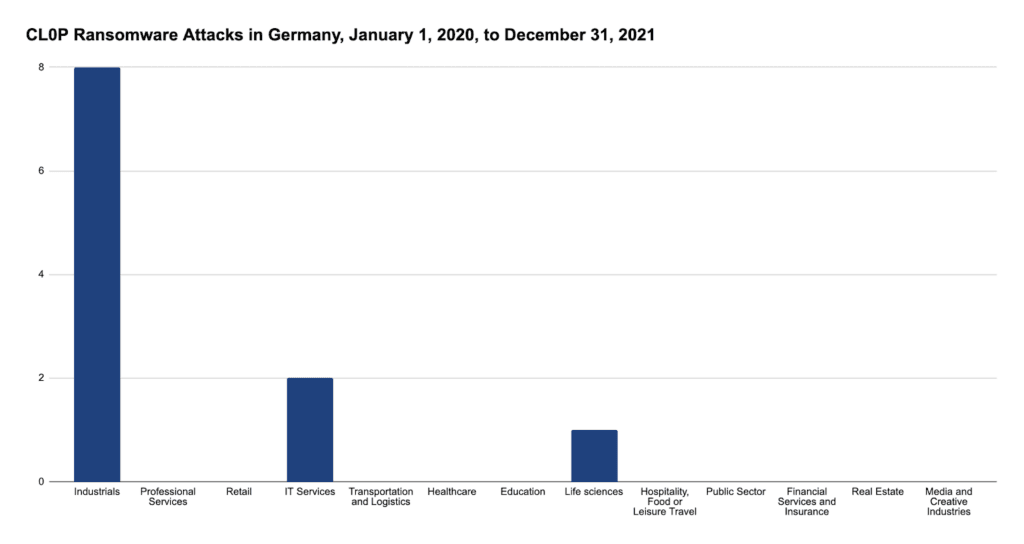 Figure 8: CL0P ransomware attacks in Germany by industry from January 1, 2020, until December 31, 2021
Figure 8: CL0P ransomware attacks in Germany by industry from January 1, 2020, until December 31, 2021
Outlook
This report on ransomware in Germany discussed the five most salient, high-level trends over the last years. These trends include the inclination to attack larger organizations, increasing technological sophistication, organizational specialization with the RaaS model becoming the de facto business model, multi-faceted extortion schemes, and further internationalization.
Amid these trends, the number of ransomware attacks in Germany increased substantially between 2020 and 2021. This goes hand in hand with an increase in the number of active ransomware gangs, higher activity per gang, possibly more media coverage and thus more available data, and the ongoing pandemic. Germany’s industrial sector seems to be hit hardest. However, when considering only non-attributable ransomware attacks, the public sector, education, and health seem to be most affected. This deserves further research.
While it is hard to say how the general trends will change in the near future, it is likely that ransomware groups will further advance technologically. One example are Linux-specific ransomware builds that are already becoming more popular among ransomware gangs such as REvil or Conti, enabling them to encrypt virtual machines on ESXi servers and quickly increase the scope of an attack. It is also expected that both encryption algorithms will become faster and time between the actual deployment of the ransomware payloads and initial access shorter. In addition to technological advancements, ransomware gangs and the whole cybercrime ecosystem are likely to further specialize. What should be monitored is the rapid, innovative development of the initial access market, which has become key for the ecosystem.
However, there are also positive developments: For example, in 2021, law enforcement played a major role in combating the threat of ransomware, not only drastically changing the composition and hierarchy among the ransomware gangs but also the general environment in which ransomware gangs, their affiliates, and facilitators operate. In anticipation of the next few years, more internationally concerted law enforcement actions are to be expected that will further disrupt infrastructure, arrest suspects, and target facilitators (such as cryptocurrency exchanges or other malware). Besides law enforcement actions, the general awareness for ransomware attacks has increased in all sectors of society, leading to new initiatives and resources. Both, together with strong security postures, will hopefully prepare organizations for what is to come.
Related
